With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Welcome back, my nascent hackers!

You can create an image gallery of any directory on your file system with Konqueror. If you are a KDE user and you need to see the images in any directory, but if there are any other stuffs beside images in that directory then you will see that stuffs too. So if you do not want this, you need to click on tools in Konqueror menu and choose "create image gallery" for the current directory. There will be many options like folder, look etc. so set your options as you like and click on create, it ...
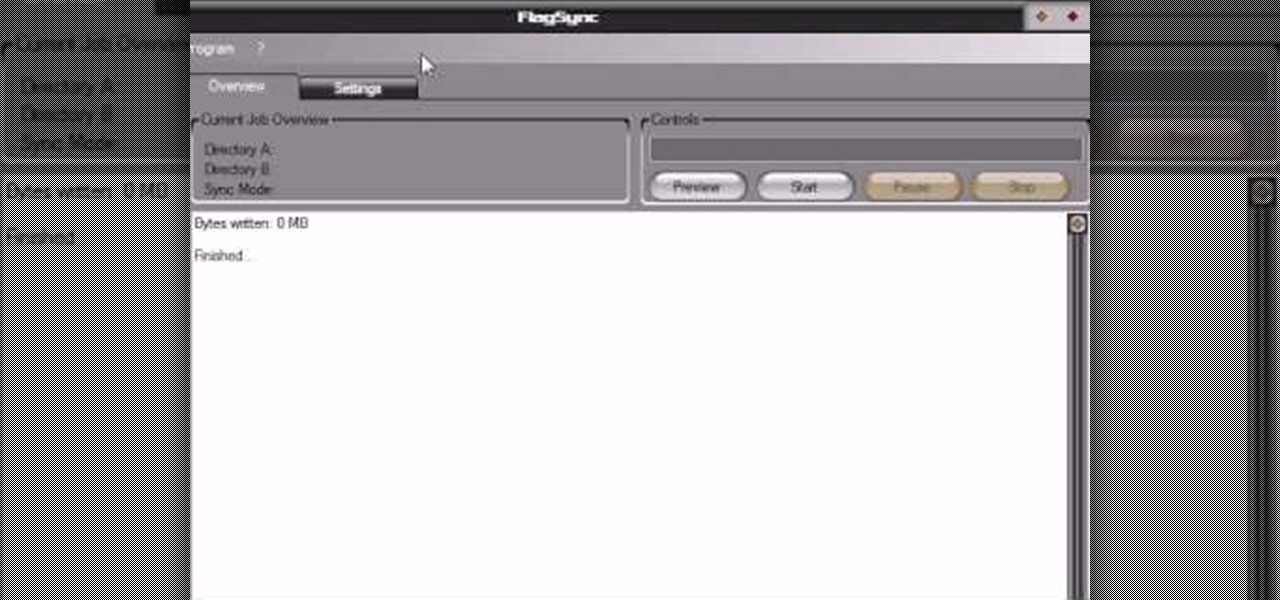
Video demonstrates how to synchronize two folders on windows without doing much of copy pasting and does the job easily. This is a free wear, “FlagSync”.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.
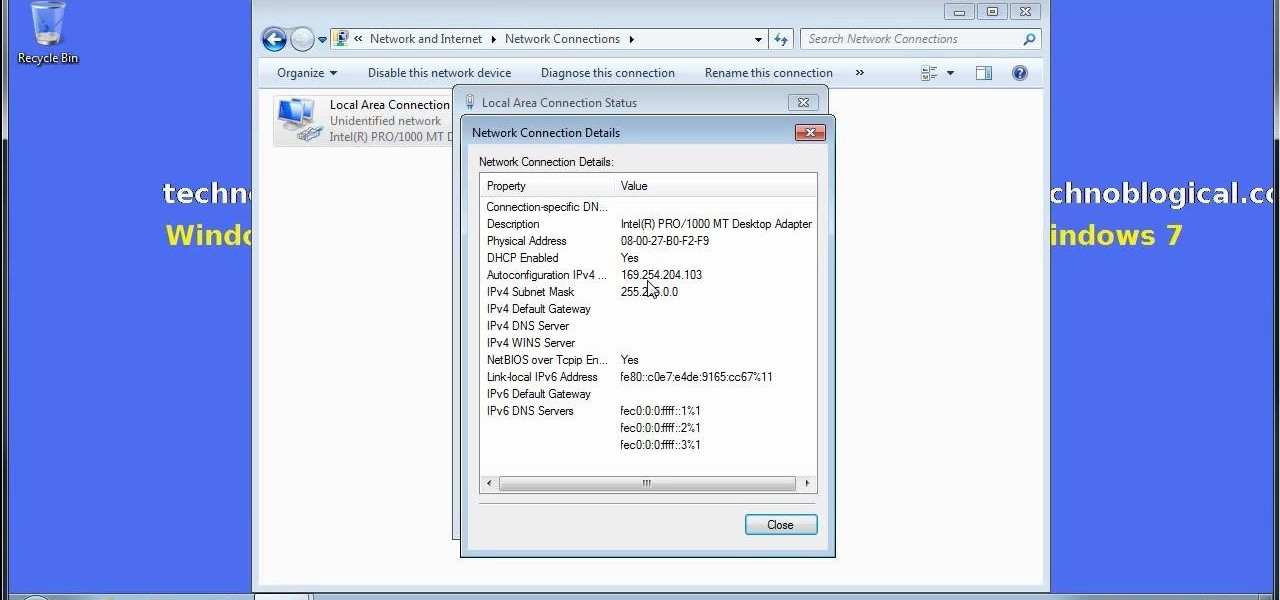
Want to share Internet connectivity between two computers without a wireless network but have an extra CAT5 ethernet cable? You're in luck. This home networking how-to will show you what to do to get your machines talking not only to one another but the web at large.

