Check out this instructional dance video to learn how to do "The Dip". Learn this smooth move to rock in the clubs or at parties. This is a prerequisite for one of the types of freak dancing. Chihoe "Groove" Szeto teaches you popular, fun dance moves step by step in these tutorial videos. Remember to have fun and practice your hip hop skills with this tutorial video.

Want to perform a wall flip? Take a look at this instructional video and learn how to do a wall flip. It would help if you knew how to back flip already, but that's not a prerequisite. To perform this you'll want to run at the wall in a normal running speed. Then jump and place your foot high. Afterwards, you have to rotate. To achieve rotation you must kick up with your other leg that was not planted on the wall and swing back by leaning your head backwards.

Perform butterfly high reels for poi beginners. To do this poi move, it is a prerequisite that you know how to do the basic butterfly, spinning, and butterfly low reels.

When you're using vacuum power, moving water, or compressing air, it's more than likely being done with some sort of pump. I'll be needing a pump for some of my future projects, so in this tutorial, I'll be showing you how to make your own customizable PVC hand pump that will let you do all three.

Heartbleed, move over. There's a new bug in town, and this time it's also affecting Mac and Linux computers. It's called Shellshock (its original official title is CVE-2014-6271), and it's currently got a 10 out of 10 severity rating over at the National Cyber Awareness System. While some updates have been issued to fix this bug, they were incomplete, and your system is probably still vulnerable, as it has been for the last probably 20 years.

While some Android applications have built-in gestures that allow you to perform certain actions, it's not a feature that's been comprehensively, let alone consistently implemented. If you're on Twitter or Facebook and you want to go back, the only global way is by tapping on the capacitive back button at the bottom of your device. Thanks to XDA dev PeterCxy, you can now enable a global swipe back gesture on your Android smartphone or tablet, making it easier than ever to backtrack within apps.

We've shared a capture-the-flag game for grabbing handshakes and cracking passwords for Wi-Fi, and there are some upcoming CTF games we plan on sharing for other Wi-Fi hacks and even a dead-drop game. While security-minded activities and war games are excellent ways to improve your hacking skills, coding a real video game is also an excellent exercise for improving your programming abilities.

Owners of Google Pixel devices now have a plethora of imaginary friends to play with thanks to the Playground augmented reality app.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

When I became serious about cooking, nearly every cookbook and guide I picked up emphasized the importance of using fresh stock, whether it was chicken, beef, or vegetable. When I didn't have time to make my own, I bought the highest quality boxed or canned stock I could find at the market.

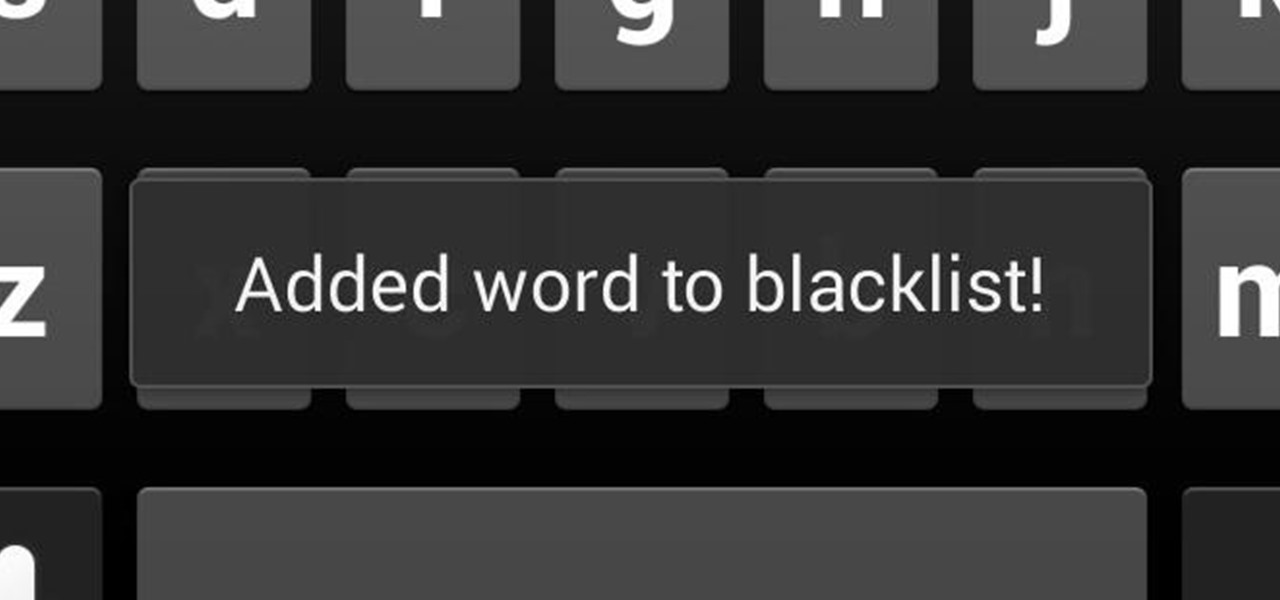
In the midst of furious finger typing on a small non-tactile screen, you're sure to make mistakes—so the majority of keyboards have autocorrect. Generally it works pretty well and is a welcomed feature.

