This video speaks about removing sensitive information in Adobe Acrobat 9. The viewer might get a very obvious idea of removing sensitive information by redaction. Redaction is the process of permanently removing sensitive information from a PDF file. This is done by opening the Advanced menu, clicking "Redaction" and then clicking "Show redaction tools", which can be in any format, images or text. The viewers will definitely get a clear idea of removing such sensitive information by redactio...
This video shows how to use a special tool to redact or remove sensitive information from Adobe Acrobat 9. This includes hidden metadata, file attachments, comments, hidden text and layer elements within a PDF file. You can also set it up when you're emailing. The Examine Document function highlights information that you may want to remove. You can then select the different types of data and choose which things you want to remove.

Here is a demonstration of a custom designed brush for the TVPaint software. This pen is sensitive to a realistic method of gestural drawing. Watch this instructional video to use this software brush to make several types of digital drawing strokes.

Have a file or a number of files too sensitive to be stored on your desktop hard drive? Thwart would-be snoopers with an encrypted USB flash drive. This free video tutorial from the folks at CNET TV will show you everything you'll need to know to create your own password-protected thumb drive directories.

Data thieves don't have to be programming wizards to get their hands on your personal information. They often find hard drives that contain financial and other sensitive data at flea markets, charity shops, the city dump—even on eBay. In this video tutorial, PC World explains how to completely erase sensitive data from old drives before recycling or discarding them. Wipe your old hard drives with this how-to.
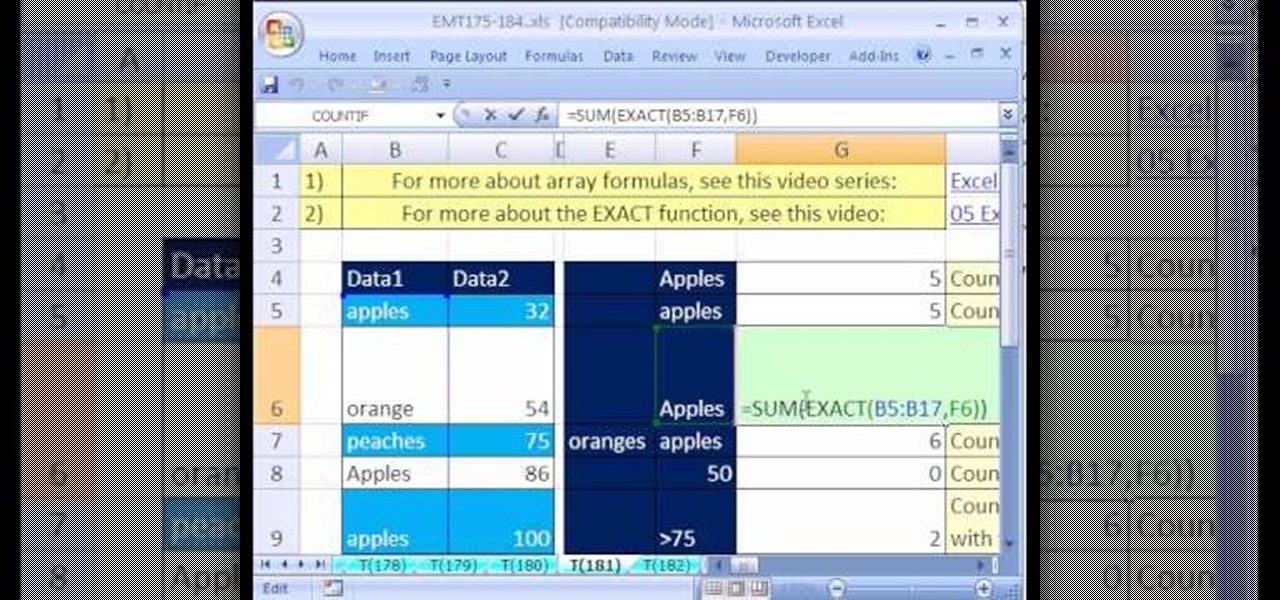
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 181st installment in their series of digital spreadsheet magic tricks, you'll learn how to count words (case sensitive) using the SUM and EXACT functions in an array formula.

TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

In this how to video Raven Symone teaches us about three different skin types and then makes a mask for her face. For dry skin you will need 1/2 a carrot, 1 avocado, and 2 tbs almond oil for your face mask. If you have oily skin you will need 1 apple, 1 egg white and 2 tbs lemon juice for your face mask. If you have sensitive, combination skin you will need 1/2 banana, 2 tbs yogurt, and 1/2 small cucumber for your mask. Raven Symone will also teach us how to do a tea steam to open your pores....

When the climate changes, so do all the things that rely on the climate, including people, plants, and pathogens. A European study recently took a broad look at what kind of microorganisms are most likely to be affected as climate change heats, cools, dries, and wets the world around us.

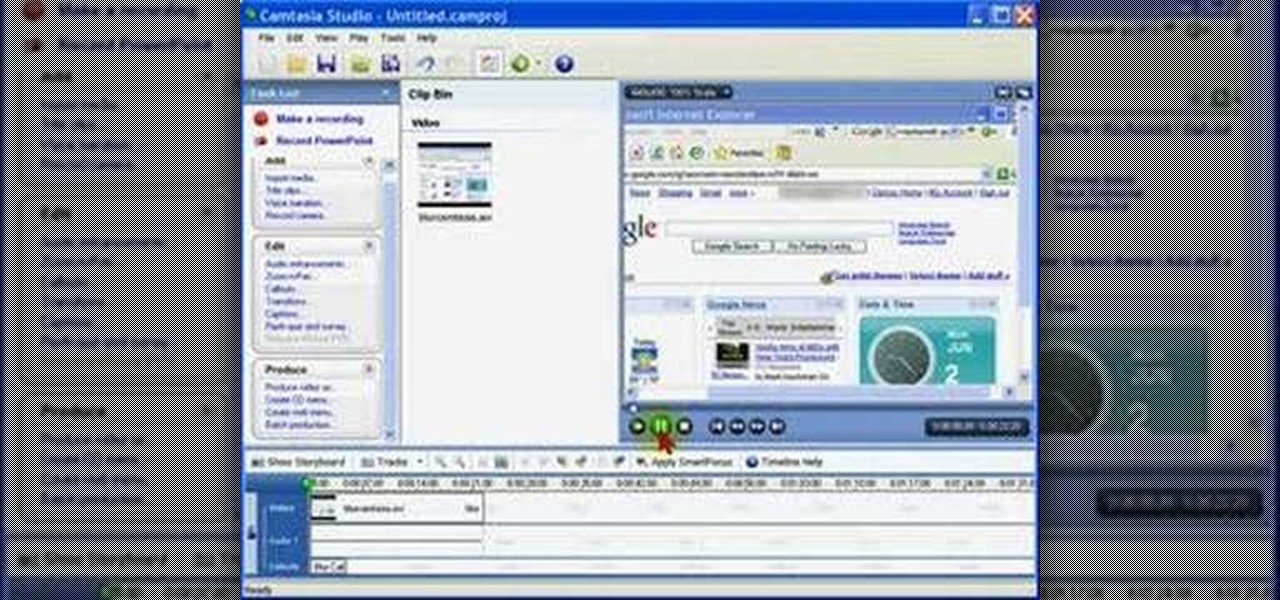
Watch Bill Myers show you an easy way to quickly hide sensitive screen capture text or images using Camtasia Studio.

