
TypoGuy Explaining Anonymity: Who Is Anonymous?
Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.


Continuing this series, I am now moving on to the section, 'Anonymous'. Hope you are looking forward to read this.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.
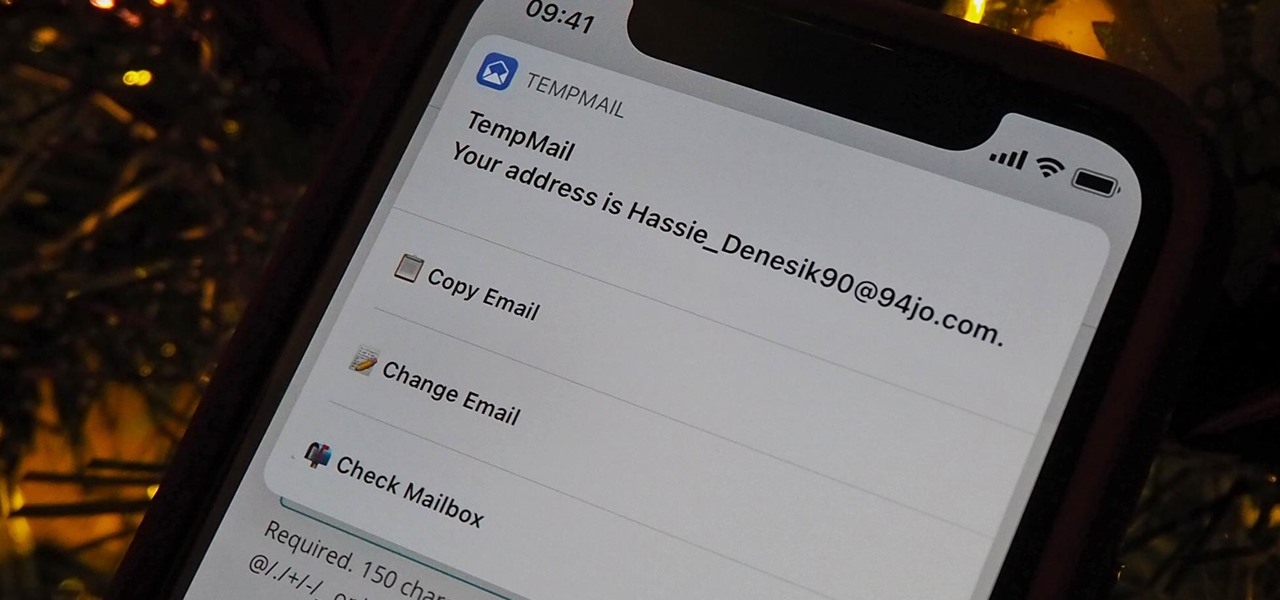
A temporary email can go a long way. Using your actual email to sign up for a mailing list to receive 10% off a purchase doesn't make sense if you don't use the website much. It means you'll have to deal with spam emails from then on, which is why an anonymous email is perfect not to have to deal with all that trouble. And that's where the TempMail shortcut for your iPhone comes in handy.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.
The long standing popularity of 4chan has been due to the entirely anonymous setup. The site's anonymous community and culture has provoked media attention, in turn inciting larger audiences. On the other side of the spectrum is Facebook—popular for its connectivity and easily identifiable names. With the brush of keyboard stroke, you can be connected with your entire high school class in a matter of seconds.
When browsing the web, you may not be quite as anonymous as you think, especially if you are using public WiFi. The easiest way to stay as anonymous and safe as you are going to get, is to use a VPN (there are a number of great free ones). In this tutorial, we will show you how to set up a VPN on Android, and how this protects you.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

