Greetings to all geeks, hackers, nerds, and explorers of Null Byte. Welcome to my brand new tutorial, "Using BASH for Computer Forensics". This tutorial will give you a look at how the computer programming language, Bash, can be used to find out details on apple devices for later use.

The iPod kids shows viewers how to covert movie files that are already on your computer into a format that will work with your iPhone or iPod Touch (2nd generation).

Beauty schools Directory presents how to cut and take weight out of long hair. Video also demonstrates two style options to hair. In the video we have Jenny with long hair whose hair is being cut.

It's important to know who you're dealing with after hacking your target's MacBook. Getting remote access is simple, but covertly gathering information about the user and their system can be a challenge.

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my newbie hackers! Recently, I "upgraded" to Kali as my hacking platform, despite my preference for BackTrack. I did this reluctantly, primarily because new readers here could no longer download BackTrack from their site. I want to point out here that we all must keep in mind that with any software—or for that matter, any product—that is newer is not necessarily better.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Trying to find your friend's Yahoo! mail address so you can send them a letter or tell them about a cool new website you found? Yahoo! directory makes it easy to find someone you're looking for. All you need is is their name.

Interested in using the Active Directory Administrative Center on a machine running Windows Server 2008 R2? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over three minutes. For more information, including complete, step-by-step instructions, watch this sys admin's guide.

Interested in installing Active Directory Domain Services (ADDS) on a machine running Windows Server 2008 R2? This clip will show you how it's done. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over five minutes. For more information, including complete, step-by-step instructions, take a look.

Dr. Preis has received Top Doctors recognition in the last 10 years of Castle Connelly's Directory. This video is perfect for parents and gives advice on recognizing if lack of eye contact may be a sign of Autism.

Oded Preis MD FAAP Associate Clinical Professor of Pediatrics SUNY Downstate Brooklyn Dr. Preis has received Top Doctors recognition in the last 10 years of Castle Connelly's Directory. In this DrMDK video, he discusses what bonding is and how to bond in birthing centers.

The free download manager wget lets you download all the files on a page or directory with a single command. It also allows you to resume downloads after getting disconnected letting you start where you left off instead of starting the download at 0% again. Check out this tutorial and see how to install and use wget.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

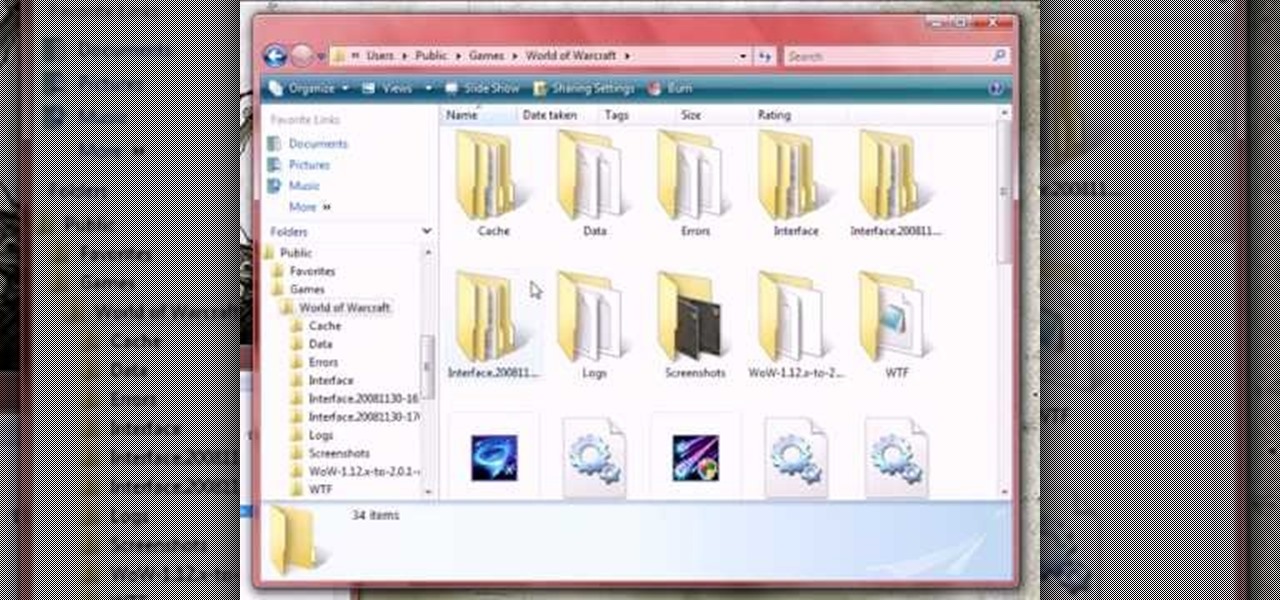
In this tutorial, we learn how to clear your World of Warcraft cache. First, you will go to your computer, then the local disk (C:), then users. From here, go to the public folder, then click on 'games', and then 'Word of Warcraft'. Once here, you will need to delete the 'cache' and 'wtf' folders. Next, you can exit out of this and continue to play your game as normal. This will clear out history from your game and make it load faster than before. If you aren't a Vista user, you will be able ...