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.

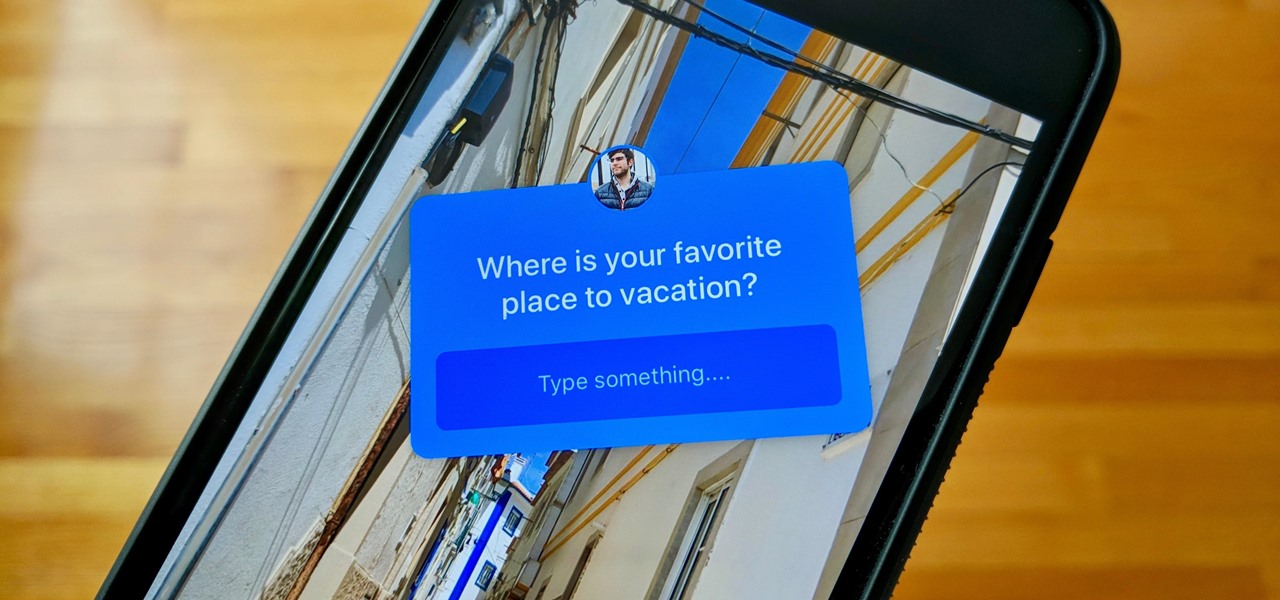
Your Instagram followers deserve to be heard. Whether through polls or DMs, Instagram offers your followers a unique way to share their thoughts and opinions with you on any subject you can think of. Now, the social media giant is expanding these options with the introduction of a new "Questions" sticker for your stories.

Sometimes it's the smallest feature in your smartphone that makes the biggest difference in user experience. Take screen timeout, for instance. You can probably think of plenty of times when your handset's display blacked out while you were in the middle of something. You could have been cooking with a recipe on the screen or looking at chords while you learned a new riff on your guitar.

With Geohot's Towelroot allowing us to root our Nexus devices in under a minute without ever leaving Android, many of you are probably enjoying all of the Gadget Hacks that root access has unlocked.

One of the most frustrating things about full touchscreen phones, especially for those coming from one with a physical keyboard, is typing and editing text. Whether it's a quick text message, or Swyping out a full e-mail, it sucks realizing you've messed up a few words and have to go back and fix them.

When you were younger, you probably had your parents bugging you not to have your cassette player headphones up too loud. For all you younger readers out there, it was probably a CD player. The even younger readers likely had an iPod or other MP3 player. Either way, your parents didn't want you to mess up your hearing, blasting that Limp Bizkit in your ears (wow, I'm showing my age here).

