
Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Watch as world freediving champion Guillaume Nery takes an incredible dive into Dean's Blue Hole in the Bahamas (on ONE SINGLE BREATH!)

Via WonderHowTo World, LoadSave: Rock Band 3, coming this Fall, was revealed at none other than USA Today. Fully functional 25 key keyboard, 80+ songs including The Doors and Bohemian Rhapsody, Pro mode, updated guitars, and a kitchen sink are included in this new sequel. USA Today:

These are pictures of our garden, as of New Year's Day. Everything looks different now. The grapevines are coming back, and the oranges have finished their season. Our artichoke, sadly, got trampled and didn't really survive the pollution of the large Station fire.
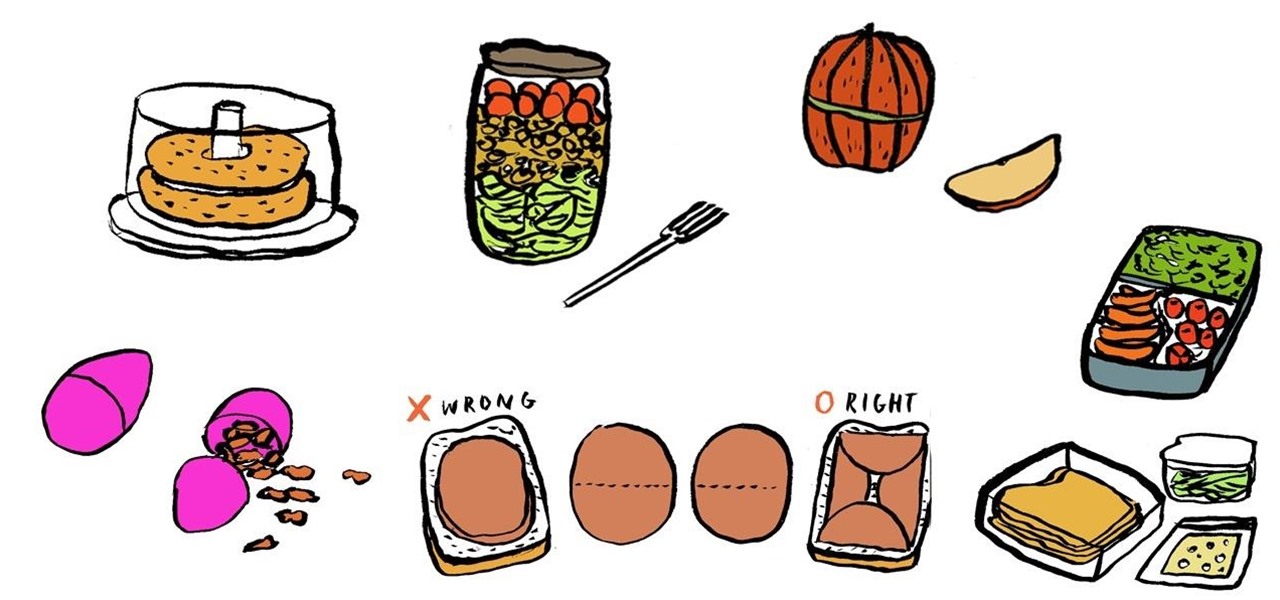
Bringing your lunch to work doesn't always have to involve boring brown paper bags and plastic ziplocks.

Candy machine hacks are so popular now, one might think it's easier to get candy from a vending machine than from a ... baby.
Some interesting news this week, from Obama's new political ad, to the $20,000 payments by Cardinal Dolan. Take a look:

When was the last time you took some time out of your day to play with your favorite action figure? Or build an entire town of Legos? Well, it’s time for you to dust off that old toy chest for this week’s Phone Snap challenge!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe".

Hello readers again! Sorry about the long wait (scary computer problems). Today I am going to talk to you about security problems on Wizard101. I have recently encountered many security flaws on Wizard101, including hacking, frauding and other crazy things. Wizard101 is the target for many online predators, many of who are fully-grown adults aged 60 or 70. Here is the link to an article I found about it: Wizard101 Internet Predators

Apple used to be a great, innovative company. But lately, it's filling its coffers with money raked in from selling folks on "new" and "unique" features that have been blatantly ripped off from Android.