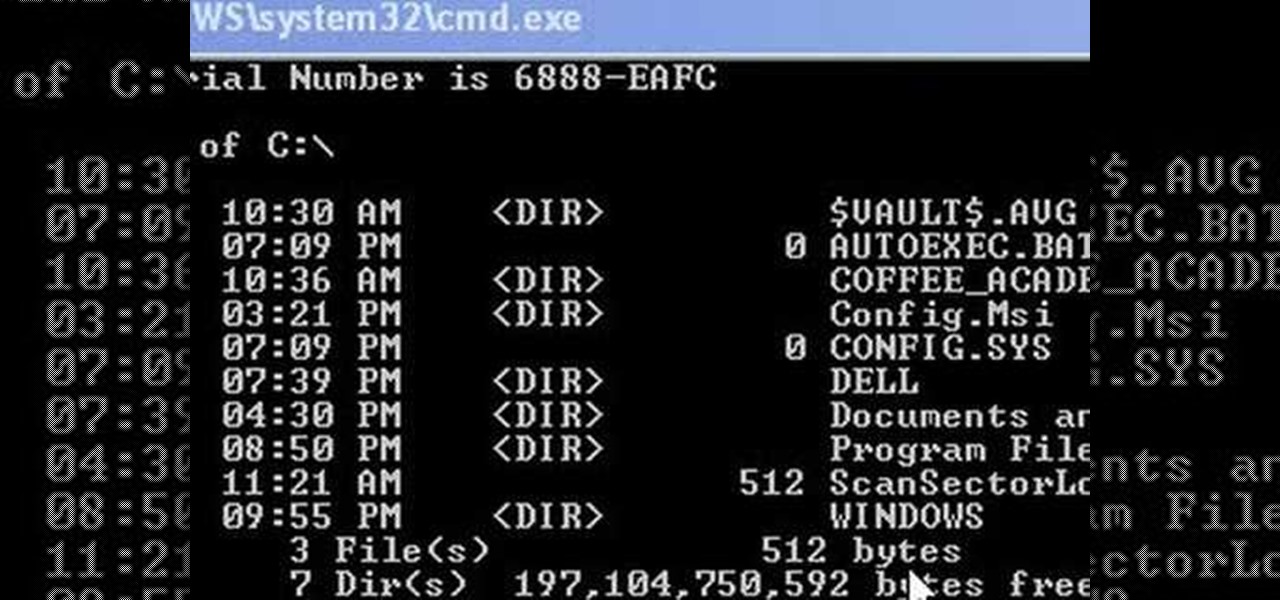
This video shows us how to change driving letters or directories in DOS command. Firstly go to start menu and then click on run. Then type cmd and press OK with which a DOS command cmd window will pop up. Now you need to change the directory and these is done by typing ‘cd..’ and after that press enter. Now you have changed the directory and now you need to see what’s in there and for that type ‘dir’ and press enter and this shows what’s in that directory. Now change to other directory by typ...

