If you're a God of Mount Olympis, you may want to leave town, because Kratos is still angry in God of War 3 for the PS3. Killing Gods and defiling women are just a couple of his his hobbies. The other is treasure hunting. And in this IGN Strategize video, you'll find the locations of all ten Godly Possessions in God of War III. The Godly Possessions are more than just conversation pieces. Each has a special power you'll be able to use after beating the game once. You'll also get a gold trophy...

ShapeWriter is the iPhone version of Swype. With this app you can type texts extremely fast without ever lifting your finger off the keypad! In this tutorial, learn all about how to type at the speed of light using ShapeWriter and send messages so fast you'll wonder why you ever bothered to type things out in the first place. Have fun!

Check out this six-part video lesson on shaving for men. This covers the most uncomfortable places to shave on the body. Body shaving can be sensitive, so do so with caution. Yes, you WILL learn how to shave your private parts with this video.

Check out this video tutorial on how to make a cheap multi-touch pad like in the MacBook Air. Yes, that's right... you can make your very own multitouch, finger-sensitive touch pad for your computer. This is definitely the cheap way to go to make a Multitouch Mini (MTmini), with a maximum of fifty bucks down the drain. This multitouch touchpad (or trackpad) is easy!

There are almost as many types of sutures as there are types of wounds that a human can sustain. This video instructs the viewer in performing one popular type of suture: the vertical mattress stitch. This type of stitch is relatively simple and strong, and thus a good choice for many types of wounds.

To open the body of an HTML first open the HTML document, to do so write an open bracket, then html, the close the bracket. Next press enter. Type another open bracket, then type the word body, then type a closed bracket. Next press enter again. Now you can type an open bracket, then a backwards slash. Next type the word body again. Now type a closed bracket. Press enter once again. Now type another open bracket and then type html. Then type a closed bracket. Now you have just opened and clos...

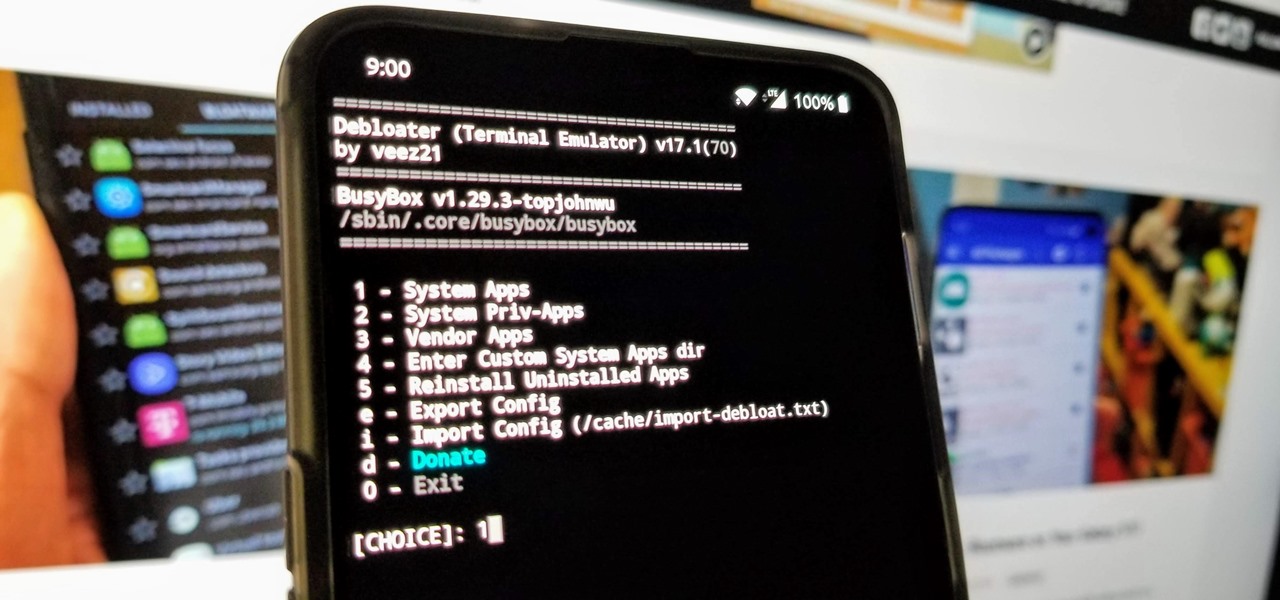
When you get a new phone, the last thing you want to deal with is a ton of preinstalled programs staring back at you. They not only clutter your home screen with apps you'll probably never use, but they're also wasting space on your internal storage and potentially draining battery. To truly uninstall them, you'll need root — but even then, it can be hard to pin down all the apps that should be removed.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