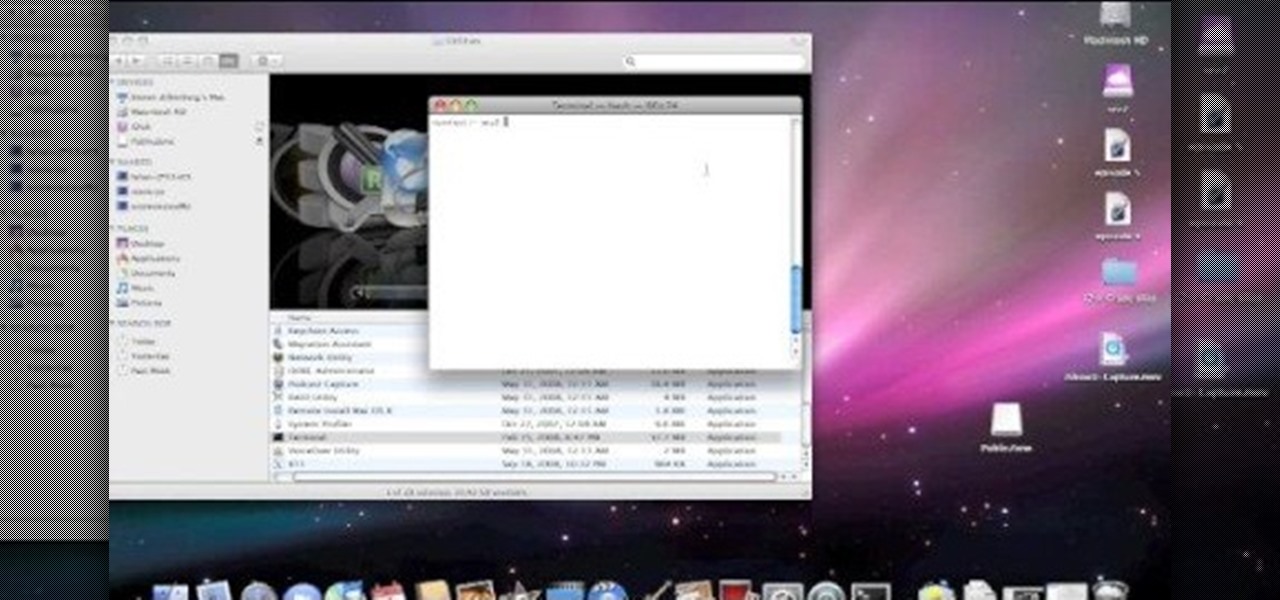
In this tutorial, we learn how to eject devices from the use of the terminal for Mac. First, go to the terminal of your computer where you will see a notepad sort of page. Next, type in "df" and then press return. You will now see a list displaying processes on your computer. On the bottom will be your public zoning device, which is your USB device. Next, type in "hdiutil eject -force (the code under "mounted on)- volumes-publiczone". This is not case sensitive, but don't forget or add in any...

The video shows how to join a home group on a Windows 7 network by helves shows you how to join a home group on a Windows 7 network of computers. It is approximately one minute thirty seconds long. To join a home group on a Windows 7 network you first go to control panel, then you click on Network and Internet, after that you click on network and sharing center, and finally click join a home group in the top right. You now select what file types you want to share with the other Windows 7 comp...

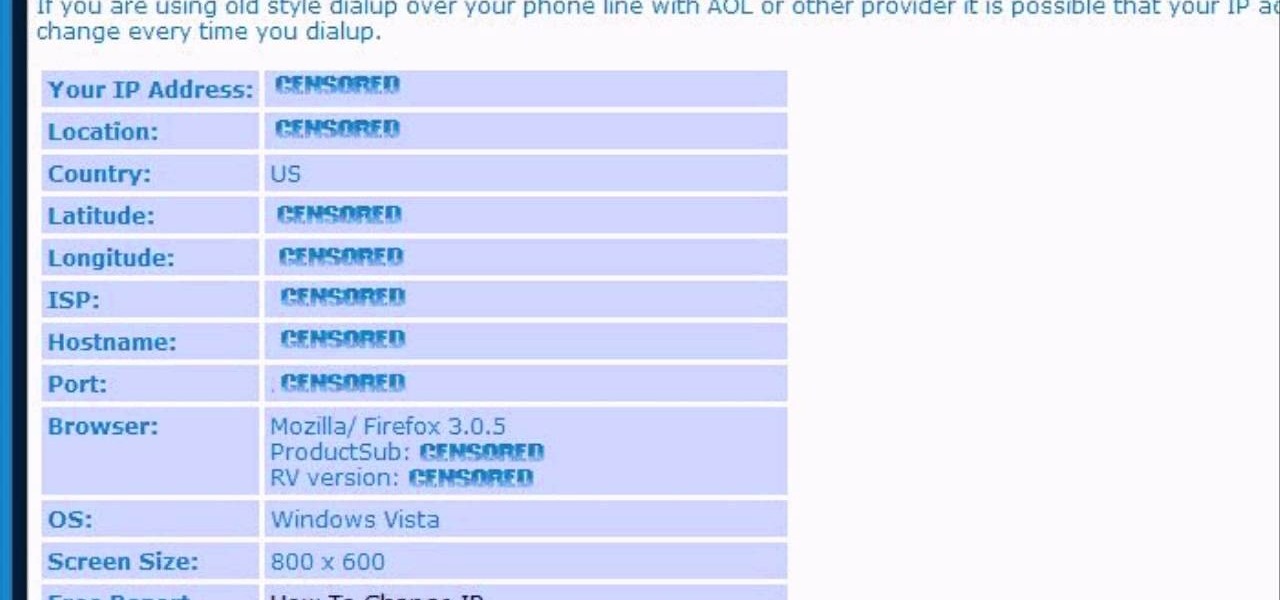
In this video, we learn how to find your IP address. First, start up your computer and open up your web browser. Next, you will type in the site: WhatIsMyIPAddress. Once you do this, you will be led to a new site which will load up your IP information at the top of the page. Once you have this information, make sure you don't share it with anyone else. If someone gets this information, they will be able to hack into your computer and ruin it. They could also access sensitive information and s...