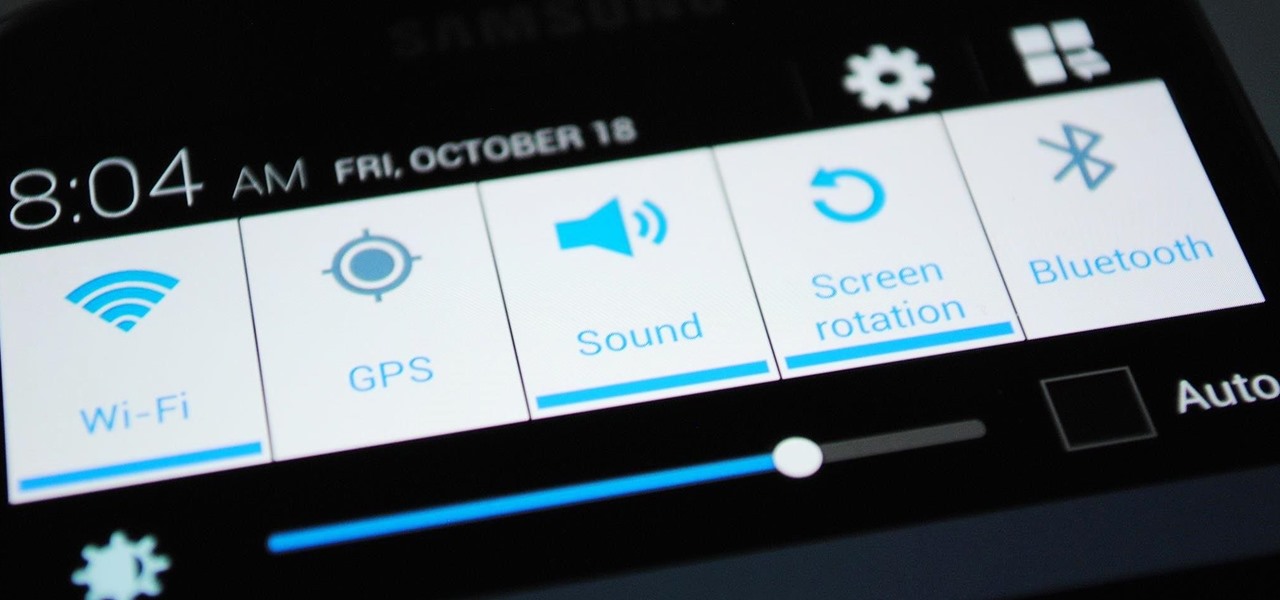
Samsung's quick settings toggles are insanely useful for accessing settings that you would normally need to dig into menus for. Definitely a case of function over form, though. TouchWiz's bright green on dark blue has to be one of the fugliest color combinations I have ever seen.

We've gotten pretty close to a Google Experience before, and even played around with the actual Google Play Edition build. However, the devs over at XDA have a much better solution: actually converting your HTC One into a complete factory-fresh Google Play Edition.

Don't always believe the marketing hype. "PlayStation Certified" does not mean anything to a softModder. All this indicates is that a smartphone or tablet labeled as "PlayStation Certified" has met the guidelines and hardware requirements issued by Sony to display PlayStation Mobile (PSM) content from the PlayStation Mobile Store correctly. No Nexus 7 here.

If you want to play games that aren't in the iOS App Store, Apple makes it pretty tough for you. Usually, the only solution is to jailbreak your iPad or iPhone, but that's something most avoid because it will void the warranty and may cause potential bricking issues.

Okay, you're Nexus 7 is awesome, but ever wish you could explore those nifty TouchWiz features that make the Samsung Galaxy Tab and Samsung Galaxy Note 2 so interesting?

For some people, a costume is just a necessary prerequisite to get into Halloween parties. If you're female and you're going the sexy route, it's not too hard to find something to wear, but transforming yourself into something terrifying takes a little more work.

The art of privilege escalation is a skill that any competent hacker should possess. It's an entire field unto itself, and while it's good to know how to perform the techniques involved manually, it's often more efficient to have a script automate the process. LinEnum is one such script that can be incredibly useful for privilege escalation on Linux systems.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

When attempting to compromise a target, we want as much control as possible over the victim. Metasploit's meterpreter allows us to have immense control over the victim, the only issue is that sometimes we can't land a meterpreter. We may only be able to land a standard shell, but fear not, there is a way to upgrade our shell into the all powerful meterpreter!