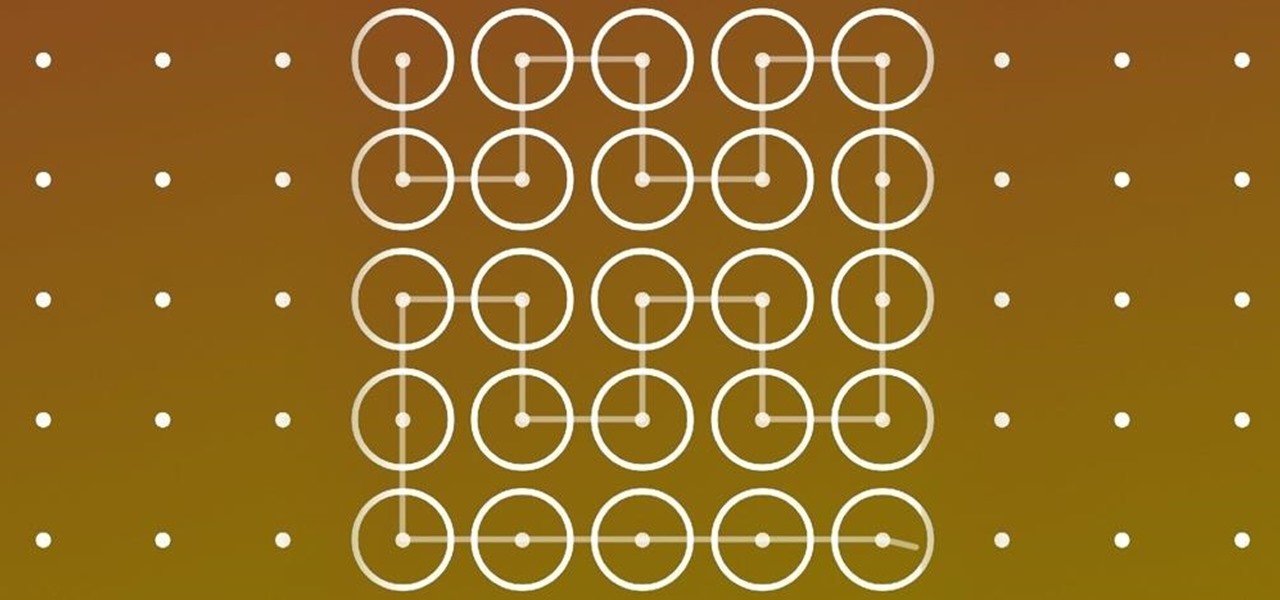
The first question people ask me when they come to my apartment is usually "What's your Wi-Fi password?" While I'm happy to give my friends free access to the internet, it's hard to walk each person through my secure password. Luckily, there's a way to create a QR code that will let people easily connect to a Wi-Fi network.

Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treatment has sent scientists in search of alternative ways to deal with the bacteria and prevent its catastrophic damage.

Welcome my aspiring hackers and programmers! Today i will introduce you to a programming language that as a hacker you should have in your set of hacking/programming skills (except if you're only interested in web hacking/programming...then you should go learn some html or PHP instead of C#).

