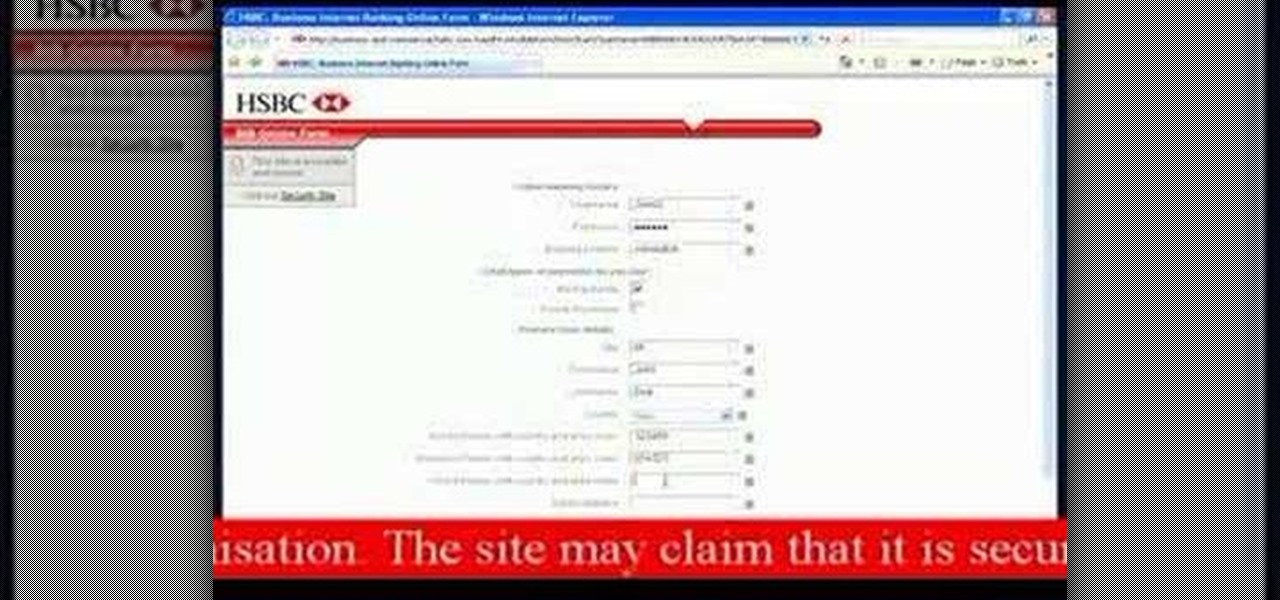
See what phishing (attempts to steal your online information with fraudulent email and webpages) is all about and read the tips on how to avoid becoming the next victim. In this example a HSBC bank phishing attempt is displayed.

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?
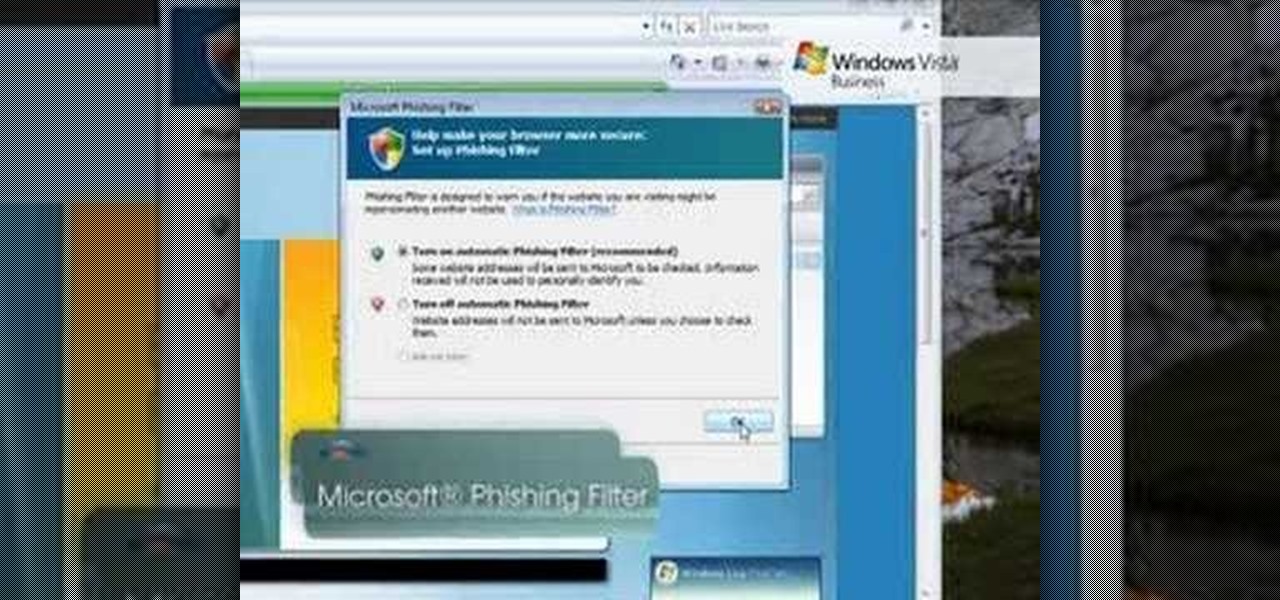
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Phish bone keychains feature a highlighted midsection with three different colors of hemp (in this video we use regular rafia-colored hemp, red hemp, and green hemp) that surround wooden beads.