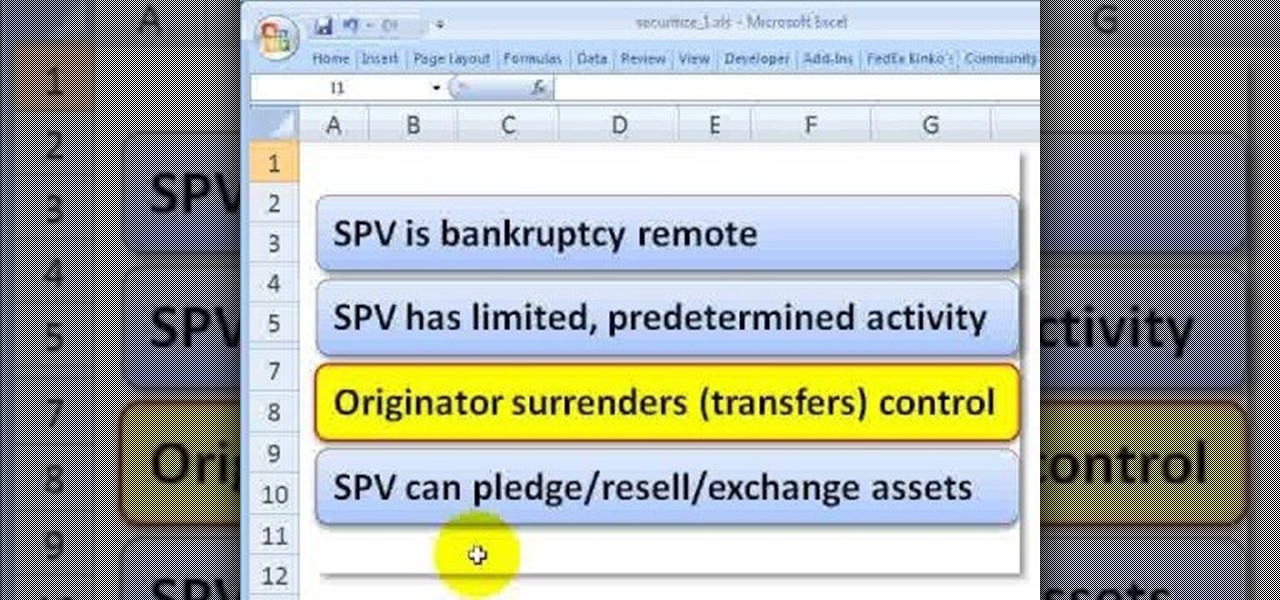
In this tutorial, we learn how to understand a securitization. This is a type of structured finance that has three key elements. the first is that there is a pooling of credit sensitive assets. In pooling the assets, you introduce diversification. The second element is to transfer credit risk to the third party and make rules around whether there has been a true transfer of credit risk. The third element in this is trenching of liabilities. This means when cash flows are transferred to a spec...

