Three-dimensional printing is one of the many wonders of modern technology. It's the first step towards real life Star Trek replicators and Timeline-esque teleportation chambers. While we aren't at the level of reconstructing strands of DNA, it's already possible to make tons of fun and useful designs on a 3D printer.

With the advent of 3D printers, advancements in the technology allow some truly amazing possibilities. Just a handful of examples include printable architecture, Anish Kapoor's sculptures; even Boeing uses some printed parts in the manufacturing of their airplanes.

Printers are getting pretty high tech these days. Print a building, print some organs... and now, print your own cement sculptures.

No matter if you've used one or not, you've got to admit that 3D printers are pretty darn awesome, especially the self-replicating ones that extrude molten plastic and the shoebox-sized versions that use mesmerizing stereolithography to build tiny objects layer by layer. But what's even cooler? A solar-powered printer that uses the sun's energy to melt sand and make 3D objects out of glass.

Aside from food, oxygen, sunlight and water, there are other necessities that humans arguably need today to survive—clothing, love and shelter among them. Almost everyone wears clothes, needs somebody (or something) to love and a place to call home. And what's the one thing that connects all three? Something we all have? Keys.
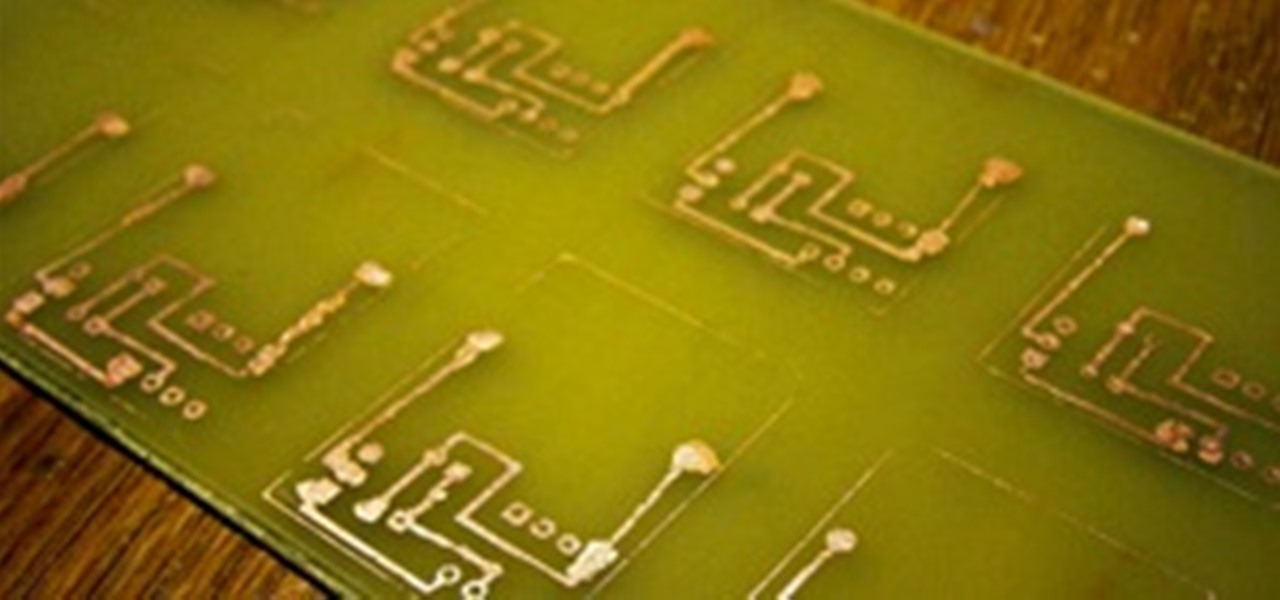
Homemade circuits are amazing. You can build any kind of circuit on a simple perfboard, as we have seen in previous projects. However, some projects require very tiny circuit boards. We could special order some boards from a printed circuit board (PCB) factory, but that will most likely involve a high price per board and a few thousand miles of delivery service to pay for.

