Whether you've got an itch for a mini-flamethrower, a shower of burning sparks, or a exploding ball of flames, these little fireworks-producing lighters may be the answer to your pyrotechnic cravings!
Apple's new iOS 16 software update is finally here, and there are over 350 new features and changes for you to enjoy on your iPhone. There are major lock screen and home screen improvements, a pleasant surprise for the Contacts app, and tons of new upgrades to Safari, Mail, Messages, and more.

Most of us skip through documents like privacy policies and EULAs (end-user license agreements) because they're long and boring. But, as Congress just passed the SJR34 bill in early April, you're probably a little concerned about your personal data, so we summarized the privacy policies for major ISPs and mobile carriers in the US.

If you're always taking blurry and underexposed pics with your mobile device, try using some of the tips below to turn your phone into a valuable photography asset. It doesn't matter if you have an iPhone, Android smartphone, or even a first-gen camera phone... you can still take some beautiful, winning photographs.

Increasingly, cutting-edge platforms like blockchain technology and augmented reality are overlapping, forging new digital frontiers that promise to change the way we interact with the virtual and the real world.
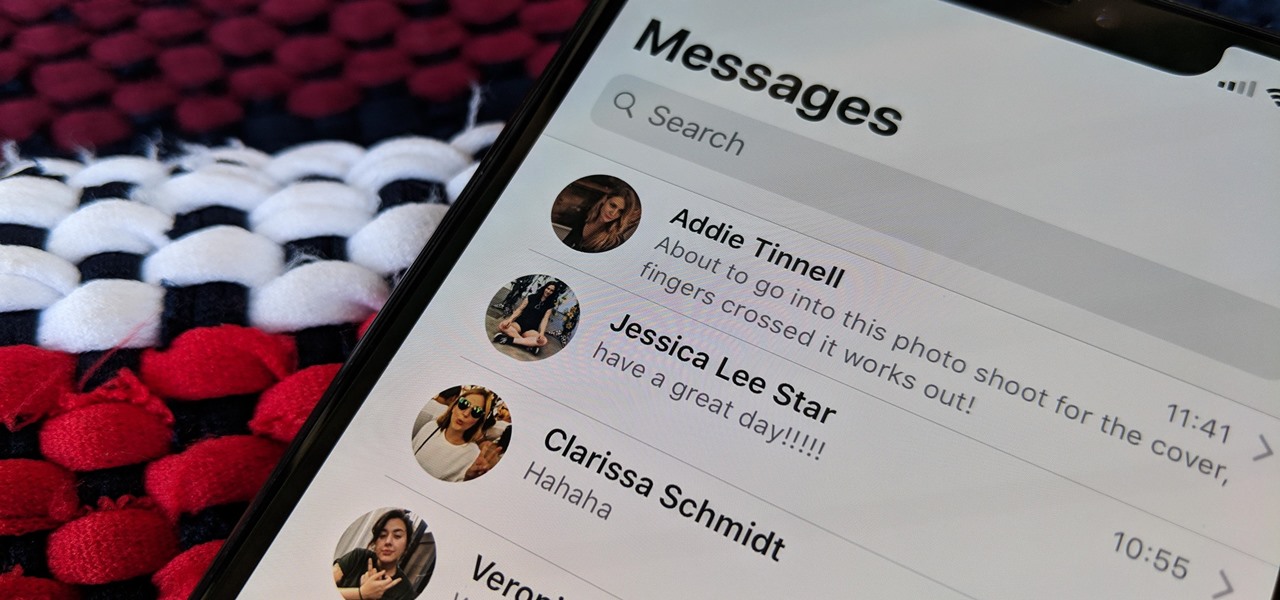
The Messages app on iOS features contact photos for every one of your conversations — including group chats. Even if you don't have a picture for a specific contact, their initials will appear instead. For non-contacts, a generic profile avatar appears. These give threads a bit of flare, but if you're looking for extra privacy or don't enjoy the look, you can easily hide those images and icons.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

