Welcome back, my tenderfoot hackers! Hacker newbies have an inordinate fixation on password cracking. They believe that cracking the password is the only way to gain access to the target account and its privileges. If what we really want is access to a system or other resources, sometimes we can get it without a password. Good examples of this are replay attacks and MitM attacks. Neither requires us to have passwords to have access to the user's resources.
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

The new Call of Duty: Black Ops 2 is the hottest game on the market right now, and there's no doubt it'll end up being the most unwrapped gaming gift come Christmas morning. The first-person shooter hopes to carry on the tradition of its many predecessors in bringing the most action-packed gaming modes, along with a high-replay value, to its legions of fans.

According to Digi-Capital, investors poured $1.8 billion into augmented and virtual reality companies over the last 12 months, including $300 million in the third quarter. These investments are not made without a means to monetize products and services.

Spider-Man Noir, a universe catered to the stealthier, forward thinking Spidey. To get a full 100% play through, you're probably searching for all the hidden spider tokens. If you're lost or confused, this great video will give you a complete walkthrough of every location along with great commentary to help if you get confused on specific areas.
Spider-Man 2099, one of the four dimensions in Spider-Man: Shattered Dimensions, and quite possibly one of the coolest! If you're going for a full 100% completion of the game, you're going to want to get all the hidden spiders. In this video you will get a full walkthrough of each location in the Doctor Octopus level, where you will find the spider tokens as well as a great commentary for each area where you might be confused.

The dreidel, the small top that's among the most recognizable symbols of the Hanukkah season, is a fun game of chance to play with friends and family.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

At its core, Valentine's Day is about love, the act of loving, and harmony. So it only makes sense to give your amor a heart-shaped token of your affection this Valentine's Day.

One of the main reasons Authy was able to top our list of the best two-factor authentications apps was its ability to transfer access to a new device. This feature ensures that whenever you get a new phone, you don't lose all your tokens. However, if the process is done incorrectly, you can leave your account vulnerable.

Waste your quarters (or tokens) no more after you watch this video from Brainiac. Learn how to beat the system and win at those stuffed animal crane games.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

MetaRL is a site you can sign up with that will let you accrue points that you can cash in for free online currency in your favorite online game. It's a very secure and perfectly legal way to get game currency without having to hack your games.

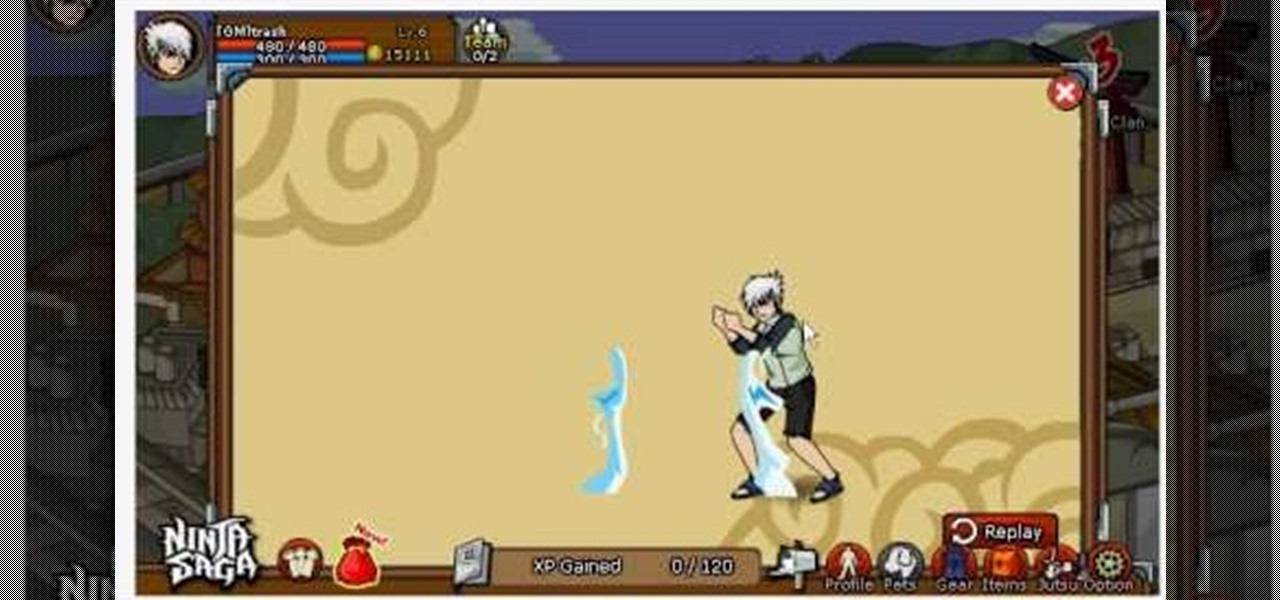
Here's a way to hack Ninja Saga to increase all your skills to be precisely where you want them to be! You'll need to be running the game in Firefox, and have the latest version of Cheat Engine downloaded on your computer.

Give her a Valentine's Day gift that will last forever by making this romantic red, pink, and white polymer clay Valentine's Day heart shaped cake.

