In this tutorial Mike Lively of Northern Kentucky University shows you how to get started with Wireshark. Wireshark is a network protocol analyzer for Unix and Windows. It is used for network troubleshooting, analysis, software and communications protocol development.

This video demonstrates how to fold the origami model "Cigarette Packet" that David Brill designed. Dave kindly gave me permission to make this video accessible to you.

Welcome back, my tenderfoot hackers! As you should know from before, Snort is the most widely deployed intrusion detection system (IDS) in the world, and every hacker and IT security professional should be familiar with it. Hackers need to understand it for evasion, and IT security professionals to prevent intrusions. So a basic understanding of this ubiquitous IDS is crucial.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

This video shows how to make Trail Oatmeal for camping or hiking. In a Ziploc bag put some dehydrated fruit with cinnamon and a dash of salt added. In another bag put some quick cooking oatmeal, wheat germ, Fiber-sure, and brown sugar. Put the fruit packet in with the oatmeal packet, add a packet of peanut butter, and it’s ready to go.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

This video displays a very interesting experiment or magic trick involving the concepts of density and buoyancy. You will need an empty plastic bottle with its label removed, some water, and a ketchup packet. Using the concepts of pressure and density, this video demonstrates an interesting experiment which can also double as an interesting party trick; by squeezing a full water bottle, you can cause the ketchup packet to rise and sink in the bottle at your whim. This video is an interesting ...

When it comes to sniffing Wi-Fi, Wireshark is cross-platform and capable of capturing vast amounts of data. Making sense of that data is another task entirely. That's where Jupyter Notebook comes in. It can help analyze Wi-Fi packets and determine which networks a particular phone has connected to before, giving us insight into the identity of the owner.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

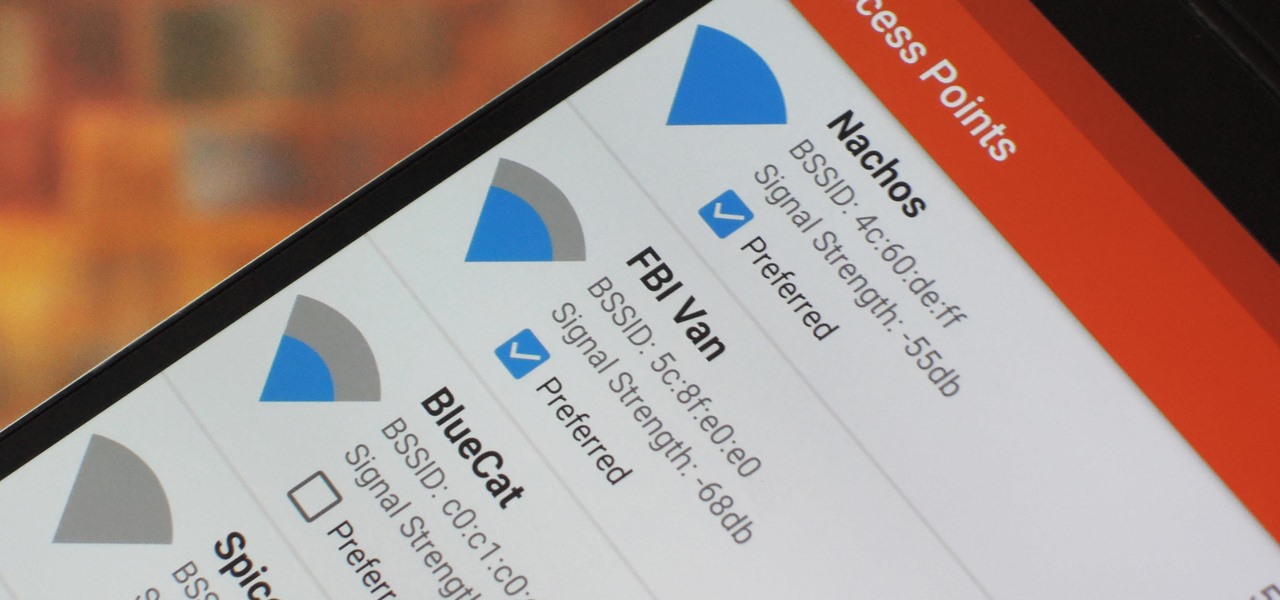
What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

Welcome back, my novice hackers! I have tried to emphasize throughout this "Hack Like a Pro" series that good reconnaissance is critical to effective hacking. As you have seen in many of these hacks, the techniques that we use are VERY specific to the:

Check out this tutorial for steps on how to perform a very cool slight of hand trick. In this video, learn how to take a solid sugar packet, toss it in the air and catch it - like a ring - around your pointer finger. Your audience will be totally amazed, but you will know the secret.