If you need to share something online but don't want your personal information attached to the file, use an anonymous file hosting site. By uploading files anonymously, you keep your IP address safe and won't need to create any kind of account that could provide further logging. You can do this in a web browser, but it's much easier to do using a shortcut on your iPhone.
Log in to your LinkedIn profile, and you'll immediately be prompted to check out who's peeked at your profile. With one click, you can discover how many recruiters, companies, and random people have viewed your online resume.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)
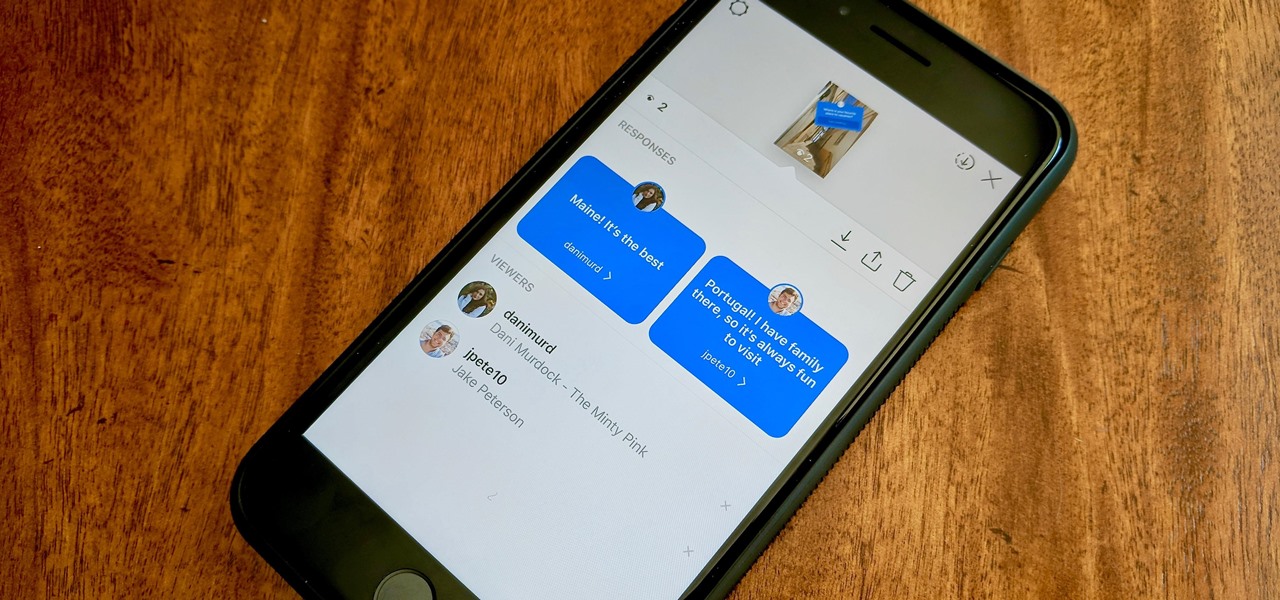
Users on Instagram have taken the app's new "Questions" sticker and run with it — it's tough to find a story in your feed that doesn't proudly sport "Ask me a question." However, it appears there's some confusion when it comes to the anonymity of your answers to these questions. News flash — your username is attached to every response.

Configuring onion services for the first time can be tricky. A surprising number of system administrators make seemingly trivial mistakes that ultimately lead to catastrophic cases of de-anonymizing supposedly anonymous sites on the dark web. OnionScan is a tool designed to identify common misconfigurations in onion services and aid us in understanding how to fix them.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

Welcome back, my nascent hackers!

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

Internet Relay Chat, or IRC, is one of the most popular chat protocols on the internet. The technology can be connected to the Tor network to create an anonymous and secure chatroom — without the use of public IP addresses.

There will always be a time when you're not entirely sure what you're doing with a certain subject. But the days of weighing the pros and cons yourself are coming to an end. Whether it's a common quandary like "Where should we eat?", or a more specific question along the lines of "Should I buy this shirt or not?", you can now simply AskInternets.