It's hard to believe that a photo-sharing service could become as big as Instagram has. So big, in fact, that there are tons of websites, software, and products aimed at integrating it into our lives even more. Hell, you can even be Instagram for Halloween.

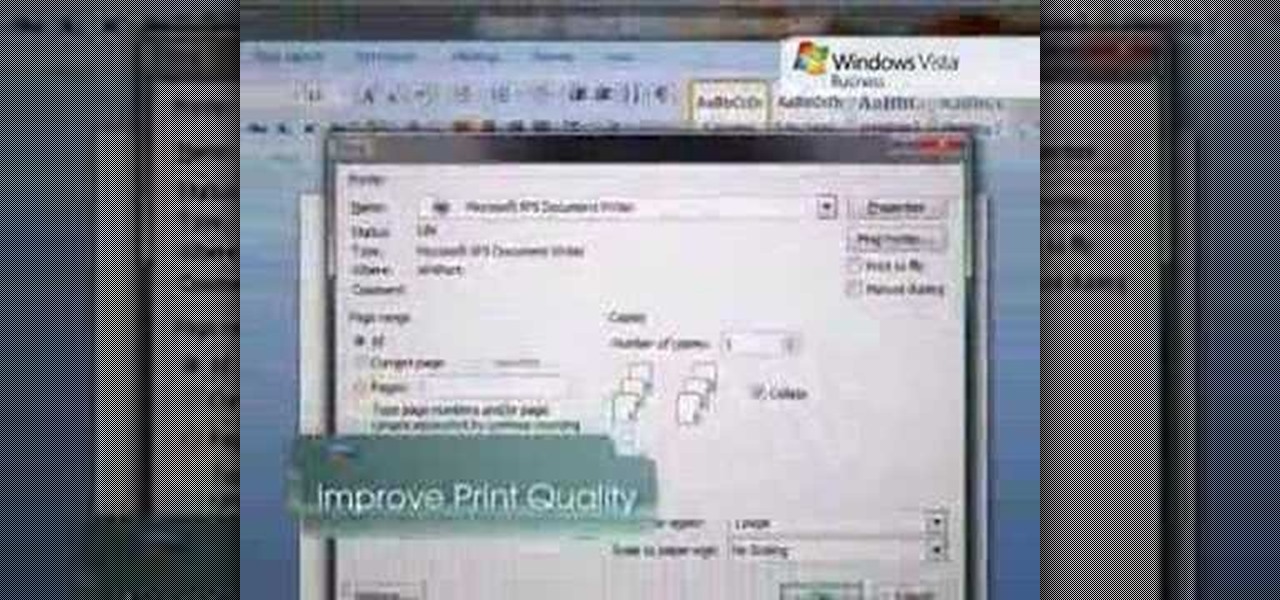
While printers are not normally considered to be at the leading edge of computer technology, these devices have evolved at a lightning pace over the years. Before today's low cost, high-quality inkjet and color laser printers, we used low-quality dot matrix printers and slow laser printers where quality and performance of printing was often questionable. Additionally, documents that looked correct on screen often came out looking differently on paper, due to differences between what the scree...

Windows 7 is the hot, new operating system replacing the past XP and Vista systems. Windows 7 is the most simplified, user-friendly version that Microsoft has developed - ever. Get acquainted with your new version of Windows straight from Microsoft.

If you use your inkjet printer regularly, you’ve probably discovered that the cost of replacing the cartridges can quickly exceed that the printer itself. Refill the cartridges yourself to save some money.

This video demonstrates how to show and hide the ruler in Microsoft Word 2007, along with working with page margins. The presenter indicates that if you click the small button above the vertical scroll bar, Microsoft Word will then display Rulers. To work with margins you'll need to click on the Page Layout tab to display the Page Layout ribbon. The video shows the different options located on the Margins menu. There are several built in settings for wide, narrow, normal, moderate, and mirror...