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

Are you tired of wrinkled clothes? Have you ever had to iron one of your shirts more than once? Get tips and advice on how to fold your various items from ShaNay Norvell in this free clothing care video series.

Looking for a unique picture frame? Learn all about decorative picture frames including rustic frames, veneer frames, ornate and dark wood frames and more in this free video series about professionally framing pictures.

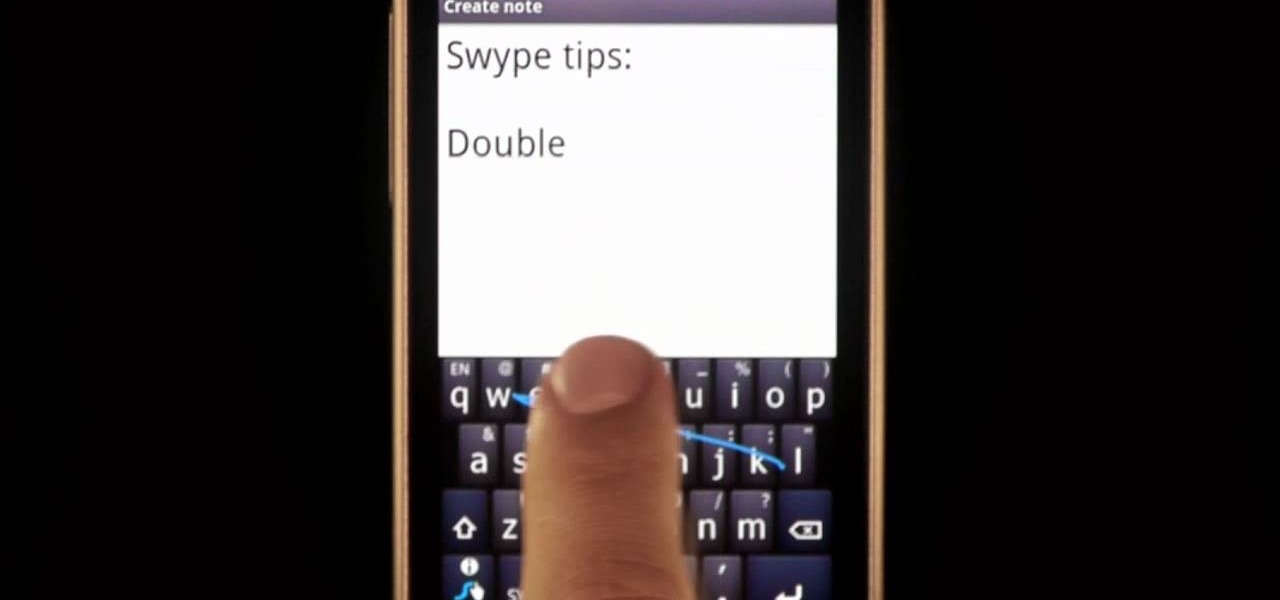
Typing notes with Swype is as fast and easy as you can get and in this clip, learn how to tackle less common word combos like double letters. For example, how would you type "cool", "common", "letters" or "bubble"? In this quick tip tutorial from the makers of Swype, learn how to add these words to your texts and not lose a second of speed! So, follow along and get started typing things like "speed", "follow", "Google".. there is no limit to the "speedy" words you will be sending!

This film was awarded the Green Ribbon in Itami Film Festival, 1993. Learn how various techniques of animation work and see some amazing examples- including an animated pin up girl! The film is in Japanese dialogue with English subtitles.

Waking up your Apple Watch to see "your heart has shown signs of an irregular rhythm suggestive of atrial fibrillation" might come as a shock. While your watch can send you warnings if it detects a fast or low heart rate, those messages are pretty vague, while the abnormal arrhythmia alert can downright scary. So what should you do if you receive one of these AFib notifications?

