
How To: Be a good band manager with the Naked Brothers Band
The Naked Brothers Band's manager offers some tips on how to be a great band manager. Rock out with the Naked Brothers Band!


The Naked Brothers Band's manager offers some tips on how to be a great band manager. Rock out with the Naked Brothers Band!

Watch this video to learn how to get any app you want in the Android Market for free. Using Astro File Manager and 4shared.com you can run any app you want for free on your Android device. Get all the apps you've ever wanted.
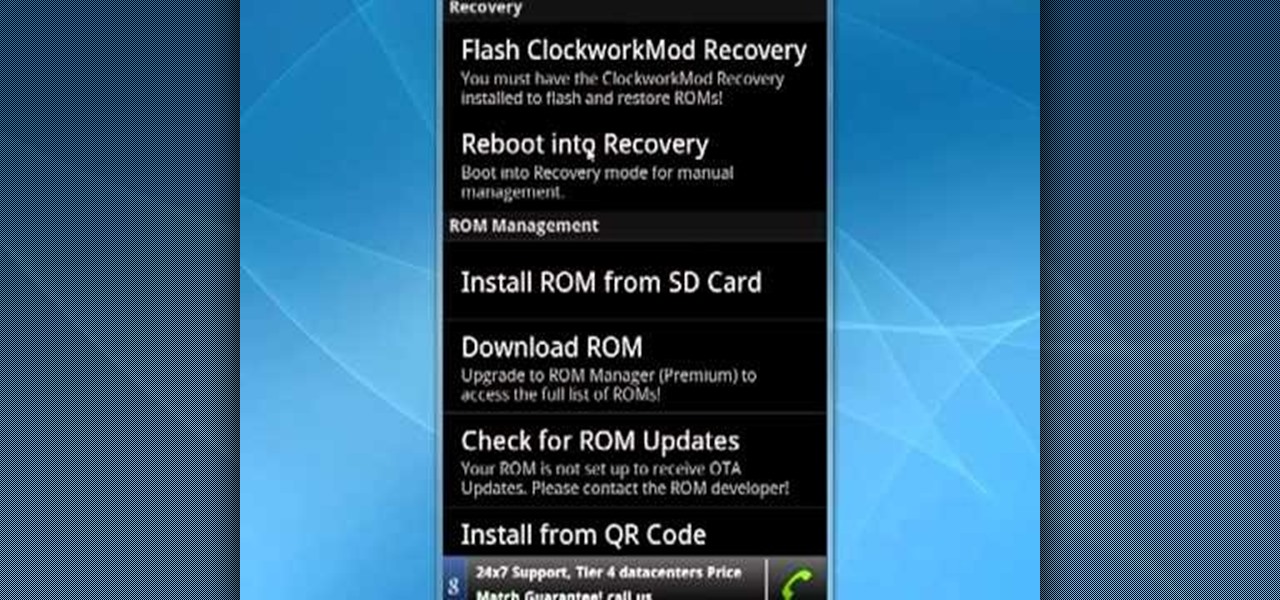
Learn how to manage custom ROMs on a rooted Moto Droid Google Android smartphone with a ROM manager app. Whether you've rooted your own Motorola Droid smartphone or just want to learn more about the process, you're sure to be well served by this video guide. For more information and detailed step-by-step instructions, watch this phone hacker's how-to.
Looking for a quick primer on how to use the File Manager on a Microsoft Windows XP PC? It's easy! So easy, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in a matter of a few minutes. For more information, including detailed instructions, take a look.
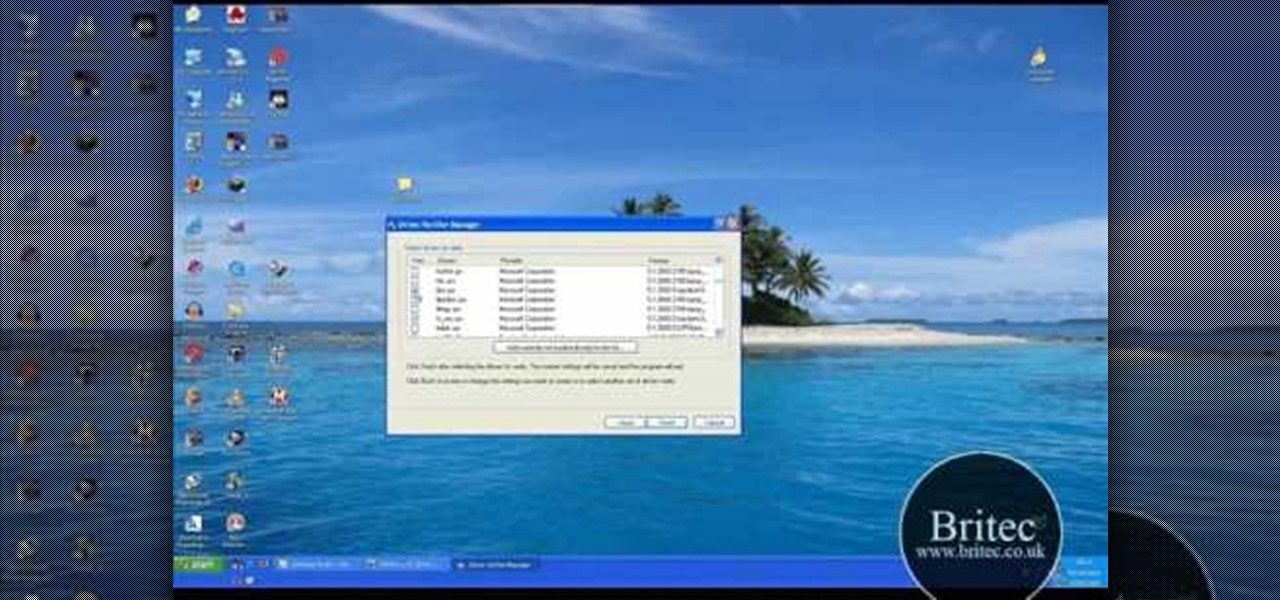
Need to know how to troubleshoot driver issues on a Microsoft Windows PC? With the Driver Verifier Manager, it's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