New user to Windows 7? Microsoft has put out a series of video tutorials explaining how to maximize your Windows 7 experience. Follow along with this computer lesson and learn how to:

New user to Windows 7? Microsoft has put out a series of video tutorials explaining how to maximize your Windows 7 experience. Follow along with this computer lesson and learn how to:

This how-to video is about how to make PS3 controller work on the computer that have either Windows XP, or Vista or 7 as their operating system.

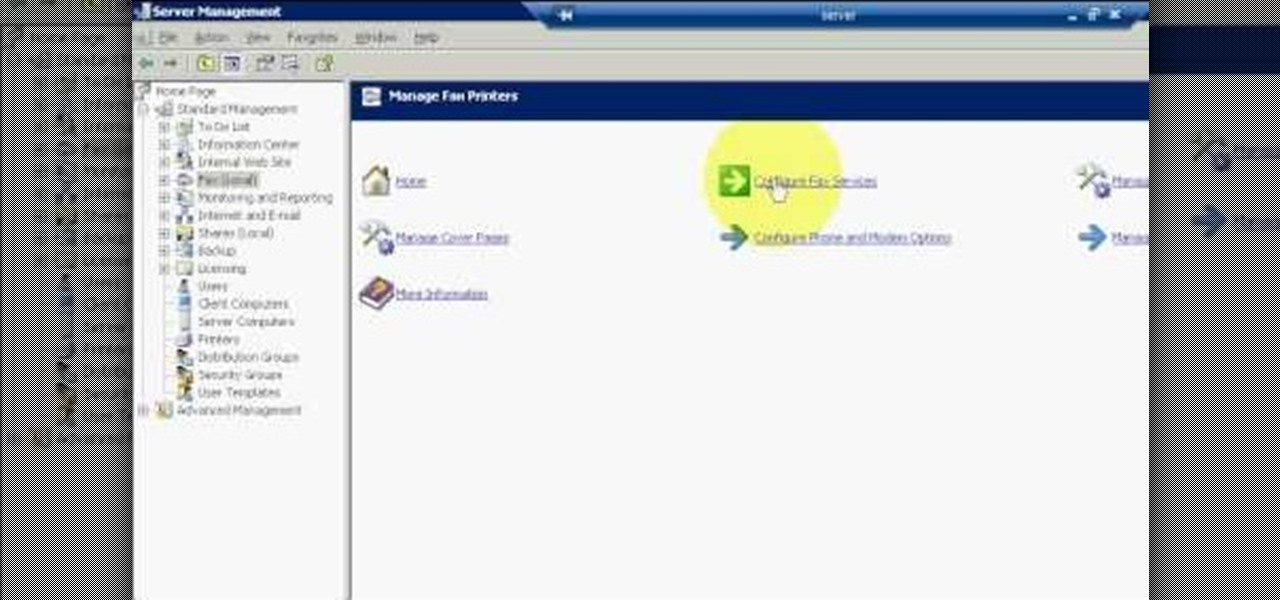
The first step to create a fax using Outlook 2003 and 2003 server. Using add/remove windows component make sure your fax equipment is properly installed. Under the start menu select the printers and fax option and select the share option. Then under administrator tools/users/new/users/fax to enter your password to turn our fax information transfer on. You must now select fax user and select advanced settings and double check to make sure the fax is able to see the object it needs to send the ...

