
News: Worrisome Outbreak of Mumps Spreads in Colorado
Officials in Colorado are concerned as 61 cases of the mumps were reported so far this year, a significant increase in the prevalence of the contagious disease in the state.


Officials in Colorado are concerned as 61 cases of the mumps were reported so far this year, a significant increase in the prevalence of the contagious disease in the state.

For a long time, Apple has kept the upper hand on Android as far as app revenue is concerned. However, this tradition looks likely to change this year, as Android's app sales are expected to surpass Apple's.

A market research report, posted on February 27, 2017, forecasts that the image recognition market will grow to nearly $40 billion worldwide by 2021. The market, which includes augmented reality applications, hardware, and technology, generated an estimated $15.95 billion in 2016. The report estimates the market to grow by a compound annual growth rate of 19.5% over the next five years.

Android's stock battery menu is pretty decent. You can see which apps have been using the most power, and you can tell when your CPU was awake or asleep, among other things. But a lot of times, battery-sucking services will get lumped under the generic "Android System" header, and even though you can see when your CPU was awake, you can't exactly see why.

As we get closer to the release of the iPhone 7 this September, more and more details are emerging about the features the new smartphone could have. The well-regarded analyst Ming Chi-Kuo of KGI Securities, who has an uncanny ability to predict new Apple features, has reported another detail involving a dual-lens camera on the upcoming iPhone 7 Plus model.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.
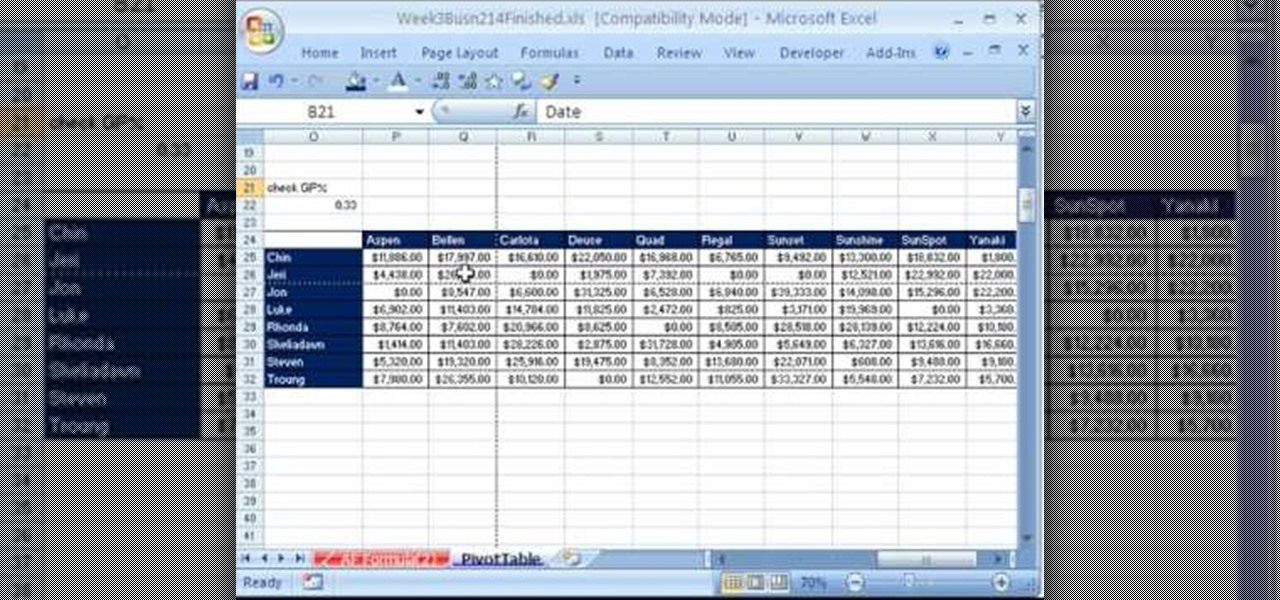
Whether you're interested in learning Microsoft Excel from the bottom up or just looking to pick up a few tips and tricks, you've come to the right place. In this tutorial from everyone's favorite digital spreadsheet guru, ExcelIsFun, the nth installment in his "Highline Excel Class" series of free video Excel lessons, you'll learn how to create and work with pivot tables (PivotTables) in Microsoft Office Excel. Specifically, this video covers the following topics and examples:
This subtle trick will lengthen your school report without your having to write a single extra word. Learn how to extend the length of your papers with this simple video. You will need a paper and flexible ethics. The trick is to enlarge the font of all the periods in your paper! Fact: If you have a 16 page, 12 point paper, changing the periods to 14-point will stretch the paper to 19 pages!

