You probably already know what you want to do when you grab your phone. More than likely, you're either going to make a call, send a text, or open an app. So why can't you just do that right from your Samsung Galaxy S3's lock screen?
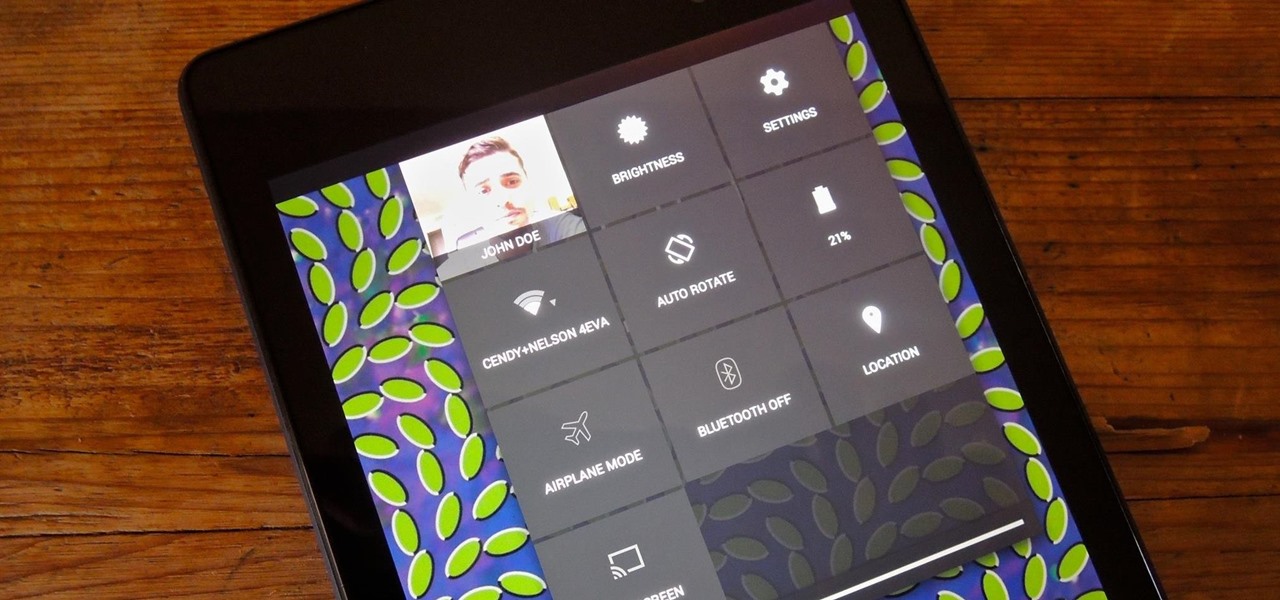
Accessing notifications and quick settings from the lock screen just makes things move quicker and more efficiently, unless of course we're using a secure lock screen. It makes sense that if we have face, pattern, or pin security enabled, we may not want notifications accessible, but really, that should be something we decide for ourselves—and now we can.

Julia, AKA Hairbeauty4you, gives detailed instructions on how to do a quick half up-do with a twist in under 10 minutes. She notes that this style is best for medium to long length hair. Julia starts with straight hair, then sections off the top part and clips temporarily. She then separates another section on either side of the top part- from the ear to the clipped section- and pulls it back into a high pony tail and repeats identically on the other side, securing each with clear rubber band...

While the clove hitch is not a particularly secure knot, it's useful in situations when the knot requires a little bit of give. The steps to tying this knot are demonstrated in this how-to video, and are shown at a fast pace so you can see how quick and easy it is to do. Watch this video knot-tying tutorial and learn how to tie a clove hitch knot quickly.

Deadbolts are a security lock which are usually put on exterior doors. Many saftey experts recommend increasing the strength of your home deadbolt lock. This quick tutorial teaches you how to make your deadbolt extra secure and increase the safety of your house.

Watch this quick instructional cinematography video that shows how to balance a Canon XL2 professional HD digital camera on a GlideCam 4000 Pro. Learn how to secure the camera using this handheld camcorder stabilizer to prevent unwanted swaying, shoot fluid traveling shots, and produce professional works.

Learn how to tie a Round Turn and Two Half Hitches - a quick and secure way of attaching a rope to a railing or other fixed object. This is a good knot for sailing, boating, general outdoors and even bondage.