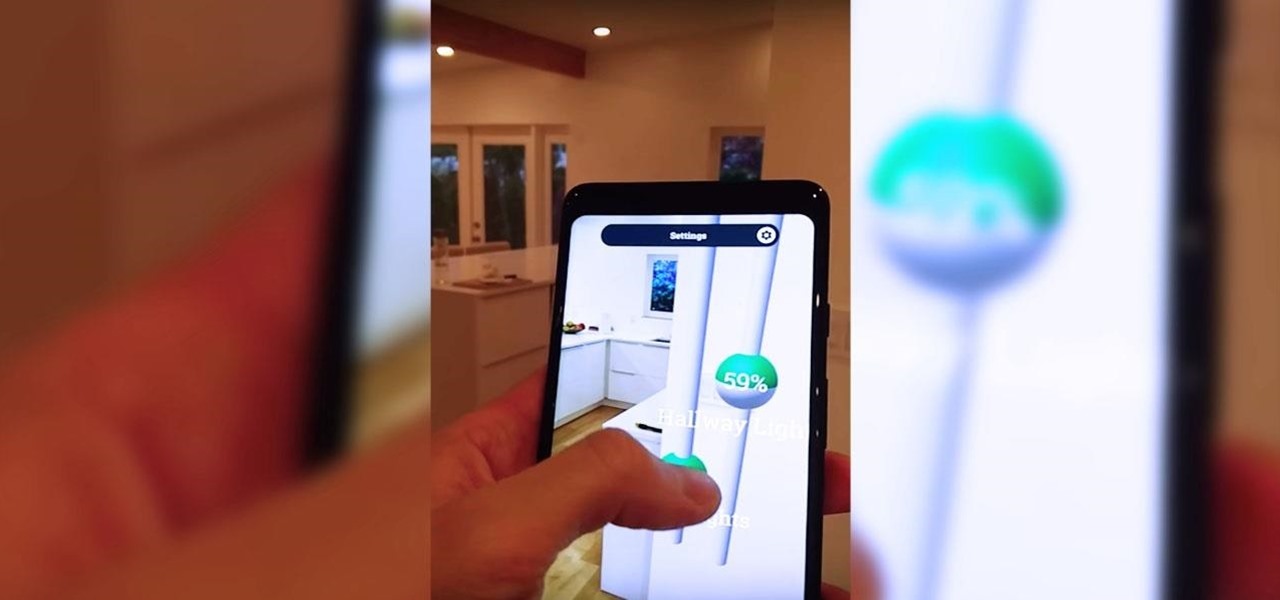
Voice-activated digital assistants from Amazon, Apple, and Google currently have the upper hand for home automation integrations, but a new augmented reality mobile app promises to give homeowners and renters visual control over their connected appliances.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

These days, our smartphones carry some very sensitive data. From banking app passwords to personal photos, there are many things on your Nexus 5 that you might not want other people to have access to.

