Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

In this video we learn how to entice more opportunities with feng shui at home. First, find your focus room with an energy map to find the career area. This room is from the front door walking in. Use water, because this is the element for positive career changes. Put a painting of depth that makes you feel like the wall is not right in front of you. Also, add a table with rounded corners and musical instruments or something that you need for your career. This will ensure that you walk into a...

Almost every website on the web has buttons that enable users to interact with it. They are easy to make, but making them interesting and reactive to user's activities is more of a challenge. This video demonstrates how to create animated rollover buttons in Adobe Flash CS4 quickly and easily. Your website will be much more dynamic and enticing if you apply the skills taught in this video.

A friendly blond in a tank top shares several tips to help the average joe video game enthusiast to entice his girlfriend to grab a controller and embrace gaming.

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

Trying to entice new opportunities, or does your entryway just look a little blah? The art of feng shui can help arrange your home to boost your career, or at least make everything look better. Learn how to attract energy to your front door by watching this video interior design and feng shui tutorial.

Learn how to shimmy from this enticing belly dancer. She will show you the basic hip movement and then how to accelerate it to shimmy speed.

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Welcome back, my nascent hackers! Earlier, I wrote a guide on finding operating system and application vulnerabilities in Microsoft's own security bulletins/vulnerability database. In this tutorial, I will demonstrate another invaluable resource for finding vulnerabilities and exploits by using the SecurityFocus database.

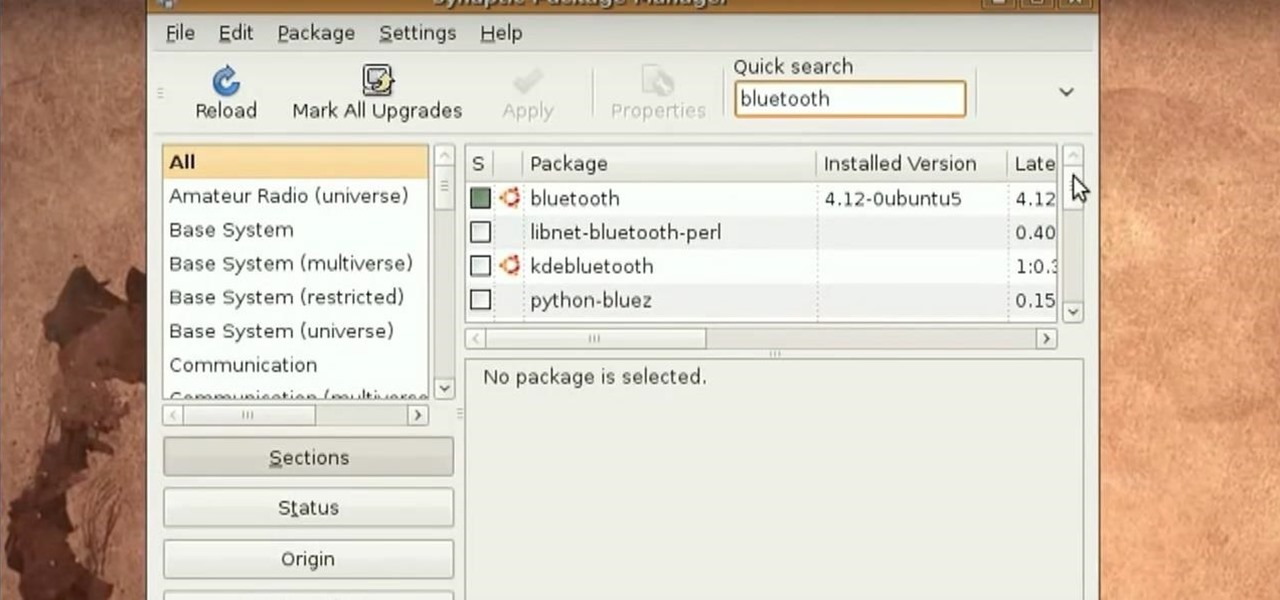
Tinkernut presents the Bluetooth headset hack! This video shows one of the vulnerabilities of some bluetooth headsets. To prevent this vulnerability, it's best to invest a little more money into a more secure headset and making sure your headset is turned off when not in use. You can find all of the links and scripts used in this video, as well as find answers to questions you may have at the link below:

Welcome back, my rookie hackers! Several of you have written me asking about where they can find the latest hacks, exploits, and vulnerabilities. In response, I offer you this first in a series of tutorials on finding hacks, exploits, and vulnerabilities. First up: Microsoft Security Bulletins.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

Bird feeding is something everyone can do. But keeping the birds in your garden can be just as easy. This how to video gives you a few tips that will help you attract the most popular wild species of birds and entice them to stay for more than a quick lunch.

