Have you seen odd, square codes on some specific merchandise? These are called QR codes, or quick-response codes, and they are a type of bar code which your smartphone can read and then take you to a particular website, give you coupons or even a business card. Here's how you can get the most out of QR codes.

David Wygant discusses how to meet women without pick-up lines. Men like to have instruction manuals with secret codes to tell them how to do things. Women, however, are simple to relate to and interact with once you get to know them. Don't manipulate a woman. Rather, use her language to make the connection. You can use tools to boost your success with women, but your initial connection has to start naturally and authentically. If you want an amazing connection with a woman, then you have to ...
Any hacker worth her salt will need to debug from time to time. One particularly efficient way to check your code is with the RATS code checking tool. In this video, you'll learn how to use the RATS code checking tool for C/C++, PHP and Perl. For a detailed walkthrough on how to use RATS scanner to audit your source code, take a look!
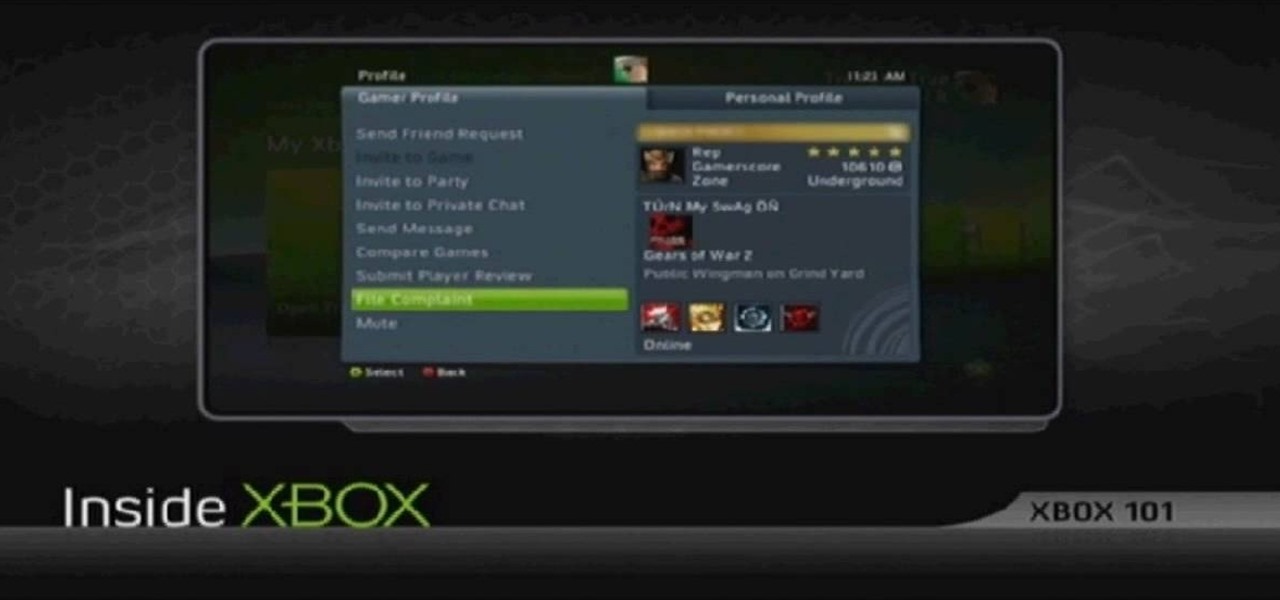
In this tutorial, we learn how to file a player complaint with Microsoft (Xbox 101). There is no tolerance for file complaints, cheating, rude remarks, and anything of that nature. The file complaint feature should only be used if someone really violated the code of conduct. When you feel someone has crossed the line, you will tap the guide button, then select friends. From here, choose the person from the group and identify the complaint. View the profile of that person, then you will be fin...
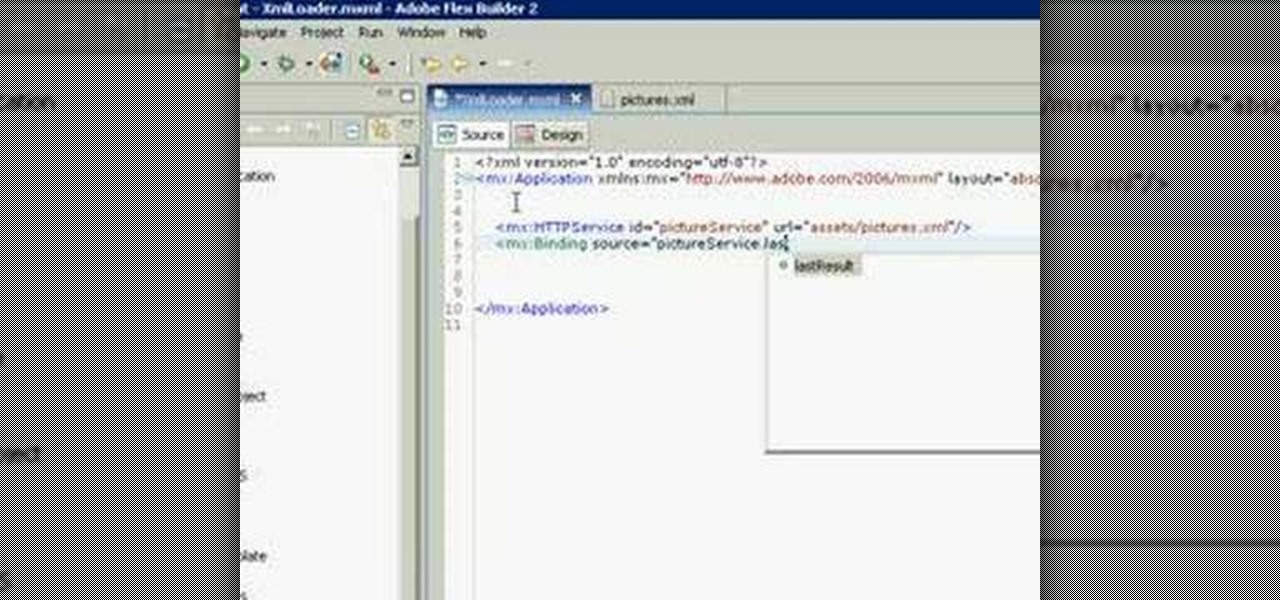
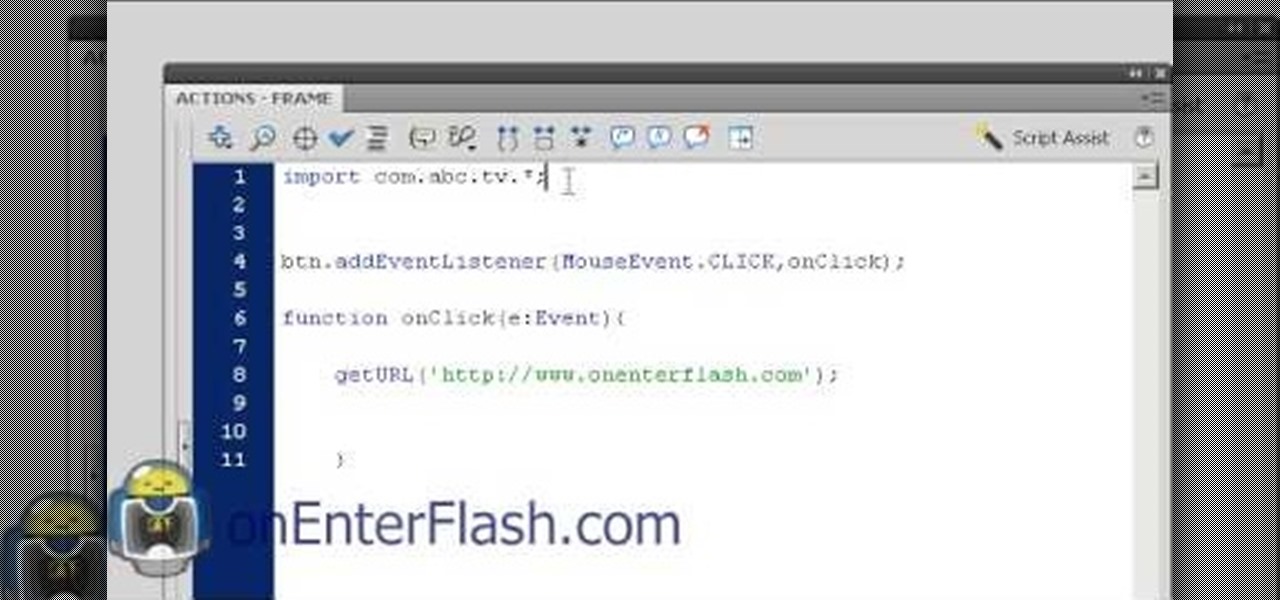
This XML video tutorial will show you how to bind an XML file in MXML in about ten lines. First you'll want to create a Flex project in Adobe Macromedia Flex Builder 2, then create an assets folder and a new XML file in MXML. Coding doesn't get any easier than this. Just watch and learn.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