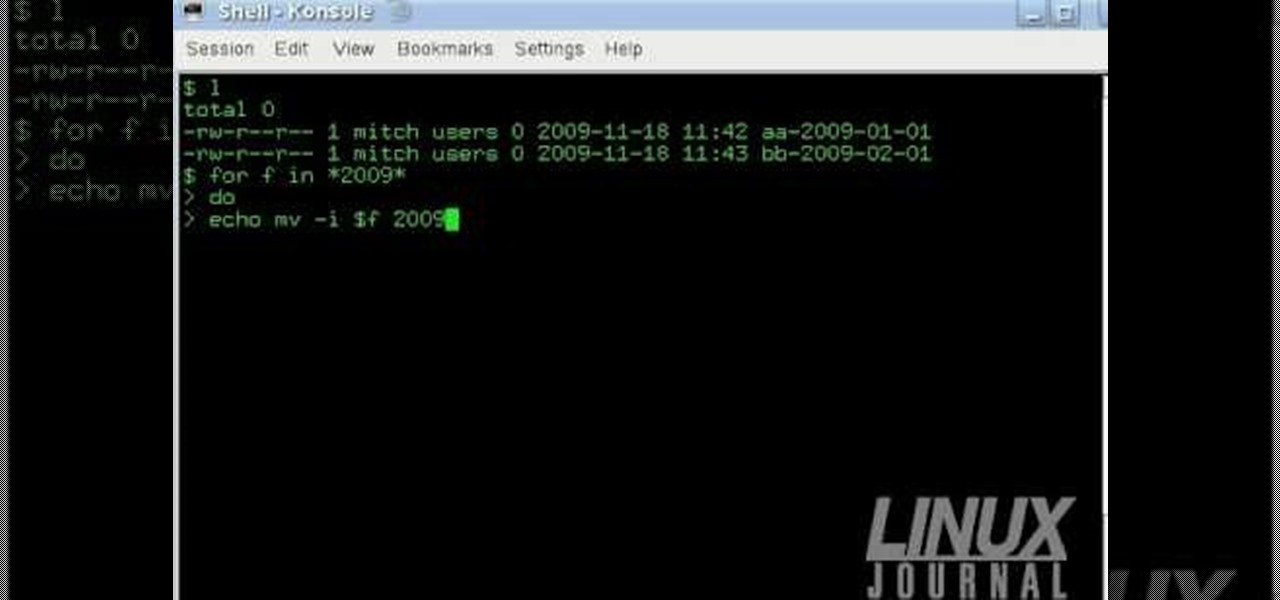
The Linux command shell provides a very powerful interface for doing various system tasks. This video explains with an example, how to use a bit of programming techniques to batch rename files with similar naming conventions.

In order to build Google Chrome extensions, you will need to familiar with scripting and codes. These are small programs that add additional functions for programmers. It is a compressed directory. These files must have a particular name: i.e. "manifest" (manifest.json). An extension will have at least one of the following: browser actions, page actions, content scripts, and utility web files.