In this how to video, Allyce and Melissa entice you to throw a Panty Party, arming you with a few simple techniques to whip up lots of these sexy undies with your girlfriends. You will see this DIY project 3 minutes in to the video, after the hosts take you to a quilting market.

Ready to clean out the clutter in your home and make a little money too? Learn how to organize a tag sale or garage sale and entice people to stop, look, and buy.

It's always nice getting paid to do something you love. That's why Nintendo is offering all Nintendo Switch owners a chance to find vulnerabilities before another hacker beats them to it first. Depending on the vulnerability you find, Nintendo is willing to shell out rewards starting at $100, all the way to $20,000, to the first bug reporter who uncovers it.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

There's a lot you can do with eggs, but usually cooks use them as ingredients for bigger and better recipes. But in this recipe, the egg takes all the glory! It's called Scotch eggs, and they traditionally consist of a hard-boiled egg, wrapped in sausage and coated with breadcrumbs. Then they're deep-fried and usually served cold.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

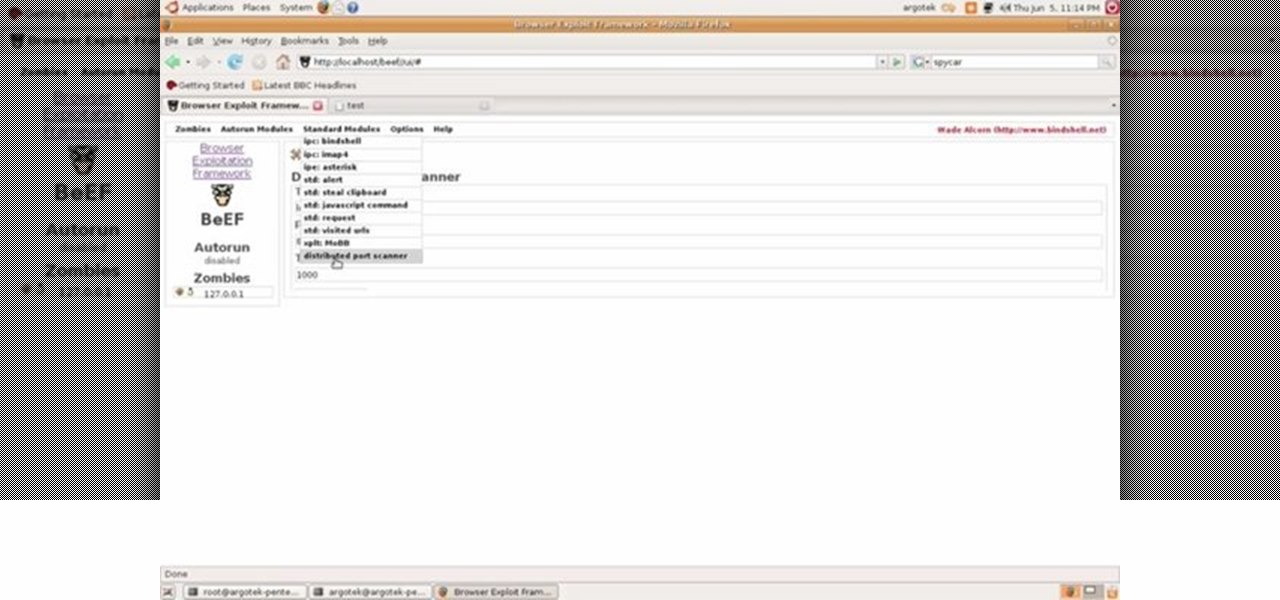
This video tutorial talks about browser exploitation. Particularly, it talks about tools, like BeEF, that can be used to hack known vulnerabilities within browsers and some cool frameworks that you can use to check the security of your own browser. To get started hacking your own browser, watch this how-to.

With chips in four out every five PCs made since 2010, few companies are as pervasive in modern computing as Intel. That's why an advisory released Monday, May 1, confirming a remotely exploitable vulnerability in all non-server business hardware made in the last seven years has sent shockwaves through the technology world.

Welcome back, my hacker novitiates! When we are trying to find vulnerabilities in a website to attack, we need a solid web server vulnerability scanner. Internet-facing web apps can open enormous opportunities for us as they are often riven with vulnerabilities and can often offer an entire point to the internal network and resources.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

In this tutorial video, YouTube user "inteltuts" discusses ways to use Photoshop CS4 to help make better looking product pictures, as a way to attract costumers to your online products. Using a black telephone as an example, he first shows how the opacity, linear dodge, and brush tools can help make a product image look shiner, sleeker and brighter. He goes onto create what he calls "glints", which are subtle reflections and areas of sparkling light that he places across the image. Lastly, he...

