The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Hello friends. This is actually my first how to.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

With iTunes, you can listen to the radio over the internet and hear broadcasts from around the world. Make sure your computer is connected through the internet, then click "Radio" in the source list to see the internet radio stations available through iTunes.

This tutorial demonstrates how to use Microsoft Internet Explorer and Mozilla Firefox. Learn more about web browsers in this free instructional video series.

Firewall solutions for macOS aren't impervious to attacks. By taking advantage of web browser dependencies already whitelisted by the firewall, an attacker can exfiltrate data or remotely control a MacBook, iMac, Mac mini, or another computer running macOS (previously known as Mac OS X).

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

With the rise of website encryption (TLS), sniffing passwords from network activity has become difficult. However, it's still possible to quietly exfiltrate a target's network traffic in real time to extract passwords and sensitive information. Pertaining to macOS, there are two methods for retrieving traffic from a backdoored Mac.

Alright, let's dig into this and get the simple stuff out of the way. We have a journey ahead of us. A rather long journey at that. We will learn topics ranging from creating object filtering systems to help us tell when a new object has come into a scene to building and texturing objects from code.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

In the wake of its 20th anniversary, the folks over at Eltechs have released Original DOOM, a full shareware version of the revolutionary first-person shooter DOOM for Android, available for free on the Google Play Store. It's unmodded and unaltered from the original FPS classic.

Hello fellow peoples of the earth and welcome to another tutorial by me! Noah! you know popcap make bejewled blitz and zuma and pvz for facebook but what if you want the big games like pvz or bejewled 3 from them but don't want to pay. Then worry not as this simple tutorial will help you get those games you enjoy for free without any trials or limitations! to the startthetutorialmobile

In this video, we learn how to automatically clear browser cache in Internet Explorer. This will help your internet run faster and it will also help protect your computer from your personal information being store. First, open up Internet Explorer, then click on the tools drop down menu and go to internet options. From here, go to temporary internet files and click on the button that says "automatically", then adjust the disk space to use to what you prefer. After you have changed the setting...

The iPod kids shows viewers how to covert movie files that are already on your computer into a format that will work with your iPhone or iPod Touch (2nd generation).

There are many different applications and games on the Nintendo 3DS that can take advantage of an active internet connection over Wi-Fi such as Netflix or the eStore. Unfortunately, since the 3DS is a mobile device, you won't always have access to the internet. If you have a mobile hotspot on a smartphone or tablet, you can share the internet connection over wireless with the gaming handheld.