Getting a new phone is exciting, but having access to its exclusive apps ahead of its release is what we're all about here on Gadget Hacks.

I'll give Samsung credit where it's due—the stock keyboard on the Galaxy S5 is actually pretty nice. There's a dedicated number row that resides at the top (something that the Google Keyboard needs a hack to achieve), and various settings exist to make switching between languages a breeze.

KitKats? Toast? Sorry if that headline made you hungry, but no I'm not talking about Nestlé's chocolatey wafer treat, nor the crunchy slices of bread you have with your eggs in the morning.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.

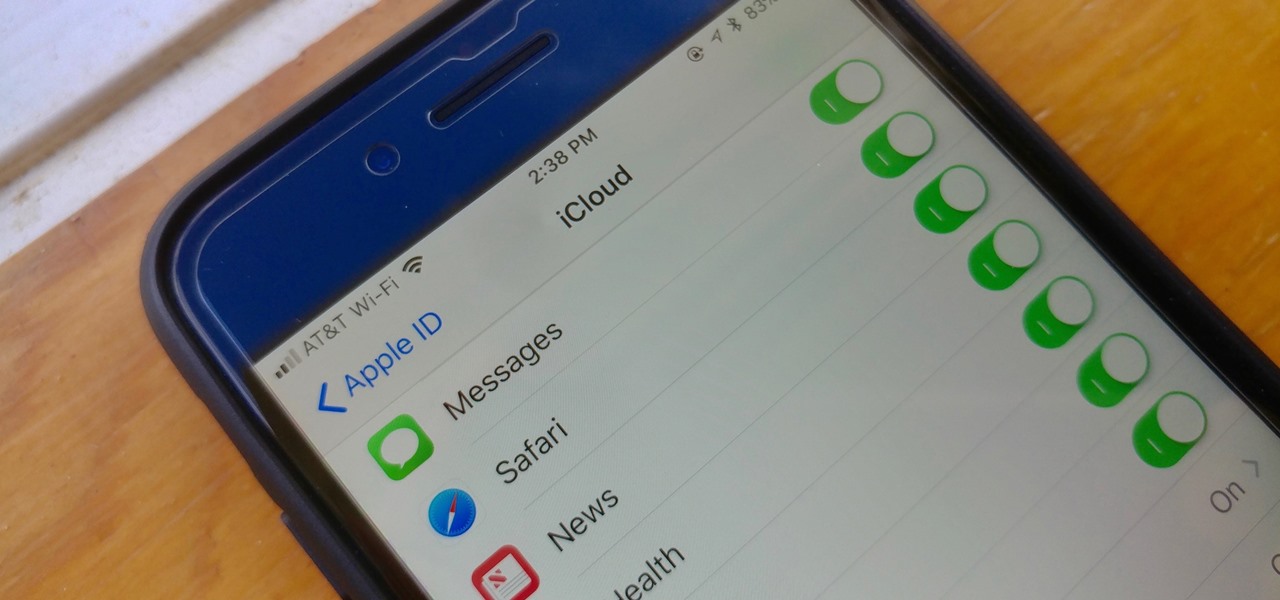
One major problem in previous iOS versions is that there was no way to keep messages in sync between an iPad, iPhone, iPod touch, and Mac. If you deleted a message in the Mac app, it would not be deleted on your iPhone, and vice versa. Apple finally fixed this issue in iOS 11.4 by storing all of the messages in iCloud, not on individual devices.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

Your iPhone just went missing, and now you're panicking. You need it for work, to get around, to contact your friends and family, and pretty much everything else in your life. So, what are the chances you might get it back? The odds may be stacked against you unless it's just under a couch cushion, but you can improve your chances of recovering your iPhone by taking certain steps.

Ceramic tile floors offer a very attractive and durable alternative to other floor finishes. They come in many different sizes and colors to match the décor of any room and they can provide years of maintenance-free use. Additionally, ceramic tiles are fairly easy to install. Ceramic tiles have one major prerequisite – you must have a smooth and rigid sub-floor to support the installation. Ceramic tiles are not flexible in the least, so they can crack if installed over a rough surface or thin...

Once you get past the initial quick start setup of the Canon EOS 5D Mark II, capturing pictures in auto mode is a breeze. But what do you do after you've snapped those photos? This quick guide will show you the easy steps to viewing your images directly on the camera.