This is a cheap little hack from a $5 discount store headlamp. Check it out. Quick and easy. You need a bolt to secure to your camera. This is great if you are shooting long shots and need different brightnesses. Otherwise kind of ghetto.

This hacker's guide demonstrates a quick PHP script which may allow you to crawl through the operating system on your hosting provider. demonstrate the power of PHP on a Virtual Host, or vhost, if PHP is not correctly secured by your web hosting provider. For more information on this hack, watch this helpful video guide.

In iOS 13, Apple introduced HomeKit Secure Video, which allows smart home devices with cameras to give iPhone users a private and secure way to store recorded videos. Plus, it has benefits such as object detection and activity notifications. Logitech is the first to add support for HomeKit Secure Video with its Circle 2 cameras, and all it takes is a quick firmware update to get started.

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.

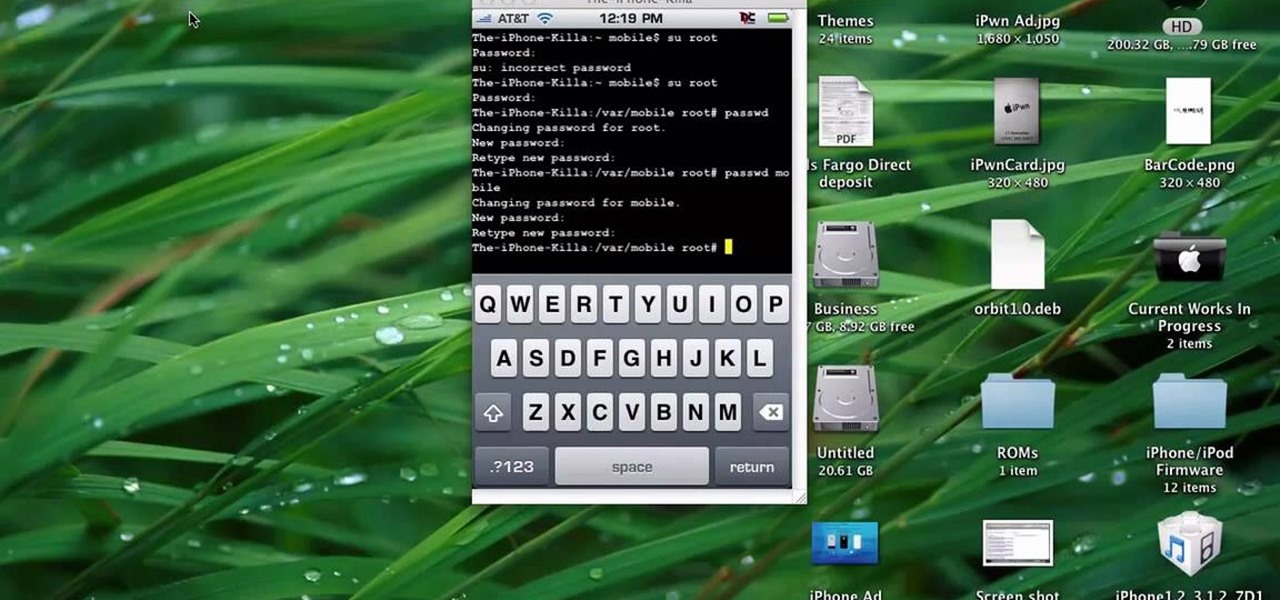
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to secure your Gmail account.

For anyone looking for a new way to style their hair, follow this quick beauty video to learn how to create a side pony tail style. This style works best for anyone with medium to long hair. All you need is bobby pins and some rubber bands to create this look. Take a boar bristle brush and tease the crown to create more volume. Take the upper half of your hair and pull it in the opposite direction you actually want your ponytail going in. place a rubber band about two inches down the ponytail...

The trucker's hitch is a good, strong knot with many uses. It's ideal for securing a load in a vehicle, and was used that way dating back to the days of wagons hauled by horses. In this video the folks at ITS Tactical teach you how to tie a trucker's hitch, quick and easy.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