Want to run Apple's popular word-processing application, Pages, on an iPad? It's easy. That didn't stop Apple from producing this clean video overview, however. Get started creating, editing and sharing your own newsletters, reports, flyers & other documents with this how-to.

A new profile on Apple's exiting design chief Jony Ive, the man behind many of the company's most successful products, paints a fuller picture of what led to his departure.
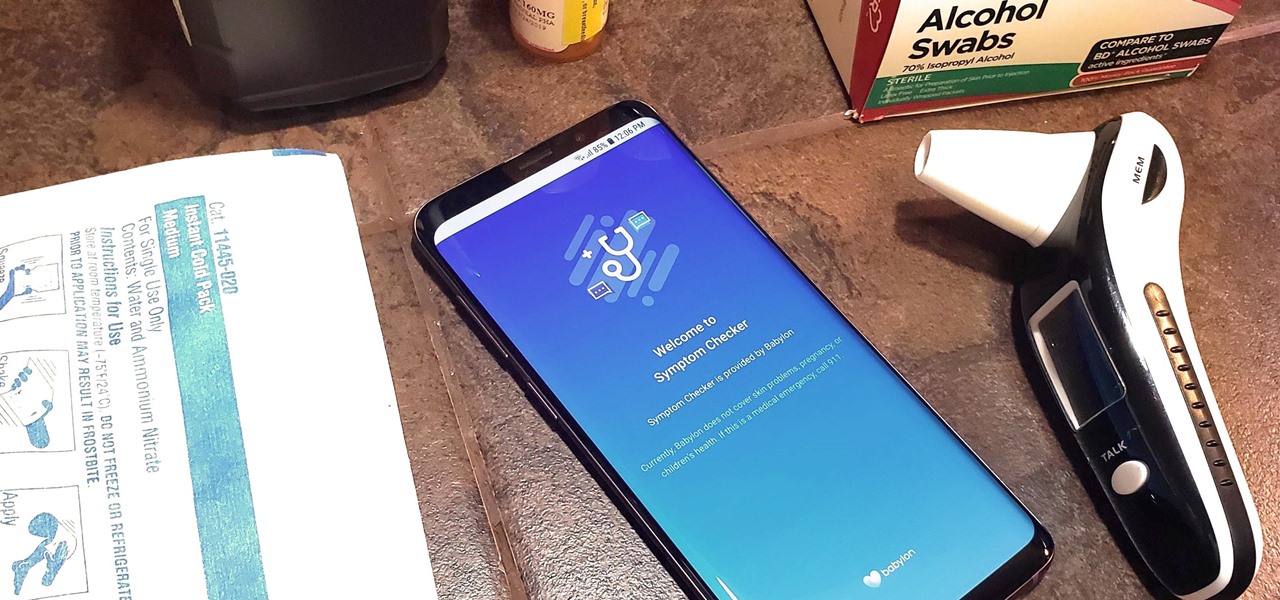
You really can't go wrong with Samsung Health when it comes to staying on top of fitness-related data. Its features help you keep track of workouts, track calorie and nutrition intake, and monitor your heart rate, just to name a few. And if you start exhibiting symptoms you've never had before, you can even use the app to find out more about what's wrong with you.

The legal travails of Magic Leap appear to have no end in sight, as a lawsuit filed by an ex-employee further threatens to dampen the startup's 2018 launch.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Recently released accident reports by the state of California's Department of Motor Vehicles show humans did a lot of dumb things to cause accidents with General Motors' (GM) Cruise Automation driverless vehicles in San Francisco this year.

The National Transportation Safety Board (NTSB) said it is still investigating the circumstances of a fatal Tesla crash last year to determine if the car or Tesla's Autopilot driverless system was at fault, but revealed more details about the circumstances of the crash.

You know, I was actually starting to get comfortable with the idea of the iPhone 8 not showing up until next year. As an Apple fan, I made my peace with it. "There's a lot coming in this model," I told myself. "It does make sense that this many features could cause delays." I was fine. But then ...