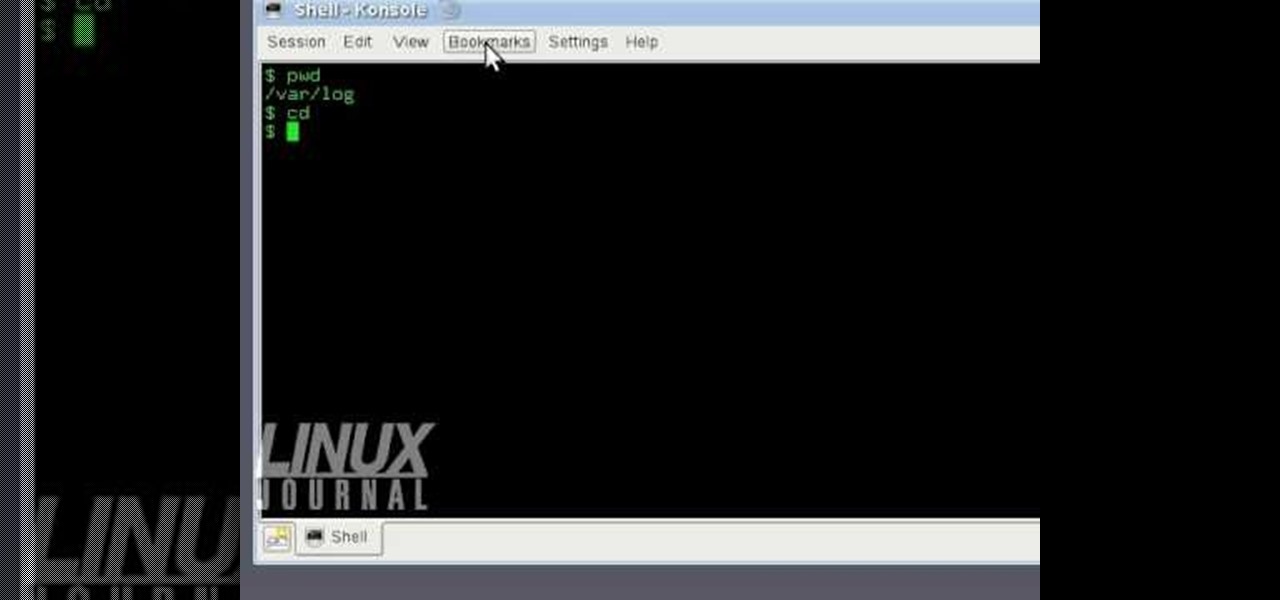
In this tutorial, we learn how to use KDE konsole bookmarks. You can add a bookmark, then go to the home directory and then you will be able to go back to where you previously were. To do this, save the bookmark of the entry that you are in. Do this by clicking the bookmark tab, then add bookmark. After this, go back to the home entry and then click on your bookmarks tab again. Once you click this, you will see your new bookmark on the bottom, when you click that it will bring you back to you...

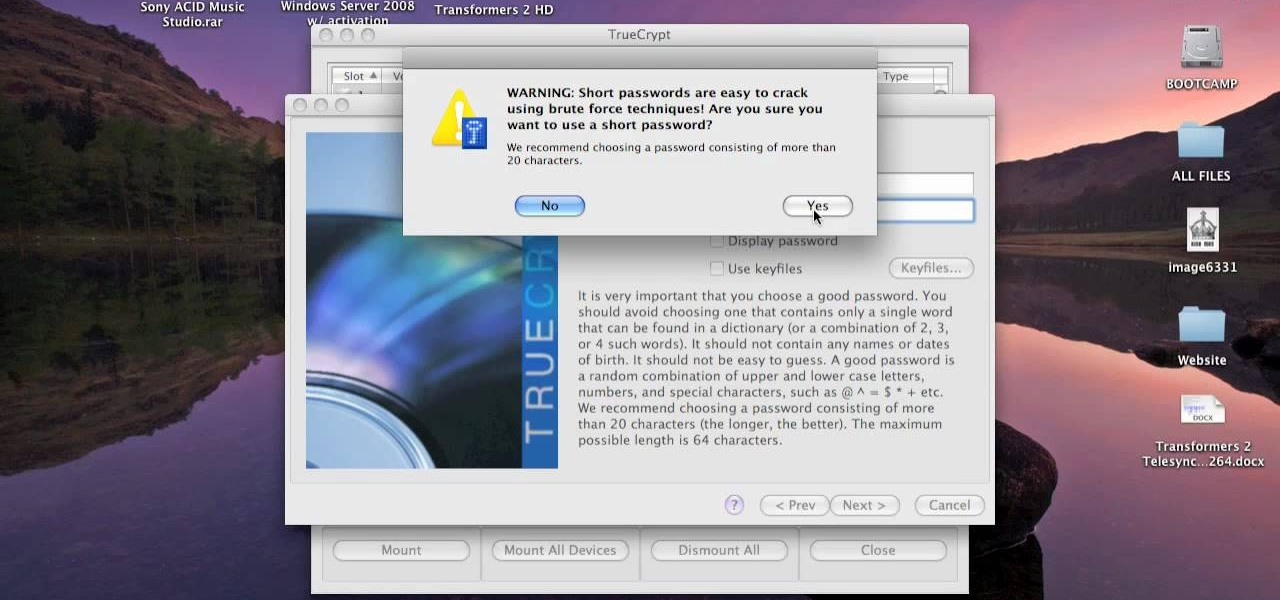
This video tutorial is in the Computers & Programming category where you will learn how to encrypt files & folders on a Mac with TrueCrypt. Open up TrueCrypt and click on create volume > create an encrypted file container > next > standard truecrypt volume > next. Here you name your file, choose the directory where you want to put the file and click 'save'. Choose the encryption type and click 'save'. Choose the volume size and click 'next'. Now type in a password and click 'next'. Then in th...