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Any electronic equipment is bound to accumulate dust, slight moisture, dirt or any combination of the above on its sensitive parts over time. The delicate nature of items also means further care is required.

There are 10 major ways to protect your PC. Disable Autorun, in Windows. Make sure that your system is up to date, by setting automatic updates. Always use a log on for your computer that does not have administrative privileges. Use different passwords, and change your passwords on a regular basis. Don't use simple passwords. Be careful of using links sent to you via email. Never disclose your sensitive information in public forums: e.g. social networks. Encrypt sensitive data on your compute...

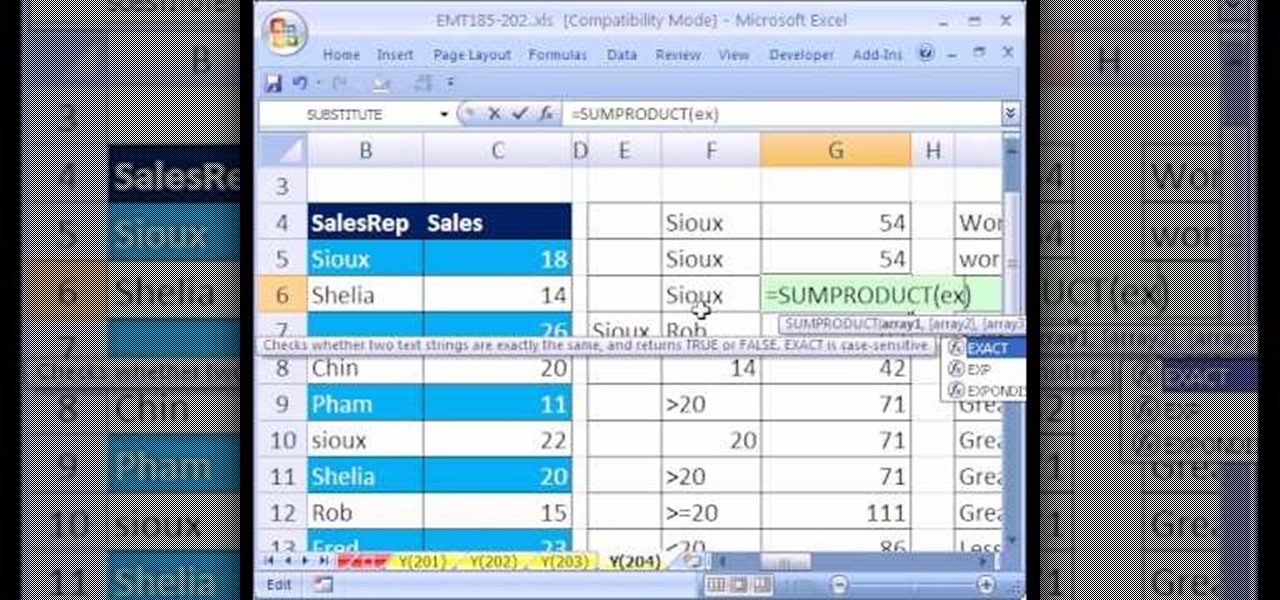
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 204th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the SUMPRODUCT and EXACT functions in an array formula to add the sales for a sales representative where lower and upper letters matter (i.e., are case sensitive) in the criteria (conditions).

Reading people's minds is something that most inquisitive and sensitive people have wished that they could do at some point. Well, what if you could? This video will show you a great multipurpose bar trick that will allow you to appear to read the mind or body of people in a variety of situations. It's really remarkable how easy this is and how well it works.