If you're worried about having your private information taken away from you by hackers and other malicious people, this tutorial may help you. This tutorial will help show you how to easily use and understand the phishing filter in Internet Explorer 8. It only takes a couple of clicks to activate and can be the difference between making sure your private information is secure or out in the open for others to use. Good luck and enjoy!

Ex girlfriend tracking you like a stalker? Find the leaks. She may be going through your email or phishing some information. Does she want a confrontation? Lure her to a public place then get her to cause a scene in front of security. Or last case scenario, fake your own death!

One downside to iOS 11's awesome built-in QR code scanner in the Camera app is its only been live for a short while. In its short life, there has already been a security vulnerability discovered that was an issue for at least the last 4.5 months, but Apple has finally patched this weakness with its iOS 11.3.1 update.

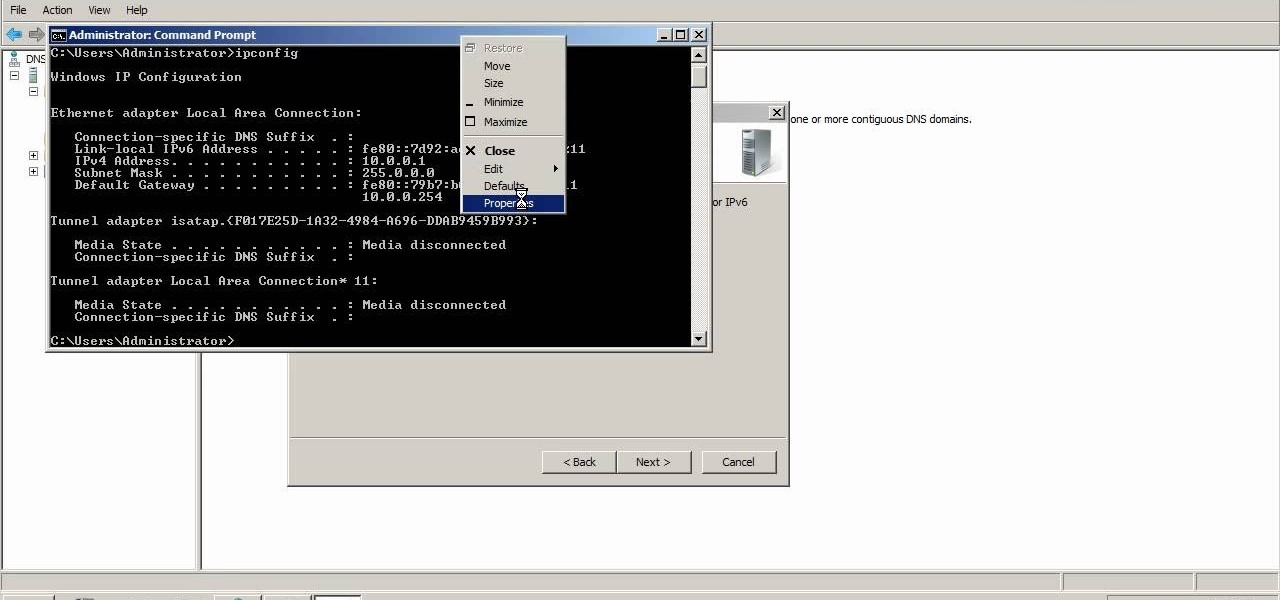
A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

Social media accounts are a favorite target for hackers, and the most effective tactics for attacking accounts on websites like Facebook, Instagram, and Twitter are often based on phishing. These password-stealing attacks rely on tricking users into entering their passwords into a convincing fake webpage, and they have become increasingly easy to make thanks to tools like BlackEye.

