Welcome back, my hackers novitiates! As you read my various hacking tutorials, you're probably asking yourself, "What are the chances that this hack will be detected and that I'll land behind bars, disappointing my dear mother who already thinks I'm a loser?"
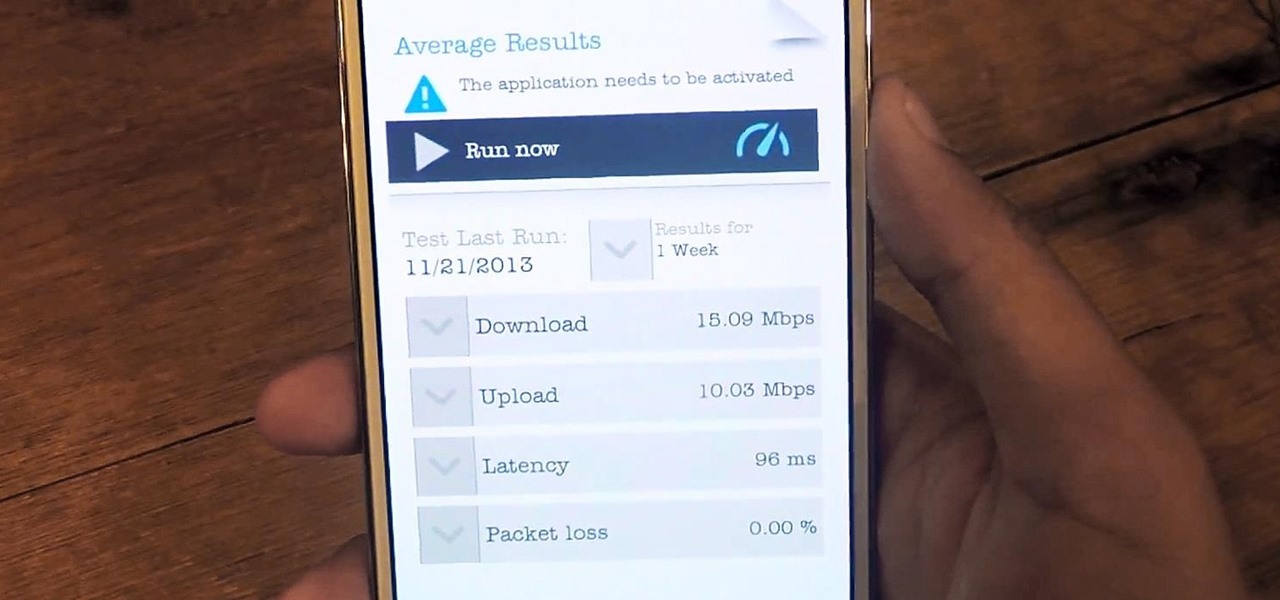
How to speed up your internet connection

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

What if someone asks you to do a Nmap scan but you left your pc at home? What if a golden opportunity shows during a pentest but you were walking around the building, taking a break?

Recently, there have been some questions regarding networking popping up and we have decided to put together this series to try and cover this gap.

Learn to do a small packet double lift card trick. With this video tutorial, you'll better your skills as a magician, and learn the proper techniques and presentation involved when performing a small double lift magic card trick. This is a great addition to your sleight of hand repertoire. Made by Richard Scorpio. Do a small packet double lift card trick.

Firesheep is a packet sniffing browser exploit that can access the exposed accounts of people on Facebook and Twitter while they use public Wi-Fi connections. This video shows what steps can be taken to protect yourself against someone accessing your Facebook account.

Here's how to make a fake blood packet, or squib to make it look like somebody got shot. It will explode when the bullet would hit. Cool special effect.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff.

To hack a Wi-Fi network using Kali Linux, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, so I've rounded up this list of 2019's best wireless network adapters for hacking on Kali Linux to get you started hacking both WEP and WPA Wi-Fi networks.

In this video, we learn how to easily make a no bank cheesecake. First, you will need to buy a Jell-O no bake cheesecake box and you will also need 1/2 stick butter, 1.5 c milk, 34 tbsp sugar, and a bowl. Now, take the butter and place it into a bowl and microwave it until melted. After this, add in the crust packet from the box and mix together with sugar using your hands. After you pack this down on the bottom of a pie pan, then pour the filling packet into a bowl and add in water with it, ...