A lot of people still trust their web browsers to remember every online account password for them. If you're one of those users, you need to adopt a more secure way of managing passwords, because browser-stored passwords are hacker gold mines. With a USB Rubber Ducky and physical access to your computer, they can have a screenshot of all your credentials in their inbox in less than 60 seconds.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Continuing our series on building a dynamic user interface for the HoloLens, this guide will show how to rotate the objects that we already created and moved and scaled in previous lessons.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

With the game Crush the Castle, it is now possible to hack the game and get a high score. By following a few simple steps shown in the video, it is entirely possible to achieve a gold medal in the game quite easily. As simple as entering a sequence of number codes into a line will make it possible to do one shot and still win gold, as well as completely crush the castle. Just by putting in the code, you are able to start the game, and, with one shot from the catapult, you are able to complete...

IF you have a Saturn S-Series and it's thrown a P0340 or P0341 error code at your on the scanner after the check engine light has come on, you might be wondering how your cam position sensor can be off if you don't actually have one in your car. Watch this video to learn exactly what this code means to your car and some thoughts on how you might fix it. Three words: spark plug wires.

Custom classes are powerful tools in Flash CS4 that enable you to reuse sections of Actionscript 3 code more easily, greatly smoothing the software development process. This video will teach you how to create, integrate, and use custom classes in Flash CS4. Don't waste your coding time repeating yourself, watch this video.

It's time to go achievement hunting! In this video from the great men at Achievement Hunter, you'll be playing the game Skate 3. In this tutorial, you'll be finding out how to get some extra characters and use a couple of cheat codes. The characters are unique and different and the codes are pretty fun to use. So check out the tutorial and have fun!

While hackers know and love the Raspberry Pi, many don't know of its cheaper cousin, the microcontroller. Unlike a Pi, which can be used more or less like a regular computer, microcontrollers like the Wi-Fi connected ESP8266 require some necessary programming skill to master. In this guide, we'll build an Arduino program from scratch and explain the code structure in a way anyone can understand.

In a previous tutorial, we were able to place the Mona Lisa on vertical surfaces such as walls, books, and monitors using ARKit 1.5. By combining the power of Scene Kit and Sprite Kit (Apple's 2D graphics engine), we can play a video on a flat surface in ARKit.

In a previous tutorial, we were able to measure vertical surfaces such as walls, books, and monitors using ARKit 1.5. With the advent of vertical plane anchors, we can now also attach objects onto these vertical walls.

Starting in iOS 11, Apple introduced a QR code scanner for iPhone that's baked right into the Camera app, reducing the need for a third-party scanner. However, not everyone knew it existed, so a lot of users were still using third-party QR code scanners. In iOS 12 and later, Apple addressed the issue, making theirs much more visible, as well as improved QR code scanning in general.

So, you want your terminal to be customized with awesome script every time you fire it up, huh?! Well, look no further because I am here to answer this calling!