Today I am going to teach the various ways that you can use social engineering to hack a system. For those of you that have followed my past tutorials, you know that social engineering can unlock a world of possibilities. This is because no matter how many firewalls, no matter how many patches there are on a server, the password is kept in the minds of people...and people, are not as smart as computers.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

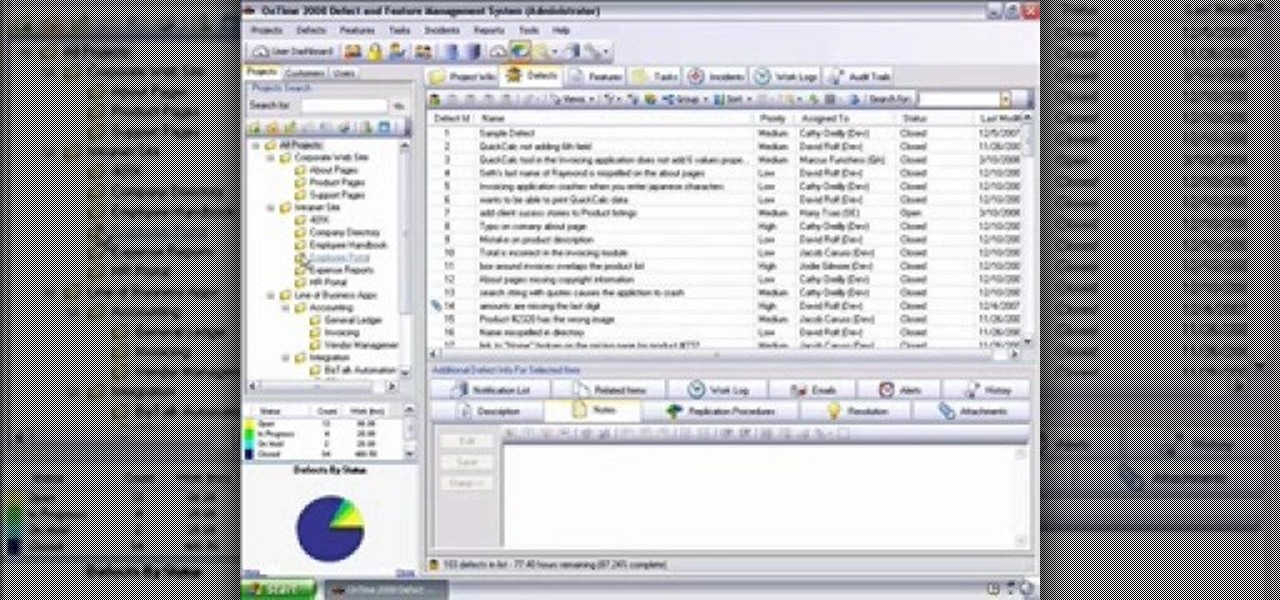
Need some help getting started running reports? This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers the basics of running reports and sending data to those reports. Did you know there are four ways you can manipulate what data is sent to a report without any direct report customization? Take a look!

My message to Russian hackers is this: LEAVE BRITNEY ALONE! Russian hacking collective Turla has been targeting governments and military operations in the United States, Europe, Asia, and the Middle East for the past decade. Now, it appears that the group is targeting everyday citizens — specifically Britney Spears fans.