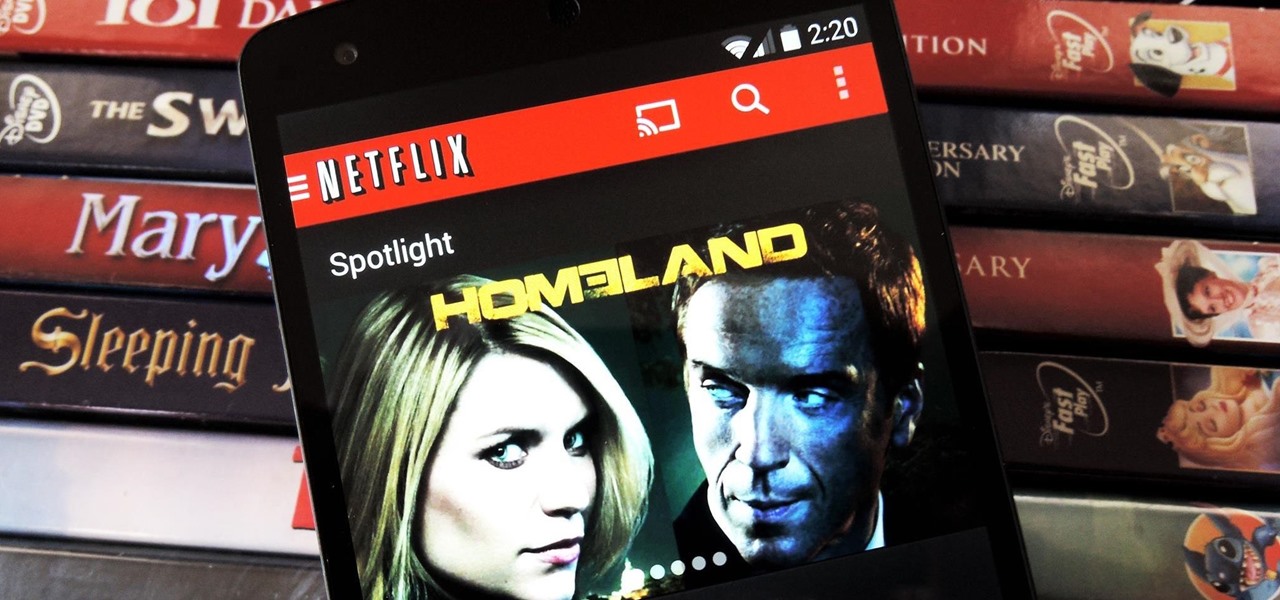
Out amongst the ether of the internet lies a completely different version of the Netflix library you've come to know and love. Because of licensing and rights fees, the streaming media giant maintains separate libraries for each country it services. Ultimately, this means that certain movies and TV shows are only available in certain countries.

The thermal fuse in your dryer is a safety device designed to prevent the dryer from overheating. The fuse is heat sensitive and when the dryer becomes too hot it will blow. If the fuse has blown then the dryer will either stop working or there will be no heat when the drum is turning. A blown thermal fuse is simple to replace. With a few tools, a do it yourself warrior can save valuable money from being wasted on a service call. Here is a detailed set of instructions on how to replace a ther...

Whether you're at work or in class, there are times when using your phone is unacceptable, regardless of that subtle yet sudden twitch in your arm that arises every time you hear the vibration of a text message.

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse. Next, you can do network pranks by running cmd.exe as administrator. Then, go and see who is on the network and type in "msg /server:(ip address) and message". You can also do a ghost typing prank, which you will create ...

There are two basic types of launchers you can use to play Beyblade: light launchers and Beylaunchers. They are both effective but play rather differently, so watch this video for a rundown of the differences and different strategies for each launcher type.

Today is the anniversary of George Harrison's death nine years ago in 2001, and we thought a commemorative music lesson was in order. And instead of the usual Beatles fare, we thought we'd show you something a little less known, but just as good— "Handle with Care" by the Traveling Wilburys. Many still aren't familiar with the Traveling Wilburys, despite the superstar musicians involved, but that doesn't change the fact that these guys were awesome!

In 1998, a Beechcraft Baron was following a Boeing 757, with approximately 3 to 5 miles separation. Air Traffic Control warned the Baron pilot three times with the phrase the phrase pilots hear on a regular basis: "Caution. Wake Turbulence".

