
News: FBI holds teleconference regarding Anonymous - but they were listening!
The FBI decided to have a large internal teleconference on ideas and plans to wrangle in Anonymous 'members' - need less to say this ended in a rather unexpected way...


The FBI decided to have a large internal teleconference on ideas and plans to wrangle in Anonymous 'members' - need less to say this ended in a rather unexpected way...

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

I'm sure we've all heard about MSN and Yahoo! Messenger, right? They can be useful, but the setup can be quite time consuming for those who need to use it just once or twice—and the privacy statements are a real bother. For example, we must provide our real details. You could use Fake Name Generator, but if you get caught, you will have your account suspended. I don't have a law degree, but to my understanding the United States recently passed legislation that gives the authorities the power ...

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

@AnonymousIRC released the source code for VMware, mentioning the Pirate Bay.

I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an updated and more comprehensive tutorial.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

If you've read my darknet series, you've probably got a pretty good idea of what I2P actually is and is capable of. One of the features of I2P is that it's designed with P2P file sharing in mind. Using a built-in service called I2PSnark, you can host and seed torrents quickly and easily!

Anonymity is very important to many internet users. By having your "e-identity" exposed online, you can be stuck with a number of unwanted issues, such as:
How to surf the net anonymously with a proxy. Download and use a proxy for anonymous web surfing.

Some of you might be using Tor to host hidden services, and some of you might not even know what hidden services are. If the latter's you, do not miss this article. Why? Because you can host your websites and services on the I2P darknet. It's safe and secure—it's anonymous.
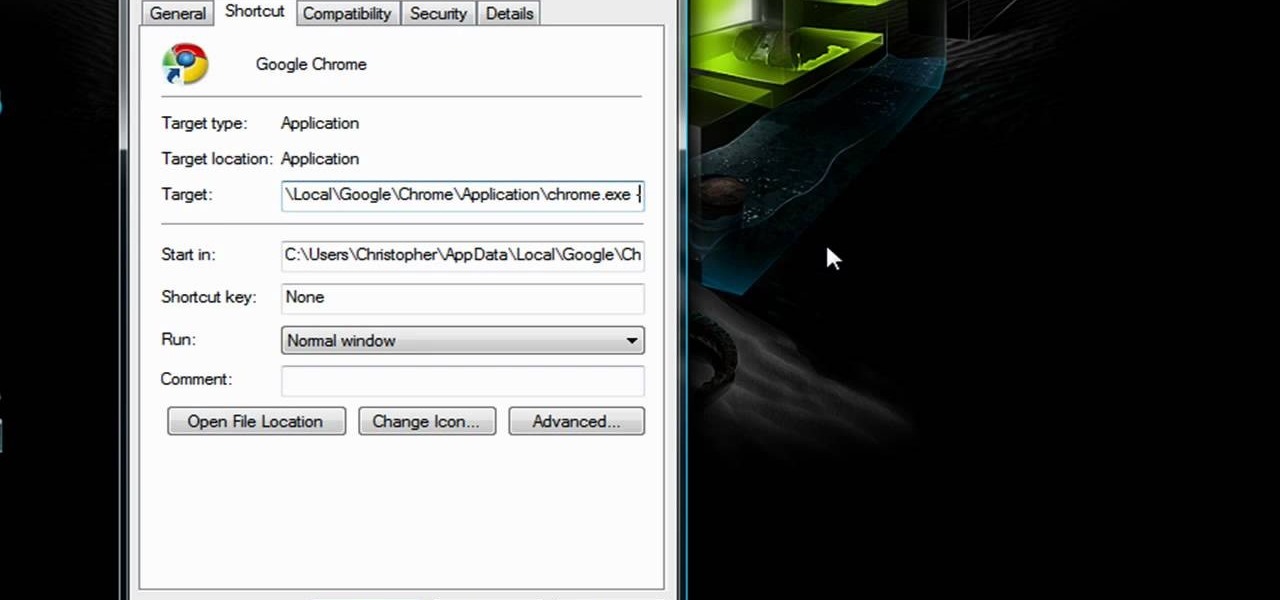
Did you know that Google Chrome has a feature called Incognito Mode that allows you to browse the web without having your history recorded or any cookies downloaded? It's perfect for shared computers, but by default you have to turn it on every time you open the browser. Watch this video to learn how to make Google Chrome default to Incognito Mode, removing one step between you and anonymous browsing.