A whole new generation, the Millenials as they are somewhat awkwardly called, is entering the workplace and has as a group a different attitude then the previous generation. Many older managers have problems dealing with the younger generation, as they always have. This video offers tips for managers for dealing with Generation Y employees who may seem arrogant and entitled.

Politics have always been an unavoidable part of office life, but that has become even more the case in this down economy when competition between coworkers is more intense than ever. This can be a major problem for managers if their workers start being more concerned about their politicking than their performance. This video for managers offers tips for reducing the role of politics in your office, keeping your employees focused on the task at hand and more productive.
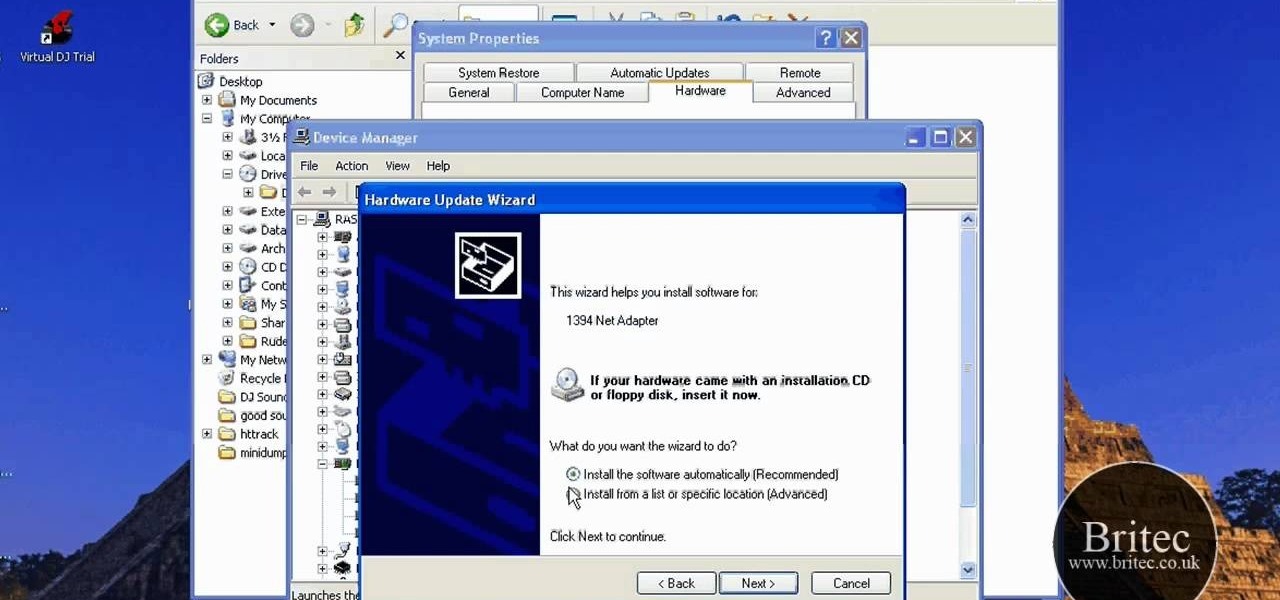
If your Windows PC has been running rather slow lately and you're not sure why - you may have unknown devices taking up space and energy. Check out this tutorial for details on how to detect and disable unknown devices in Windows Device Manager.