In this tutorial, we learn how to cook a pork chop dinner in skillet rice with Jack Scalfani. Ingredients include: Rice-a-Roni, 2 tbsp butter, 2 1/2 cup water, and 3 pork chops. Place your skillet over high heat and drop in your butter and let melt. After the butter is melted, add in your Rice-a-Roni box and lower the flame to a medium. Don't add in the flavor packet that comes with the package just yet. SautŽ your rice and butter, mixing frequently until everything has browned. Now, add in y...

This video is a demonstration of how to make the perfect ramen noodles. The requirements for the recipe are 2 packets of ramen noodles, milk and vegetable oil. Using butter instead of oil enhances the taste of this recipe. Water is heated in a pan and the noddles are added to hot water. Let the water boil and cook the noodles till they turn soft. Drain the water from the noodles using a strainer and put it back in the pan. Add half a cap of vegetable oil to the strained noodles and mix thorou...

This video will show you how to prepare a Homemade Pot Roast. For this recipe, you will need: mushrooms, onions, zucchini, Brussels sprouts, oven roast bags, potatoes, carrots, wine, garlic, 1 can stewed tomatoes, McCormick Pot Roast in a Bag seasoning packet, and a pot roast.

This video demonstrates how bread crumbs can easily be made at home. Two methods are shown for this. For both the methods first bread has to be dried in oven at 230 degrees. For this you can use fresh bread or stale bread. After heating the bread should become dry and hard. In the first method, break the dried bread into smaller pieces and put in a blender. Start the blender and crush them. Your bread crumbs are ready. In the second method Put the dried bread in a plastic bag and close the ba...

Follow the simple ViewDo steps on how to make perfect Barbeque Beef Ribs. The first step will show you how long to sear the ribs on each side before applying your favorite barbeque sauce. Once the ribs are seared watch and follow the instructions on saucing then sealing the ribs within a packet made from aluminum foil that you will slowly cook and steam on your barbeque grill. After and one hour and a half, open your packet and you will have the perfect fall off the bone beef ribs! Enjoy!

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Lots of people have problems with XBox Live matchmaking due to the NAT for their network not being Open. It's not readily apparent how to make your NAT open, but this video will show you how to do it.

Welcome back, my fledgling hackers! A short while ago, I did a tutorial on conducting passive OS fingerprinting with p0f. As you remember, p0f is different from other operating system fingerprinting tools as it does not send any packets to the target, instead it simply takes packets off the wire and examines them to determine the operating system that sent them.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Google's new Project Fi cellular carrier has been making waves across the mobile industry, so we decided to put it to the test against T-Mobile, one of the more established networks. For the actual testing, we slapped a SIM card from each carrier into two identical Pixel XL phones, which offer full compatibility with both networks.

Welcome back, my greenhorn hackers! As expected with Null Byte's dramatic growth over the last year, we have added many new aspiring hackers who are still lacking in the basics of networking. In addition, with the new "White Hat" certifications coming out shortly, the exam will require some basic networking skills and knowledge to pass.

If you read my article on the OSI model, you got a good overview on communications from that model's perspective, but how does that relate to TCP/IP? We're going to take it a step further, getting into the idea behind the two address concept. How does an IP address and a MAC address work together? If you want to hijack sessions and all sorts of lulz like that, you need to understand these concepts. Let's get into it, mates!

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

The iPhone has always has one very big problem: that it is tied to AT&T. AT&T is a terrible network, and many iPhone users out there are probably dying to switch network but keep their awesome phone. Well now they can! This video will show you how to unlock you jailbroken iPhone 4, 3GS, or 3G using a program called Ultrasn0w, leaving it ready for use on any cell carrier in the country. Except Sprint, they don't have SIM cards.

If you're interested in installing an application that you can't find in the Android Market, you'll need to use an apk (or Android packet) file. Don't know how to load an apk onto your phone? No problem: this Android owner's guide will walk you through the process. You'll find that, with a file manager application like Astro File Manager, it's a snap.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to obscure your OS fingerprint.

Sure, you go online to email and shop and do research. But have you ever been curious about how the internet actually works? Don't worry, you don't need a degree in computer science to get a handle on how your info gets from point A to point B. Learning the basics of the internet will give you a whole new appreciation for all those emails and chat messages that seem to magically appear. Get ready, because we're about to enter the wonderful world of digital data!