Just because the internet renders you virtually anonymous does not mean social customs should be ignored. Just like in the outside world, there is etiquette that should be obeyed if you want to be treated as a friend rather than an annoyance online. In this how to video, Proper Ollie teaches you how you can have proper internet etiquette in social networking forums.

If you've ever participated in a Anonymous protest against scientology or celebrated Guy Fawkes day, you probably know that drinking through a Guy Fawkes mask is tough, especially if you're keeping your identity a secret. Watch this video to hear an Anonymous member explain how to drink water without compromising your anonymity.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.
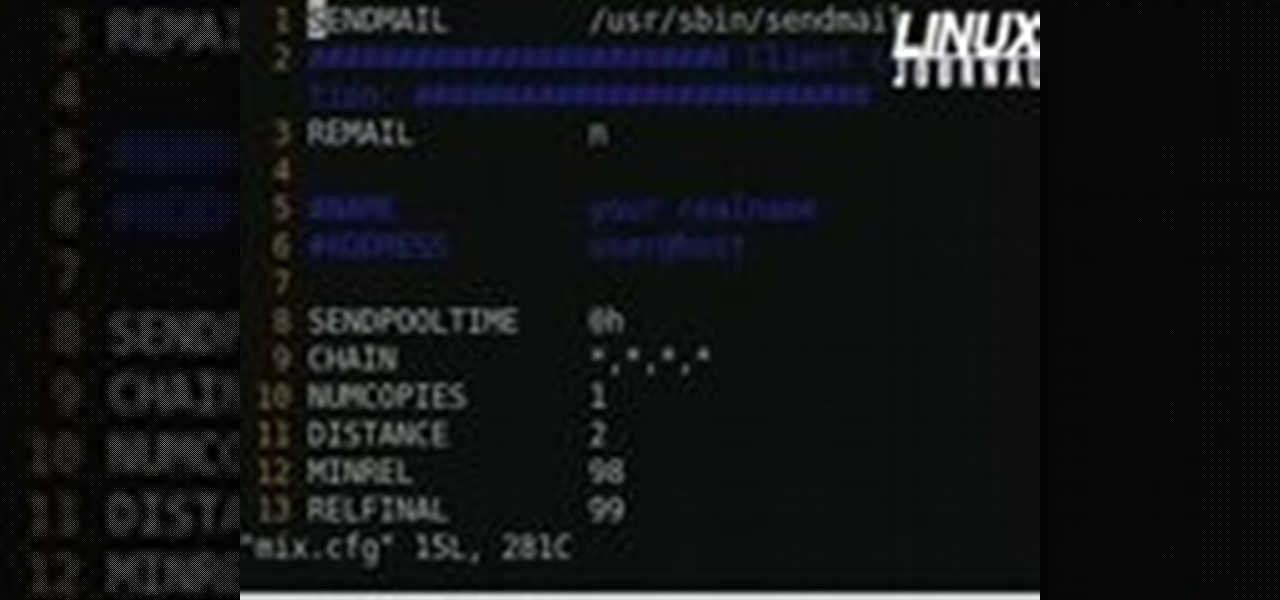
Email is one of the least private and least secure forms of communication, although few people realize this. MixMaster is one way to allow secure, anonymous communication even over the very public medium of email. This tutorial will get you started with MixMaster quickly and easily.
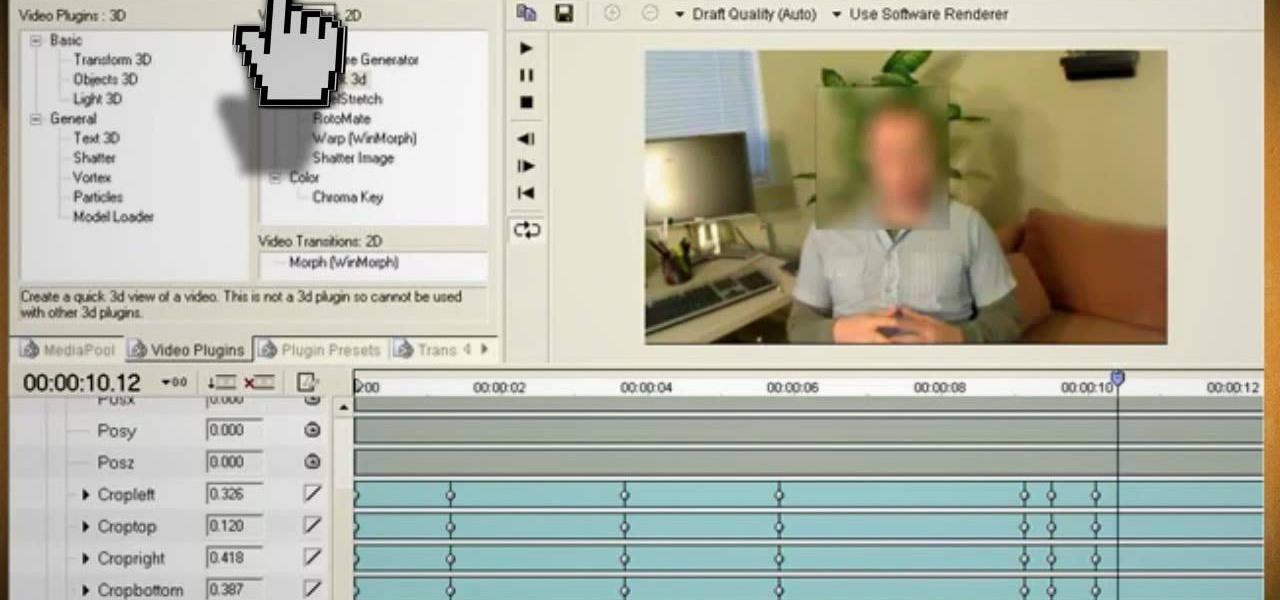
Watch this video and learn how to protect your identity on the internet. This clip will help you learn how to blur out your face and alter your voice when posting videos on the web, where your identity is an important secret. Stay anonymous while portraying your opinions. This software can also be used to avoid release issues with strangers in the backgrounds of your videos. Preventing passers by from having there picture posted with your opinions opening you up for legal action. This can als...