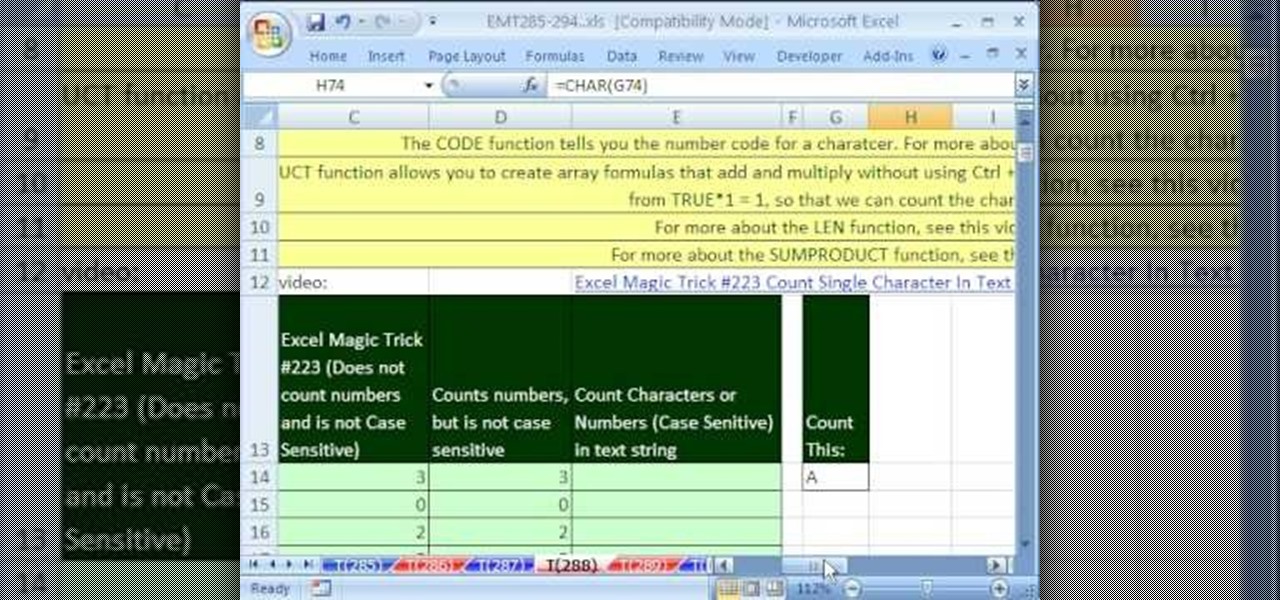
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 288th installment in their series of digital spreadsheet magic tricks, you'll learn how to count the number of characters or numbers in a text string with a formula that is case sensitive.

There's something seriously wrong with Apple's new Shortcuts app, and it's severely limiting the number of shortcuts users can install on their iPhones.

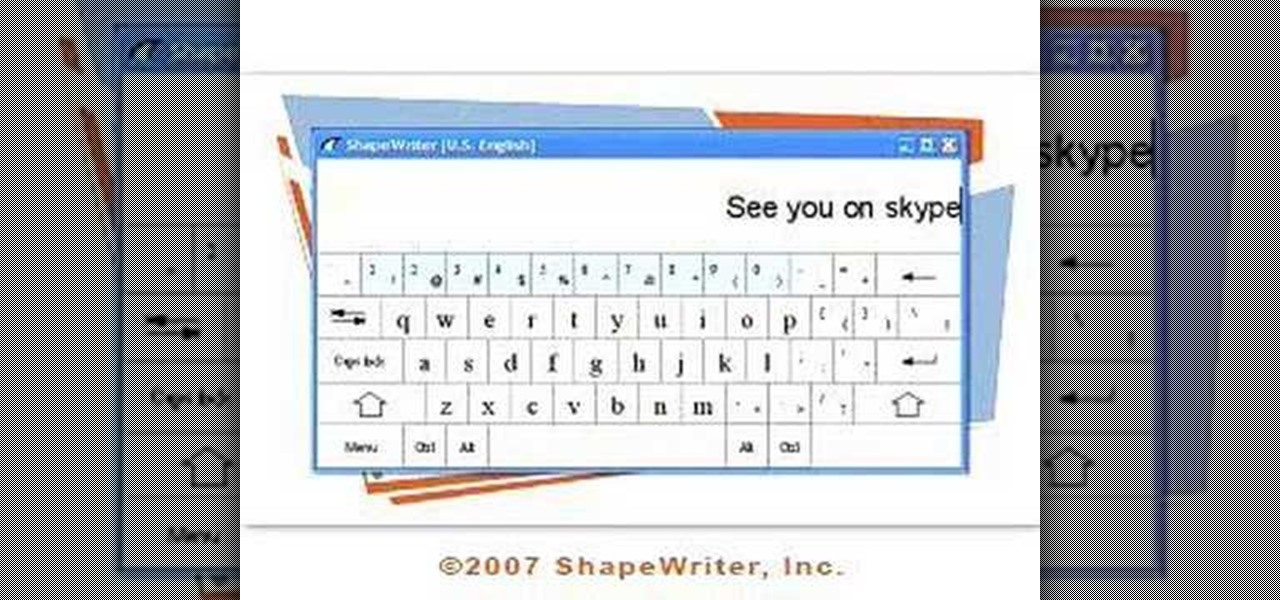
ShapeWriter is a quick typing program that is made for anything with a touch screen. You can use ShapeWriter on a tablet computer, PDA, cell phone or anything else where you have access to a touch sensitive screen.