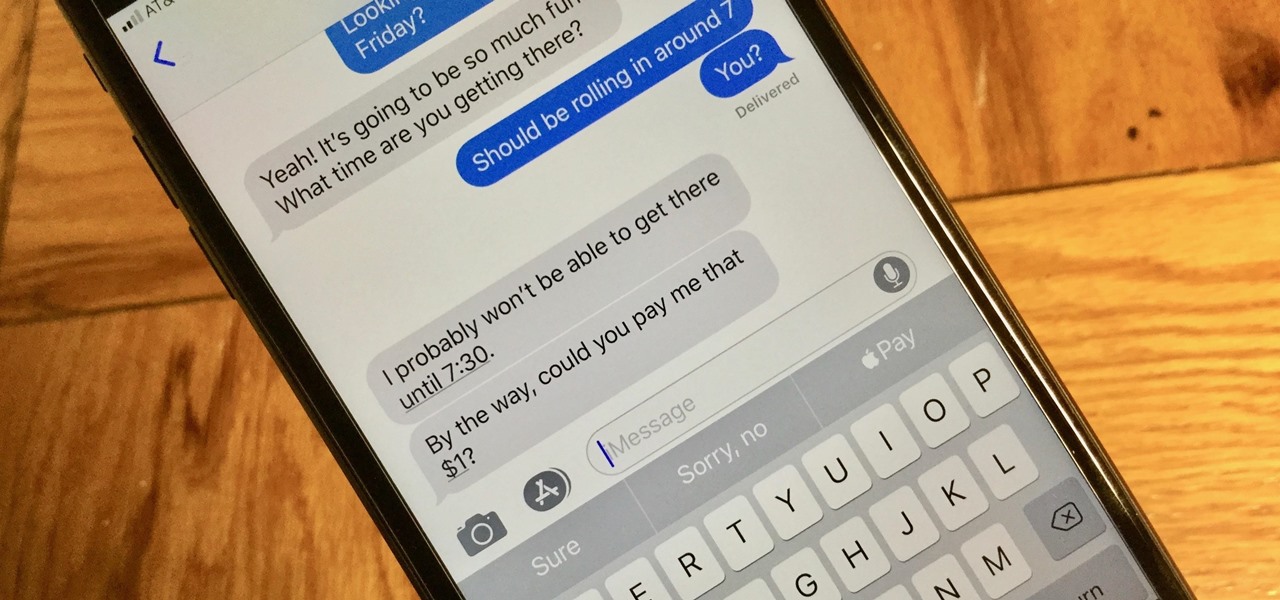
With Apple Pay Cash, you can easily and securely pay your contacts directly in your iPhone's Messages app. While you can always use the normal method of paying someone with Apple Pay Cash, there's actually a faster way, as long as your contact asks you for money in an iMessage.

While unveiling various other gadgets, Google announced the Pixel Buds at their October 4th event in San Francisco. These wireless earbud-style headphones are particularly interesting thanks to their ability to offer real-time language translation via Google Translate when paired with a Pixel 2 or Pixel 2 XL.

Everyone feels a little safer with Android's security updates, which are welcome and often necessary protective measures. But what happens when the update that's supposed to safeguard your phone actually ends up wreaking havoc with its security system?

Although I love a good kitchen gadget just as much as the next food writer, the truth is that my drawers are bursting with unused tools. I usually like to take the simpler approach to cooking and prepping, and for everyday cooking, I find that the best gadgets are usually the ones that do more than one thing.

Thanks to a couple of photoshopped images that made rounds across Twitter last year, iPhone users were duped into thinking that iOS 8 included a security feature that would lock individual apps. Of course, none of it ended up being true, but we covered other features and apps that could accomplish roughly the same thing.

In the wake of the NSA scandal and celebrity-photo hacks, lots of people scrambled to find more-secure ways to send text messages, share emails, and surf the internet. Known for their incredibly secure data networks, Germany's email services saw a remarkable increase in new users from across the world. Last year, we covered Sicher, a German app that lets you send and receive encrypted self-destructing messages on your smartphone.