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

In this video tutorial, viewers learn how to quickly copy a folder's content list in Windows. Begin by clicking on the Start menu and open the Run program. Then type in "cmd" to open the Command Prompt window. Now navigate the desired folder and type "dir | clip" beside it. Press Enter and it will automatically copy the directory to the clipboard. Essentially, it is a tool that will the command prompt command to the clipboard. This video will benefit those viewers who use a Windows computer, ...

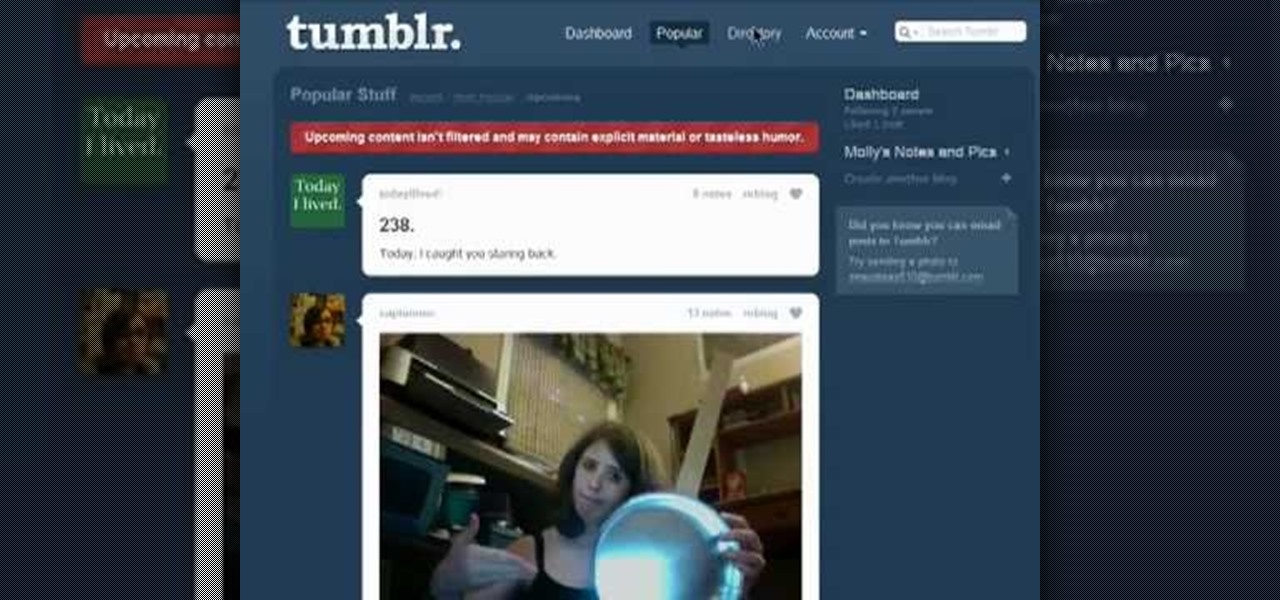
Eager to find new and interesting Tumbleblogs to follow? With the Tumblr directory, it's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started browsing the Tumblr directory yourself, take a look.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