You keep all kinds of important and sensitive information and data on your computer, and if your hard drives crashes, you're done for… unless you've backed it up. CNET has some "Insider Secrets" on how you can backup your system with an external hard drive, network-attached storage, and online services.

If your iPod is broken, don't worry! In this tutorial, learn how to remove and replace the screen on your iPod Touch so that it looks brand new again. This fix will not destroy your iPod if you do it properly and will still function as a heat sensitive touchscreen. Follow along and be careful!

Cooking Light food editors show you what to do -- and what not to do -- to create the perfect caramel. There are certain do's and don'ts to making caramel. It involves sensitive heat and making sure not to burn the sugar.

Like the crab that symbolizes them, Cancers can be a little soft-shelled at times, so woo these sensitive souls cautiously. Learn how to use astrology advice in dating, by watching this how-to dating video. Pick up tips on making a relationship with a Cancer work. Here a hint, do something nice for a Cancer when you suggest an activity for the both of you to do.

Password protect your files and folders in Mac OS X. This free video tutorial from CNET TV will show you how. Thwart would-be snoopers with this home cryptography guide, which presents easy-to-follow, step-by-step instructions on how to protect your privacy by encrypting your sensitive data.

Password protect your files and folders in Microsoft Windows XP or Vista. This free video tutorial from CNET TV will show you how. Thwart would-be snoopers with this home cryptography guide, which presents easy-to-follow, step-by-step instructions on how to protect your privacy by encrypting your sensitive data.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Have sensitive data that you want to make sure you securely delete? Or maybe you're getting an external drive ready to recycle or to give to a colleague. In this video tutorial, you'll find instructions for securely emptying your trash and also securely delete the contents of an external hard drive. For more, and to learn how to remove data from your Mac computer securely, watch this video tutorial from Apple.

Onion water makes invisible ink. The drawing becomes visible when it is heated. Use this as inspiration for one of your April Fools Day pranks!

Open up your mobile phone and solder on a light sensing resistor to make an alarm go off when the phone is in the light. Possible uses?

Shown here is another video tutorial made possible through TutVid. In this video, you are learning the basics of Action Scripting in Flash. This lesson is titled "Action Scripting:101." Action scripting is one of the coolest thing about flash. The thing that makes flash special is the ability to make simple actions interactive. Flash possibilities are endless!

If you had to answer the following statement, which answer would you choose? Water is:

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

Eczema sucks. It's a skin condition characterized by dryness, redness, and itching. Often this dryness leads to patches of dry skin that, if bothered excessively, can lead to pus. Those who suffer from eczema have extremely sensitive skin that needs to be treated professionally.

Baby hair can usually be extra fine, and baby skin is also sensitive to harsh shampoo. Detangling can also be a challenging. This tutorial shows you how to take care of your child's hair, and still let them express themselves.

Bathing a baby means not only keeping them clean, but also taking care of their skin. This video shows you how to keep your child's skin soft and well moisturized. Make sure your baby doesn't continually suffer from dry skin, and always moisturize after a bath.

Need a hand figuring out how to care for the sensitive skin of an infant? This video guide from Health Guru will teach you everything you'll need to know. For all of the details, watch this video guide for new parents.