I love cheap, nutritious food: lentils, rice, toor dal, and other beans and grains. Even popcorn. The only problem is that they usually come in floppy plastic bags that make measuring ingredients more difficult. I usually open up one corner of the bag only to have everything come spilling out all at once whenever I try to pour out measured amounts.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

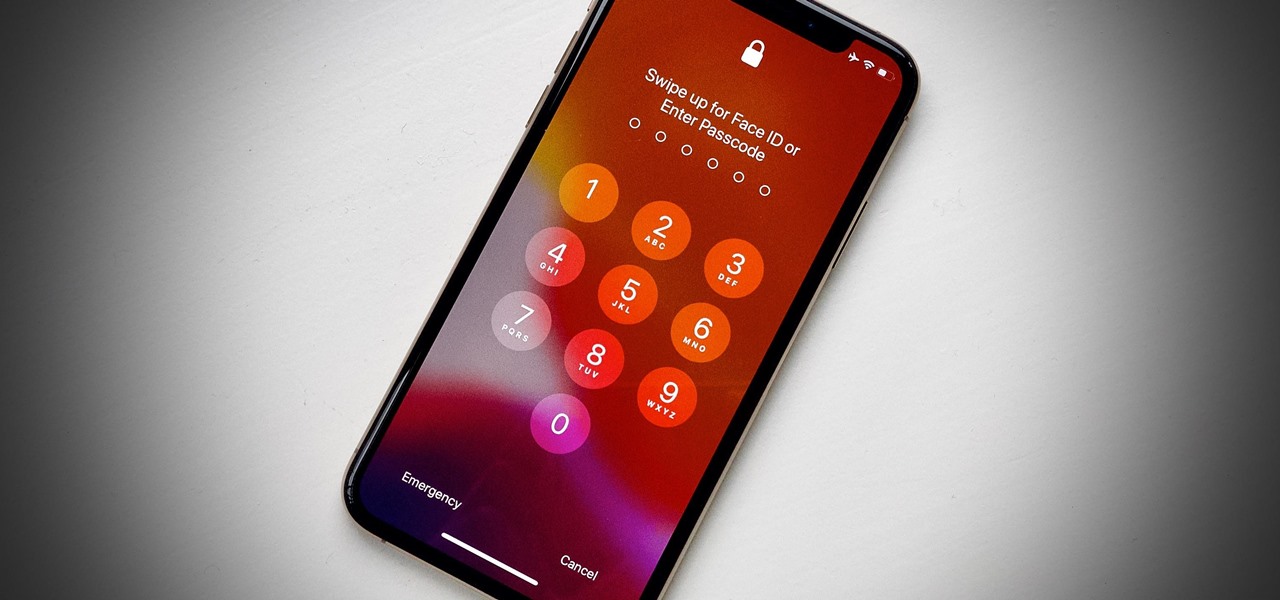
The lockout feature in iOS 7, which securely locks your device after a few incorrect passcode entries, can be a real pain in the ass sometimes.

The high limit thermostat can be found in gas and electric dryers and serves as a safety feature that helps to prevent the dryer from becoming too hot when it’s running. The thermostat is designed to shut off power to the dryer’s heater when the dryer vent is blocked or clogged. The high limit thermostat on your dryer is something that does need to be replaced from time to time. Fortunately, it is a job that you can do on your own with basic tools.

If you're one of the many professionals transitioning to working from home amidst the current pandemic, there's a good chance you're now realizing how far behind your at-home setup is compared to what you had at the office.