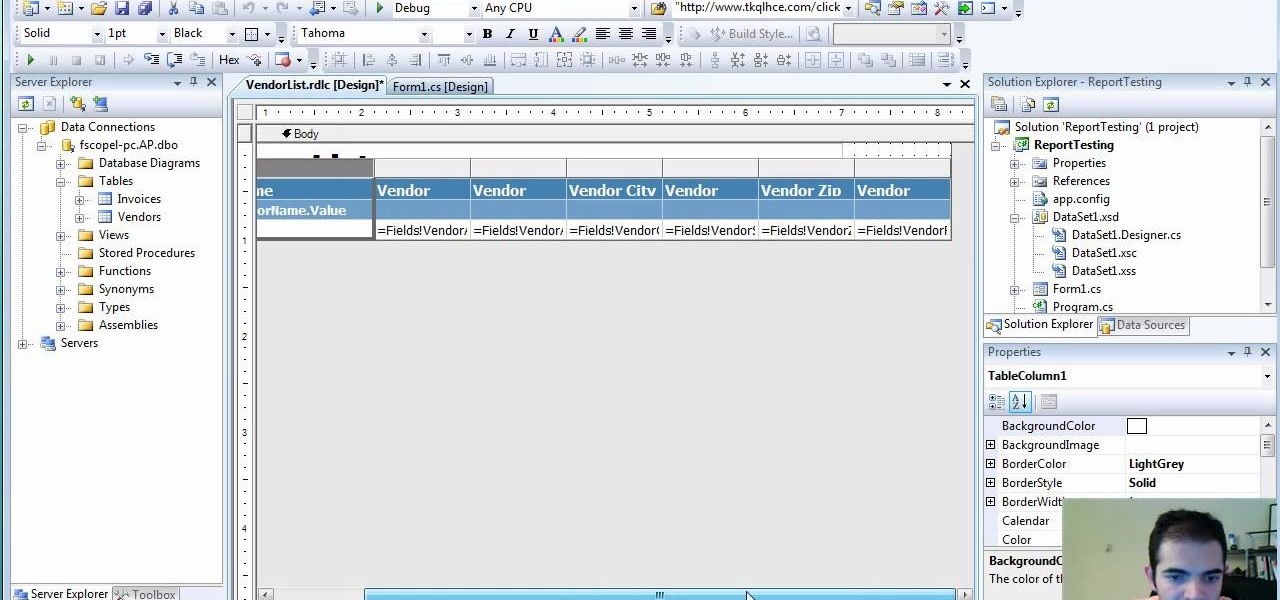
If you're not sure about creating reports in Visual Studio, this two-part video will cover the entire process. This assumes that you already know a few things in Microsoft Visual Studio and the C# programming language. So, if you're not a beginner and still need help to create reports from data in the SQL Server, this is how you do it. Also, learn a quick and easy way to pass parameters to reports in C#.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.

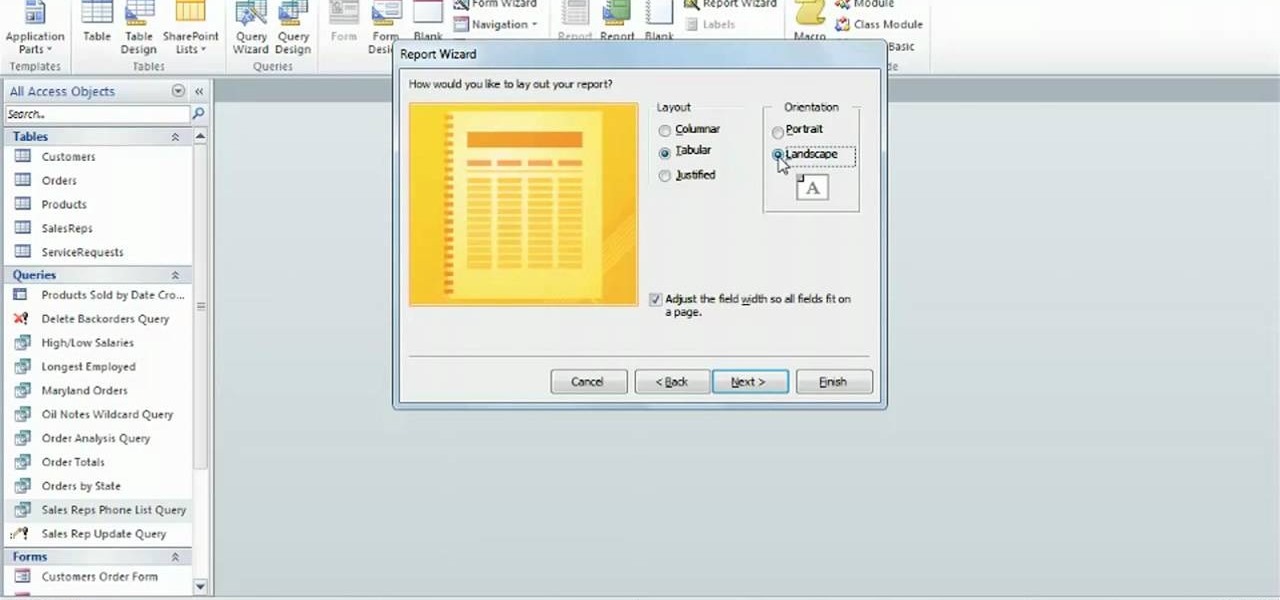
Learn how to work with the Report Wizard tool in Microsoft Access 2010. Whether you're new to Microsoft's popular database management application or a seasoned MS Office professional just looking to better acquaint yourself with the Access 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started using the Report Wizard in your own Access projects, watch this free video guide.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