An anonymous sushi chef explains how to make a Volcano Roll. First, he pats down a thin layer of rice over the sliced seaweed. Then, he spreads toasted sesame seeds all over the rice. A layer of salmon is then applied. He then spreads salmon eggs and scallions all over the salmon. Some tempura flakes go over the layer of salmon fish as well. He rolls the entire thing up very tightly to make sure it does not fall apart when eaten. He then deep-fries the entire roll and slices it into even piec...

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...
As Eric Hughes writes in his "A Cypherpunk's Manifesto," privacy, otherwise known as the power to selectively reveal oneself to the world, is necessary for a free and open society. One way to protect your privacy is through anonymous browsing. In this tutorial,

Over the past decade the Internet community has been witness to the rise of many new forms of online interaction. These new technologies have given rise to anonymous networks (like TOR), black markets within the deep web network (like the Silk Road), and even forms of digital currency, or more accurately crypto-currencies, such as Bitcoin. All of these technological advancements have contributed to securing users around the world and protecting their privacy. Therefore it is no surprise that ...

In this video tutorial the maker of the video teaches us how to setup an account for a friend in order for that friend to be able to download whatever they would like from the Playstation store for absolutely free. The video is extremely detailed and even offers a word of caution as the maker begins the process of creating an account for an anonymous friend. This video is extremely informative and very quick to the point. Its not long and drug out and it is a useful video tutorial to watch. O...

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

Isn't it annoying when you want to check your Facebook or MySpace but you are at school and hit a big giant Websense blocker? Well, if you are stuck in a library or somewhere else where there are filters on your surf-ability, check out this tutorial for a useful hack.

Go to web browser, click on tools- under tools click on 'Fire ftp.' Add an account to get into recall server. Under 'MANAGE ACCOUNTS' - click 'Add new one.' In host type 'Recall.(yourserver.)' then click on 'anonymous.' Click 'okay.' Now hit 'Connect.' the ftp server is then going to connect to your remote server. On right side you can see the remote server and it's file structure. Clicking on plus button (+) will expand the file tree structure. At this point you can see all the folders but y...

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Hotels are anonymous and while this is a great thing, you should also be careful about the nameless folks who've used your room before you. Follow this tutorial to make the most of your hotel and ensure a great vacation experience.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

Welcome to the Part 2 of the series 'Cryptocurrency'. It has been late because of some errors, where all I typed was lost.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

It's time to enjoy one of America's longest lasting favorite pastimes. No, not baseball—pranking our friends! With the internet currently overrun with countless pictures and memes of cats, there's no way for your feline-hating friends to surf the web without coming across a kitten or two. But things can get worse for them. Way worse...

How much privacy are you getting as an AT&T customer? With the recent leaks confirming the National Security Agency's surveillance on AT&T users, and the ongoing trial of Jewel v. NSA, it seems not much at all.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.