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

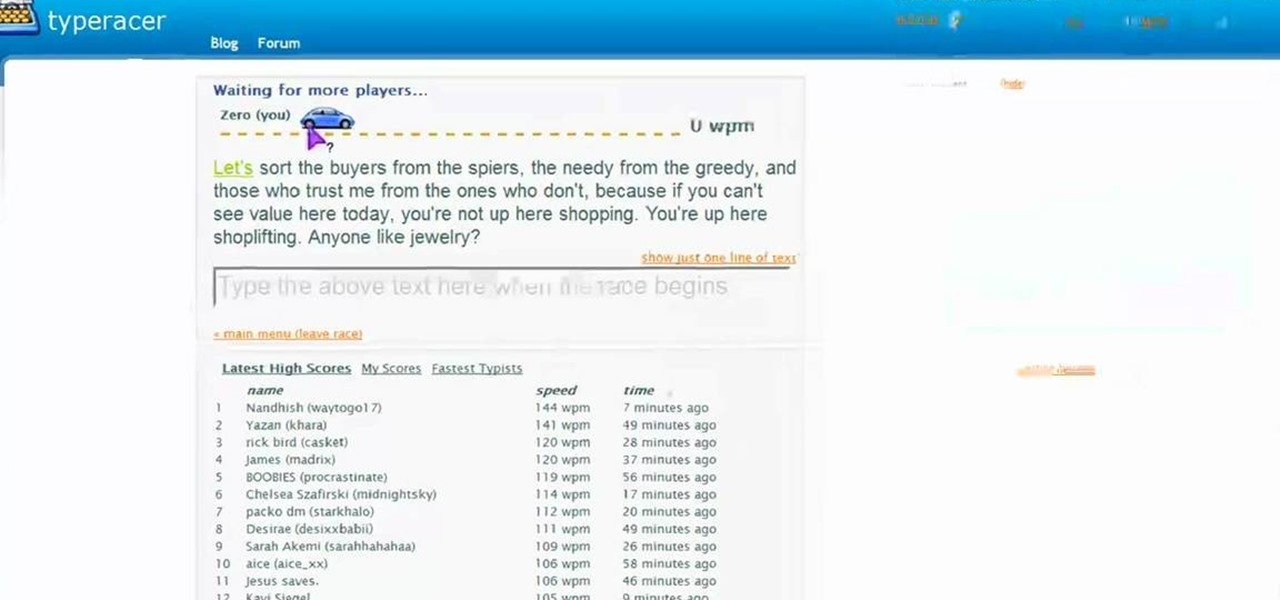
In this tutorial, we learn how to improve your typing speed. First, log onto your internet browser and go to the website, Typeracer. Once you are on this site, you can create an account and start to type on it! When you are on this, you can go into different types of races, then see what your scores are against other people. You continue to type until you win the race you are in. Once you are finished typing, you will see your stats and you will be able to improve from there. This is a great ...

This video is about how to dress to flatter your body type. Curvy body types look good with vertical stripes and clothing that accentuates the waist. High-waisted and belted bottoms and over-sized accessories work well for this body type. Pear body shapes look good in structured clothing. Form fitting tops work well with a smaller bust, making "pears" look slimmer. Cinching in the waist is also flattering for pear body shapes. For athletic body types look good in skinny jeans to show off thei...