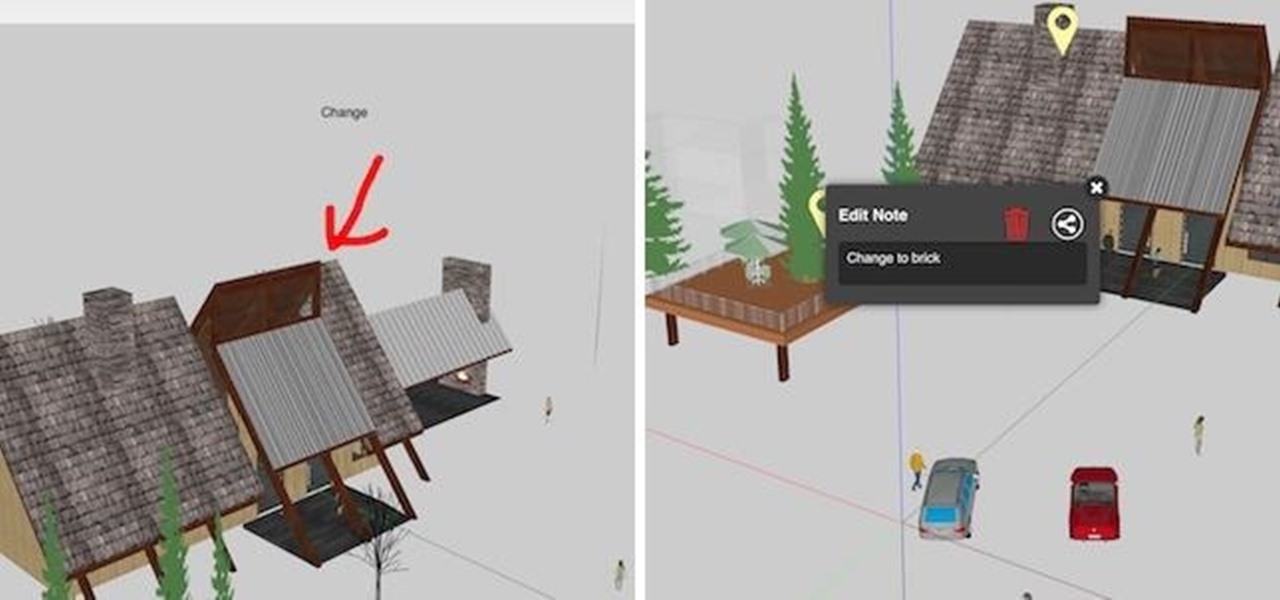
To revise a line from the Blues Brothers, when it comes to ARKit apps, we've got both kinds — home utilities and games. As such, two more candidates for each category have made their way to the app store.

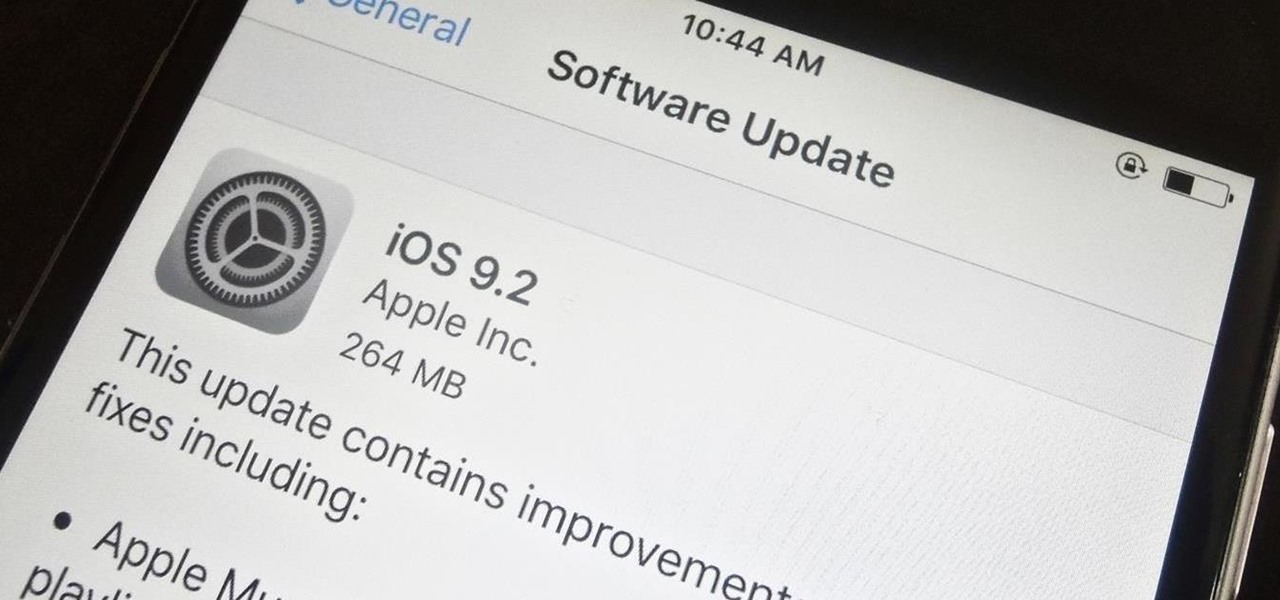
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

Samsung's Galaxy series of devices have one common design theme that ties them all together—the physical home button at the bottom of the phone. This button can wake the phone, take you to your home screen, and even scan your fingerprint to securely unlock your device.