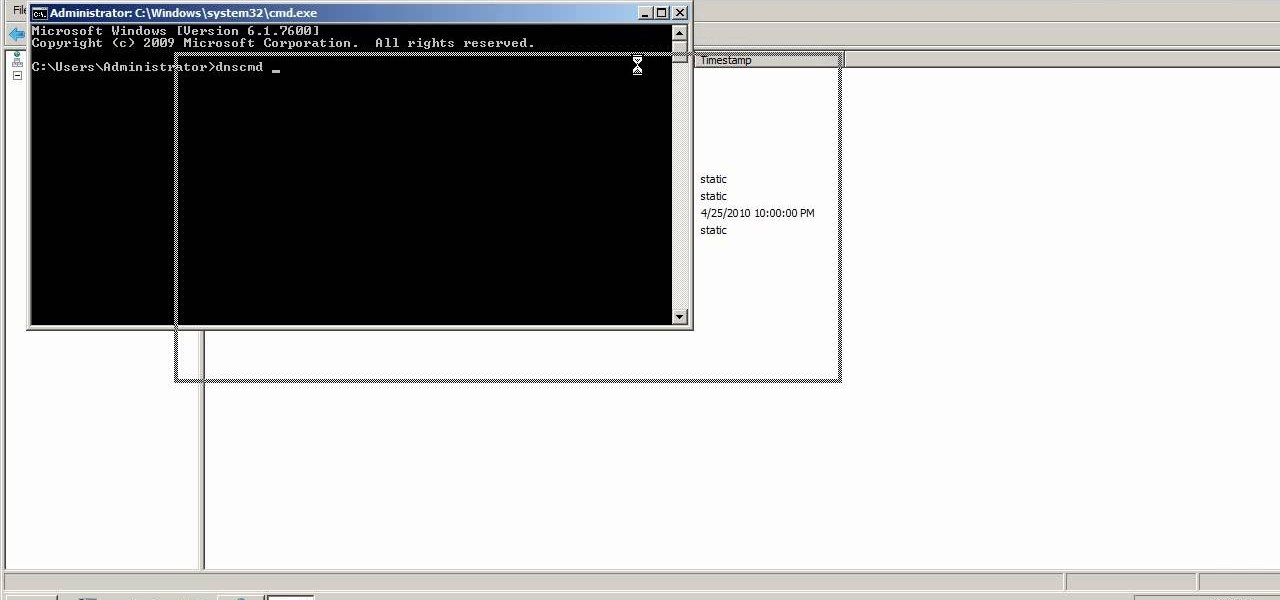
A custom application directory partition is a method of dividing your DNS servers for replication, and allows replication to occur between domain controllers. This video shows you the process of setting up your own using Windows Server 2008, though it will also work for the 2003 version as well.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional brushes for GIMP on Ubuntu Linux.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the local files on your server. Look in the root directory of your server and right click, then choose "create directory". Now, click on the plus sign to see a blog sub directory. Next, find where you downloaded Wordpress onto...

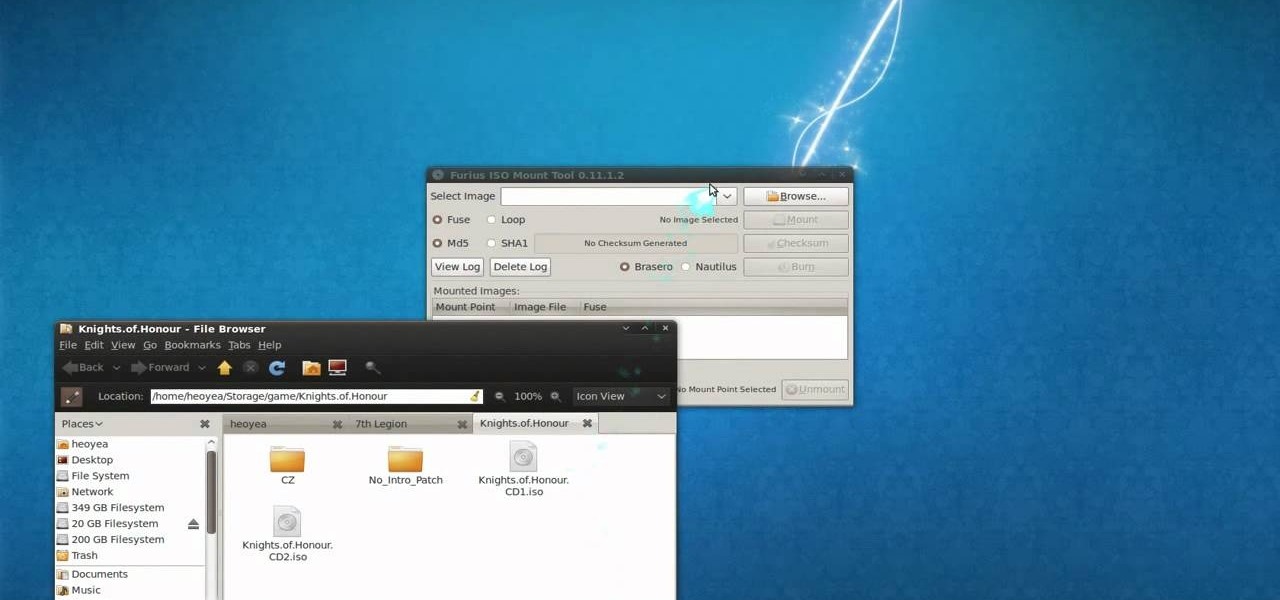
This is a tutorial video on how to use a virtual CD/DVD drive software tool called Furius ISO Mount. Furius ISO Mount is an .ISO, .IMG, .BIN, .MDF, and .NRG image management utility, that allows you to automatically mount and unmount disk image files. This utility application will allow you to mount multiple images at once, burn image files to optical disk, and create MD5 and SHA1 checksums to verify the that the image files are not corrupted. This program also automatically creates mount poi...
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my tenderfoot hackers! As you know, DNS, or Domain Name System, is critical to the operation of the Internet. It provides us with the ability to type in domain names such as www.wonderhowto.com rather than the IP address. This simple service saves us from having to memorize thousands of our favorite website IP addresses. Instead, we simply type in a domain name to retrieve the website.