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

Welcome to the maiden voyage of our new Market Reality column. Each Friday, NextReality will give you a roundup of news briefs from the financial end of the augmented and mixed reality industry. We'll cover funding news, market analysis, and more.
Starting in October, many Nexus 6P users have been experiencing a bug that causes their phone to completely shut down, even though there was 20% or more battery life remaining. At first, it was thought to be a direct result of the recent Android Nougat update, but a combination of factors indicate that this isn't necessarily the case—or, at least, it's not the only problem.
In recent weeks, thousands of Nexus 6P users have reported that their devices are shutting down with 30% or more battery life remaining. The phones won't start back up until they're plugged into a charger, so it's as if the battery completely dies even though there is plenty of juice left.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.
In this tutorial, we learn how to speak English: Imperatives or reporting verbs. Imperative sentences are sentences like "open it!", where you are asking someone to perform an action. You can also say this in a nice fashion, asking "please open it". There are many different forms of imperative sentences, which include: commands/orders, directions, instructions, requests, and warnings. All of these different types of sentences are asking someone to do something, just changing up the way they d...
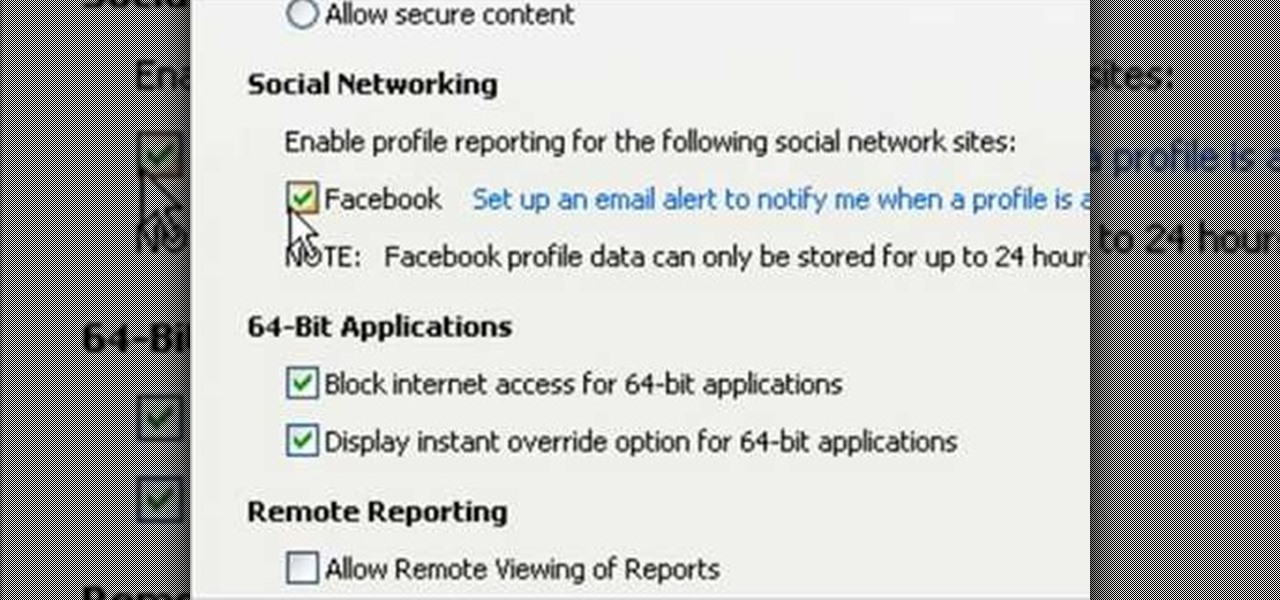
Danny with Top Ten Reviews will show you how to monitor social network activity with the Net Natty program. This will be helpful for monitoring social networking accounts on websites such as Facebook and MySpace. First, open Net Nanny. Go to the dashboard and select Additional Settings under Filtering. With this section, social networking sites that have been used on the computer will be listed. You can check whichever account you want to monitor. Under the dashboard, go to Reports and select...

In this tutorial, we learn how to speak English with conditionals. Conditional statements need special attention and usually start with the word "if". An example of a conditional statement is "if you want, we'll go out to dinner". This has two parts, a condition, and a result. The condition is expressed by "if". To report them, don't change the verbs unless you're dealing with a real condition. Look and see if verb tenses can change depending on how the sentence is structured. Try to remember...

In this video, we learn how to get credit when you don't have any. Most credit agencies are now gathering information about younger people to figure out if they are allowed to get credit cards, which will help them build a credit score. There is a website, PRBC, where you can start a file and enter your information, and it can verify all the information you report. This information will be given to credit reporting agencies, and give you more of a chance to get credit. Next, you can get depar...