Both bObsweep Standard and Pethair models have two bumper sensors inside their covers. Whenever Bob runs into an obstacle, the sensors tell Bob to back away.

Everybody loves the stars. Well, I certainly do. As a child I'd spend hours outside during summer nights marveling at the seemingly endless amount of sparkling dots spanning the sky. Maybe you have children of your own and want to create a sparkle in their eyes, or in your own. This tutorial will provide a basic method of bringing the stars inside—at least, in part.

Greasy fast food. Snacks. Candy. Empty stomachs. What do these all have in common? They're all things that people commonly have for lunch during the week, because it beats the hassle of having to plan, make, and pack lunches before their workday.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

More and more devices are using iOS 8 over iOS 7, and that means more and more developers are adding iOS 8-friendly features to their apps, especially widgets. However, not every widget available for your Notification Center right now is awesome. Take for example the Dropbox widget—it's essentially nothing more than a real-time notification, as the only action it performs is opening a recently updated file within the app.

Salad greens are a staple in my house and for good reason: they're cheap, nutritious, and work as a base or an accompaniment for almost all meals. However, it's all too easy to forget about them and then pull out a bag filled with sludgy dark goo or yellow, inedible leaves.

Whether it's embarrassing pictures and videos on your smartphone, or files you just don't want anyone reading, there are plenty of ways to hide them. For most devices, that means installing third-party apps like Gallery Plus - Hide Pictures, Sectos - Photo & Video Vault, TimeLock, or Hi App Lock.

Although it's always been important to safeguard your data and private information in the digital age, privacy has recently taken on an entirely new meaning.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

Since Apple launched iOS 13, we've seen four major updates for iPhone, each of which added some cool new features. Between iOS 13.1, 13.2, 13.3, 13.4, and all the minor updates in between, there's never been a better time to be on iOS. And now, we've got even more positive changes with the iOS 13.5 update.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

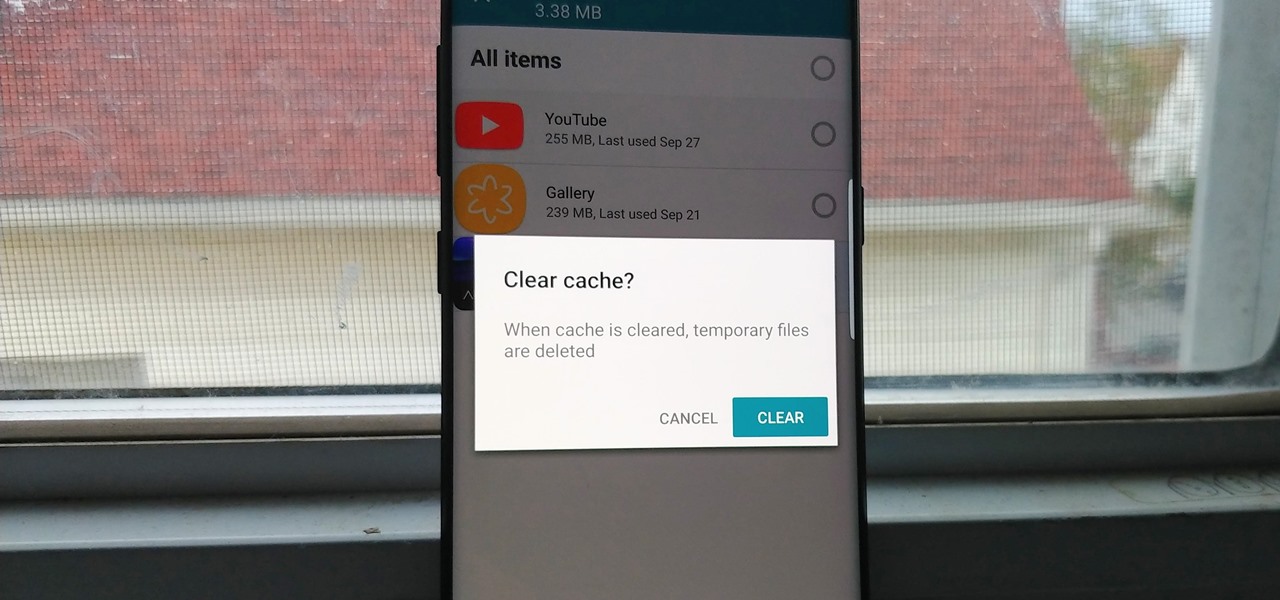
Since the release of the T-Mobile G1, the Play Store has been flooded with apps that claim to improve performance by clearing cache and storage. These apps are typically useless, rarely providing more than a temporary fix which Android undoes immediately. As Android has continued to improve cache and storage management, such apps have become more trivial. However, there are few decent ones out there.