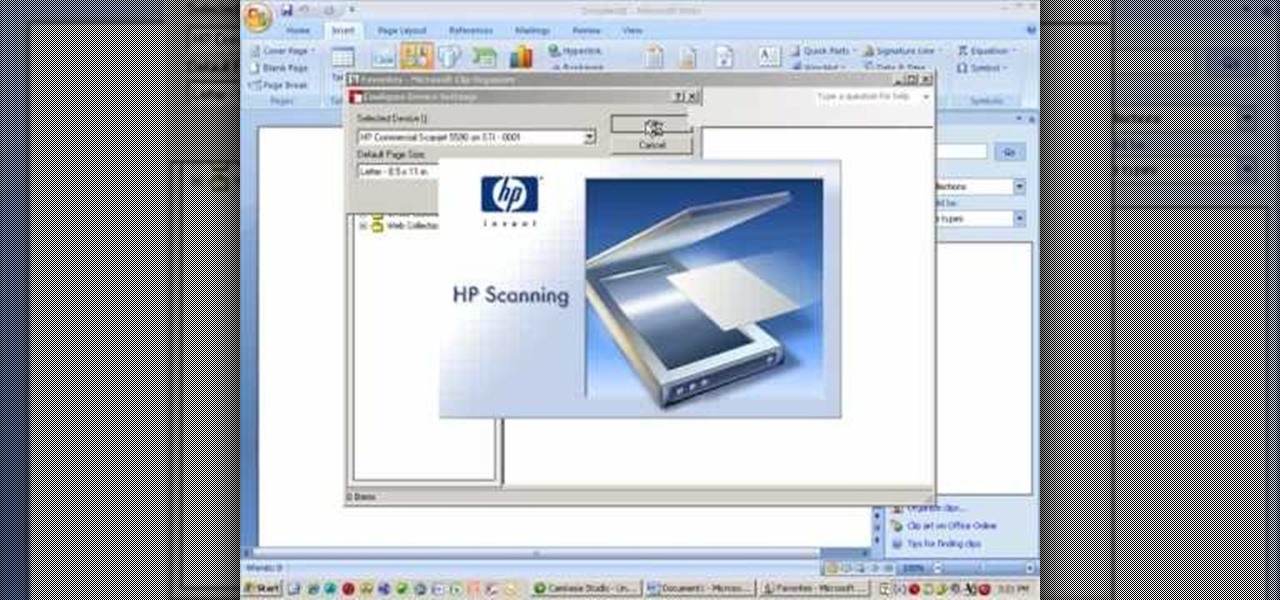
With technology nowaday, it has become so much easier to scan documents. In the past, people would always take their work to places like Kinkos and pay others to do something that would be simple and easy to do at home. But since the release of multi-functional printers that not only print, they scan, fax, and can even download pictures directly to your computer. This tutorial will show you how to scan a document and send it to your Word program. Enjoy!

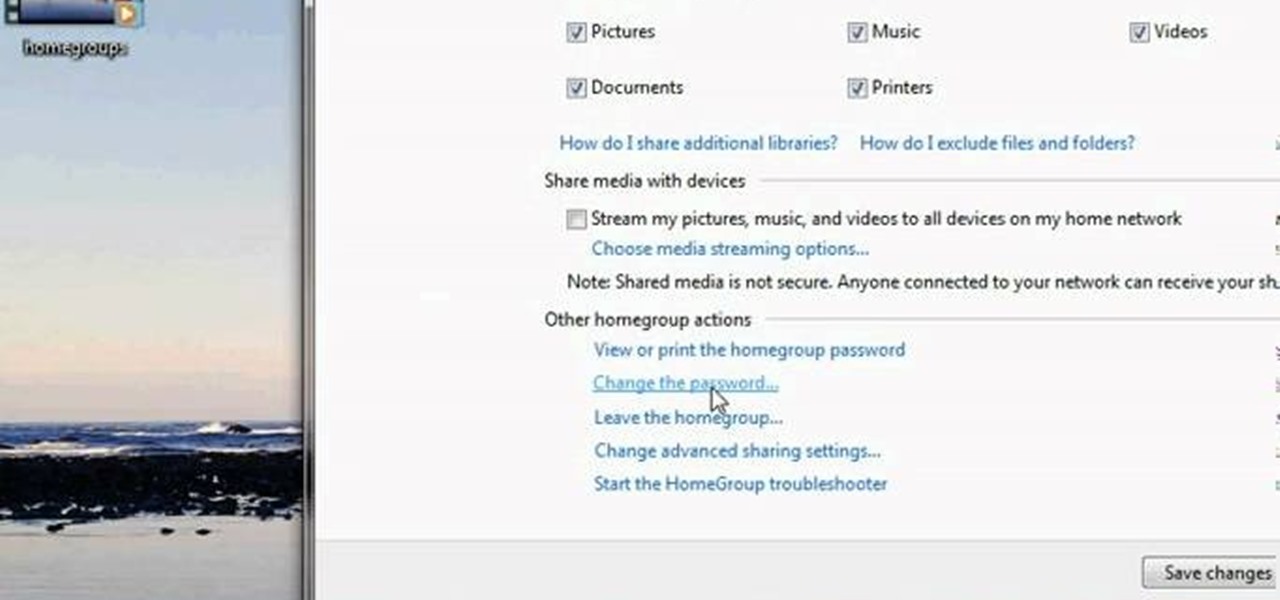
This video tutorial from pctechbytes presents how to quickly set up Homegroups in Microsoft Windows 7.This feature allows to easily share files between computers with Windows 7 operating system.Press Start button, select My Computer option. In the newly opened window select Homegroup from the list to the left. Select View Homegroup Settings link.In this window you can choose what types of documents you want to share with other Windows 7 operating system users.You can share pictures, documents...