Chocolate and cheesecake are wonderful and enticing, but somewhat an uncommon combination. If you want to learn how to make a delightful chocolate cheesecake, follow along with our expert chef as she takes you step-by-step through the process showing you how to make a chocolate cheesecake. She starts with the graham cracker crust, displaying the easy process of making the crust from store bought graham crackers, then moves on to display how to prepare bitter-sweet chocolate for the recipe and...

Hummingbirds are just as pretty as flowers—and a lot more interesting to watch. Here’s how to bring these tiny miracles within view.

No dark makeup here; this how-to video demonstrates a soft look based on the Fairy Godmother in Disney's Cinderella. The cosmetic products used to create this look are MAC's Velvetone Eye Brows, Kryolan Pearl Eye Shadow, Kryolan Cobalt Blue Aqua Color Eye Shadow, Seak & Sky Mineralized Duo, Black-Black Pigment, Stargazer Eye Dust #35, Kryolan Cobalt Blue Aqua Color Eye Shadow, Seak & Sky Mineralized Duo, Black-Black Pigment, Feline Kohl Power Pencil, Fusion Beauty Lash Fusion Mascara, Full Fu...

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

Samsung's 2016 line of smartphones has a new update, at least for the devices on AT&T. The update brings the Galaxy S7 to version G930AUCS4BQL1 and the Galaxy S7 Edge to version G935AUCS4BQL1. Here's what's on the table.

Welcome back, my hacker novitiates! Every so often, a MAJOR vulnerability appears that makes millions of systems vulnerable to attack. The most recent, named Shellshock, basically leaves every Mac OS X, Linux, and UNIX system on the planet vulnerable. As nearly two-thirds of all web servers on planet Earth run one of these operating systems (primarily Linux), that's a whole lot of systems out there waiting to be harvested.

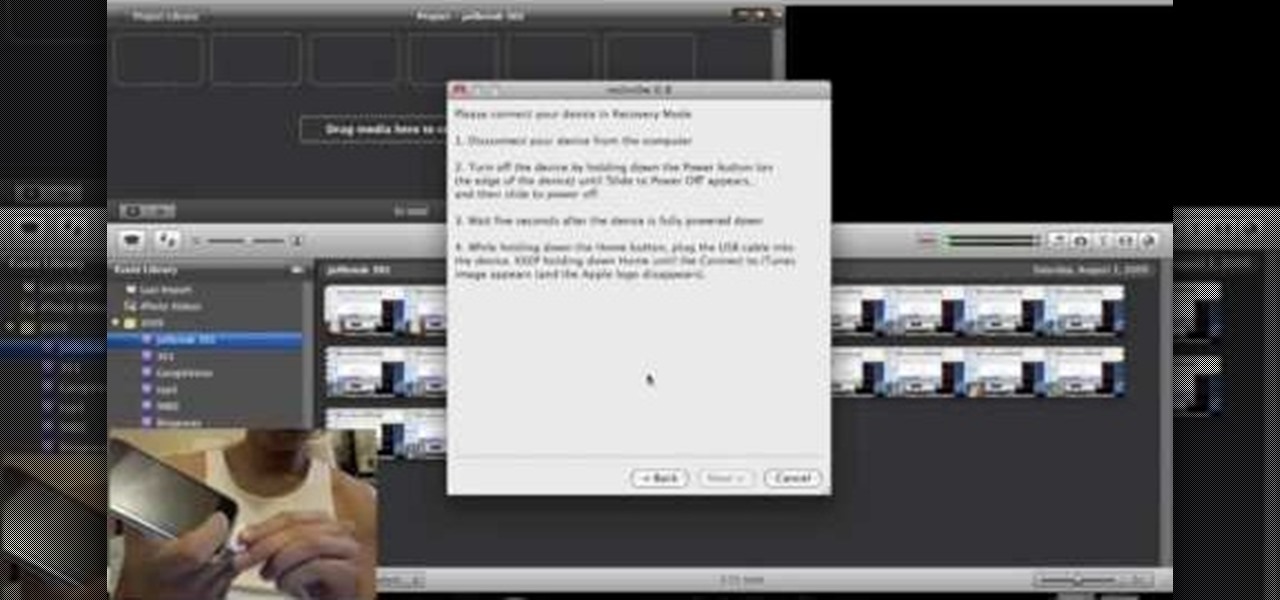
This is a step by step tutorial on how to update and jailbreak/unlock your iPhone on 3.0.1 firmware. The firmware is almost the same as 3.0 except for fixing up the SMS vulnerability. The following files are needed:

Few Bluetooth users realize that Bluetooth headsets can be hacked or otherwise exploited to a remote attacker the ability to record and inject audio through the headset while the device is not in an active call. SANS Institute author and senior instructor Joshua Wright demonstrates, and explains, the security vulnerability in this how-to. For more information, including step-by-step instructions on how you can replicate this hack yourself, take a look.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.