If you just got a new Android mobile phone, then chances are, the first thing you're going to want to set up is your email account, so you have instant access to your emails all the time, everywhere and anywhere. Setting up your specific email account or accounts is actually not hard. Best Buy has answers. The Best Buy Mobile team explains how simple it is to set up an email account on an Android cell phone.
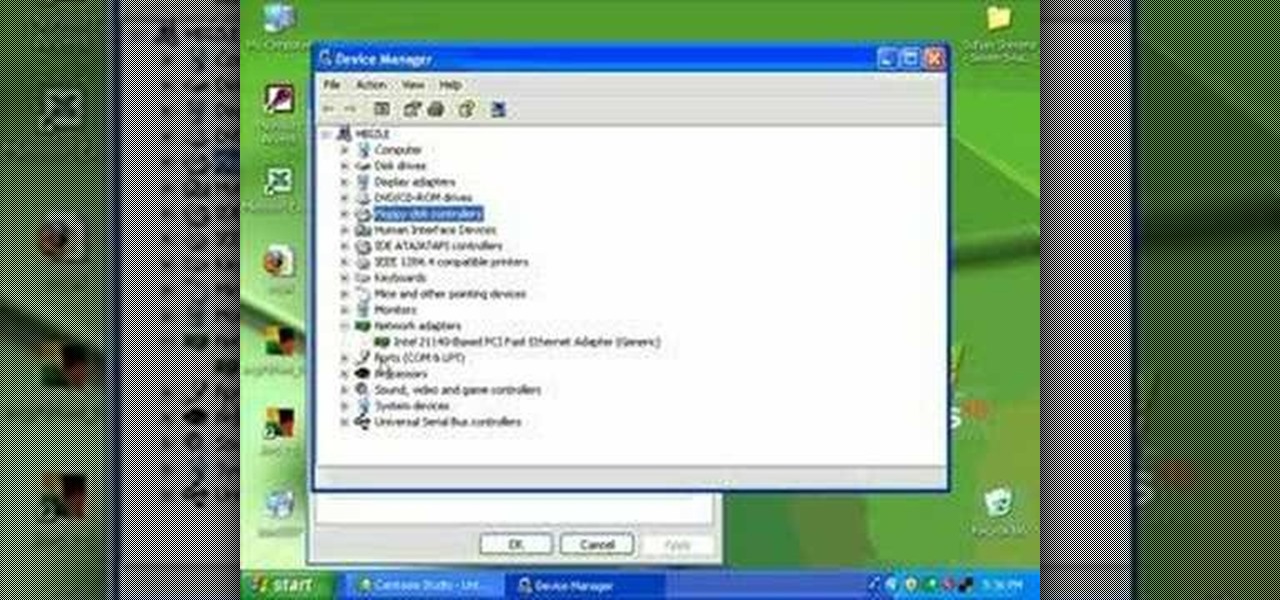
The beyourownit shows you how to remove and reinstall devices in Windows XP. The first thing he shows what to do is Right click on the My Computer icon and select properties then select then choose the hardware TAB. When you click on the Device Manager button, the Device Manager will appear where you can make changes to your computer. The user explains more to help you understand better. If you watch this video, you will find out how to reinstall devices in Windows XP.

Communication is an essential skill for successfully launching products. Whether you're developing the latest and greatest app or trying to get ahead of a large data science project, effective communicators are always in high demand.

If you didn't get the memo, passwords aren't enough protection for your online accounts. Even a long and complex password offers only one line of defense which can falter. Two-factor authentication adds an additional layer, bolsters your defense, and decreases the risk of your account becoming compromised.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

Task Manager got revamped quite a bit in modern versions of Windows. First introduced in Windows NT 4.0, it's become pretty popular among more advanced users. In Windows 10, Task Manager is not just a task manager anymore, it's also a system monitor, startup manager, history viewer, user controller, and the list goes on.