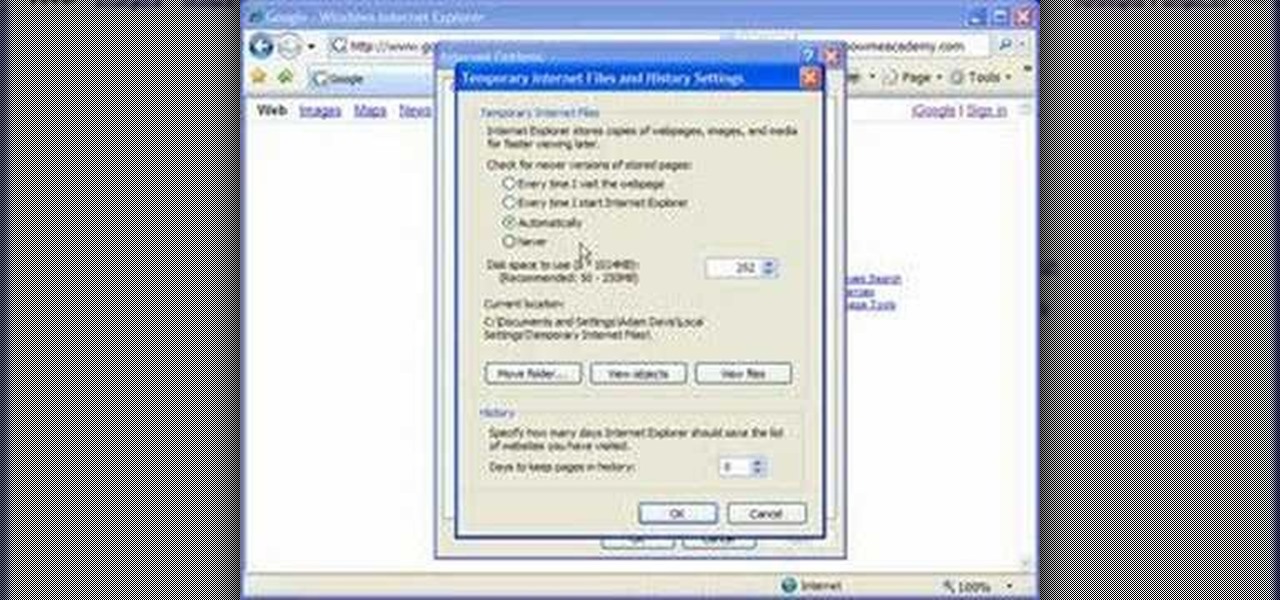
If your computer or web browser is running slowly, a good place to start clearing space is in your Temporary Internet Files. Temporary Internet files, as well as cookies, are collected every time you visit a site online. These files make it easier for your PC to remember your browsing history, and your log in information for various websites. However, sometimes all of these little files can add up into one big clog on your machine. If your computer isn't running up to par, follow along with t...

HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...