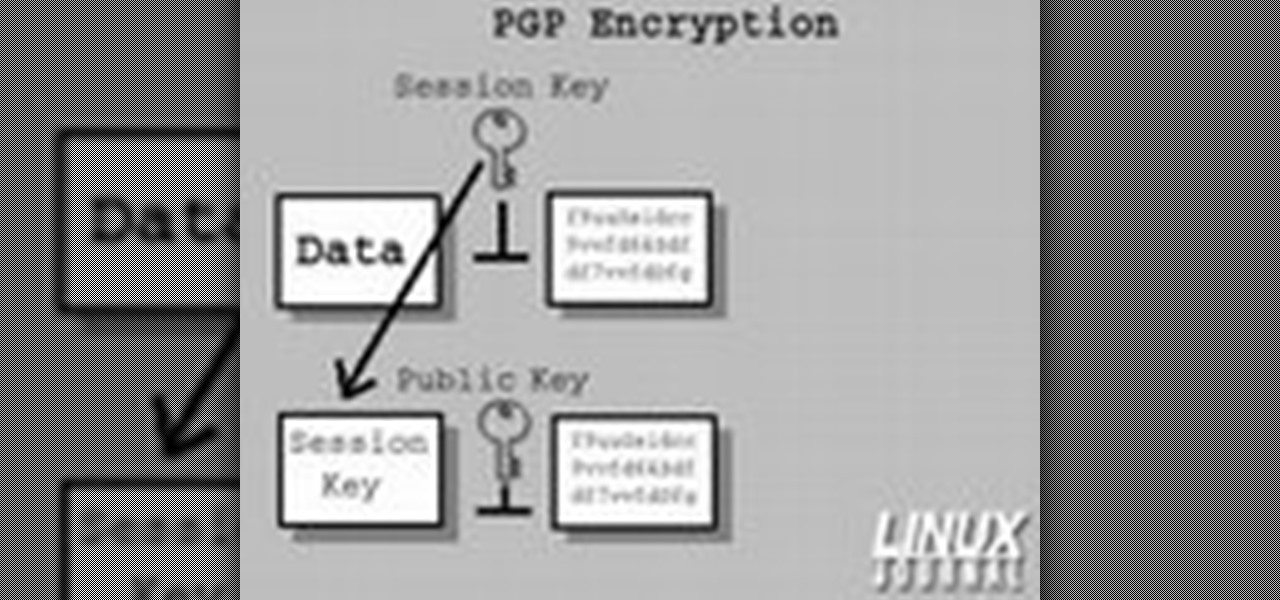
In today's time of rampant IT crimes, including identity theft, security is more important to the average computer user than ever. This tutorial, which was recorded and encoded for the Internet usingly only open source tools, demonstrates how you can use GnuPG to secure and verify data on your GNU/Linux box. Secure your Linux computer with this how-to.

The Flower god gets us all ready for the Chinese New year with a quick and very simple flower arrangement for a table centerpiece. You'll need some good luck bamboo, some ivy, little pieces of ginger and some passion flowers to accent the green. Take some of the ivy leaves and cover the centerpiece base. Cut them short at a sharp angle to cover everything. Next use the good luck bamboo to add height. Cut these at a sharp angle as well so that they will stay secure. The angles help it work as ...

The pitzen knot has various uses, but it's ideal for securing a hook to a fishing line. It's relatively easy to learn and quick to do once you know how. In this video the folks at ITS Tactical teach you how to tie a pitzen knot.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

You know how sometimes you'll wake up in the morning gunning for a fabulous hairstyle, then spend an hour curling your strands to perfection only to find that when you step outside it's raining? Rain literally rains on your hair parade because it brings lots of frizz-causing humidity and wetness.

In this tutorial, we learn how to fit a dry lining back box. This is very easy to install, and the sides will grip the wires on your light. First, determine where you want your switch, then mark a quick line using a sturdy level. Next, you will cut out a hole in the wall the size of the box. After this, push the box into the wall. Then, you can add in the light switch to the box and secure it with the wires that are inside. This will finish up this project, just make sure the wires are place ...