This video tutorial belongs to the software category which is going to show you how to set up a home server from behind a router using WAMP. You will need a free program called wampserver. Go to their website, download and install the program. Then click on the icon and click 'put online' and the local host comes online. To check it, open up your browser and type in local host in the search box and it will show you the default index.php file. Again click on the icon and click 'www directory'....

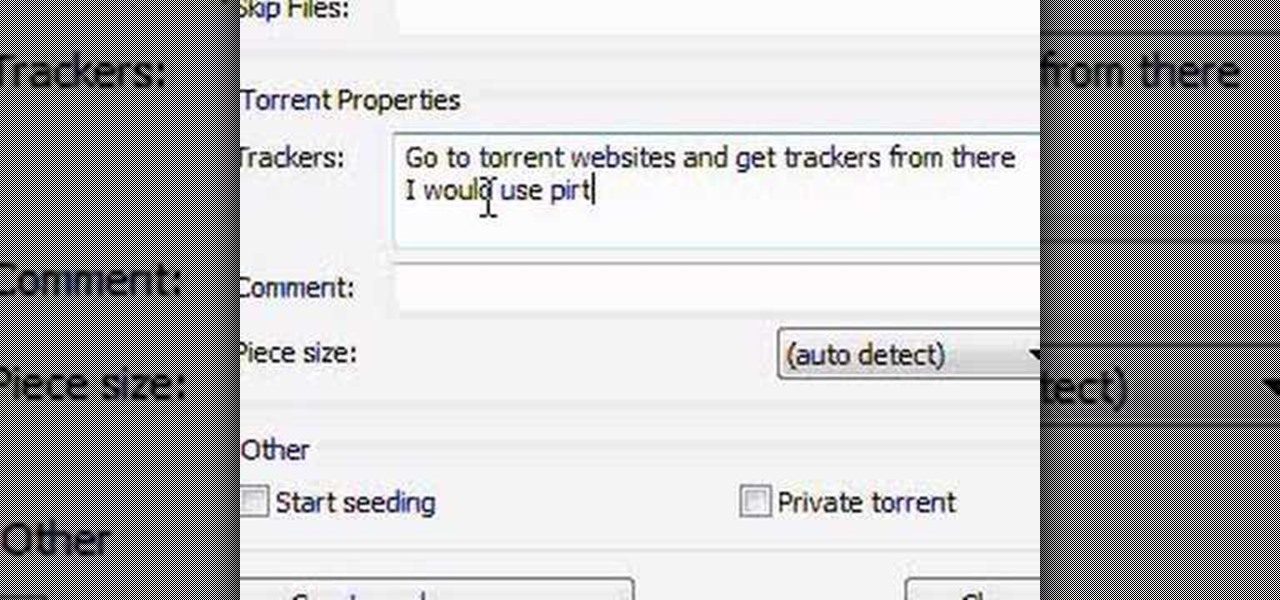
In this video tutorial, viewers learn how to create a .torrent file using u-Torrent. Begin by opening the program. Click on File and select Create New Torrent. Now select the file, select the directory and type in the tracker code. Then click on Create and save as. Once the file is created, click on File and select Add Torrent. Locate the .torrent file click OK. Now wait for the torrent file to finish downloading. This video will benefit those viewers who use u-Torrent and would like to learn...