If you haven't heard yet, Google made it possible a couple months ago for every Android user running 2.2 or higher to track his or her smartphone or tablet using their Android Device Manager service. It's a super easy way to track, lock, and secure erase your Android device from the web without ever having to download a third-party application, like Droid Finder, since it occurs in the background via Google Services.
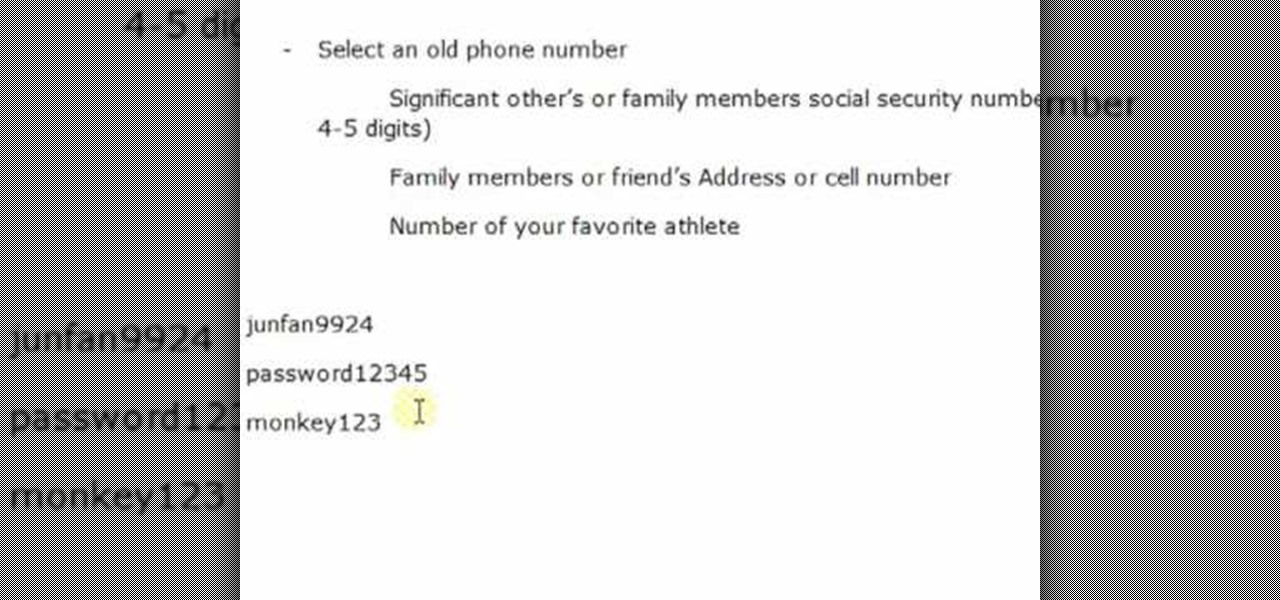
Life on the Internet is made up of passwords. You have a password for your Facebook, a password for your email, a password or your online banking - And the list goes on. In this video, learn how to create good passwords that are easy to remember.

When we reviewed the best file managers on Android, MiXplorer easily topped our list with its abundance of features, including tabbed browsing, support for up to 19 different cloud services, file and folder encryption, and much more. The only major complaint we had was the fact it couldn't be installed from the Play Store, but now, that is no longer the case.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

LastPass is a password manager that's been around for some time, and has finally made its way over to Android for use with apps, not just websites.