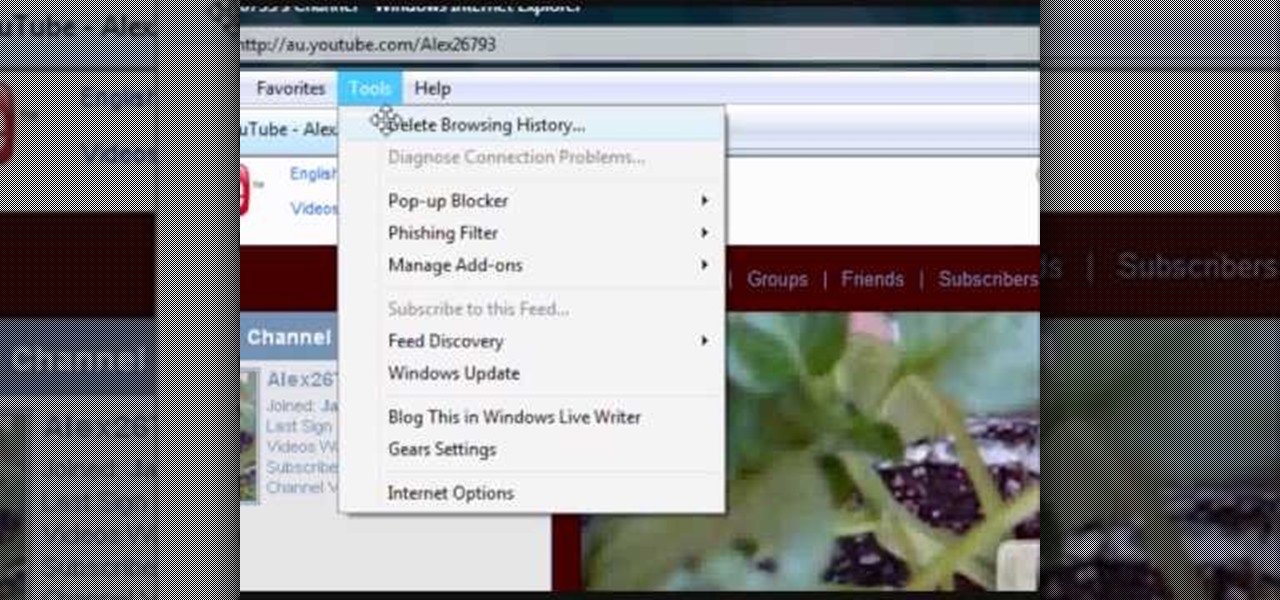
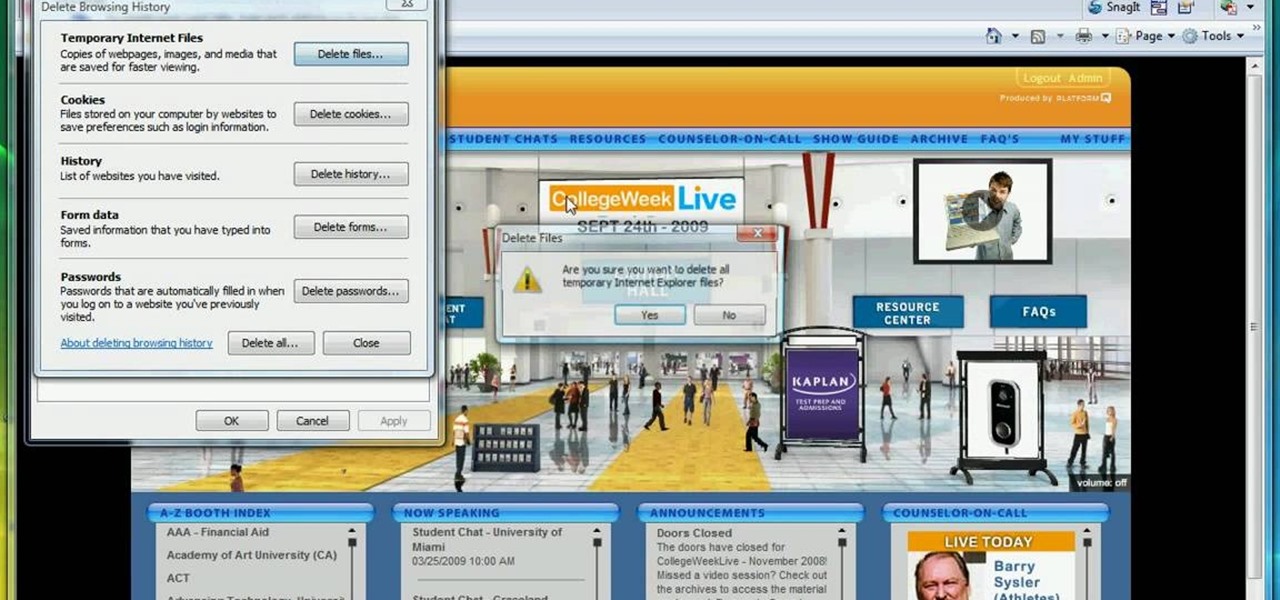
In this video, we learn how to remove our browsing history on Internet Explorer. First, click on "tools", then click on "delete browsing history". If you want to delete all of your browsing history, then click on that option. Most people are content with only deleting temporary internet files as well as browsing history. Getting rid of these will speed up your internet a bit. Another way is to go into "internet options", click under the "general" tab and choose which files you'd like to delet...

