With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...
A custom application directory partition is a method of dividing your DNS servers for replication, and allows replication to occur between domain controllers. This video shows you the process of setting up your own using Windows Server 2008, though it will also work for the 2003 version as well.

In this video tutorial, viewers learn how to quickly copy a folder's content list in Windows. Begin by clicking on the Start menu and open the Run program. Then type in "cmd" to open the Command Prompt window. Now navigate the desired folder and type "dir | clip" beside it. Press Enter and it will automatically copy the directory to the clipboard. Essentially, it is a tool that will the command prompt command to the clipboard. This video will benefit those viewers who use a Windows computer, ...
Faced with an "Unable to create directory" error when attempting to upload an image to WordPress? This clip offers instructions on how to fix it. Every version of WordPress brings with it new features, new functions and new ways of doing things. Fortunately, the very same technology that allows an open-source blog publishing application like WordPress to exist in the first place also makes it easy for its users to share information about its features through videos like this one. Take a look.

Eager to find new and interesting Tumbleblogs to follow? With the Tumblr directory, it's easy. And this brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started browsing the Tumblr directory yourself, take a look.

Designate a back end or administrator sector of the website, a place you can use to manage the content on the rest of the site. This tutorial shows you how to use Dreamweaver to set up this area of your website and cordon it off from the rest of your website.

In this clip, you'll learn how to make recourse to the documents folder from within an iOS application. Whether you're new to the Objective-C operating language and Xcode IDE or are a seasoned developer merely looking to pick up a few new tips and tricks, you're certain to be well served by this tutorial. For more information, including a complete overview and detailed, step-by-step instructions, watch this free video Objective-C programming lesson for iPhone & iPod Touch developers.

This tutorial explains how to list the files in a directory using a C# application.

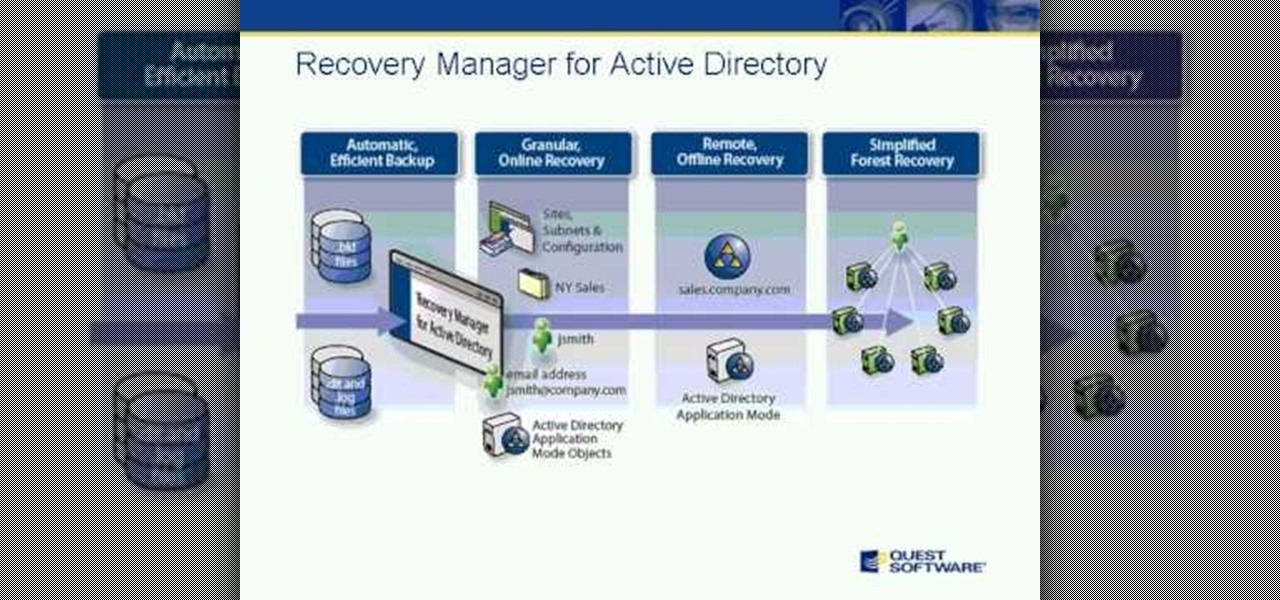
View our webcast to learn about the advantages of using a comprehensive Active Directory recovery solution -- and view a product demo. With Quest Recovery Manager for Active Directory, recovery time can be reduced from hours to minutes!