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...
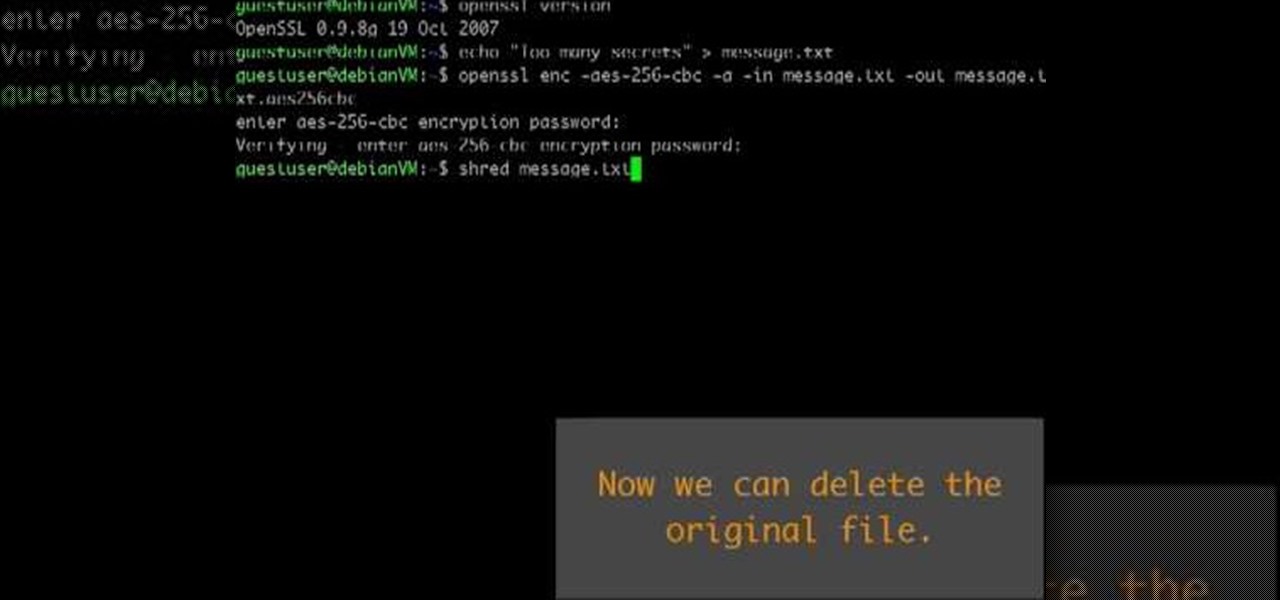
This video shows how to encrypt files with OpenSSL in Debian Linux. First we check if open SSL is installed on the system. If not, install it using packet manager. Next create the file going to be encrypted. Now encrypt the file. In this case AES algorithm in ypher block chaining mode is used. AES is US-government standard and can be considered secure. Now we are prompted for a password. In order for the encryption to be secure, we need to choose a strong password. Now we can delete the origi...
Video demonstrates tutorial of how to hide the logical drive icons in Windows. In the demonstration there is two partitions C and D and also there is a DVD drive, DVD Rom and DVD Writer. Here drives C, D and F from My computer is going to be hidden with help of utility called “No Drives Manager”. If you don’t want your young ones to access some of your important data you can hide it. It will just be hidden. This means if go to the address bar and types the name of the drive you can go to that...
Need to protect a section of your overall flash content (say movie or slideshow) from unauthorized access, learn how to do so in this video.
First things first: You can't actually recover a Joomla administrator password. That's because Joomla uses a one-way MD5 hash that prevents you from doing so. However, it is possible to reset your password.
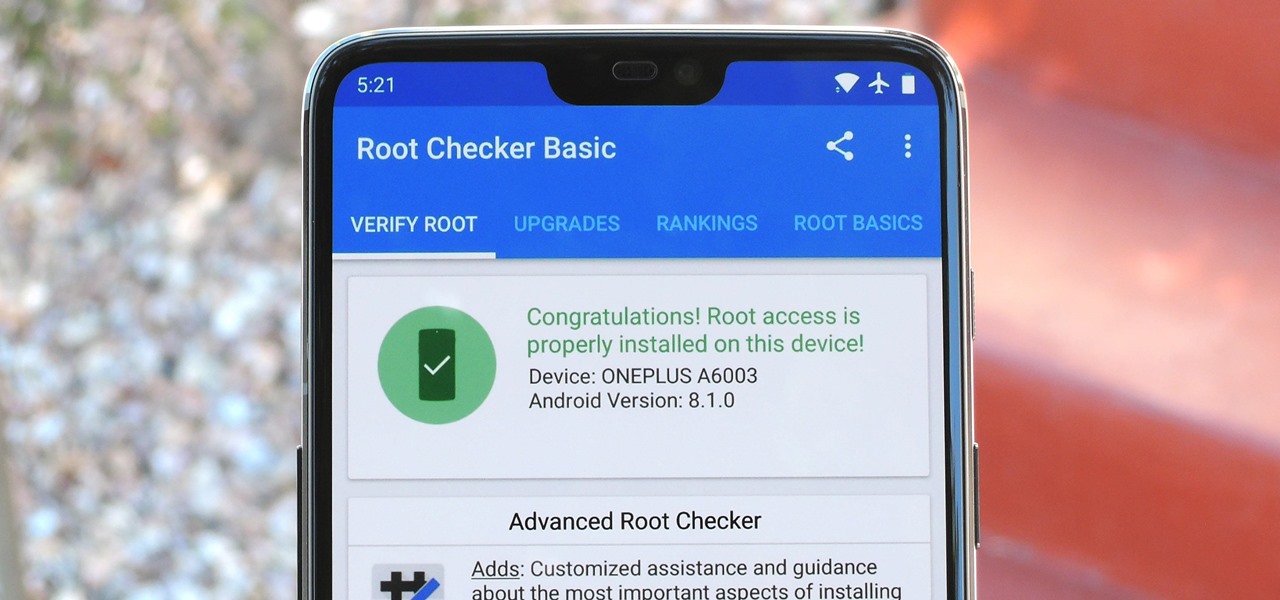
Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

