Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my budding hackers! I began this series on Linux basics because several of you have expressed befuddlement at working with BackTrack on Linux. As a hacker, there is no substitute for Linux skills.

Welcome back, my tenderfoot hackers! So many of you responded positively to my post about using the keylogger, as well as my post regarding turning on the webcam, that I decided that you might enjoy another similar hack. In this article, we will enable the audio recording capability on the remote system of your roommate.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

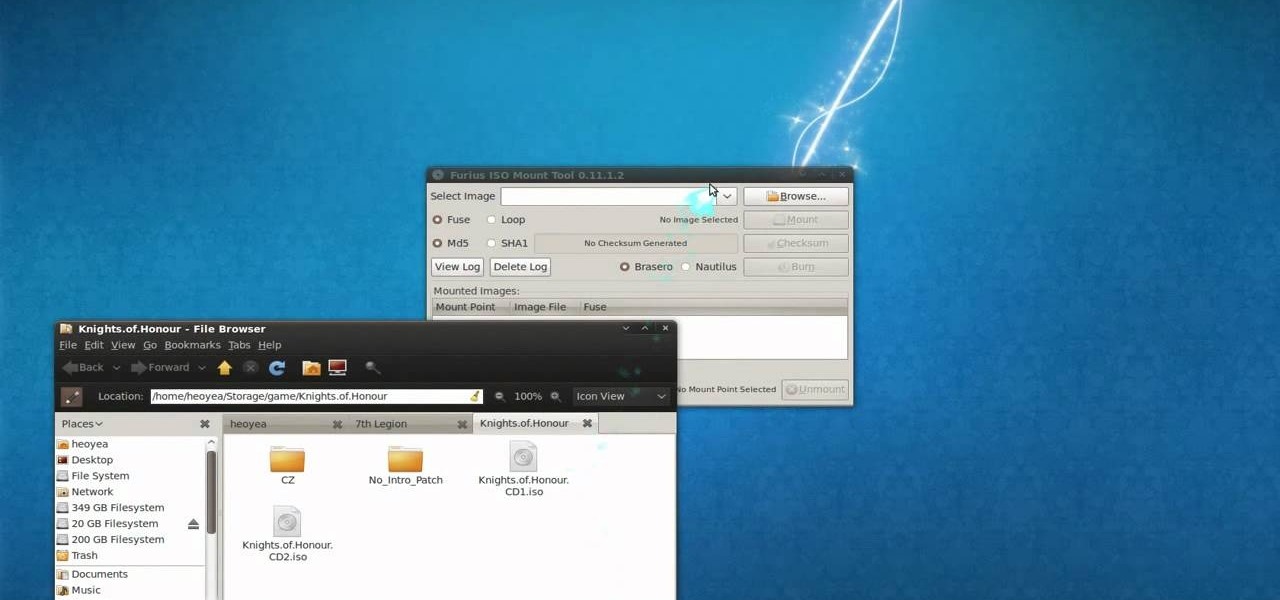
This is a tutorial video on how to use a virtual CD/DVD drive software tool called Furius ISO Mount. Furius ISO Mount is an .ISO, .IMG, .BIN, .MDF, and .NRG image management utility, that allows you to automatically mount and unmount disk image files. This utility application will allow you to mount multiple images at once, burn image files to optical disk, and create MD5 and SHA1 checksums to verify the that the image files are not corrupted. This program also automatically creates mount poi...

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

In this video, we learn how to download torrents on the iPhone 2.0 or 2.1. Before you do this, you will need: Cydia, Mobile Terminal, C Torrent, Safari Download Plug-in, and Mobile Finder. to start, you will first go to a torrent site and find the torrent that you want to download. Then, click on the download torrent button. From here, you will see a warning appear on the screen. Choose to download this and then go to your Mobile Finder. Find where you saved the torrent to. Then, hit the home...

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

File inclusion can allow an attacker to view files on a remote host they shouldn't be able to see, and it can even allow the attacker to run code on a target.

When attempting to run a script, it can be rather inconvenient to have to locate the script, and run it time and time again. What if there were a way to run a script from anywhere. Well that's what we'll be doing today. This can be useful for any scripts you use frequently, it can save you time by removing the need to locate and execute.

Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

The default tool for payload generation is MSFvenom, a Metasploit standalone payload generator as well as encoder. This tool is an incredibly powerful tool for payload generation, but it can be difficult and requires a bit of reading for newer users.

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

In this video, we learn how to upload Wordpress files using Filezilla. Before you get started, you will need to know the host, username, and password for your domain name. After this, click the quick connect button to connect to your server. The left hand side will show the local files on your server. Look in the root directory of your server and right click, then choose "create directory". Now, click on the plus sign to see a blog sub directory. Next, find where you downloaded Wordpress onto...