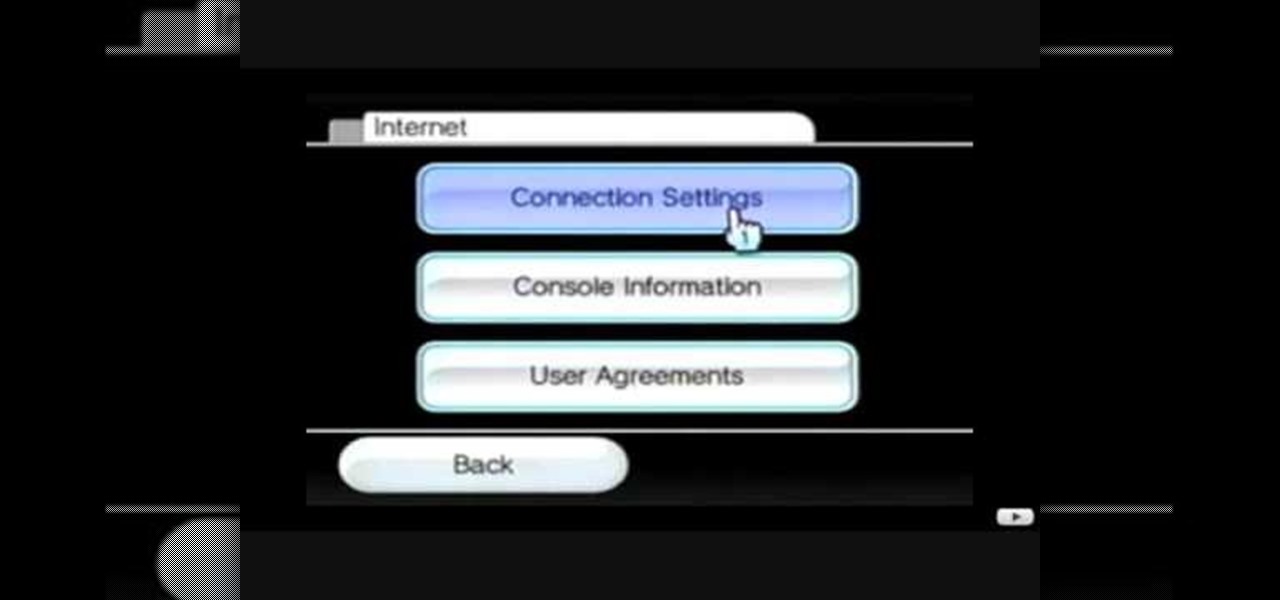
This video tutorial shows how to connect to the Internet using the Wii video game system. The advantage of connecting to the Internet with your gaming system is to play games, such as Animal Crossing or Call of Duty, with other players. You can also get the Internet Channel which allows you to watch YouTube videos and do other tasks you would normally do on the internet. You will need a wireless router to do this. On the Wii home menu, click on Options, Wii Settings, and scroll once to the ri...

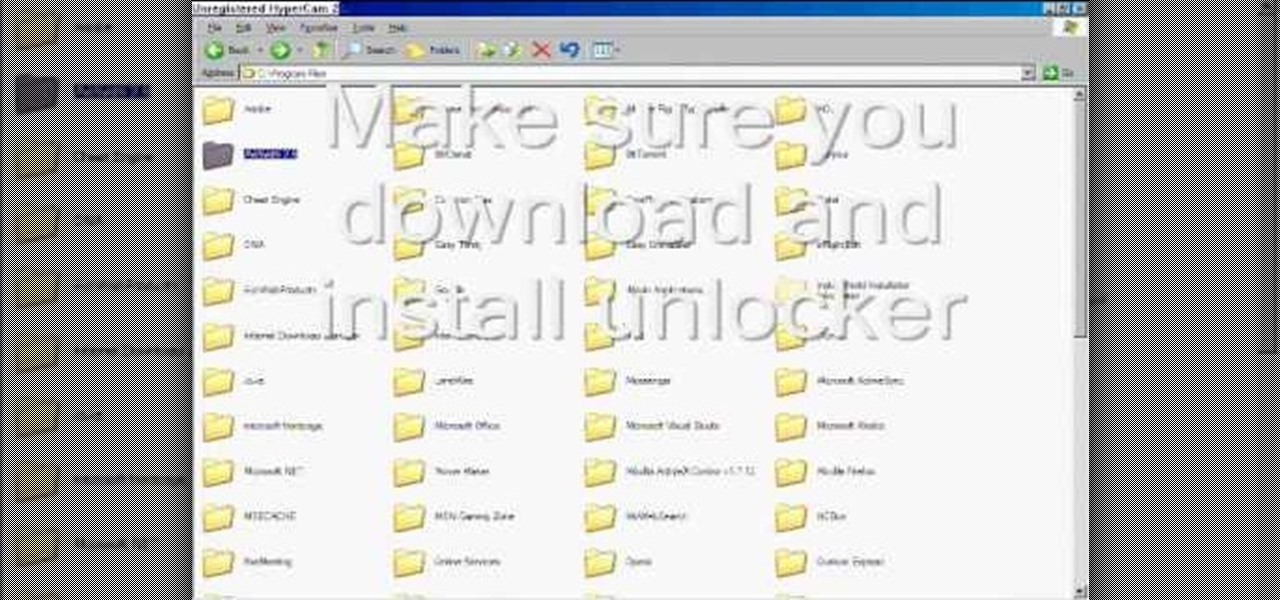
To delete Internet Explorer 7 or 8 from you computer, search for "unlocker" in the Google search engine. Click on the first search result to go to the unlocker site. Click download to access the unlocker application. Click the save me option when prompted. Next, find the downloaded files and install the unlocker application on your computer. Go to the local disk C, open the program files and find Internet Explorer. Right click on Internet Explorer and then click on the unlocker. Select the ap...