We've all been hit by inopportune screen rotations at some point or another. Having the display orientation suddenly go from portrait to landscape when reading an interesting article in bed is one of the biggest irritations that come with using a smartphone (at least, for me). Thankfully, there are apps out there for your Android to help alleviate this inconvenience.
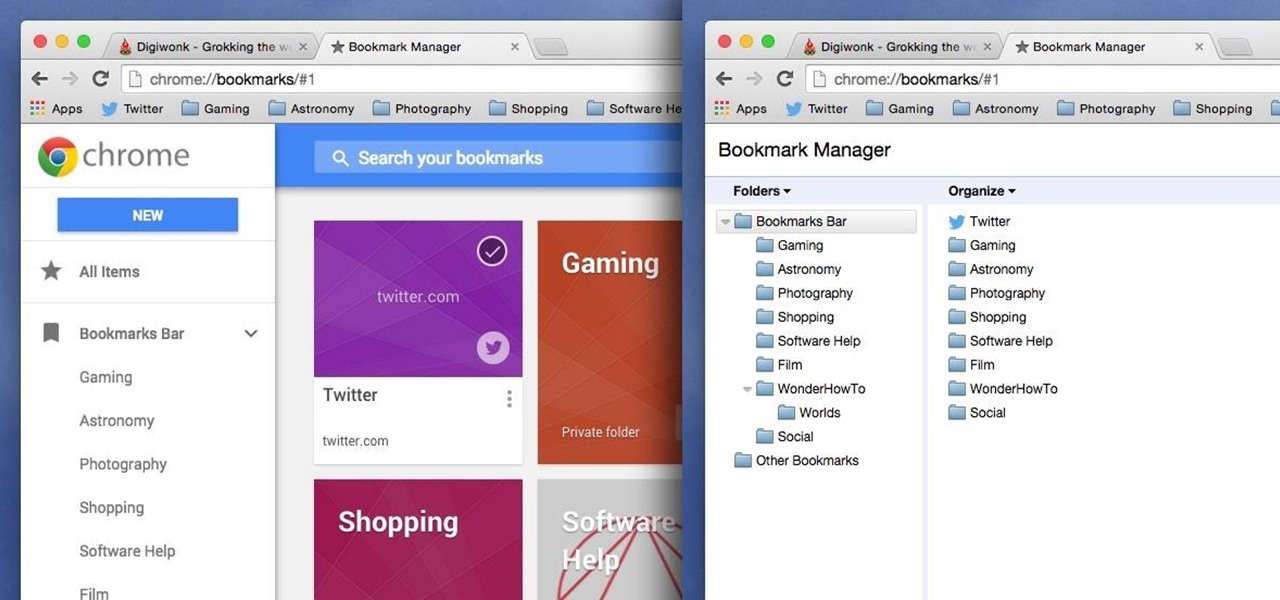
Chrome has been pushing out a lot of new changes lately, but not all of them are as good as they think they are. Earlier this year, there was an update that changed how user profiles worked, which made it harder to actually switch profiles. Luckily, there was a way to get back the old profile management interface, but now there's another "improvement" that you might want to change—Chrome's new Bookmarks Manager interface.