Ever wanted a specific directory in your site to be available only to certain people? Password protecting a directory can be done several ways. In this cPanel video tutorial you will learn how to password protect a directory. Make sure to hit "play tutorial" in the top left corner of the video to start the video. There is no sound, so you'll need to watch the pop-up directions. Password-protect a directory in cPanel.

http://www.snoft.com - This video show how to do the site setting after you finish installing Snoft Article Directory Script. The site owner should login as an admin and go in the general setting area and start customizing the different options. This is for the article directories that are built on Snoft Article Directory Script.

In my first tutorial on Linux basics, I discussed the importance of hackers using Linux and the structure of the directory system. We also looked briefly at the cd command. In this second Linux guide, I'll spend a bit more time with changing directories, listing directories, creating files and directories, and finally, getting help. Let's open up BackTrack and getting started learning more Linux for the aspiring hacker.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

Welcome back, my tenderfoot hackers! This is the third installment of my series on basic Linux skills that every hacker should know. Although some hacking tools are available for Windows and Mac, every real hacker uses Linux—for good reason.

Learn to setup a visual dial icon on your iphone. This one click application allows you to call anyone in your directory by clicking on a photo of them on your phones desktop.

This is the first of 3 steps that will show you how to juggle three balls. Jim the juggler demonstrates how to get them up and going. Step 1 begins with one ball, so be patient, you need to work your way up! (WMP files and smaller videos are available at the root directory)

If you own a PS3 slim and you'd like to jailbreak it (read: hack) this video will show you what to do. You'll be dealing with a firmware of 3.41 or lower, and you'll need an iPhone (2G or 3G only) or an iPod Touch (First Generation Only)

There are several different kinds of disc drives that come in different iterations of the XBox 360, and each one has to be hacked a little differently. This video will show you how to flash the ms28 drive used in some systems, the second part of the video will show you how to determine what model of drive you have. It is very detailed, and should have you well on your way to hacking you beloved XBox 360 and maximizing its potential.

In this web TV presentation the host is talking about Grub 2. In Grub 2 you can mount an ISO file like a device with the loop back function. In Grub 1 you can use tack tack mem to mount iso files if the files are not fragmented by using the map command. Grub 2 is an application available for download that will be available after download as a chain from Grub 1 to Grub 2 to your operating system. Grub is a program that compresses all of your favorite boot programs into one.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