This video is a step by step guide to clear cache for Internet Explorer version 7.0. On your Internet Explorer browser version 7.0, go to tools. Click Internet options. Go to general tab, then click browsing history and hit delete. Window will pop up. Click delete on temporary files and click yes to confirm. Click delete on cookies and click yes to confirm. Click delete on history and click yes to confirm. Click x to close the window and the current Internet Explorer window. Pull up a new Int...

Not sure how to plan a funeral? A well-planned memorial service honors the deceased and comforts those who are grieving. Learn what steps to take when planning a funeral in this how-to video.

Are you a young aspiring actress? A triple threat? Many top singers and entertainers today got their start on the Disney Channel. In this video, learn how to get that audition with the Disney Channel... Who knows, it could be your big break!

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

Hello, everyone! If you haven't read the recent announcement on the official release of the Null Byte suite, I suggest you do so. This is going to be a quick tutorial on how to download and install the suite so you can see our communities genius. So, let's get started!

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

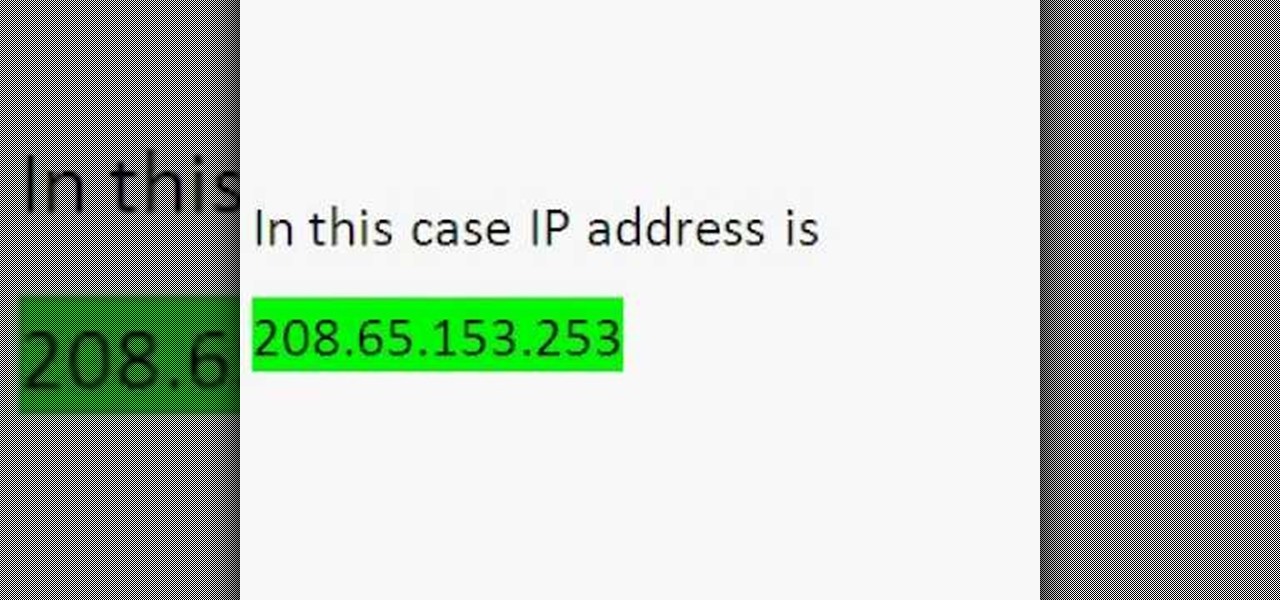
Wondering how to find the Internet Protocol address of a website?