In the 21st century, we're all looking for ways to stay private, especially on our electronic devices. We have big tech corporations, enemy countries, malicious hackers, and other prying eyes watching our every move, so it's only natural to want to limit what they can see. Making your web browsing experience on iPhone and iPad more private is one way to do that.
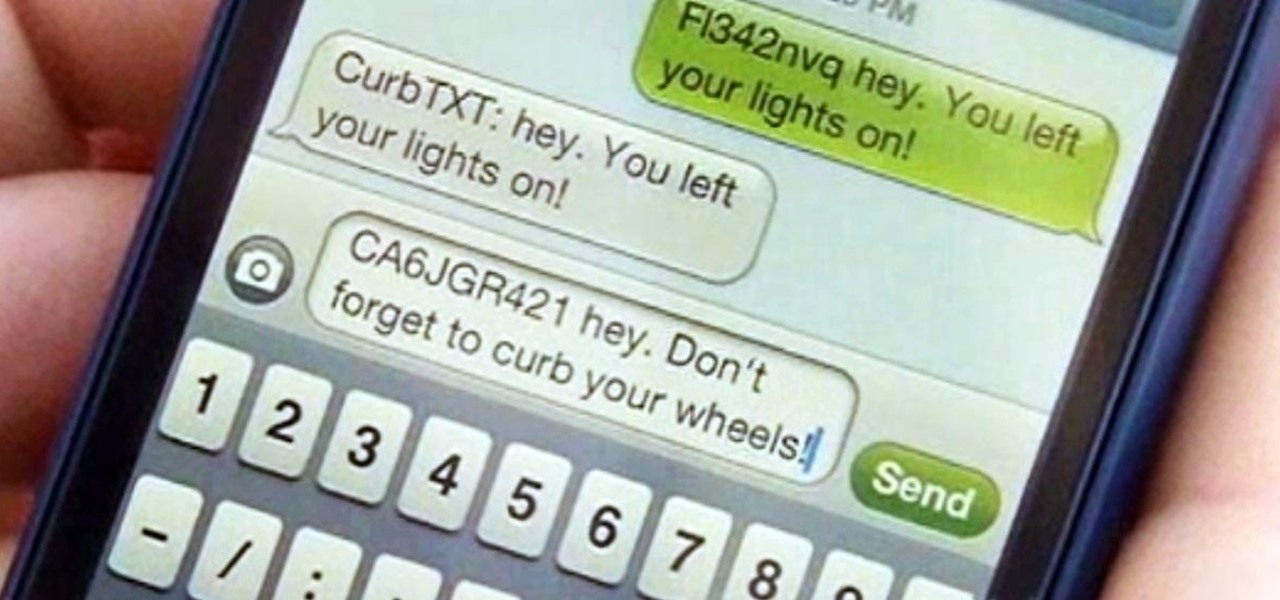
Parking. Ugh. Parking is about as fun as running through a swarm of bees while being chased by a pack of wolves from The Grey.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.
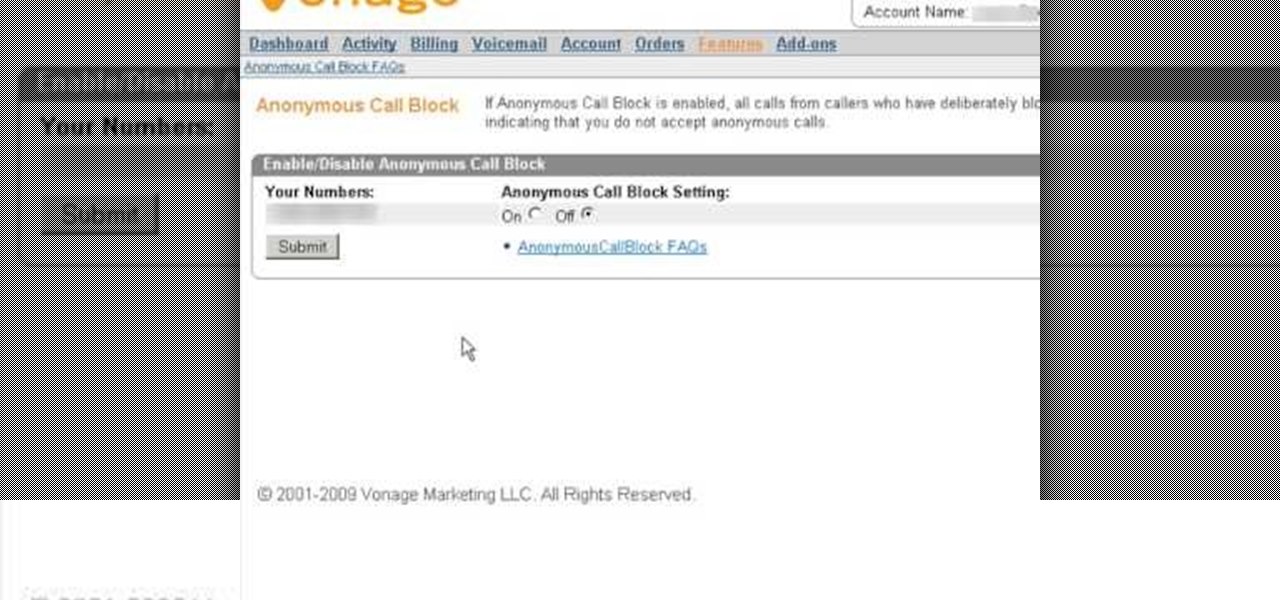
If you are looking for a way to prevent telemarketers and nothing else is working, consider signing up for Vonage's call blocking feature. In this tutorial, brought to you straight from the professionals at Vonage, learn how to set your phone to block any incoming call without a number attached to it.

