Directory traversal, or path traversal, is an HTTP attack which allows attackers to access restricted directories by using the ../ characters to backtrack into files or directories outside the root folder. If a web app is vulnerable to this, an attacker can potentially access restricted files that contain info about all registered users on the system, their permissions, and encrypted passwords.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.
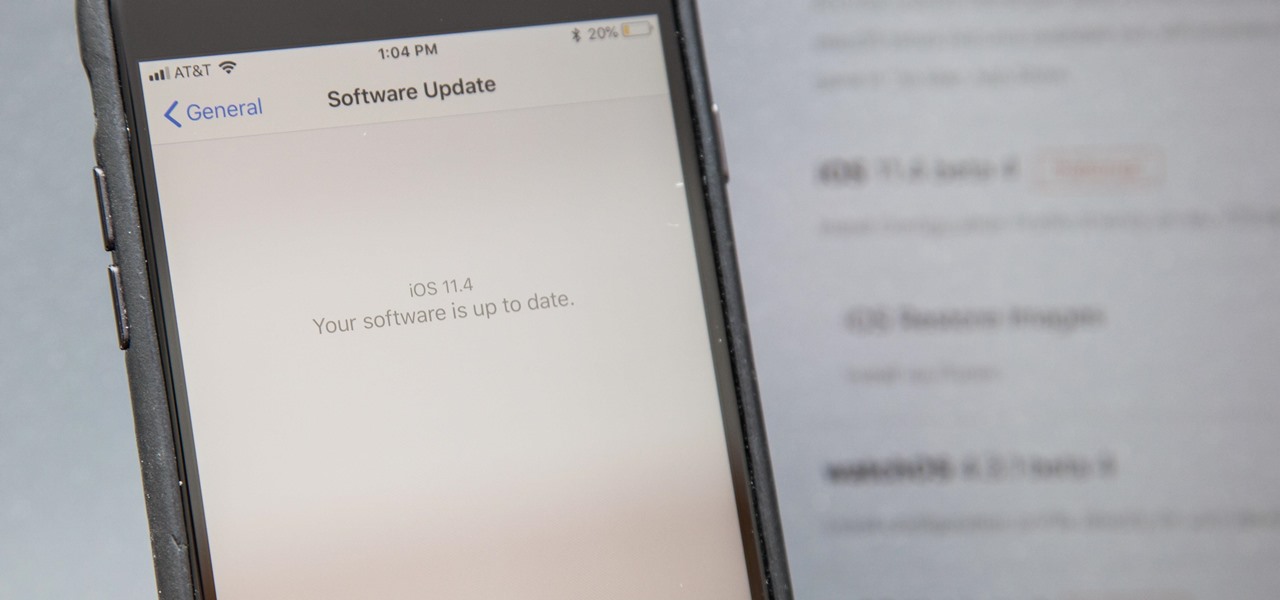
Apple released the fourth developer beta for iOS 11.4 on Monday, May 7, followed the next day with the public beta release. This update arrives just six days after the company seeded beta 3 to users, which fixed an 11.3 issue with 3D Touch, among other various bugs.

Apple released the third beta for iOS 11.4 on Tuesday, May 1. This update comes exactly two weeks after the release of the second beta, which, in addition to adding a new wallpaper, fixed issues with AirPlay, Music, and Keychain. The only noticeable change in beta 3 is a fix for unresponsive 3D Touch.
This how-to is for everybody who faced the problem of intercepting personal data sending through the Internet and is looking for fast and secure method to protect his activity in the global network.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Welcome back, my novice hackers! In this third installment of my Hacking Web Apps series, we will look at the authentication of web applications. Remember, there are many ways to hack web applications (as I pointed out in my first article), and cracking authentication is just one method.

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...

It's been a while when the major web browsers first introduced HTTP Strict Transport Security, which made it more difficult to carry Man In The Middle (MITM) attacks (except IE, as always, which will support HSTS since Windows 10, surprised?).