Need internet but don't want to pay? Well, try lusting of those around you by picking up their Wi-Fi signal. Live out in the boondocks? No problem… if you have an old satellite dish laying around.

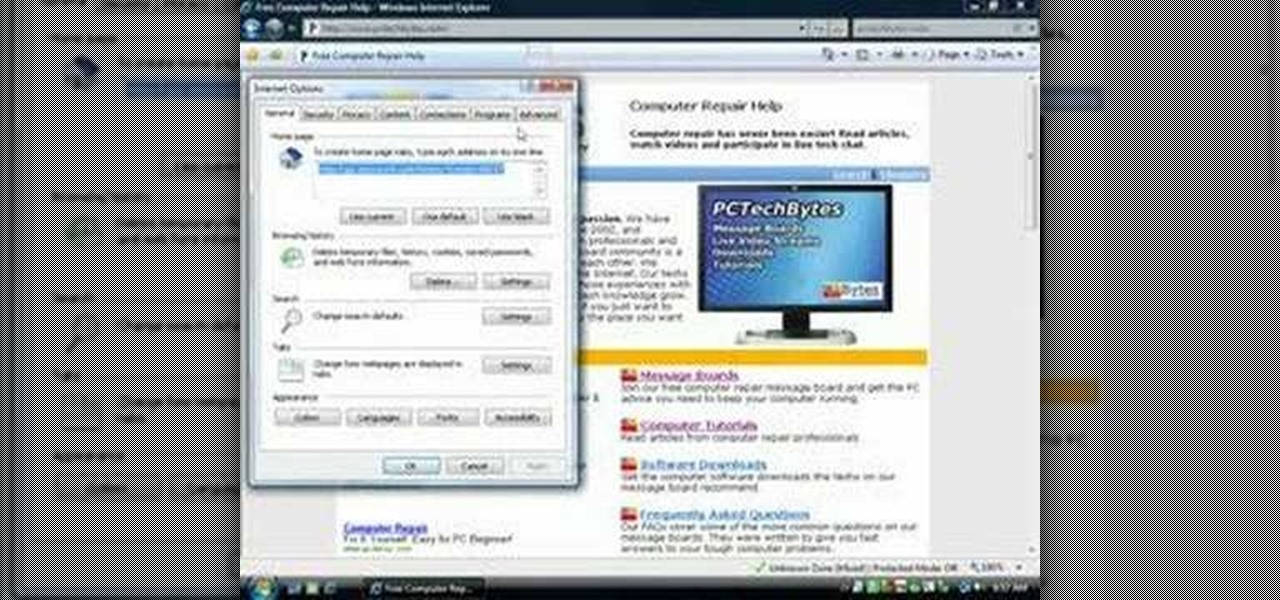
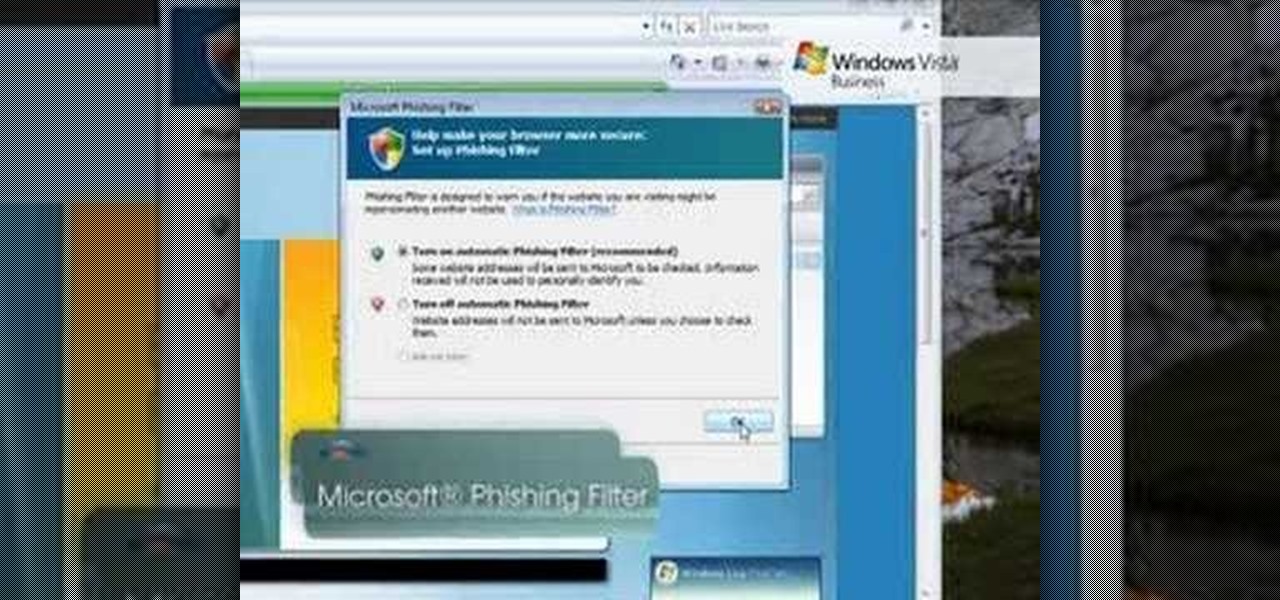
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