Talk about taking the adage "count your lucky stars" literally. This video demonstrates the birth and making of origami lucky stars, also known by their street name, puffy stars.

What's the meaning of life? That's the age-old question; but can it ever really be answered? I mean, isn't life just a big game anyway? Perhaps, a game of inches?

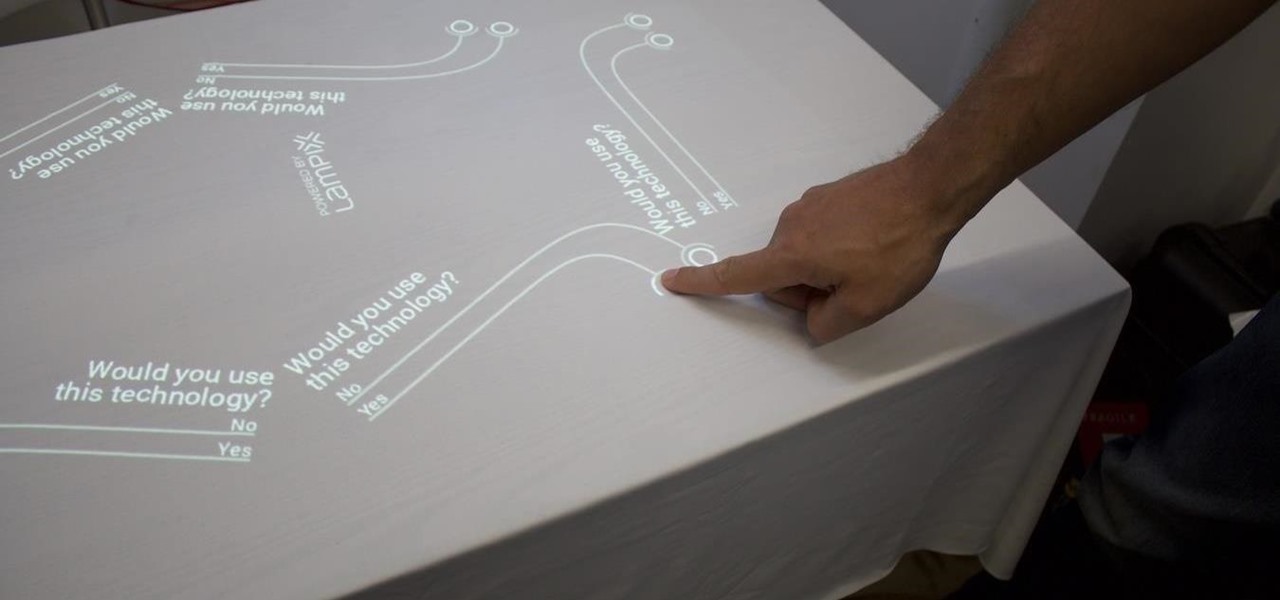
Over the past week, companies took a variety of approaches to investing in augmented reality. Lampix is backing its own effort to build an ecosystem for augmented reality platforms. Nokia and Xiaomi are teaming up on numerous fronts, potentially including augmented reality.

Want more credits, tokens, gold coins or other forms of virutal currency that you use and trade in your online games? MetaRL is a site that can help you get more currency for these games, and it's free to sign up. This tutorials shows you how to use it.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

The newer Graph Search in Facebook can help you find friends in specific cities, photos of a particular subject, restaurants that your friends liked, and a whole lot more. One thing it can't help you with just yet is searching public posts on Facebook, which you could do in the previous search version. Actually, some users do have the option to search public posts with Graph Search, but it's very limited and doesn't include me. If you're like me and don't have access yet, there is a workaroun...

Nearly two years ago, Peter Chou, CEO of HTC, confirmed that the company would no longer be locking bootloaders. Whether or not they've actually lived up to this claim is debatable. Any phone bought from a wireless carrier comes locked. Only the new HTC One Developer Edition ships with an unlocked bootloader, and it does not have any carrier add-on software installed.

Phish bone keychains feature a highlighted midsection with three different colors of hemp (in this video we use regular rafia-colored hemp, red hemp, and green hemp) that surround wooden beads.

Dove cookies make such great treats to give to friends and family. Doves are traditionally representative of peace and healing, and so sharing doves (albeit in cookie form) with those you love shows that you care for their well being.

When OnePlus announced their partnership with T-Mobile and the deal the magenta carrier is set to offer, mouths dropped. But as usual, this deal comes with some caveats. The bulk of these will hurt the folks who love to root, something a large portion of the OnePlus community enjoys doing.

Motorola launched a new webpage on Friday that tells Android users how to unlock the bootloaders on a limited number of new Motorola smartphones and tablets. This new 'Unlock My Device' page helps demystify the process and make it easier for users to customize their phones.

If you're having slot problems in your casino, you're going to have to do some troubleshooting. Knowing all there is to know about slots is important for any casino or slot machine owner. This video will show you the trick to installing a coin into a coin comparator. One thing to remember, is that if there is no coin inside the comparitor, the machine will not work. And no matter what coin kind you have in the hopper, whether quarter, nickel, token, etc., it has to be the same coin inside the...