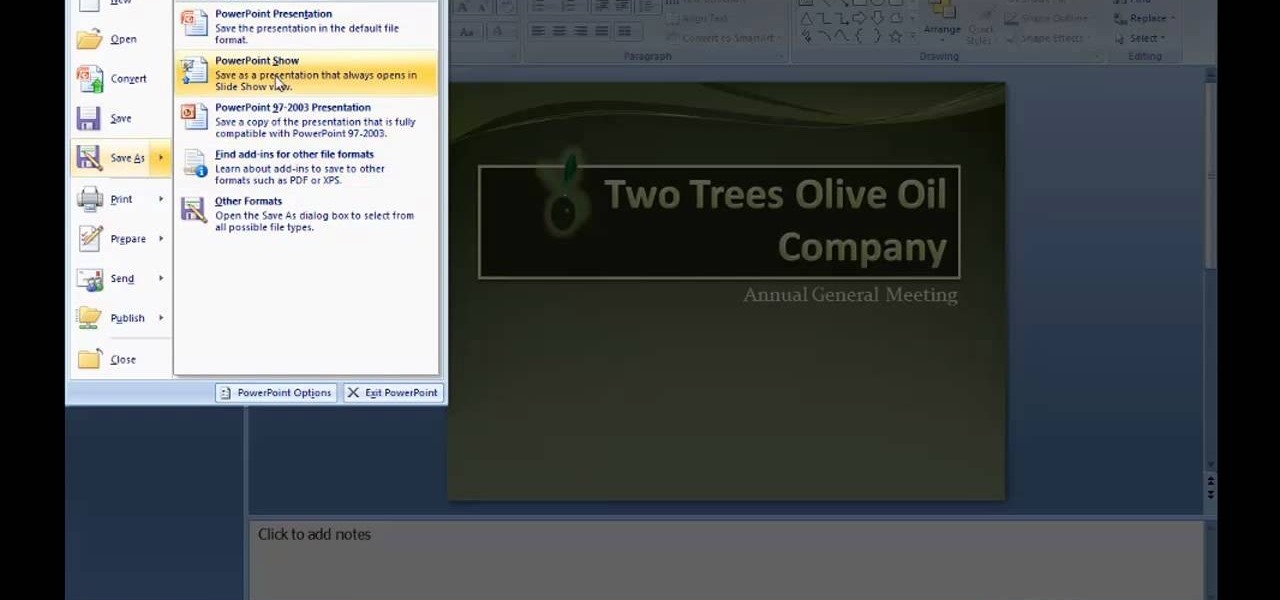
There are many new features which will make you more comfortable in doing your work in PowerPoint 2007 which will force you to switch from PowerPoint 2003 to PowerPoint 2007. There are number of new features in PowerPoint 2007.

Need a girl toga fast and easy for that crazy party coming up? This tutorial will show you how to make a toga quickly using common materials. Taking a bed sheet, you will need to open it and hold it lengthwise, folding it in two. Then, taking two pins, measure out the distance between two shoulders and secure the pins at two locations on the bed sheet which more or less will match up with the location of your shoulders. Then simply slip the toga over your head for a quick and simple outfit to...

Framing and matting your favorite posters or art can get expensive! In this Curbly video tutorial, you'll learn how to make a quick and inexpensive frame. All you need are some basic supplies available at almost any arts and crafts supply store including: A sheet of plywood, a plexiglass cut to the size of the plywood, archival paper cut to the size of the plywood, frameless corner clips, and a bracket.

There are tons of quick pop up tents available nowadays, but the classic A-Frame tent still remains one of the most popular. A-Frames are those classic tents with the spikes in the ground that hold it up. They take a little more effort to erect but they are perfect for backpacking or short camping trips.

This new episode of Full Disclosure shows you how to use a SSH Tunnel to secure your data when you are on an untrusted LAN (ex. Coffee Shop, School's network, or Defcon). Furthermore, you can use the SSH Tunnel to bypass the LAN's internet filters. The SSH tunnel protocol works by encapsulates your data into an encrypted payload and transmitting it to the SSH Server which is setup on a trusted LAN.

Google released its "Android Security: 2016 Year in Review" report last month, and to no one's surprise, included its own flagship phones. However, one surprise on the list was the BlackBerry PRIV, which Google named one of the best Android devices for privacy.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

In this clip, you'll learn how to get started using Secure Computing's Secure Web Protection proxy service. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just over five minutes. For more information, including detailed, step-by-step instructions, take a look.

In this video tutorial, viewers learn how to secure a home wireless network. There are 3 types of security protocols for connecting devices. The 3 types of security protocols are: OPEN, WEP and WPA. Users should use passwords that are secure but no so obscure that they are unusable. The password should not be dictionary words. They should be mixed with casing and contain the user's phone number. Go to your router's website and log into the website. Find the setting for wireless security and e...