Watch this automotive video tutorial to see how to scan your automobile for diagnostic trouble codes.

In this video series, watch as line dancing expert Dawn Williams teaches how to line dance. Learn the various steps, how to move to the different counts, how to do tricks while line dancing, how to do the tub thump, and how to put it all together.

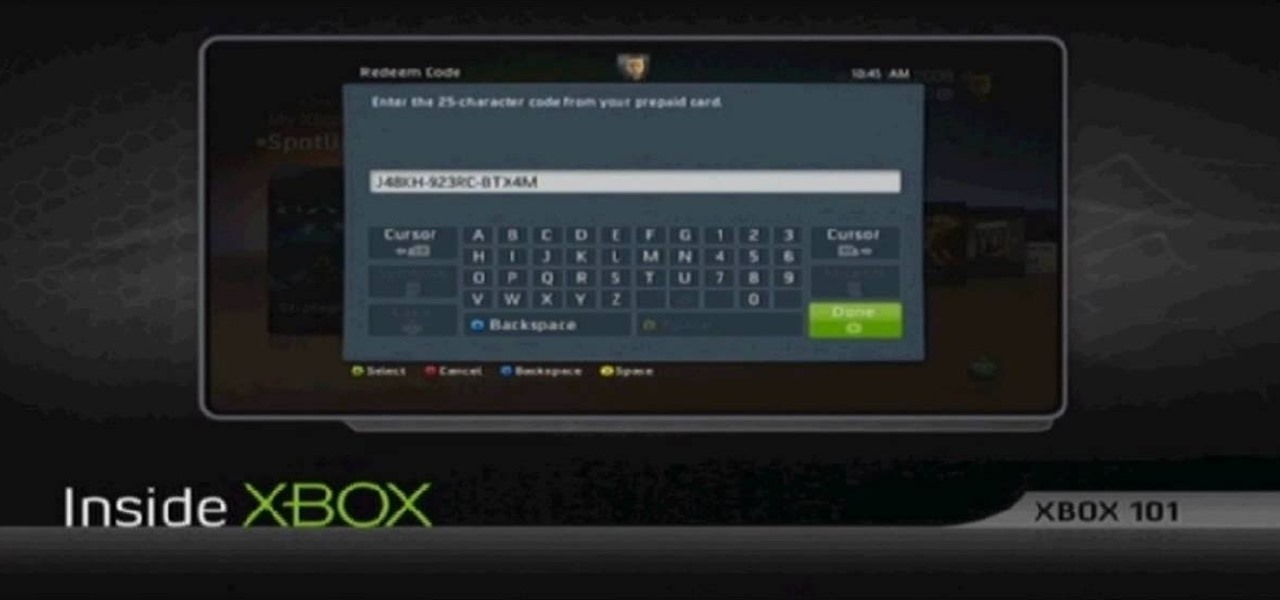
In this tutorial, we learn how to redeem a code for Microsoft Points (Xbox 101). First, you will need to log onto your Xbox Live account on your console. From here, pick a game that you want to purchase. Make sure you research the information about the game and you really want it, because you cannot return it. After this, choose the option to redeem a code and then type in the code for your Microsoft Points. After you do this, you will be bale to purchase the game that you want and you will h...

Balsamiq is a really cool software suite that allows you to create Apps visually without having to write any code! This two-part video lecture will introduce you to Balsamiq and show you how to use it to create your own cool Apps. If you want to learn Balsamiq, you really couldn't do any better than this.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

The fourth and final beta version of Android O just made its debut, and the biggest change is what appears to be a new code name. When you access Android 8.0's version number Easter egg, you'll be greeted by ... a cartoon octopus.

Hello NullByte, it's mkilic! This time I'm here with the C.H.I.P from NTC. Although it is not too popular, the C.H.I.P is a brand new micro computer. It is very similar to the Raspberry Pi or Beaglebone Black. The key difference with this particular board is its cost and size. The C.H.I.P only costs $9 and measures 2.5 x 1.5 inches. In addition to this, the C.H.I.P has built in 802.11 b/g/n Wifi and Bluetooth 4.0. Considering these great specs, what could a Hacker use this for? Step 1: The In...