In this web TV presentation the host is talking about Grub 2. In Grub 2 you can mount an ISO file like a device with the loop back function. In Grub 1 you can use tack tack mem to mount iso files if the files are not fragmented by using the map command. Grub 2 is an application available for download that will be available after download as a chain from Grub 1 to Grub 2 to your operating system. Grub is a program that compresses all of your favorite boot programs into one.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

In this video, we learn how to download torrents on the iPhone 2.0 or 2.1. Before you do this, you will need: Cydia, Mobile Terminal, C Torrent, Safari Download Plug-in, and Mobile Finder. to start, you will first go to a torrent site and find the torrent that you want to download. Then, click on the download torrent button. From here, you will see a warning appear on the screen. Choose to download this and then go to your Mobile Finder. Find where you saved the torrent to. Then, hit the home...

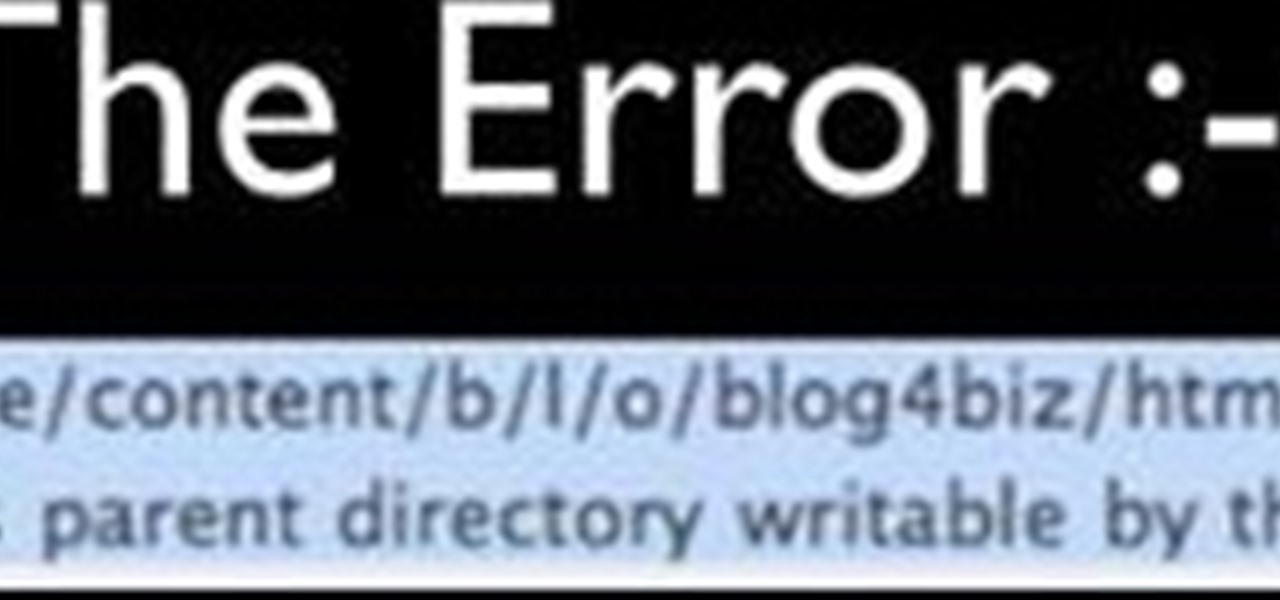
Faced with an "Unable to create directory" error when attempting to upload an image to WordPress? This clip offers instructions on how to fix it. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about its features through videos like this one. Take a look.