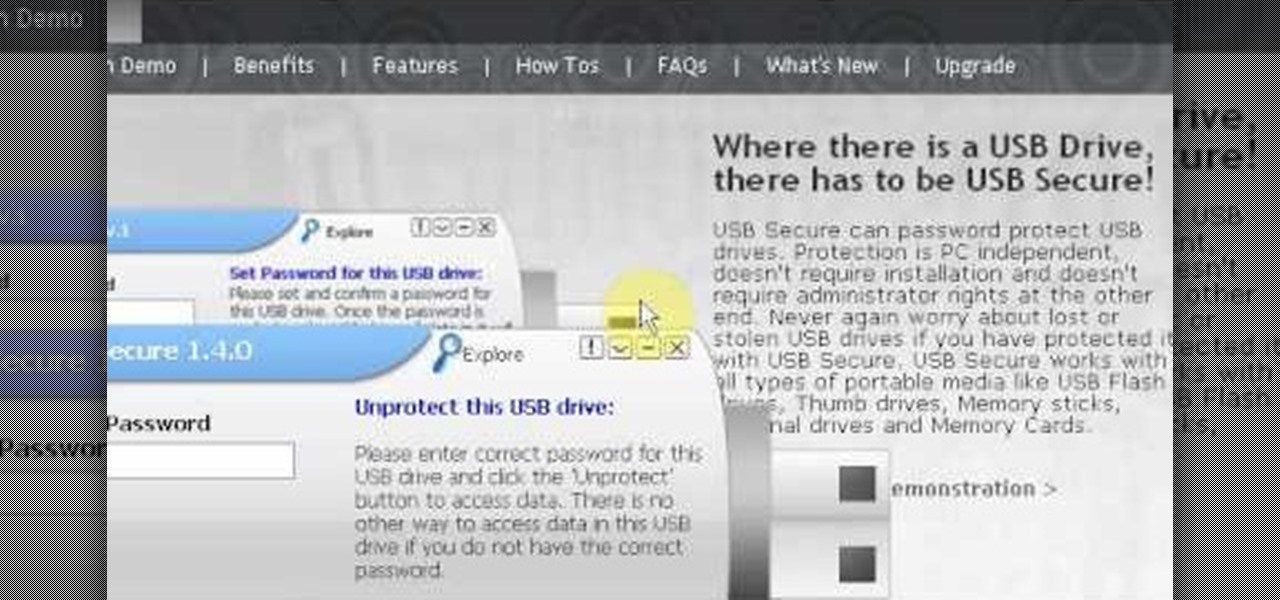
Have important files that you want to put on a USB drive but do not want anyone else to be able to access them? Put a password on it using USBSecure.net free resource.

Use three tools to create a simple ponytail. Use a hairbrush, a bobby pin, and a bungee band holder for this look. Using a bungee band instead of a standard ponytail holder eliminates some of the issues typically caused by pulling hair through ponytail holders. Start by using a bristled brush to brush the hair to one location on the head. Secure one hook of the bungee band in the ponytail and wrap the tail around the rest of the hair. Wrap it around again, and secure the other bungee band hoo...

Using ASP.NET Secure Services and Applications Services

Need to know how to tie a Bowline with a few ways of securing it? This way shows you how to secure it with a seizing so that it won't accidentally come undone. Included is a little variation of the bowline with a built-in seizing. If you don't have electrical tape to secure the bowline feed the bitter end back through the hole. It also makes it so you don't have a tail line dangling if you're towing something.

In today's time of rampant information crimes, including identity theft, security is more important to the average computer user than ever. This tutorial from Linux Journal Online shows how you can use GnuPG to secure and verify data on your Linux box. (This video was created using only free and open source software tools: TightVNC, pyvnc2swf, ardour2, audacity, jackd, LAME, kolourpaint, cinelerra-cv, mjpegtools, and ffmpeg.)

Buns and updos are gorgeous hairstyles, with one caveat: If they're not pinned perfectly and securely in place, all your hard work braiding and curling will go to waste as your hair slowly unravels.

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

In this tutorial, we learn how to lash a bamboo tripod. First, you will tie a clove hitch by taking one piece of bamboo and wrapping the rope around it, then crossing the two sides of the string together to make a hitch. Next, you will secure the clove hitch around the third piece of bamboo. Now, you will rap all the pieces of bamboo together with the rope. Continue to do this until all the pieces feel secure together. Wrap the rope several times around each of the pieces, then wrap it in the...

Picking a secure password is not only important for protecting your privacy, it's also very easy. Provided, that is, that you know how to go about it. This free video lesson from CNET TV will walk you through the process. For more information, and to get started creating and using high-security passwords yourself, watch this video tutorial.