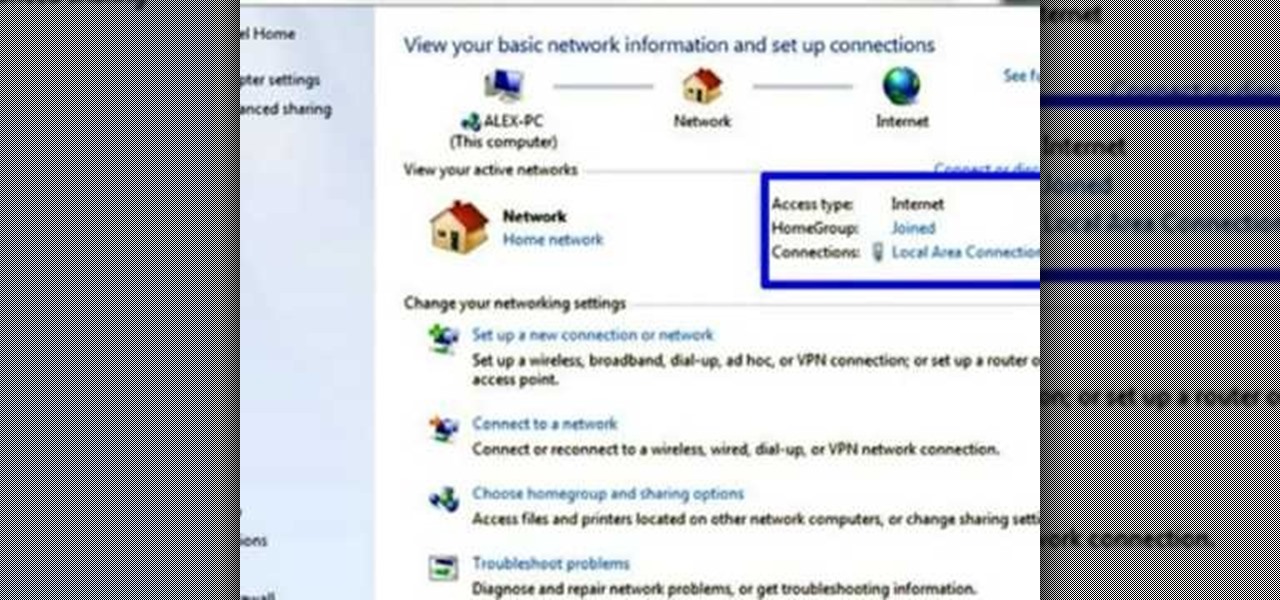
Want to access files from multiple computers at work or home? An expert from PC Remedies explains how to set up a Home Group network on Windows 7 systems. Includes a how-to of setting up your location, and managing the set-up wizard. Finally maximize your current resources by networking your work and entertainment files, as well as hardware such as printers. The excellent video gives you an exact snapshot of what you can expect to see on your own Windows 7 system. Includes advice on setting u...