In this video tutorial, viewers learn how to mount ISO files without burning DVD. This task is very fast, easy and simple to do. The first way is to simply right-click on the ISO file, go to Open With and select Open with "Archive Mounter". The second way is to open the Terminal program and type in the command line: sudo mount -o loop -t iso9660.ISO [directory]. Users will need to create a directory before using the terminal command line. Finish by pressing the Enter key. This video will bene...

If you like shortcuts, then this shortcut for Windows XP should peak your interest. In this video, you'll learn the exact steps to adding a command prompt shortcut option to the Windows Explorer right-click menu. This allows you to access hidden functionality by adding a right-click option to select "Command Prompt Here" from the menu in Windows Explorer on a directory.

Google, Amazon, and Facebook are always listening. But what's worse? Hackers are listening, too. Windows PCs are particularly vulnerable, but with a few simple commands, a remote attacker can even take over the microphone on someone's Mac computer, streaming audio and listening to private conversations in real time without the victim's knowledge, abusing an overlooked security consideration.

Screenshots taken from a compromised computer can provide hackers with access to private emails, photographs, and information found in sensitive documents. This data can be used by the attackers to build profiles of a target for social engineering attacks and blackmail or even just to release the information out in the wild.

Passwords stored in web browsers like Google Chrome and Mozilla Firefox are a gold mine for hackers. An attacker with backdoor access to a compromised computer can easily dump and decrypt data stored in web browsers. So, you'll want to think twice before hitting "Save" next time you enter a new password.

With some of the groundwork out of the way in getting a Mac set up for hacking, it's time to start looking at toolboxes. Our first toolbox is Git, which will be used throughout future tutorials.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Hello friends. This is actually my first how to.

Hello, *Note This is my first how to post on here, so please correct anything that I have missed and let me know if anything I explained is unclear and I will try to clearify. Also I am a NOOB when it comes to this art, so I might have missed something, if so please inform me so I can better myself*

Welcome back, my greenhorn hackers! Many new hackers come from a Windows background, but seldom, if ever, use its built-in command-line tools. As a hacker, you will often be forced to control the target system using just Windows commands and no GUI.

Welcome back, my aspiring hackers! In recent tutorials, I have made reference to the name and location of the Linux devices in the file system, such as sda (first SATA or SCSI drive). Specifically, I have mentioned the way that Linux designates hard drives when making an image of a hard drive for forensic purposes.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

Welcome back, my fledgling hackers! If you're like most aspiring hackers, at one time or another you've probably spent too much time playing Call of Duty and not enough time preparing for your final exams.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

In this video, we learn how to use Raw Therapee with Gimp. First, you need to go online to Raw Therapee, then download and install Raw Therapee. Once you have this, open it up and familiarize yourself with the layout of the software and where the different tools are at. Next, change your preferences and pick your settings throughout the different folders. Next, find GIMP through the program folders as your installation directory. Now, it will export your images to GIMP automatically. This way...

First click the explore button, this will open a fold in which you will click homegroup and the second computer in the network. By clicking on that you will see what is in the homegroup. For example clicking on the video icon shows you all the videos available. If you right click on the video you can choose to watch it, open it, send it to different places, drag it onto your computer or copy and paste it into another directory.