T-Mobile's "Binge On" service for streaming videos has received mixed reactions so far. On one hand, it gives any T-Mobile subscriber unlimited access to popular streaming video services like Netflix and Hulu without having to worry about going over their monthly data cap. On the other hand, it reduces video quality to 480p, which is 6 times lower than full HD.

In the last tutorial, we learned how to make functions and how they work on the high level. This time, we will take a peek under the hood again, stare deep into its soul and see its ugliness face to face to see how it works in the lower level.

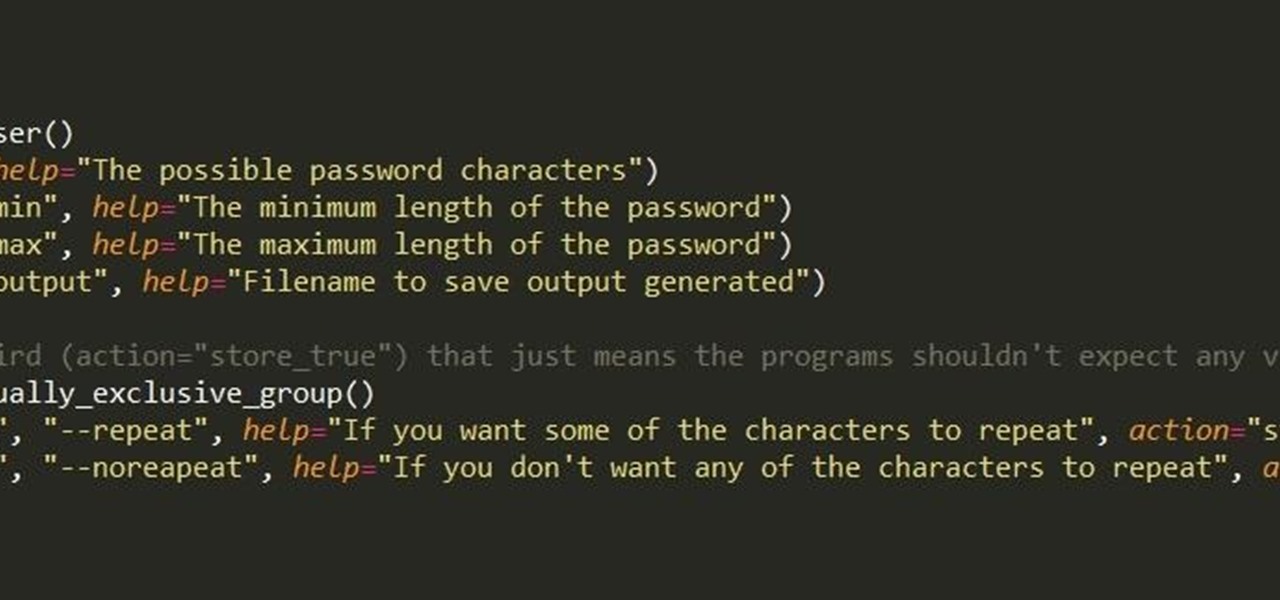
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

Welcome to the sequel to the latest post on writing 64 bit shellcode! This tutorial will assume that you are aware of everything mentioned in the last one, as I will try to make this tutorial void of formalities and straight to the point! If you have not read the last one, I suggest doing so unless you are familiar with basic assembly programming and system calls. This is by no means rocket science, so therefore I will simply repeat my TL;DR from last time before we get started, so that the a...

When you use a scanner to look for error codes on a car, many can show up at once and confuse you as to the nature of the problem. Often, all of the codes are responses to the same problem. Watch this video for tips on interpreting multiple error codes.