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

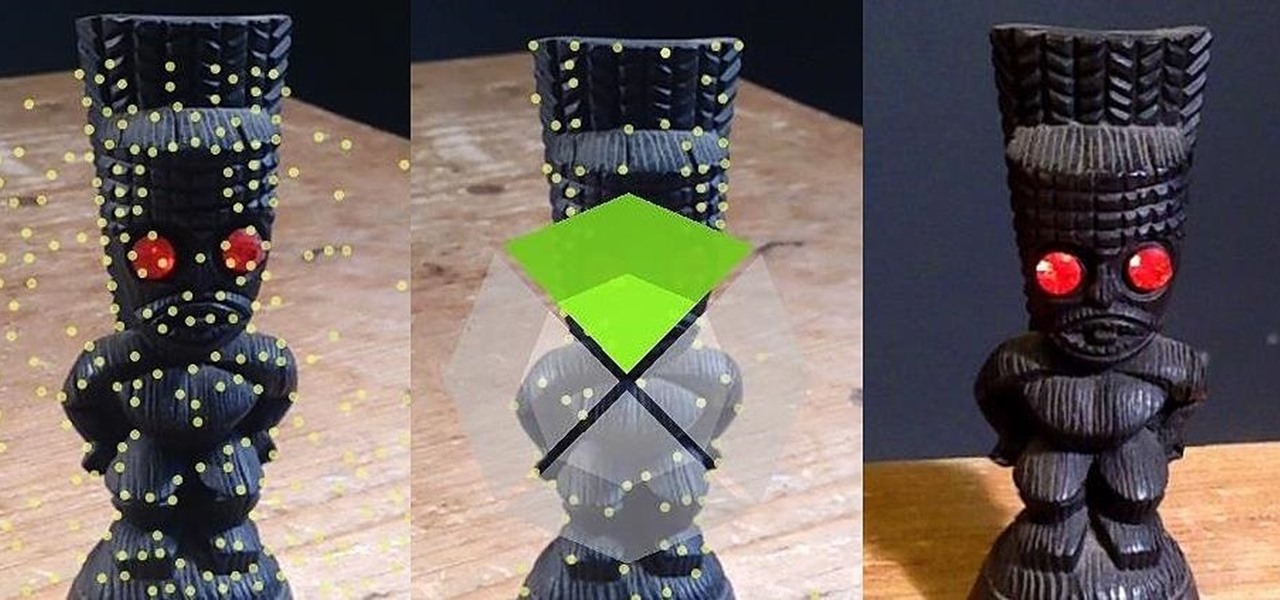
Aaron Betsky, director of the Cincinnati Art Museum and previous director of the Netherlands Institute of Architecture, reports on the world's first postage stamp to employ augmented reality. Dutch advertising agency Gummo, the NIA and the Dutch postal service teamed up to present five unbuilt models by different Dutch architecture studios in 3D form. When held in front of a webcam, the illusion of a 3D building is projected in your hand. By slowly moving the stamp, you can experience the vir...

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

At IFA in Berlin today, Sony introduced the latest models of the Xperia line, with new features in tow that should appeal to creators of augmented and virtual reality content.