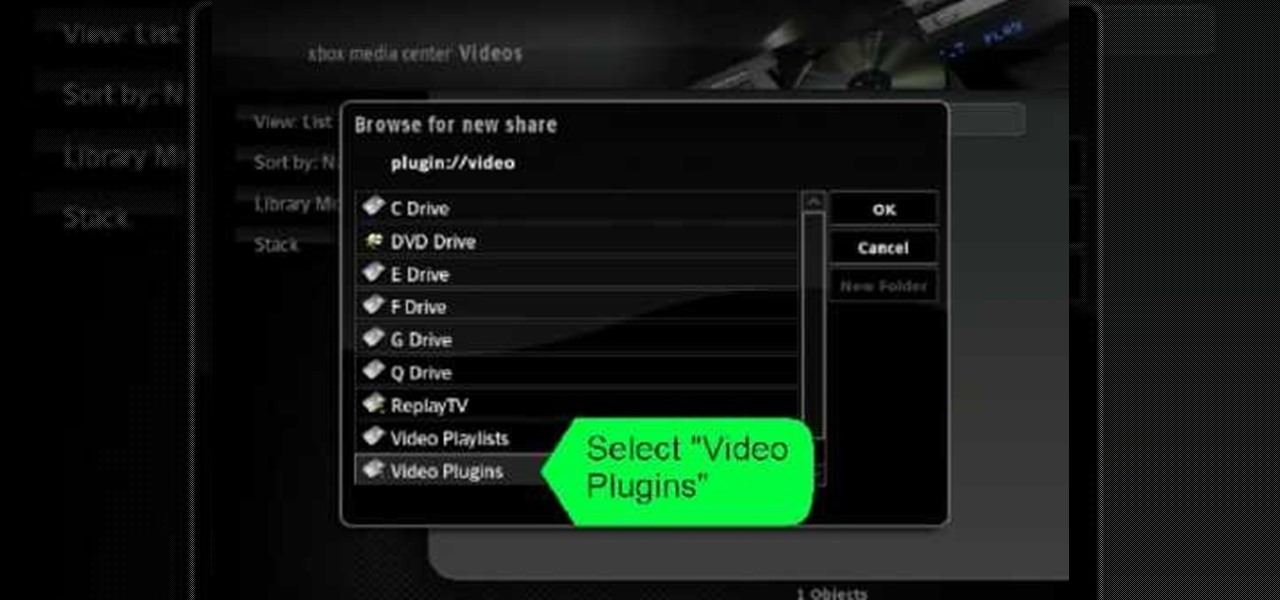
This video shows in detail and with annotations how to add plugins as sources in XBoxMediaCenter. With these plugins, you can watch selected media content from the web without browsing the websites with the computer. You browse through the items as if they were on the hard drive of the console. Available plugins include Joox, TVLinks, surfthechannel, seeqpod, powerflv, alpha centauri (german edutainment), stage6, lindenstrasse (german soap), myspace, Apple Movie Trailers, BBC radio, youporn, ...

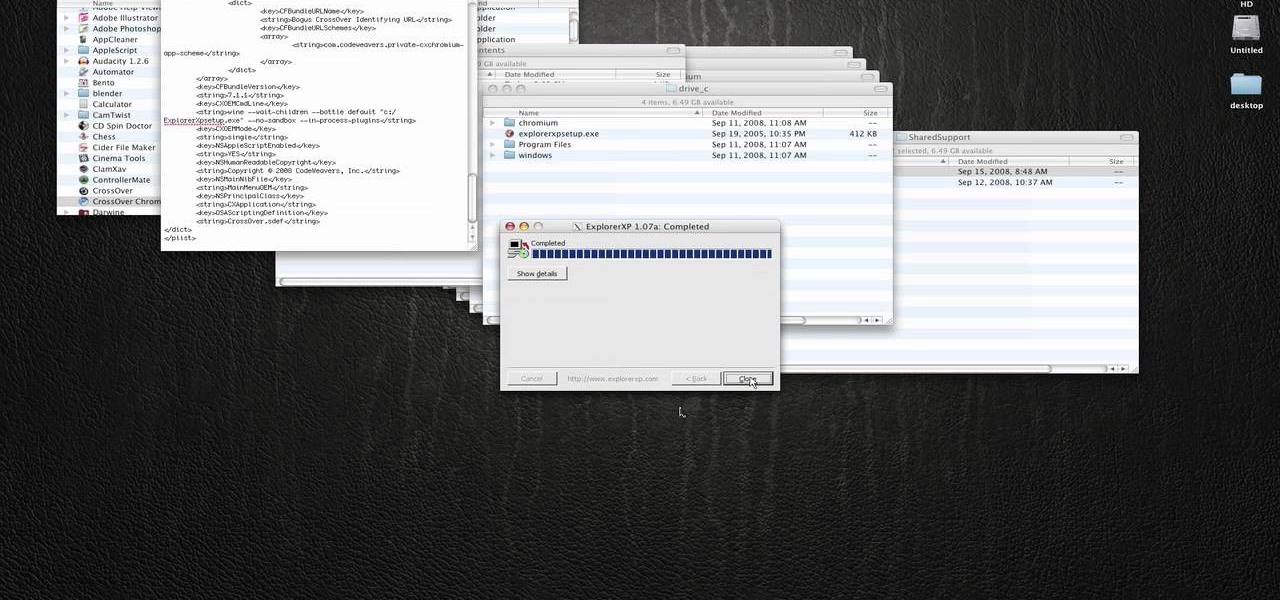
In this how to video, you will learn how to run Windows programs for free on a Mac using Crossover Chromium. You will need to download Crossover and install it by downloading it and dragging it into the applications folder. You will also need Explorer XP. Go to the applications folder and show the package content of Crossover. Go to shared support as you will need a file here later. Open Chromium, go to support, Chromium, and Drive, and then drop Explorer XP into the folder. Open the info fil...

Attention aspiring screenwriters! In this tutorial, learn how to sell that script. You may have written the next Hollywood blockbuster – but unless you can finance the film yourself, you’ll need to sell the screenplay to a producer who can make it come to life.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.