In this video, we learn how to speak English: Reported Speech/Reference Words. Reported speech is reporting another person's words or telling what someone else said. Indirect speech doesn't use the use the exact words that we use. Examples of reference words are: her, she, herself, him, and himself. Types of references can be pronouns or possessive adjectives. Listen to who the speaker is so you can change the reference words so that the statement is logical. Use this example as a reference: ...

In this Language video tutorial you will learn how to report another person's words. In other words how to restate what someone else said. This video focuses on two aspects. #1. What's the difference between quoted and reported speech? #2. When can we use say and tell? In quoted speech you quote the exact words spoken by a person within inverted commas or quotation marks. It is also called direct speech. Here is an example. Jennifer said, "I like birthdays." Whereas, reported speech does not ...

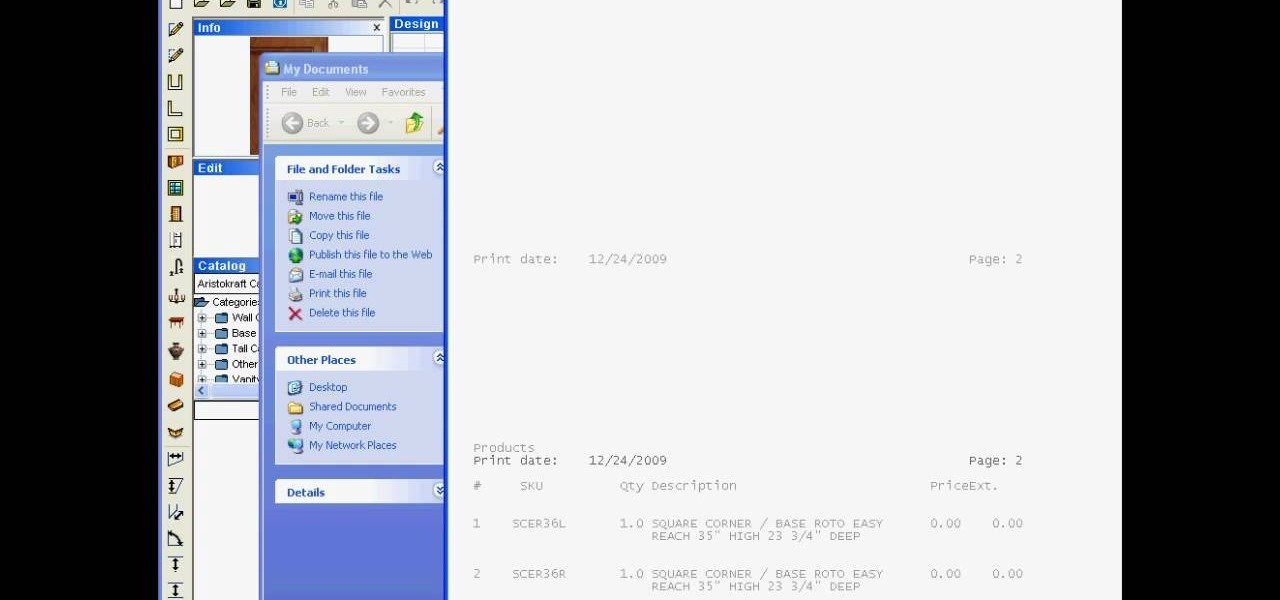
In this video, learn how to export reports to Word, PDF, Excel, and/or TXT formats. Learn step-by-step how to export your reports to any program or format in just a few easy steps.

The first thing that comes to mind when your car is stolen is: ####!! However, once calm, cover these bases when your car is stolen to notify relevant parties and help ensure vehicle recovery or replacement.