In this how-to video, you will learn how to change the password to your hotmail e-mail account. This will be useful if someone knows your password or it is not unique enough to be safe. First, go to your web browser and log in to your hotmail account. Once you are in, go to the options bar and click more options. Next, go to view and edit your personal information. Click on change next to your password. Enter your old password and then enter your new password twice. Click save to change the p...
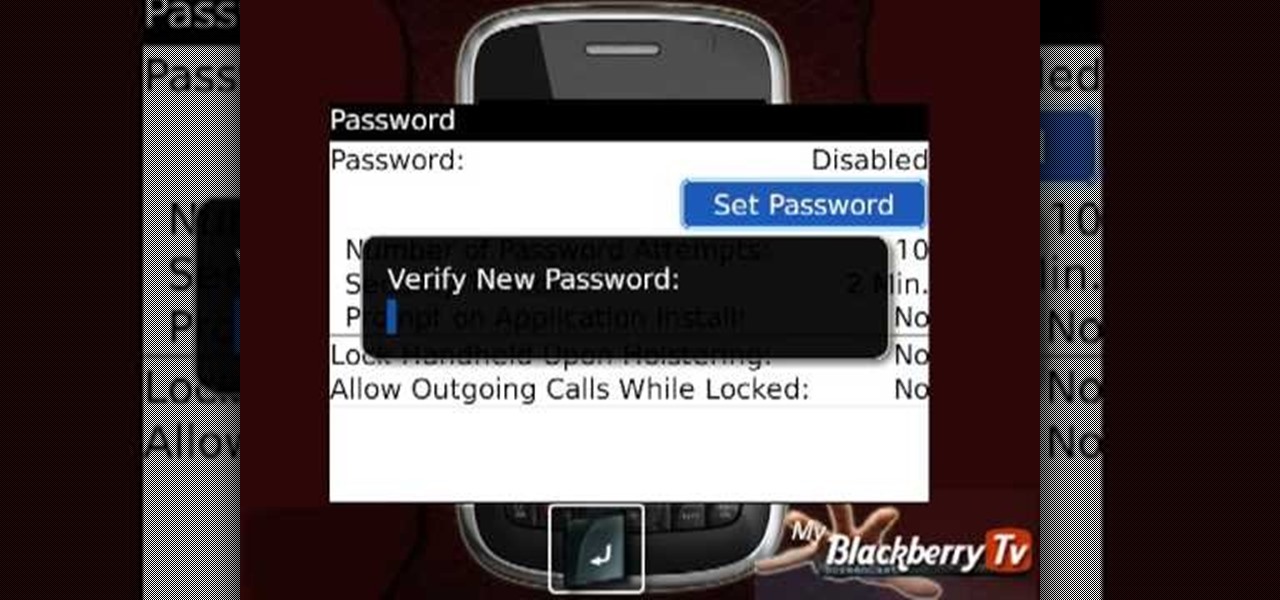
My Blackberry TV demonstrates how to protect your Blackberry device with a password. Protecting your Blackberry with a password will help to stop people from accessing your personal information on your device. From the home screen, press the Blackberry menu key. Then, select the options choice. Next, scroll down to the password choice on the options menu. Select password and then select the set password button on the password screen. Enter your desired password and then press the enter key. V...