There are over 38 million people who wear contact lenses in the United States, but nearly a quarter of those never replace their contact lens case. If you're one of those folks, you probably have a drawer full of empty, unused lens cases in your home. Start putting them to good use!

Bikes are a great form of transportation. They use human energy more efficiently than any other machine. You can keep it in your closet or hallway. You can even take it on the train in a pinch. However, this portability is also the bike's biggest draw back. If you own a bike in the city, chances are it will be stolen. Locks barely deter thieves armed with bolt cutters and crowbars. Throw the bike thieves for a loop and make a tilt-sensitive alarm. It will hopefully startle your bike's assaila...

Cryptography is a quintessential part of computer security in the modern world. Whenever you buy something on eBay or log into Facebook, that data is encrypted before it's sent to the server in order to prevent third parties from eavesdropping and stealing your sensitive information.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Since the beginning of last year, every six months or so the fine folks at Wolfire Games have gathered indie developers together to release a combo gaming pack called Humble Indie Bundle. Not only are the included games good, but the way one buys them is what makes Humble Indie Bundle one of the coolest products in games. Even better, Humble Indie Bundle #3 just came out last Tuesday and is available here for two weeks only.

So, at this time of the year, everyone seems to be going through a lot of stress - and by “everyone,” I mean, “anyone who has any contact with people who are in schools of any kind.” Still, stress can hit you at any time of the year, whether it’s right before Christmas, or when you’ve let all those little chores pile up, or when omigod all those bills are due tomorrow. When you feel like you’re being pulled in a million directions, it’s easy to want to murder everyone or plan an elaborate esc...

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

About Today's topic Today we will talk about diagnosing and fixing connection problems. Let's face it - the truth is everyone who uses a computer and has an internet connection will have to deal with this at some point. Connection problems often occur at the wrong time and it is a real pain.

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...

The small size of most indie game development teams is a strength, but also a weakness. It allows them to take risks and explore revolutionary ideas that a larger company could never justify to its shareholders, but also means they must navigate the game development labyrinth with minimal help, taking much longer than those with big development teams. Some of the most exciting indie games currently in development have been so for years, or look like they will be.

The Tokyo Game Show (TGS) is the biggest video game expo in the most game crazy country on Earth. It is kind of a big deal. As such, their "indie" game showcase/contest Sense of Wonder Night (SOWN) is a major opportunity for developers of all shapes and sizes to showcase their work to important industry leaders and expo attendees. 2011 will be SOWN's fourth year, and it began accepting submissions yesterday.

Hello, everyone. My friend and I recently released a Defense of the Ancients (DotA) map that went viral and thought I should share it with Minecraft World on WonderHowTo since you guys helped me out when I first started making videos! We were featured on Kotaku, RockPaperShotgun, Gamespy, The Verge, Joystiq and many more websites!Exciting!You can see the full details below are head straight here for the downloads.

You're sitting in front of your grandmother's Windows XP machine that has the worst infection you've ever seen. Safe mode? No dice. Restore points? They're compromised. Even worse, all of the files are hidden and none of the executables will run! This leaves her computer in a bricked state. Without some serious CPR, it will be lost to you. Sure, you could just reinstall the system, but then you might lose all of that valuable data.

WonderHowTo is a how-to website made up of niche communities called Worlds, with topics ranging from Minecraft to science experiments to Scrabble and everything in-between. Check in every Wednesday evening for a roundup of user-run activities and how-to projects from the most popular communities. Users can join and participate in any World they're interested in, as well as start their own community.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

This article is all about creating content. This is a very important concept to grasp because the content that you will learn how to create is going to be the basis for how you will advertise and promote your website. Content, meaning articles, videos, and even podcasts. Content is now really the new advertising. Instead of traditional types of advertising and instead of the traditional separation between editorial content and advertising, that has gone the way of the dinosaur.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

RESPECT - What It Means (in the picture above are my parents, both of whom I respect and cherish dearly)

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

Their were many pedestrians in the scene as,they seen firefighters struggling with the horrifying disaster and they couldn't do much only continue to stare as bodies continued to drop..

Last week, I started a weekly feature on Scrabble World called Scrabble Challenge, where you can solve a few (hopefully) challenging word puzzles. Normally, these will be on Fridays, but today I have a potentially unsolvable puzzle for you to try and solve, in addition to the upcoming one...

Ingredients: two people car






