JerkyRecipe.net provides a short preview of their online step by step video instruction and report on how to make beef, deer, or venison jerky. This homemade jerky can be made right in your own oven using 15 secret ingredients and by following step by step instructions which can be found in both the online video and printable report, all available for immediate use. A glimpse of what this delicious homemade jerky looks like can be seen in this preview video, offering up a tasty jerky recipe f...
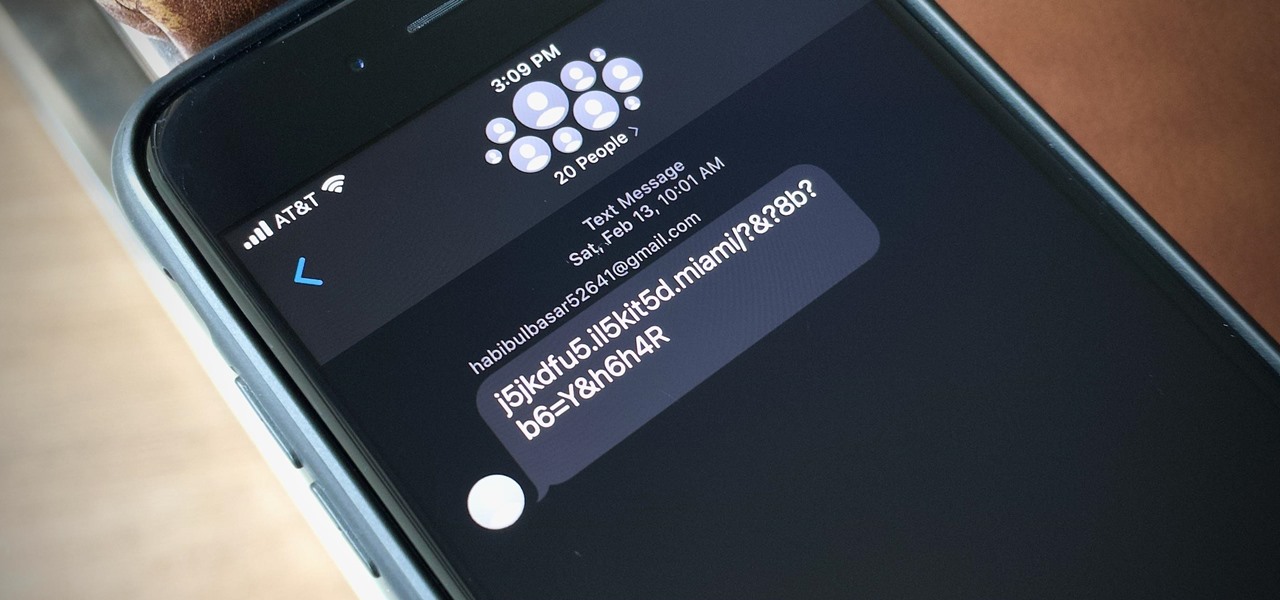
Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.

Rumors are what Apple dreams are made, so most of the time it's best to ignore the juicy ones -- but some Apple rumors demand a least a little attention.

Despite the recent gut punch of staff layoffs, Canada-based smartglasses startup North and its Focals are likely to be in the game for a while longer.

Over the past two years, Apple's Worldwide Developers Conference (WWDC) has become a showcase for new ARKit capabilities. This year, it could offer more information related to Apple's long rumored augmented reality wearable.

While the betting lines on iPhones with depth-sensing, rear-facing cameras in 2019 have already been established, a new report adds some certainty to the notion that the iPhone will get new AR superpowers later this year.