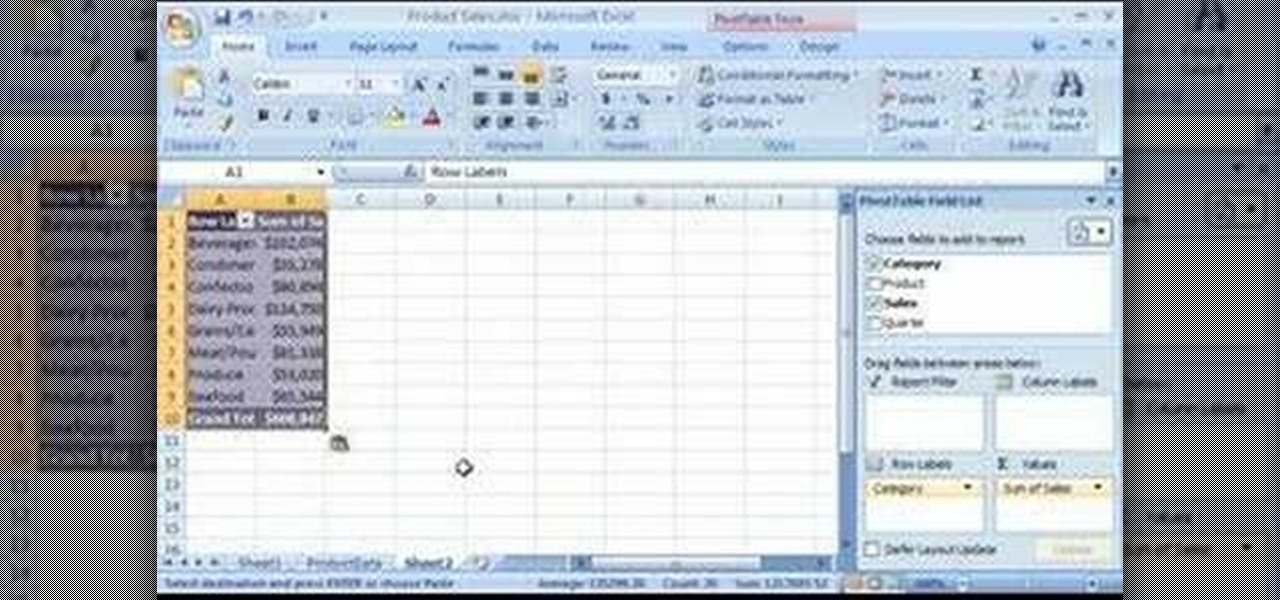
With PivotTable reports in Microsoft Office Excel 2007, your sales report will sparkle with power, flair, and functionality. Take a look at this instructional video to learn how to show the big picture, show all the details, or show anything in between. Easily create multiple worksheets to switch back and forth between the various versions of your report. Sort, filter, and summarize your data any way you like. Show the details of any summary value in your report.

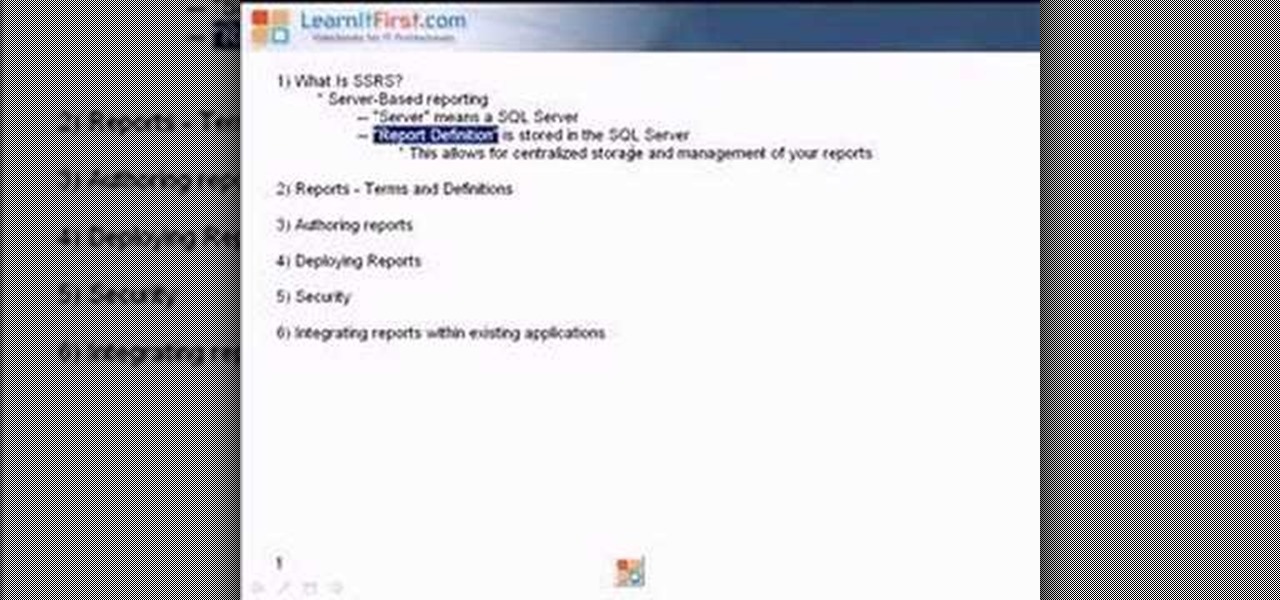
This video talks about what SQL Server Reporting Services (SSRS) is and designed for the absolute beginner - someone who wants a high-level overview of Reporting Services.