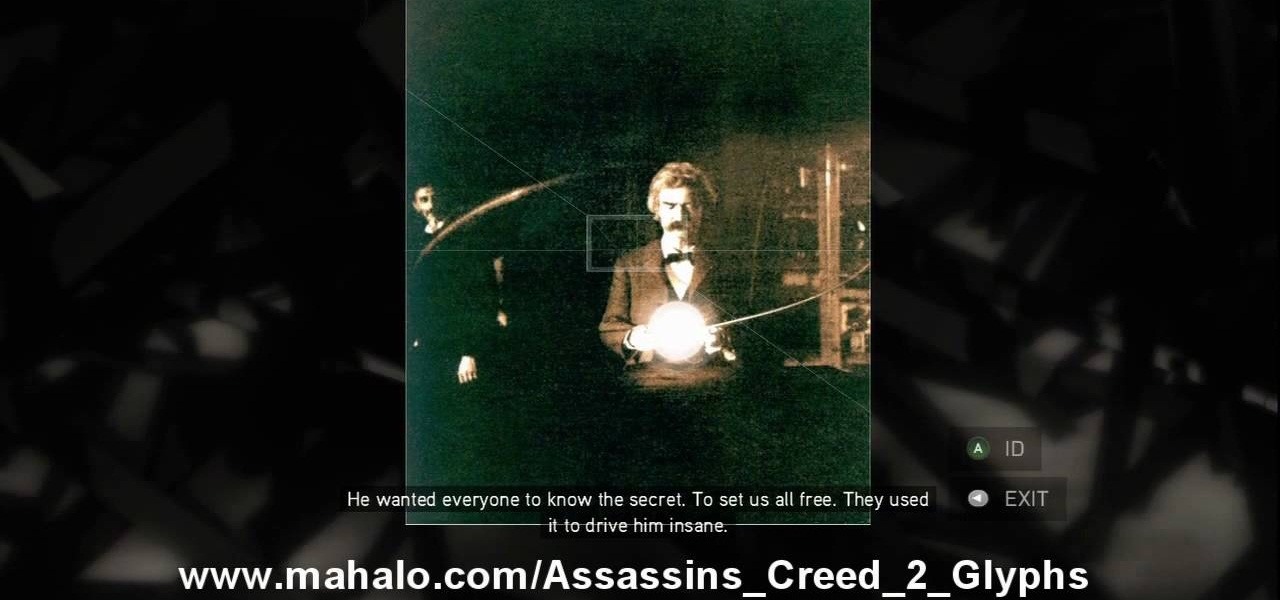
This is the 12th puzzle, entitled "Titans of Industry", in Assassin's Creed 2. Code wheel puzzle 1: The key here is in the “4=1” on the blueprint at the left of the screen. Line up the red 4 over the gray 1 and input the following code: 917240. Image 1: This one’s the opposite of the light-bulb “puzzle” from before – just move the dollar sign over the bulbs to extinguish them. Image 2: Highlight the glowing ball at the center of the image. Code wheel puzzle 2: Your hints here are the “2” on t...

This is an instructional video to learn the line dance for Alan Jackson's new single, "Good Time." Alan Jackson is a star country singer and known for making great music to line dance to. He's a Grammy winning artist that inspires many to learn line dancing so that they may participate at his huge stadium concerts.

You've seen code blues called on TV, but how about in real life? If you are becoming a nurse it is important to know what goes on as part of a code blue situation. This nursing how-to video presents a mock code blue presentation with faculty. Follow along and learn what is involved in caring for a patient that has gone into code blue.

To program your DirecTV remote for your XBox you will need to find your programming codes. Press menu on your remote and scroll down to parental fav's and setups, then system setup, select remote control, and program remote. You can use either AV1 or AV2 both should work. Then you will choose DVD, and then select the brand for your 360 and your program codes will come up. Put your TV in AVI mode and press your menu and select button at the same time. The lights at the top of the remote should...

This video tutorial program is designed to promote ground crew safety when working under and around helicopters during external load operations. This is not a safety-training and is only intended to be used with the participation of a ground crew safety officer, trainer or other qualified personnel. All training and refresher courses must be done in accordance with federal and provincial regulations and the Canada Labour Code.