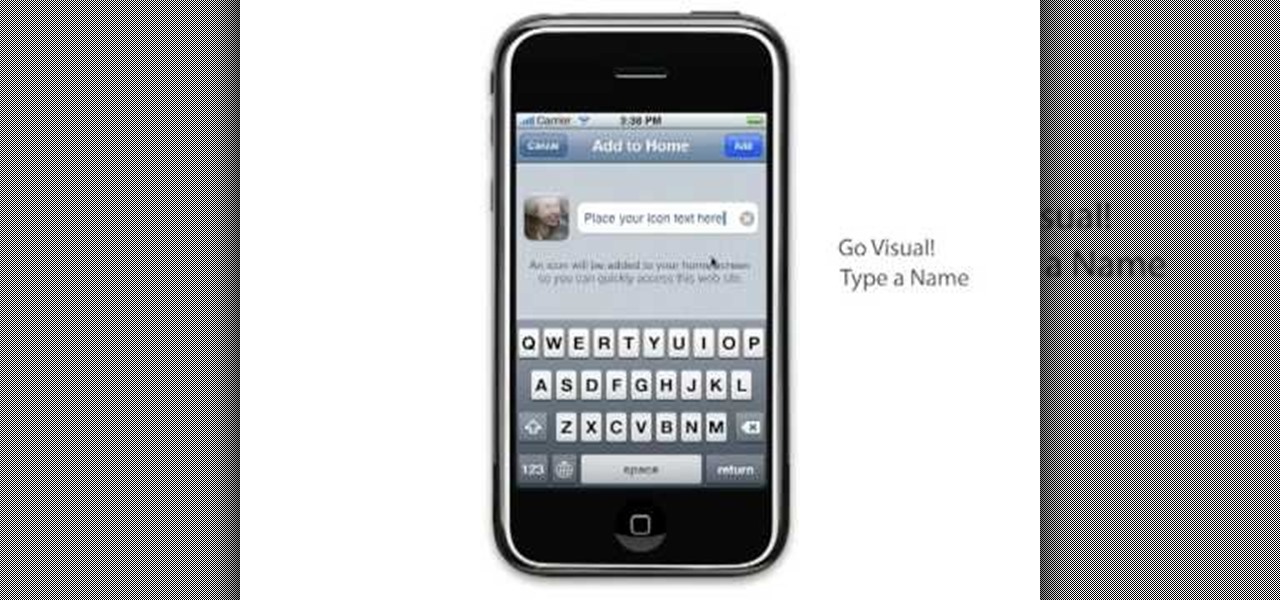
Learn to setup a visual dial icon on your iphone. This one click application allows you to call anyone in your directory by clicking on a photo of them on your phones desktop.

Flickr is the most known and dependable photo sharing website to date, so if you haven't made an account yet, you better now, if you want to share your precious photos with family, friends, and even the whole world! Flickr allows you to store digital photographs online and share them with other people.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Hello, *Note This is my first how to post on here, so please correct anything that I have missed and let me know if anything I explained is unclear and I will try to clearify. Also I am a NOOB when it comes to this art, so I might have missed something, if so please inform me so I can better myself*

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

When attempting to run a script, it can be rather inconvenient to have to locate the script, and run it time and time again. What if there were a way to run a script from anywhere. Well that's what we'll be doing today. This can be useful for any scripts you use frequently, it can save you time by removing the need to locate and execute.