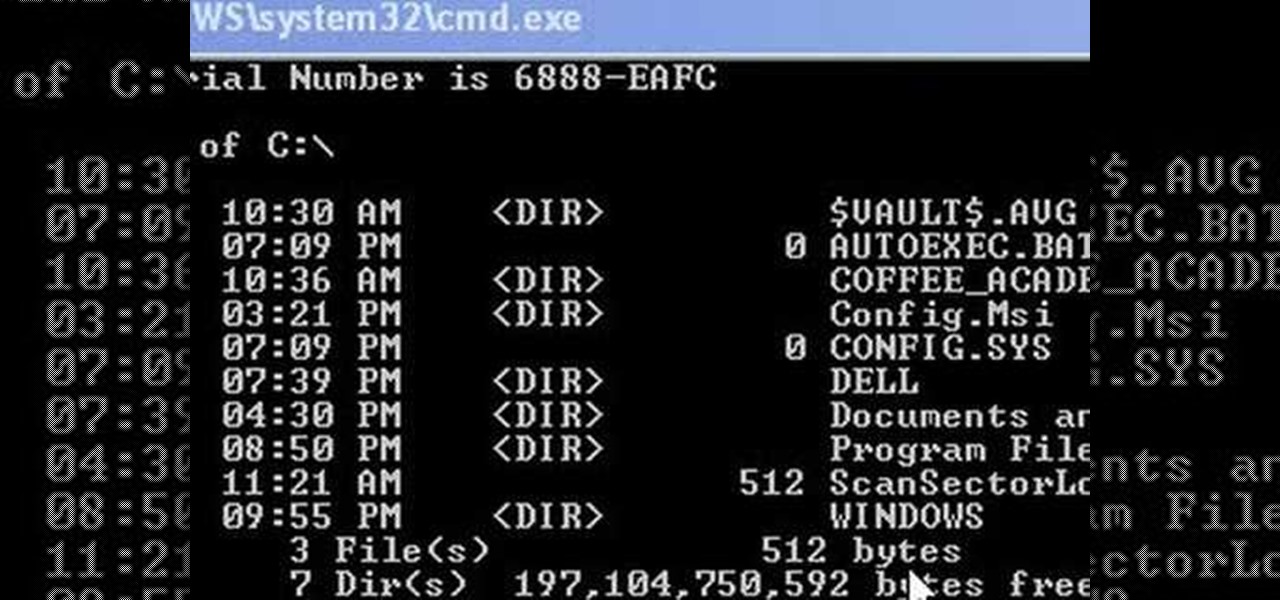
This video shows us how to change driving letters or directories in DOS command. Firstly go to start menu and then click on run. Then type cmd and press OK with which a DOS command cmd window will pop up. Now you need to change the directory and these is done by typing ‘cd..’ and after that press enter. Now you have changed the directory and now you need to see what’s in there and for that type ‘dir’ and press enter and this shows what’s in that directory. Now change to other directory by typ...

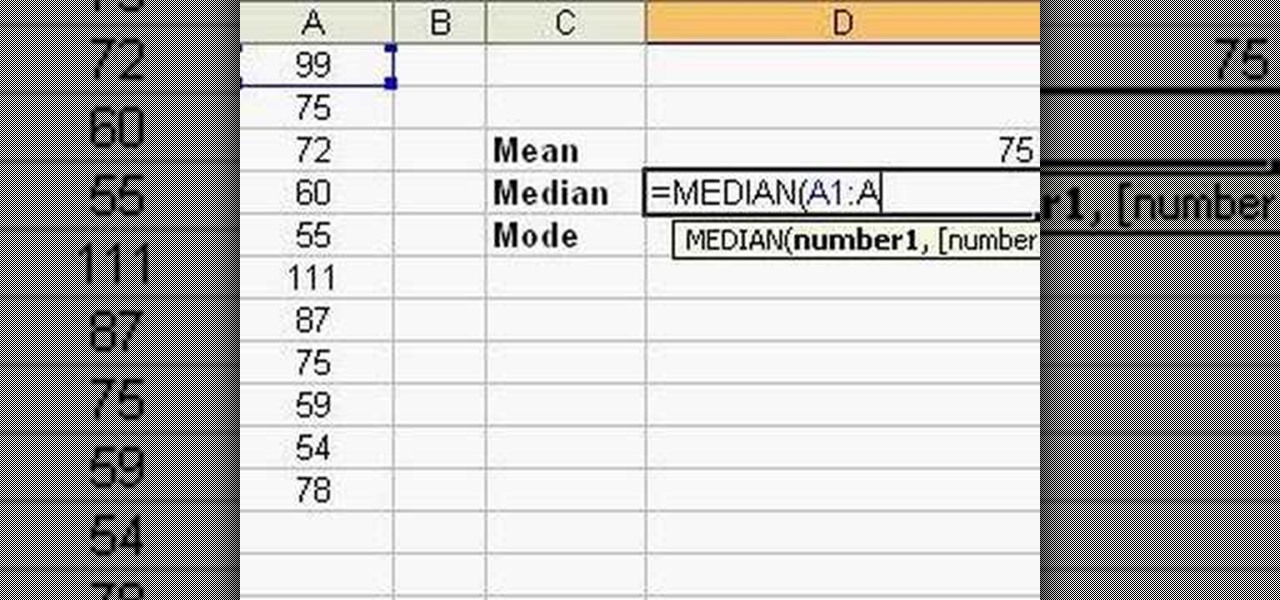
Follow this video to learn how to formulate calculations in Microsoft Excel. First type in a list of numbers in the cells. In order to calculate the median click on the cell where you want the answer to be shown. Then type equals, average, open bracket and insert the cell code where the first number is, colon, and then type in the cell where the last number in the list lies, and close brackets. In practice this is an example where the numbers are in a list from cell A1 to cell A11: =AVEARAGE(...