If you think phablets are too big to be smartphones, and not big enough to be tablets, then you're going to love what's coming next.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.
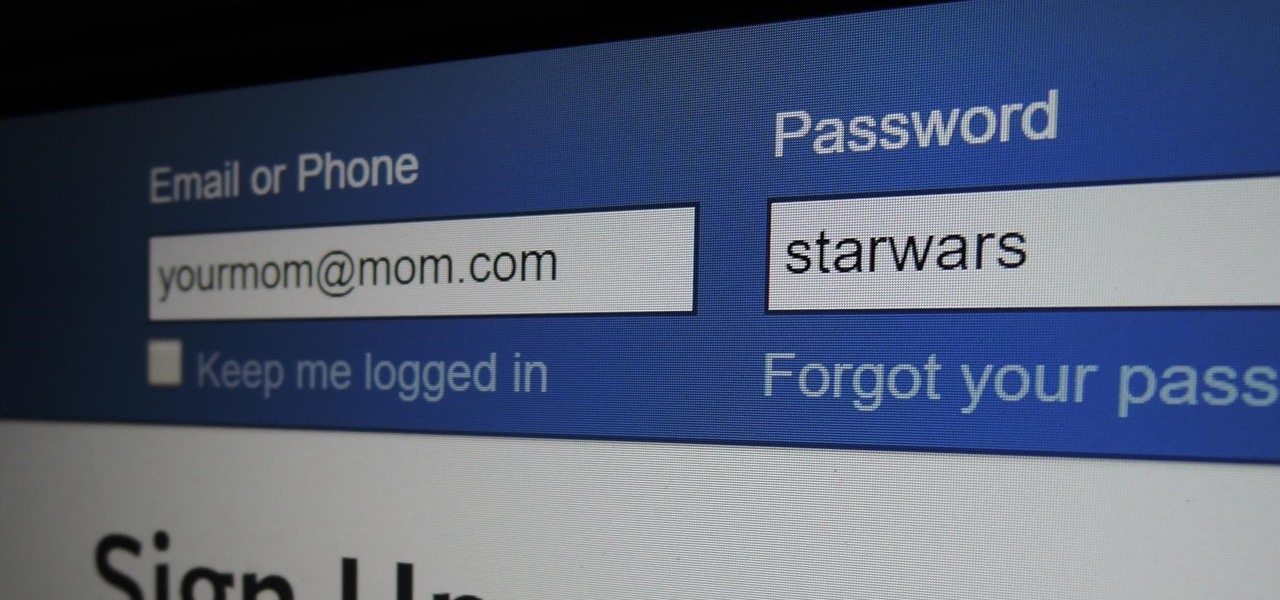
Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...
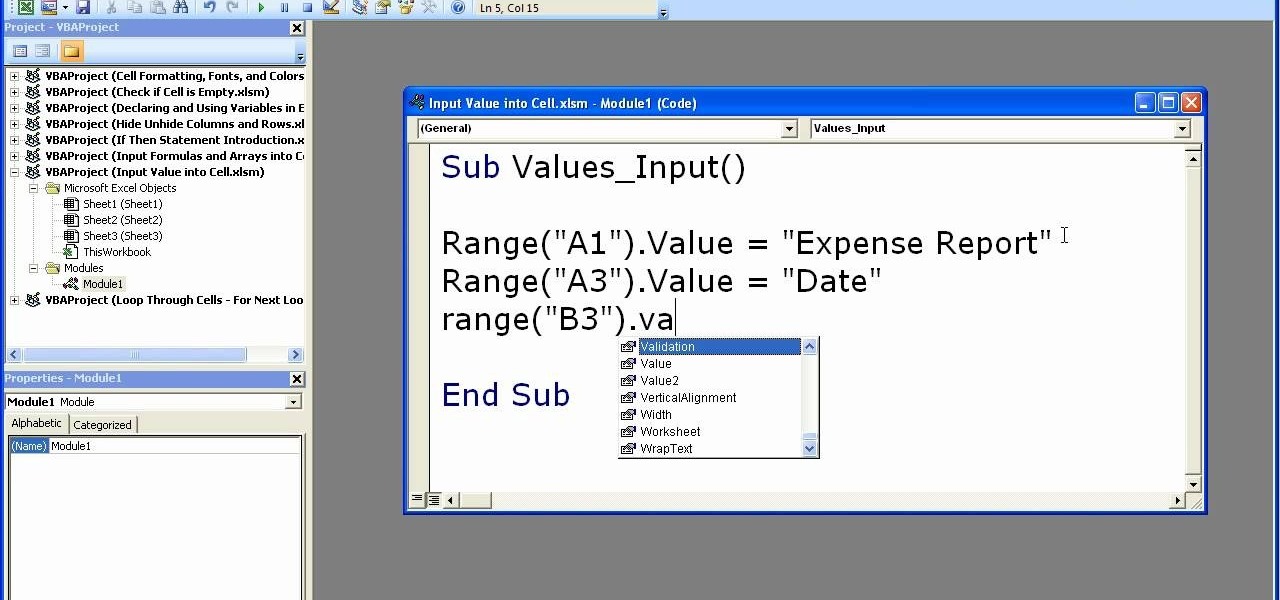
This video shows how to enter values into cells using Excel macros and Visual Basic. This includes a sample Expense Report that is used in this demonstration. In this demonstration, we will create the macro that inputs a title as "Expense Report", Three columns i.e. "Date", "Item" & "Amount", and the summery field as "Total Expenses", as well as the formulas located at the respective cells. Now, we're going to use two keyboard shortcuts i.e. "Alt + F11" to open-up the VBA window and "Alt + F8...
In this clip, you'll learn how to visual data with charts and graphs in MS Project 2010. Whether you're new to Microsoft's popular project management application or are just looking to better acquaint yourself with the Project 2010 workflow, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.