Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

Want to disguise your URLs so that they appear suspicious? In the style of websites such as Tiny URL that take your original URL and give you a shortened one to post on your blog or twitter feed, Shady URL takes your original URL and gives you one that might convince people not to click it. Go to Shady URL and paste the URL you wish to disguise. Click submit, and on the next page it will give you a URL that looks, well, shady. It might include something about a mail order bride or an investme...

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

If you suspect that there may be something wrong with the fuel pump on your Saturn car, you should make sure you have proper voltage in the connector in your trunk. If you do, the next step is to check the ground.

Suspicious of the pumpkin pie filling you can find in the store? Just feeling ambitious and want to try to make your own filling? Here's how you can bake a traditional pumpkin pie using real pumpkins. Make sure you get the right kind of pumpkins!

If you've beaten Year 1 - The Sorcerer's Stone of LEGO Harry Potter: Years 1-4 on the Xbox 360, then get ready for the LEGO-ized version of J. K. Rowling's second masterpiece, Year 2 - The Chamber of Secrets. Get every single achievement, every single collectible… everything you can imagine. All the videos and levels are listed below.

Want music now? Not keen on downloading software or suspicious files to get it? This is a handy media trick from Tinkernut on how to torrent audio files without downloads. Stream music torrents without having to download any torrent software using Bitlet.org .

Steer clear from empty flattery and malicious social engineering with these tips on how to avoid a player.

In this video tutorial, viewers learn how to locate and remove spam accounts from a WordPress blog. Begin by logging on your blog and select the User tab. Search through the user list and look for suspicious email accounts. Some keys that reveal spam accounts are: emails that have .ru, poker, Viagra, pharmacy and accounts with more then one dot. Use your common sense to find spam accounts. Select the account you want to delete. Select Delete and click on Apply. This video tutorial will benefi...

Skin Cancer Expert Dr. Coyle Connolly, D.O., does a full body check up on patient to detect if there are any new or existing moles or suspicious lesions that could be precancerous or cancerous.

Think Indian Jones when you play this mission on The Saboteur for the Xbox 360. The sixteenth mission in Act 1: Viva Le Vengeance is when you need to head into the church to drop off the chest, which seems to contain the suitcase from Pulp Fiction. Time for the dramatic climax of Act 1.

All Things Come to He Who Waits: After parting ways with Leonardo, break into the walled-off area to the northeast and trigger this mission via a waypoint on the parapet walk. After the cut scene, you need to trail a courier that zigs a zagging path through the city. Stay far enough behind him that he doesn't get curious, but also be sure to keep him in your sights. If he gets separated from you by a wall, a countdown timer hurries you to catch back up.

Learn how to crash a wedding. If you have a free Saturday, we have a way for you to score free food, free cocktails, free dancing—and maybe even a hook-up.

The Climbup Insect Interceptor is a new monitor for the use of detecting bed bugs. This is a new monitor. It's a passive monitor. You can place the monitors underneath one of the legs of a sofa or bed or other suspicious piece of furniture. This will not rid your home of bed bugs. This is a way of letting you know where the infestation is or isn't. It is a monitor, but it does not control them. Once the bugs fall into the trap, they can't get out. You will need to properly dispose of them, af...

In this Education video tutorial you will learn how to avoid wrong answers on the SAT critical reading area. Five principles to keep in mind are rephrase the question and predict the answer, answer the question being asked, find evidence in the passage, extreme answers are suspicious and finally remember a little wrong is all wrong. To rephrase the question, read 2 lines before and after, ask the question in your own words and find the answer choice that best matches your prediction. Now comi...

SomeFamousProduction here has come with a new avatar of James Bond on Xbox. First we start off with his hair. Well, we need to keep it simple, yet spy-like and somewhat blackish in color, not too light, neither too dark. Next we move to the chin or jaw. Keep it sharp but not protruding. Lips can be curvy but not too fancy, because James Bond seldom smiles. The nose can be a bit tapering at the end, again not too fancy and loud, more spy-like if you ask me. Next are the eyebrows, you can keep ...

Ever wanted to know how to smell good naturally with natural elements? You can save the earth without offending those around you when you go au natural.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

T-Mobile's credit-checking system was recently hacked, and this one is about as bad as it gets. The names of 15 million customers, their date of birth and social security number, as well as driver's license numbers and additional information was illegally accessed, meaning the potential for identity theft here is huge.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