In this free video series learn how to tie knots from knot tying expert and outdoor enthusiast Dan Schieffelin.

inDesign has some hidden special effects that will make your type on a path much more compelling. Granted Type on a Path is not a new concept and has been around in Illustrator for years. However, no other application out there can handle Type on a Path as well as InDesign CS2.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

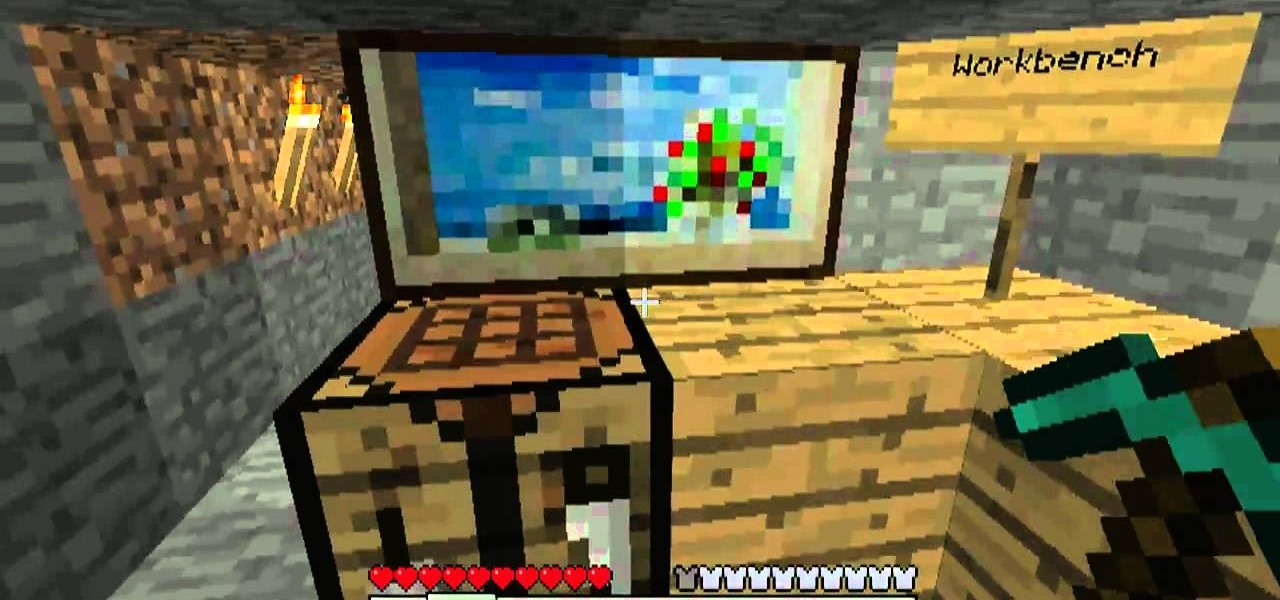
A big part of the fun in Minecraft is figuring out all of the different things that you can craft and how to craft them. Sometimes you just want to make the damn thing though, and to that end this video will show you how to make many of the game's better and more complex to craft blocks. You'll learn how to craft the following blocks:

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

Beyblade is a fun game from Japan that is very similar to Spinjas but much more complex. If you're new to the game or just ant some expert advice watch this video to learn about the four mains types of Beyblade (attack, defense, stamina, balance) and how they can each be used to play better Beyblade.