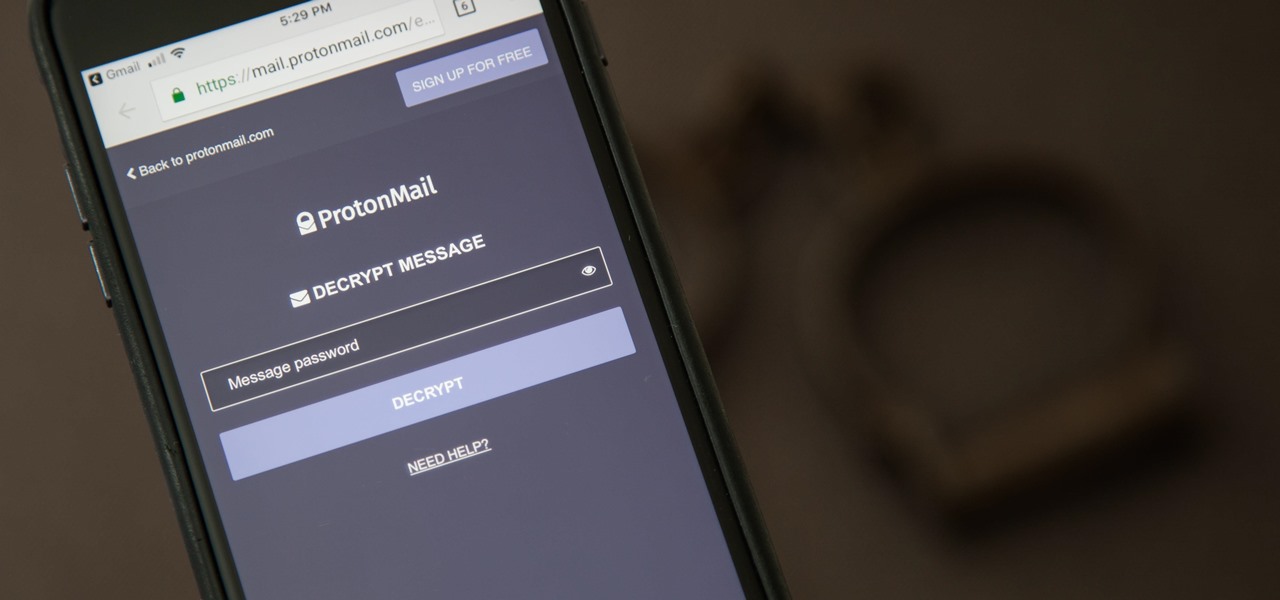
It can be hard to get all of your friends, family, coworkers, and acquaintances to jump on board with the more-secure email system ProtonMail, but that doesn't mean you can't still send them encrypted emails. Best of all, they won't even have to install any other apps or extensions to read or reply to the messages.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Last month, it was revealed that Juniper Networks' routers/firewalls were hacked. It was reported that a backdoor was implanted in the operating system of their routers/firewalls and that attackers could listen in on all encrypted communication. There are now fears that all confidential communications by U.S. government agencies and officials could have been compromised over the last three years.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

The bumper for bObsweep Pethair and Standard are installed the same way. It holds the sensors that allow Bob to see any obstacles in his path. If a repair of the wall detection sensors is needed, the steps for replacing the whole bumper are the same when working on either bObsweep model.

I'm not admitting to anything, but let's be honest, most of us download content on the Web from time to time. With copyright holders laying down the law more and more often, it can't hurt to do so with caution. And even if you aren't downloading copyrighted material, you still don't want companies snooping in on your online activities. So just how do you protect yourself when torrenting? Avoid "Open Communities"