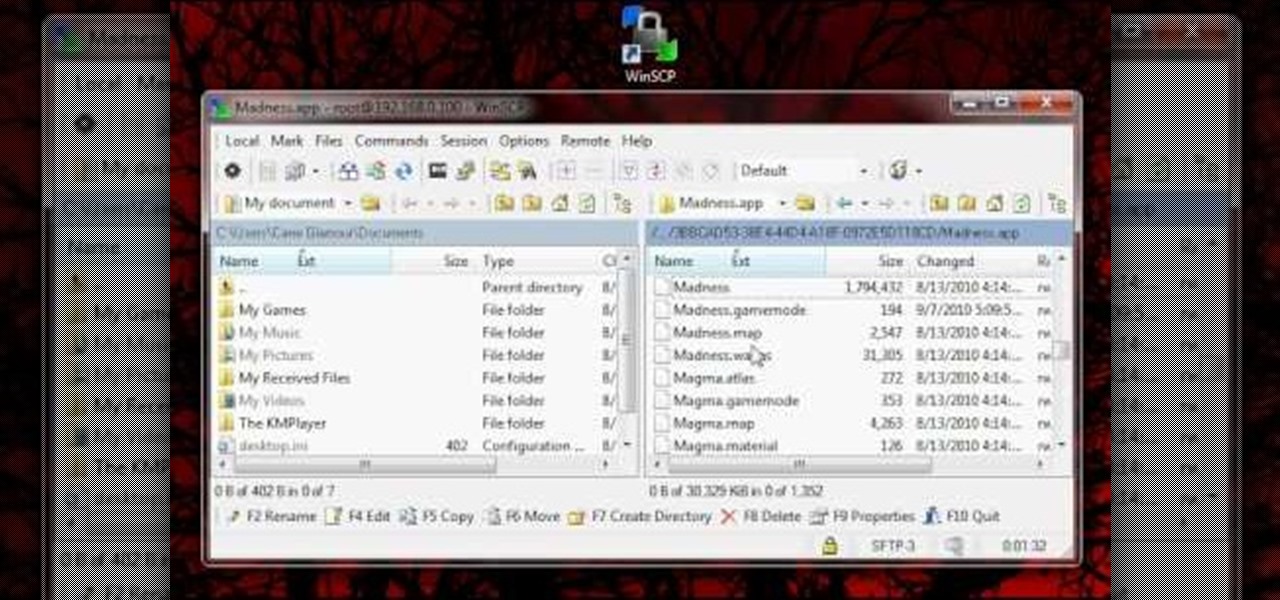
In order for this tutorial to work, you will need a jailbroken iPhone or iPod Touch. Once you have this, download the OpenSSH protocol from Cydia and then download WinSCP onto your PC. Once you've hooked everything up and logged in, navigate through your Applications directory until you find the TowerMadness app. Once you have opened the TowerMadness app, all you need to do now is find the right file and change it around to increase the amount of money you have!

In this video tutorial from Get Connected TV, hosts AJ Vickery and Mike Agerbo will show you how to safely move your iPod files to your home pc, for back up purposes, just in case something were to happen to your iTunes account or your iPod is damaged, or music directory accidentally deleted. The program they introduce in this video is called iPod-Rip, and they lead you through the steps necessary to back up your iPod files safely and easily, without damaging or deleting your files.

Conceptually, what is node-based compositing and what do nodes do? This clip uses the factory analogy to convey the concept. Blender can process video, images, sequences, and families of images in a directory. Then you'll fire up Blender and talk about threading nodes and how images are duplicated and routed through the compositing network ("noodle"), how threads are created between sockets. Creating threads, cut threads. The clip also points out common threading errors and misrouting threads...

Want to share Internet connectivity between two computers without a wireless network but have an extra CAT5 ethernet cable? You're in luck. This home networking how-to will show you what to do to get your machines talking not only to one another but the web at large.

One of the first steps when pentesting a website should be scanning for hidden directories. It is essential for finding valuable information or potential attack vectors that might otherwise be unseen on the public-facing site. There are many tools out there that will perform the brute-forcing process, but not all are created equally.

Video demonstrates how to synchronize two folders on windows without doing much of copy pasting and does the job easily. This is a free wear, “FlagSync”.

You can create an image gallery of any directory on your file system with Konqueror. If you are a KDE user and you need to see the images in any directory, but if there are any other stuffs beside images in that directory then you will see that stuffs too. So if you do not want this, you need to click on tools in Konqueror menu and choose "create image gallery" for the current directory. There will be many options like folder, look etc. so set your options as you like and click on create, it ...

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install additional brushes for GIMP on Ubuntu Linux.

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

This video shows us how to change driving letters or directories in DOS command. Firstly go to start menu and then click on run. Then type cmd and press OK with which a DOS command cmd window will pop up. Now you need to change the directory and these is done by typing ‘cd..’ and after that press enter. Now you have changed the directory and now you need to see what’s in there and for that type ‘dir’ and press enter and this shows what’s in that directory. Now change to other directory by typ...

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

One of the first steps in attacking a web application is enumerating hidden directories and files. Doing so can often yield valuable information that makes it easier to execute a precise attack, leaving less room for errors and wasted time. There are many tools available to do this, but not all of them are created equally. Gobuster, a directory scanner written in Go, is definitely worth exploring.
Fugu - a simple virus in bash. I once told a friend of mine I'd written a virus in bash and he scoffed - "You can't write a virus in bash!" - he sniggered, like an ignorant idiot.

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.