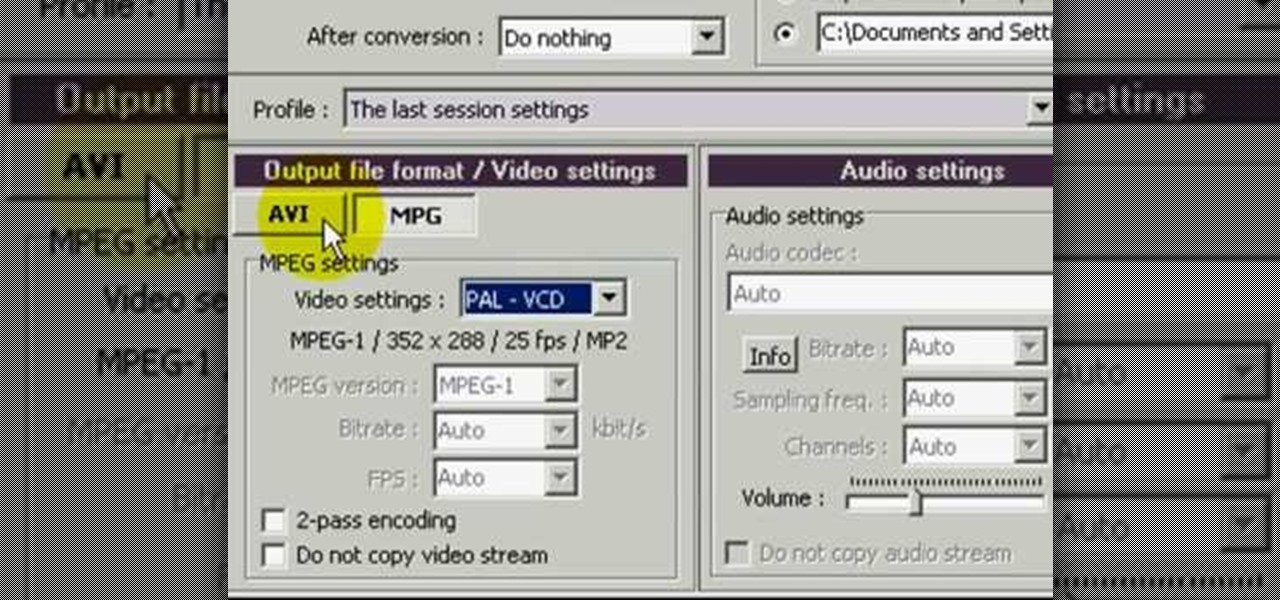
In this how to video, you will learn how to convert a flash video to an AVI file. First, download the Pazera Converter program. Open the program. At the left hand corner, click add files and find your flv file. Next, select and open it. Once it is imported, go to output directory and choose which folder you want the new file to be placed. Go to output file format and click AVI. You can also choose MPG instead if you want. Now click the convert button at the top. You will see a progress bar. O...

In this how-to video, you will learn how to see high quality pictures of your own house. First, go to your web browser and click on Maps and Directions in the directory on the MSN website. Next, click on locations and type the address of your house or whatever place you want to see. Once this is done, click on bird's eye to get a closer photo of the area. Next, click zoom in until you get an even larger image. You can also click on the picture and drag to move around the image. This video sho...

In this video, our author, atomicinteractive, shows use how to use Fetch FTP to upload a temporary webpage. Please make sure your directory has the html file. Please find your email with ftplogin information. This will also show login information for the control panel and creating alternate email addresses.

In this Computers & Programming video tutorial you will learn how to update a website with an FTP client (v† la FileZilla). Download FileZilla client from www.filezilla-project.org. Find your server IP address from your web host, which will be found in the hosting control center. In the video, it is GoDaddy.com. Open your filezilla client and put in the IP address of your web host and your username and password for your hosting account. Then click ‚Äòquickconnect‚Äô. This will connect you to ...

In this Computers & Programming video tutorial you are going to learn how to add "Hide" & "Unhide File" to the right click menu. Go to reg.exe and type in ‘regedit’ and click ‘enter’. On the page that opens up, Navigate to ‘HKEY_CLASSES_ROOT’ > directory > shell. Right click on shell and select new > key. In the ‘key’ box type ‘Hide Folder’. Now right click on the right side box of the page and select new > string value. Type in ‘HasLUAShield’ in to the box that opens up. Now on the left side...

Fetch is an FTP program for Macs (Smart FTP can be used if you don't have a Mac). These can be downloaded from Download.com

This video teaches the secrets of partitioning a hard drive on a MAC in simple steps. First open the disk utility, select the root directory of your hard drive and click partition. Now select the required partitions under the volume scheme, adjust the drive space and name them. Select the format a MAC OS Extended (Journaled) and select GUID Partition table from option if you want to boot it. Click 'Apply' to start the partitioning and when its done start using it.

This instructional video shows you how to reboot your iPod Touch 2G after shut down. First shut down the device and plug it to a computer via USB. Use the links in the description if you have the newest version of OS X. Put the device in to DFU mode by holding the home and power key for 10 seconds, letting go of the power key keep holding the home key. Download the RSlite folder from the link in the description. Open the terminal, change the directory to the Rslite folder and type the code re...

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

While hackers have taken advantage of numerous vulnerabilities in Adobe's products to deliver payloads to Windows users via PDF files, a malicious PDF file can also wreak havoc on a Mac that's using the default Preview app. So think twice before double-clicking a PDF open on your MacBook — it might just be a Trojan with a rootkit inside.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.