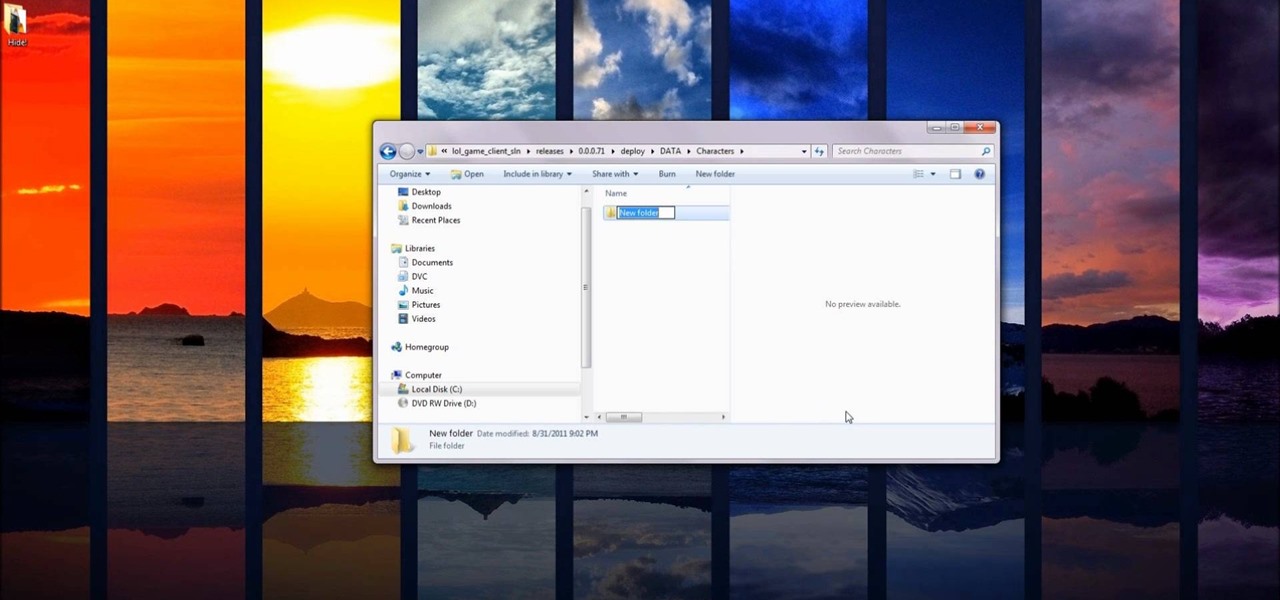
If you're interested in changing the recommended items presented to you each time you open the shop in League of Legends, check out this guide. You will need to have access to your Riot Games and League of Legends directories first.