This week, two companies looking to capitalize on the growing augmented reality industry, raised funding from starkly different sources.

The fortunes of ARKit and ARCore are still in the hands of developers, who have been increasing the number of mobile augmented reality apps on the market, but perhaps not as fast as companies like Apple might have expected. But one new product is looking to literally kickstart mobile AR gaming by introducing a few key components that harness the traditional board game model.

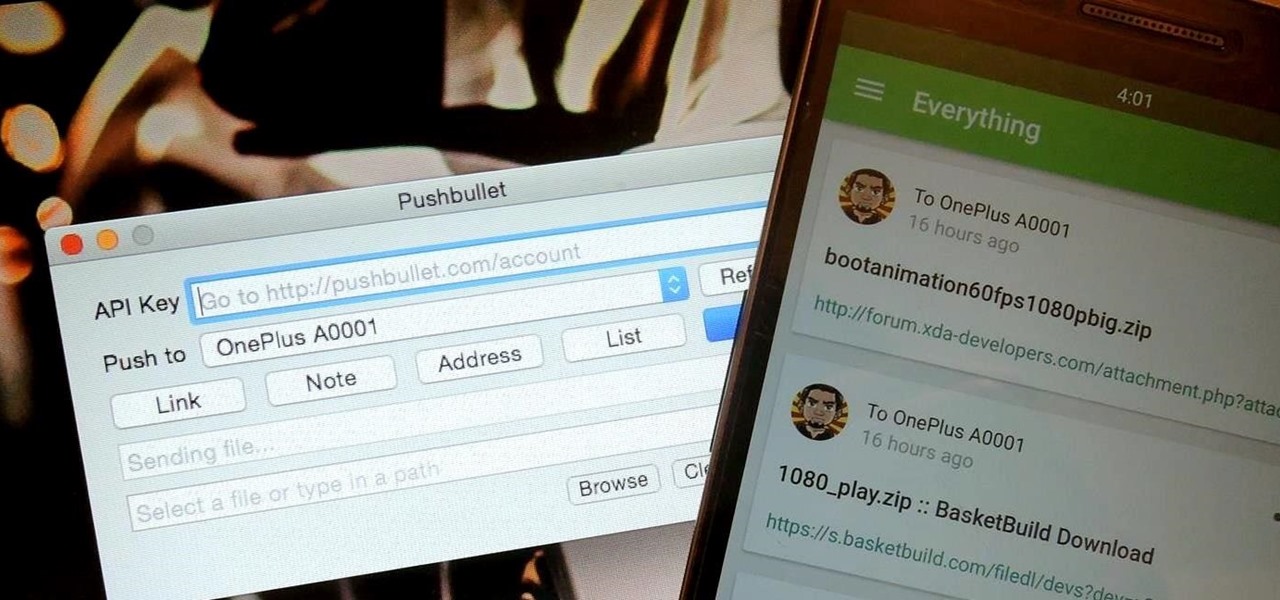
Before Continuity and Handoff were even announced, Pushbullet was already allowing users to quickly send notes, links, and photos between their devices with a few clicks.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

As with most OEMs, HTC would like you to think that you can do virtually anything with your new HTC One M8, but as a softModder, you know that isn't true. To actually unleash the full potential of that device, you need access to the whole system, not just the parts that HTC deems okay for you to mess with.

With the new screening protocols and their full body x-ray scanners, the TSA is taking constant criticism from unhappy travelers. Between the nude images the scanner produces and the awkward pat downs, air travel will never be the same. That's why it's important to make sure you're prepared for your flight and the TSA security checkpoints.

French tips are timelessly elegant for a reason: they're simple, very minimal and understated, and very feminine without being overdone. But sometimes doing the same white French tips over and over again gets a little dull.

In this tutorial, Nancy goes over the star tip. The star tip is the most popular tip used for cake and cookie decorating. This tip is fantastic for beginners and can look like stars, flowers and also be used to fill in colors for other designs. Follow along with Nancy for fabulous tips and design ideas.

In this soldering tip video brought to you by BEST, Inc. Norman Mier explains how to converting a lead solder tip to a tip that will be utilized for lead-free soldering.

Learn how to frost a cupcake using a 1M tip or large tip. The supplies you'll need are cupcakes and a bag with the frosting and the tip. First, squeeze the bag to remove any air bubbles. Take your cupcake in your hand and start at the outside and work your way in. Then, in one motion, go over the first layer to create a stacked second layer of icing. This method gives you a pretty ice cream cone type effect on your cupcakes. Next, you'll learn how to make your cupcakes look like roses. Using ...

Decorating Tips demonstrates how to use the star tip to decorate a cake or cookies. Use a medium consistency icing and position the bag at a 90 degree angle. Hold the tip 1/4 of an inch above the surface of the cake or cookie. Use the count squeeze, stop squeezing and stop to create a delicate star look with a size #13 star tip. With a size #18 star tip, shorten the count and put the icing stars right next to each other to fill in a cake. Use different colored icings as accents. You can also ...