The computer represents a whole new frontier in prank technology, and if you've aren't computer pranking people you need to get with the times. Watch this video to learn how to send anonymous emails, make crank calls online, even send people a message saying they're about to be murdered!

Watch this video to learn how to shoot anonymous interviews for documentaries. Matt explains how to maintain anonymity using the proper lighting and audio effects.
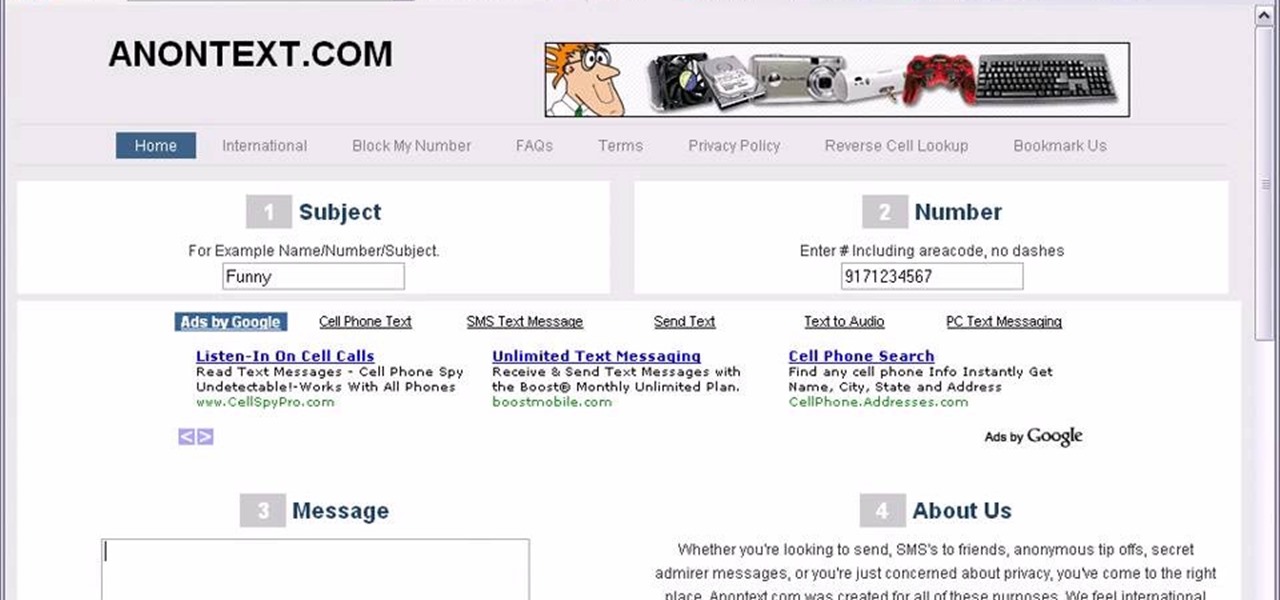
Want to send text messages, but don't want your recipient to know they're from you? You can use a website called AnonText.com, which lets you send anonymized text messages to any cell phone number. Use your computer, or, if you have a smartphone (like an iPhone, Droid HTC Evo), then you can navigate to the website using your phone's browser capabilities.

Have you been holding onto something for way too long? Been biting your tongue around your boss or teachers? Vent some of that frustration by sending an anonymous email or text. All you need to do is get online and type in all those nasty things you've been dying to say. This video will show you how to text and email anonymously.
As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through anonymous browsing. In this tutorial, you'll learn how to use the freeunblockme.com tutorial to surf the web anonymously.
We look at a nice and easy to use software on a modified Firefox browser where you can surf anonymous via the tor network.

Welcome everyone Today i will show you a simple but very useful way to stop your ip leaks . In order to stay anonymous on the web you HAVE to do this.

This video will show you a few easy steps to remain anonymous on the Internet by replacing your ip address for a fake one.

Over the past couple of weeks, there have been a series of high-profile hacks and leaks. From the rooting of CombinedSystems, to a secret FBI conference call leak, all the way to the distributed denial-of-service (DDoS) attacks on U.S. government sites—with a lot in-between. As governments move to close their long fingers around the free speech that exposes their secrets, this shadowy collective of loose-knit, but like-minded individuals are hell bent on preventing them. Or are they?

Anonymous hacktivists announced via Twitter that they had successfully hacked the website of New York Iron Works, a police-equipment supplier, and replaced the homepage with a tribute of love to arrested hacker and Chicagoan Jeremy Hammond.