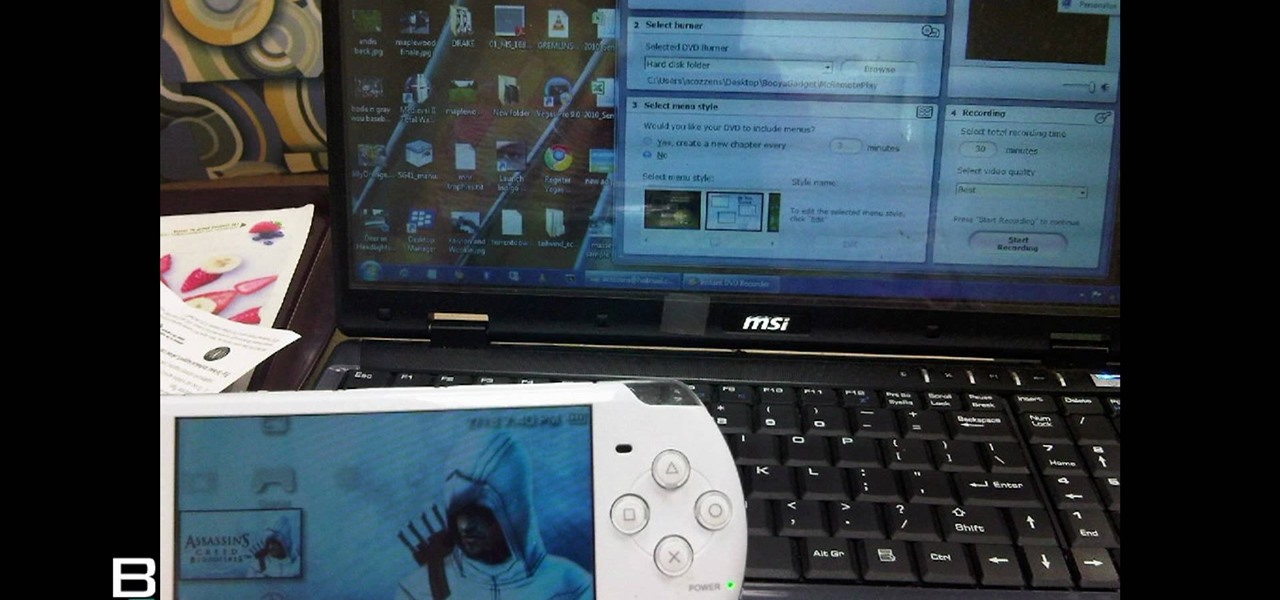
Play remotely with all your friends, stream videos and music from the Internet or even check your Facebook and email - all with your PSP. The PSP has Internet capability, but not every network will be available to you at all times. Here is how you can hack any wifi connection with your PSP.