Are you trying to access Facebook when you shouldn't? This video will help. Watch and learn how to use a proxy to get to blocked websites, like Facebook. Now you can go on Facebook and other websites anywhere, even at school.

When Pokémon GO developer Niantic launches its Real World Platform for augmented reality gaming, it will run over 5G speeds courtesy of T-Mobile parent company Deutsche Telekom and the edge servers of its MobiledgeX subsidiary, the companies announced today.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Welcome back, my tenderfoot hackers! Now that we have begun this trip down web app hacking lane, we need to first address target reconnaissance. Like any hack, reconnaissance is critical. (Are you tired of me saying that yet?)

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

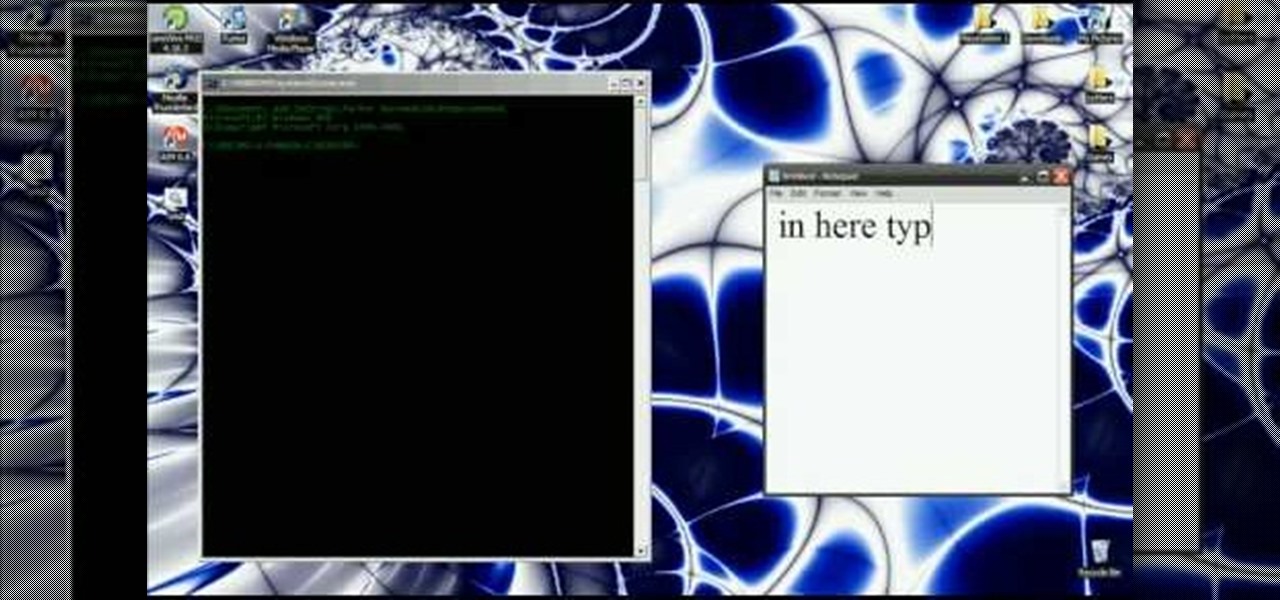
In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...

MMS is disabled on some iPhones. To enable it go to settings, and go into the general settings. From the menu select network and select cellular data in the network menu. In the Cellular Data settings go down to MMS options. Now set the APN as wap:voicestream.com, MMSC as http://mms.MSG.eng.t-mobile.com, and MMS Proxy as 216.155.165.50:8080. Once you do these settings go to the message settings and make sure that the MMS messaging is turned on. Now go to messages and create a new message. Add...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

Talk about rapid-fire. Apple released the sixth beta for iOS 11.4 on Thursday, May 17. The update comes just three days after the release of iOS 11.4 beta 5, indicating that Apple is readily approaching the official release of the software. Apple has not issued an official iOS update since 11.3.1, which found its way to users over three weeks ago.