Follow along as we are shown how to set a password for a new user in Windows 7. -First, go to the Start menu.
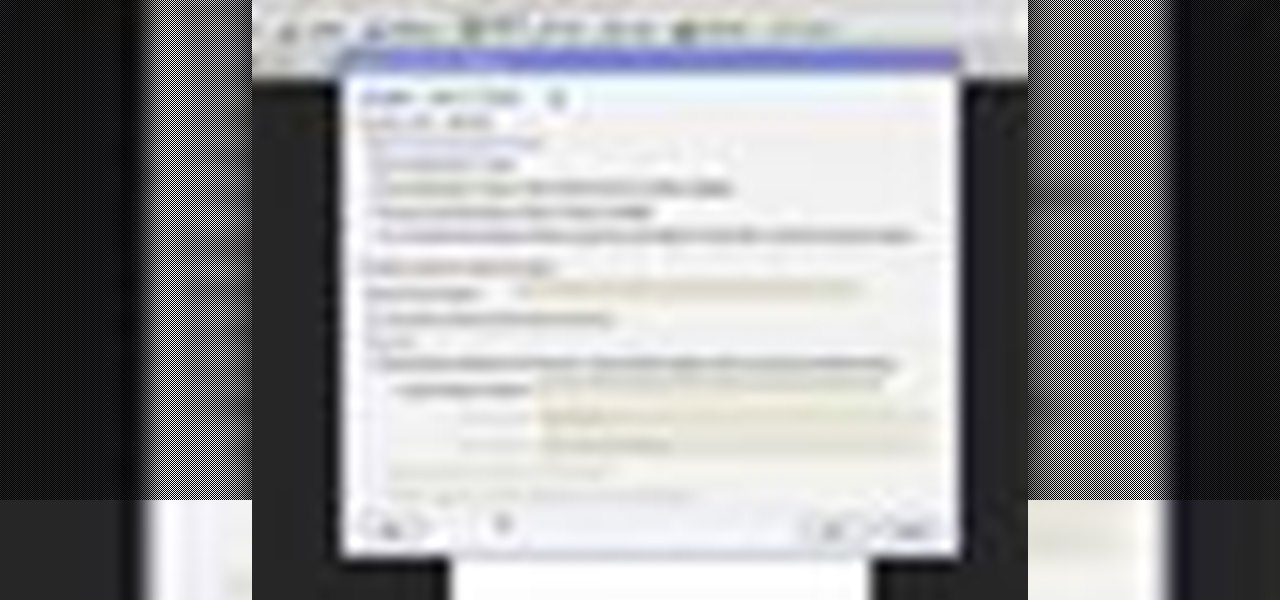
In order to secure a PDF with a password when opened in Adobe Acrobat 9 Pro, press the secure button and go into password security settings. Here you can change on what versions of this software the file will run on, the next option asks which portion of the document is to be encrypted when a password is placed. Further below here is where you actually choose the password, this ensures that only people who know the password will be able to see the contents of the document. Below this is the d...
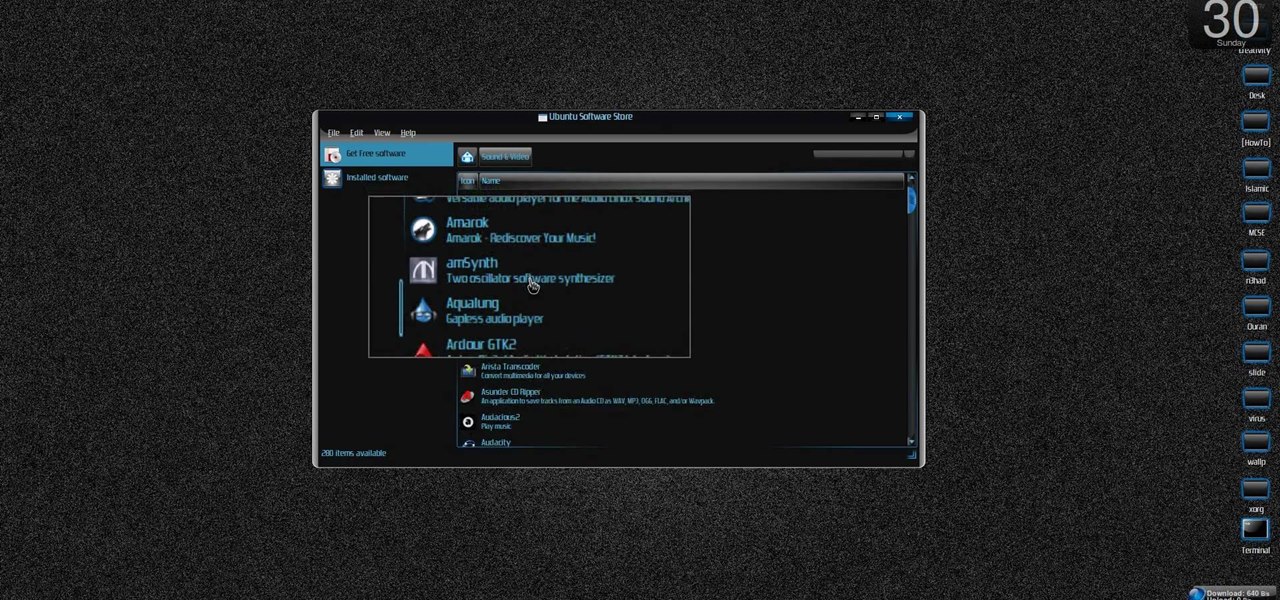
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install the Ubuntu Software Store on Ubuntu Linux.

If you've forgotten the password to one or more of the Windows XP accounts on your computer, take heart: This video tutorial will show you how to bypass, and then change, a Windows XP start-up password. For a detailed run through of this simple Windows log-in hack, watch this video how-to.

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

While the Play Store has a plethora of apps available for finding lost Android phones, Google came out with its own web-based application, Google Device Manager, earlier this year to help you keep track of all your Android devices and remote lock, erase, ring, and track if need be.

Having a secure password is essential in today's interconnected world. Hackers are just around the corner, and if you have an easy to guess or hack password that you use for all of your accounts, someone can login to all of your websites very easily. Look at this guide on how to create a strong password by following the right password rules so that your accounts stay secure.

In this video, we learn how to use secure online passwords. There are a ton of things to consider when creating a password. A weak password is something that someone can easily guess. If you are using a birthday, common dictionary word, child's name, or something common then you are at risk. Your password should combine letters and numbers, and be at least eight characters long. It should also be completely random and have upper and lower case letters. You can use a password assistant if you ...