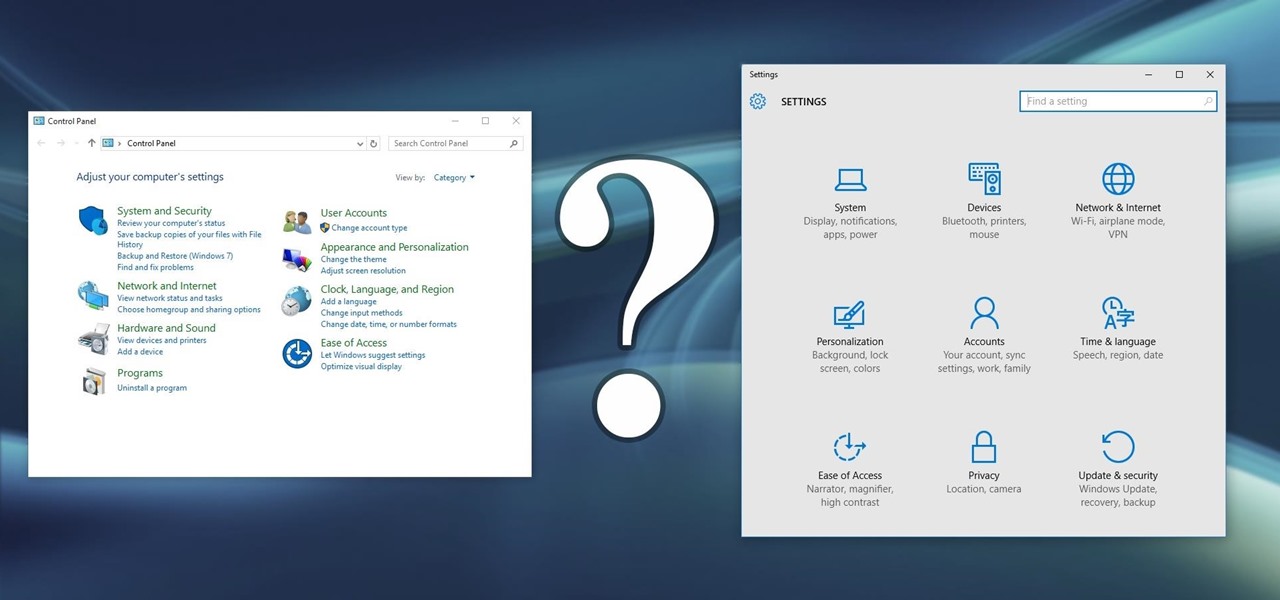
Slowly but surely, Microsoft is pushing more and more options out of the Control Panel and into a new menu simply called Settings. This new Settings menu debuted with Windows 8 and mainly focused on touchscreen-related options, but starting with Windows 10, you'll find quite a few general options residing here as well.

It sounds like a dream come true: just press a button on your phone, and 30 seconds later, a machine produces a custom-made, ready-to-eat meal. Finally, science comes through for the truly lazy!

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

3D has been all the rage for the past few years. It seems like every other film has a 3D aspect to it, our TVs have 3D capabilities, and we can even print functional objects using increasingly affordable 3D printers. And after some trial and error (ahem, Evo 3D), it's finally taking shape on mobiles.

LEDs have slowly become the standard for DIY lighting projects because they consume less power and last way longer than regular light bulbs do. Light-emitting diodes have no filament, meaning they generate their light solely by the movement of electrons in a semiconductor material.

RIP Touch ID. Apple's fingerprint sensor on iPhone and iPad models with Home buttons is about to become phased out on Wednesday, Sept. 12. While Touch ID will remain an integral part of models from the iPhone 5S to the iPhone 8 Plus, as well as the iPad Air 2 through the sixth generation iPad, Face ID will completely take over as the default security method for unlocking future iOS devices.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

We've had the pleasure of test driving the ASUS Transformer Book T100T for the last couple of weeks, and for a $400 Windows 8 machine, it's impressive to say the least.

Welcome back, my greenhorn hackers! My preference for Linux as a hacking platform is well documented, and I have even created a series of tutorials to train new hackers. Without being proficient in Linux, you can't really call yourself a hacker.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

There's nothing like buying an awesome new gadget, but it leaves you with one problem (besides an empty wallet)—what do you do with the ones you already have? There are plenty of ways to put your old gadgets to use, but if you'd rather get rid of them, you may as well get something out of it, right? Here are five places where you can recycle your electronics and replenish your cash stash.

Hi, gang! Time for another hack using Metasploit. We have exploited Windows XP (a very insecure operating system) and we have exploited Ubuntu and installed Meterpreter on a Linux system exploiting the Samba service. Several of you have asked for a hack on more modern Windows systems, so here goes.

With non-fungible tokens (NFTs), particularly those that are 3D in nature, holographic displays are becoming more indispensable for those looking to show off their valuable works of art.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.