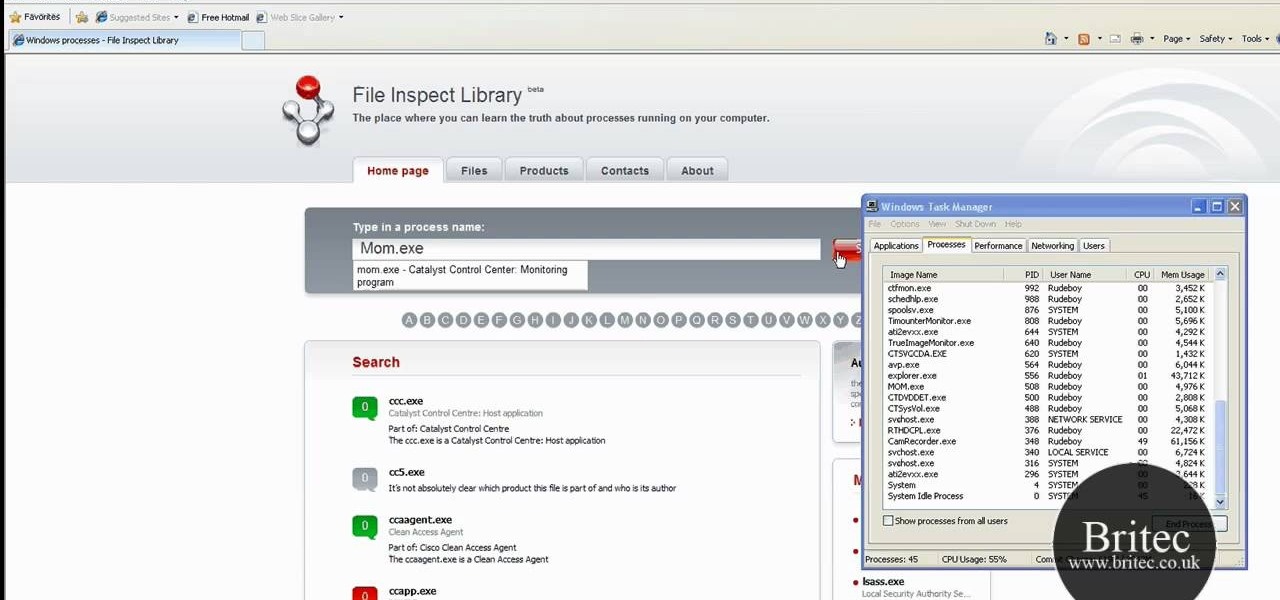
Need help figuring out what a suspicious process is up to on your Microsoft Windows PC? With FileInspect, it's easy to figure out whether a given process is benign or malicious. So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For complete details, including step-by-step instructions, watch this video guide.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

Earlier last week, there were a number of fake five-star WhatsApp reviews to be found on the Google Play Store. Now, Gmail, Chrome, Messenger, and Firefox are all the latest victims to be saturated in five-star spam that wrongly refers to the word "game" in reference to non-game apps.

Unless you've been living under a rock or ignoring recent news headlines, Ashley Madison, the dating site for married people (or individuals in a committed relationship) has recently been hacked. Millions of their users are shitting their pants, and for good reason, as all of those accounts have just been leaked.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

A recent security risk exposed by software engineer Szymon Sidor has raised a few eyebrows amongst the Android community.

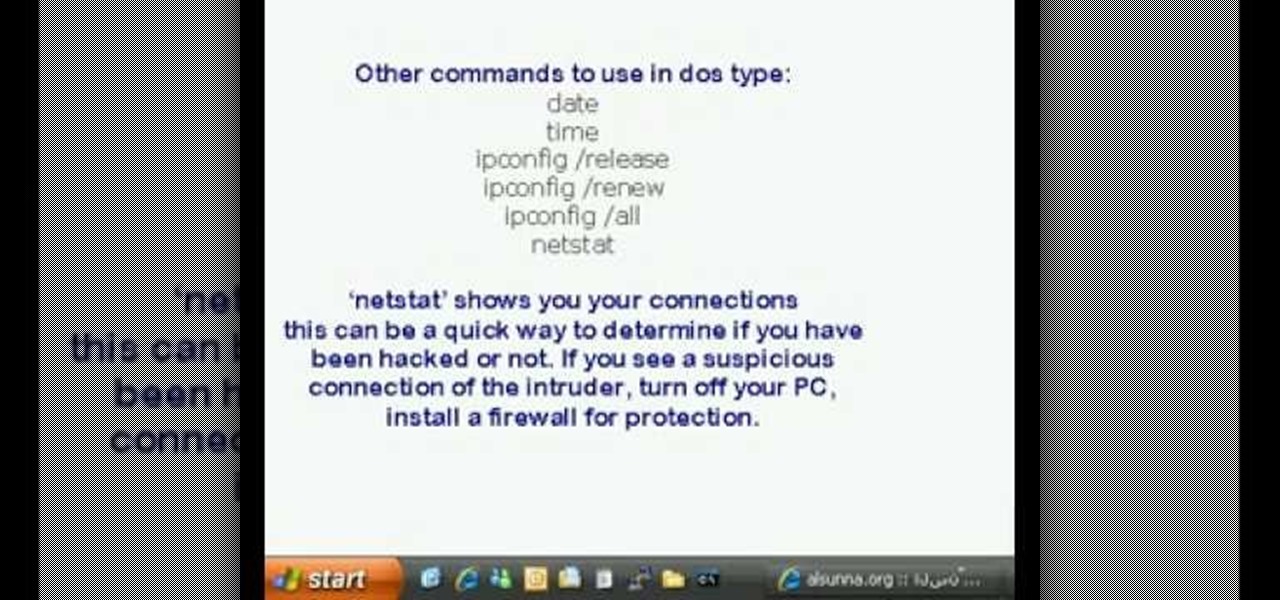
This is a video tutorial in the Computers & Programming category where you are going to learn how to find and ping your IP address. Go to start > run and type in "cmd" to get the DOS window. Here type in "ipconfig" and hit enter. If you are online, your IP address will be displayed. If you are offline, go online and try again. Then in DOS type in "ping yahoo.com". This is to see if you can connect to Yahoo. If you are online, the site will reply 4 times. If you type in "netstat", it shows yo...

The USB Rubber Ducky is a famous attack tool that looks like a USB flash drive but acts like a keyboard when plugged into any unlocked device. The Ducky Script language used to control it is simple and powerful, and it works with Arduino and can run on boards like the ultra-cheap Digispark board.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.