Learn how to spot a fake invite on MySpace and report the scam. This happens a lot with music and bands so help them out and report the scams - this video shows you how!

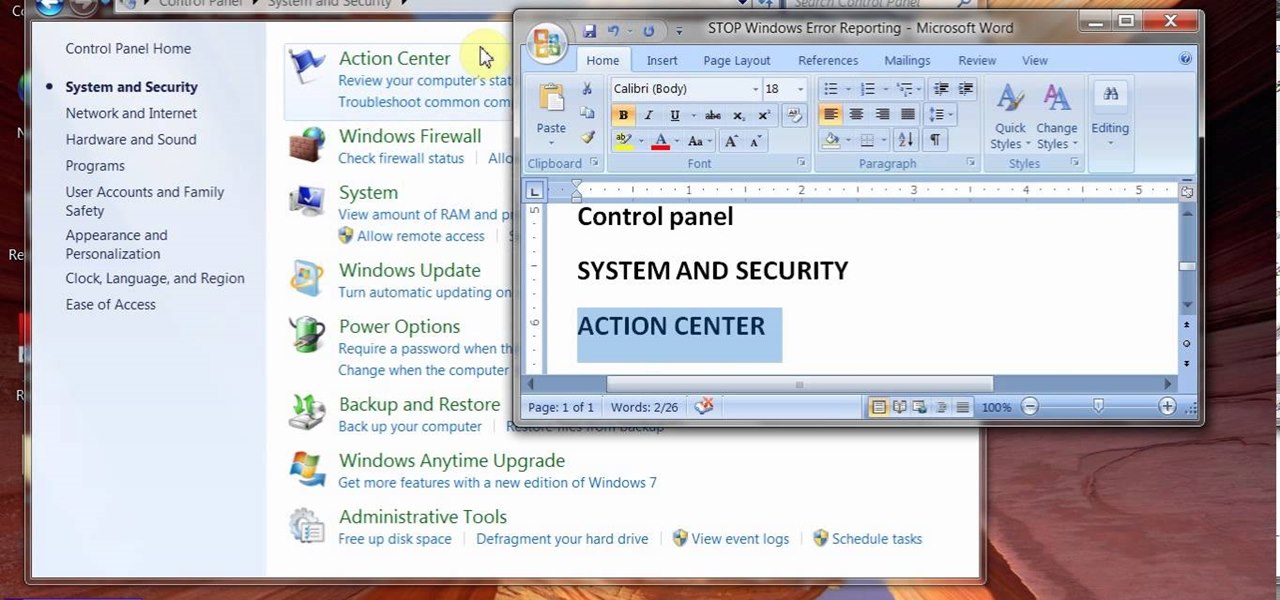
Error reporting in windows 7 sometimes create problem for users. They want to stop or disable this error reporting. Here are the steps to follow for stopping Error Reporting.

You should watch this video if you want to improve your credit score with just 3 steps. To improve your credit score: Check your credit report. It is where your score comes from. You can also get a free copy of your credit report once a year at Annual Credit Report. Check it for errors. Timing. If you're going to apply for a loan as the application month approaches, stop charging because if your balance happens to be reported while it's big, it will temporary lower your score. Don't close you...