Apple is speeding things up in the iOS 11.4 development. The company released to developers the fifth beta for iOS 11.4 on Monday, May 15. Public beta testers got the update just hours later. The update comes just one week after the release of the fourth 11.4 beta, which introduced minor bug fixes and security patches to iPhone running the software. This beta version doesn't seem any different.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

In this video, Justin Kredible will focus on magic tricks that can be performed on the run. These tricks don't require you to carry many props or do any pre-trick prep so you will always be ready. Follow along and twist your friend's minds into a pretzel while they try and figure them out.

Pet-proofing your house won't just protect your possessions from becoming chew toys—it could save your dog's life. You will need a dog crate, a dog who's ready to move in, dog manuals, pet repellent, electrical cord covers, baby gates and a dog bed or towels for bedding. These are helpful tips for pet proofing your home for your new puppy or dog.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Greetings all. Today I intend to append a new series to my mini-collection of posts. This series will consist of informative guides for the purpose of depicting certain aspects of the White Hat profession that I believe are of profound importance. Furthermore, I will keep this series simple for everyone to follow, regardless of your tech level. So without further ado, let's get right into it.

This four-part video tutorial is furnished by the (FCC) Federal Communications Commission shows you how to get ready for the digital television transfer. Is your television ready for digital? By February 17th, 2009 TV stations will stop broadcasting in analog and broadcast only in digital. Your TV needs to be ready so you can keep watching. Digital television, also known as DTV, is here, and after February 17th, TV stations will turn off their analog signal. The FCC wants to be sure you are r...

Welcome everyone to the second part of the How To Become Anonymous online series. Today I will (briefly) introduce you to what has been defined "The most secure OS" : Tails a Debian based OS. (Official website: https://tails.boum.org/)

This is a quick and easy method for receiving the backend IP (1) of a server who is hidden behind a proxy (2) or a firewall (3).

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

In order to get the Canon 5D Mark II production ready, you're going to need to invest in a few accessories to get you up to speed. Fortunately, this video from Mauro Media gives a great breakdown of how you can get your slick camera up and ready to go for any handheld doc, narrative, or ENG shoot.

Check out this instructional climbing video that illustrates how to get ready for glacier travel while climbing. Learn everything you needed to know to properly prepare for a safe glacier trip. This tutorial video offers crevasse rescue tips and safety precautions. Follow along with this video and get ready to glacier travel and crevasse hunt.

When it comes time for a Showdown, you better be ready, and the best way to be ready is to watch this NextGenTactics video on playing Showdown in Call of Duty 4: Modern Warfare. There's a lot to know about the multiplayer map Showdown, and if you don't know the ins and outs, you need to pay attention. This will help you move around the map, minimizing enemy confrontation and increasing the chances of surprising the enemy.

Britney has her ups and downs but when she is hitting the high notes she is always stylish. In this tutorial, learn how to recreate Britney's makeup look from the 2008 MTV Video Music Awards. This simple, smokey look will turn anyone into a red carpet ready pop star, so follow along and get ready to turn heads.

If you are looking for a red carpet ready look, look no further than this tutorial. In this video, you will see how to get longer, curlier, fuller locks that will make any budding starlet jealous. So, if you are looking to add some volume to your 'do, follow along with Judy as she shows you how to look camera ready no matter what the occasion.

This video is about how to draw a pirate ship For this you have to remember only few easy steps that are the following (1)draw the ship with pencil or light color to make it error free

Comic artist Mark Crilley demonstrates how to sketch a classic fighting stance, really helpful in your own character or cartoon drawing. Instead of focusing on anatomy, this rendering technique focuses more on style. Follow along with Mark's great artistic advice and make your own action figure. Watch this how-to video and learn how to draw a "ready to fight" pose.