In this video tutorial, viewers learn how to do the swing false cut card trick. This cut makes it seem like the magician actually shuffled the deck. Hold the deck with one hand and cut a portion of it. Then lock the packet with your other hand's thumb and cut another portion of the decking, forming 3 packets. Put the top pack at the bottom as you pull out the center pack. Then swivel the packet on top to the other hand and drop the final pack on top. This video will benefit those viewers who ...

The goal of this video tutorial is to teach you how to perform the "coin through sugar packet" magic trick. This instructional is to help anyone wanting to be a magician, helping you understand technique and presentation of simple but effective illusions. These tricks are pretty easy, but with time, practice and patience you will be able to amaze your friends and your family. Learn the coin through a sugar packet magic prop trick.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build a firewall from a junk PC to protect networks.

When making Coconut Kefir you should use young ty coconut from a whole foods store because it will be sweet. You will also need a product called Kefir starter. Open your coconut and strain out the water and remember to save the meat from the coconut. Heat the water from the coconut to about body temp. Once heated pour the water into a large jar and add a packet of kefir. The Kefir packets should be measured one packet to one quart of water. You will need to store your kefir in an airtight con...

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Watch this instructional magic card trick tutorial to learn how to perform the binary routine. This is an original series of user-created moves. There are 9 phases of the Binary Routine, 6 of which are false, and the other 3 are closers that involve a color card change at the end. This video provides instruction on 2 false cuts and 1 closer, along with some possible variations. Just keep in mind, there is room for adjustment with these phases. If you find a better way to do a certain move, th...

You're in your car. You've got a bag of piping-hot French fries with you. You want those fries in your mouth ASAP, but you also want to dip them in ketchup. So what do you do?

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

ARP spoofing is an attack against an Ethernet or Wi-Fi network to get between the router and the target user. In an ARP-spoofing attack, messages meant for the target are sent to the attacker instead, allowing the attacker to spy on, deny service to, or man-in-the-middle a target. One of the most popular tools for performing this attack is Ettercap, which comes preinstalled on Kali Linux.

Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

Welcome back, my fledgling hackers! In the first part of my series on Wi-Fi hacking, we discussed the basic terms and technologies associated with Wi-Fi. Now that you have a firm grip on what Wi-Fi is exactly and how it works, we can start diving into more advance topics on how to hack Wi-Fi.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

If you own a Pixel or Nexus device, Project Fi is a great alternative for cellular service outside of the four major US carriers. Project Fi is a Google-managed MVNO, providing service primarily through the T-Mobile and Sprint networks. One of the biggest mysteries on Fi is which network you're connected to at any given time, but there's a simple solution.

Welcome back everyone. I apologize for the lack of training articles, but I've been rater busy lately. I've recently picked up a second job and my college courses are now back in session, so I'm a bit strapped for time.

In recent weeks, major bank websites around the world have experienced outages after being have been hit with Distributed Denial of Service (DDoS) attacks. Although few, if any, of these banks have been totally knocked offline, these DoS attacks have dramatically slowed the response time of their websites to legitimate customers. The most recent victim was the Royal Bank of Scotland. Due to this attack, RBS customers were unable to access their accounts for about an hour last week.

Welcome back, my fledgling hackers! Nearly every commercial enterprise worth hacking has an intrusion detection system (IDS). These network intrusion detection systems are designed to detect any malicious activity on the network. That means you!

This tutorial shows you how to make spell packets. It's designed for NERO, but many larps use the same rules. All you need is a square of natural fiber cloth (like cotton), some birdseed (or rice or crushed walnut shells or any biodegradable matter) and a rubber band.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

How to speed up your internet connection

The archenemies of cell phones— puddles, toilets, swimming pools— can cause serious damage to your gadgets. And if your mobile phone has taken the dive, don't panic— there's hope for recovery.

After a long marathon run, runners like to refresh with a nice bottle - or ten - of water. But if you've ever run for an extended period of time, especially in high heat, you know that you not only lose water through sweat, but also electrolytes and salts that help keep your energy up.

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

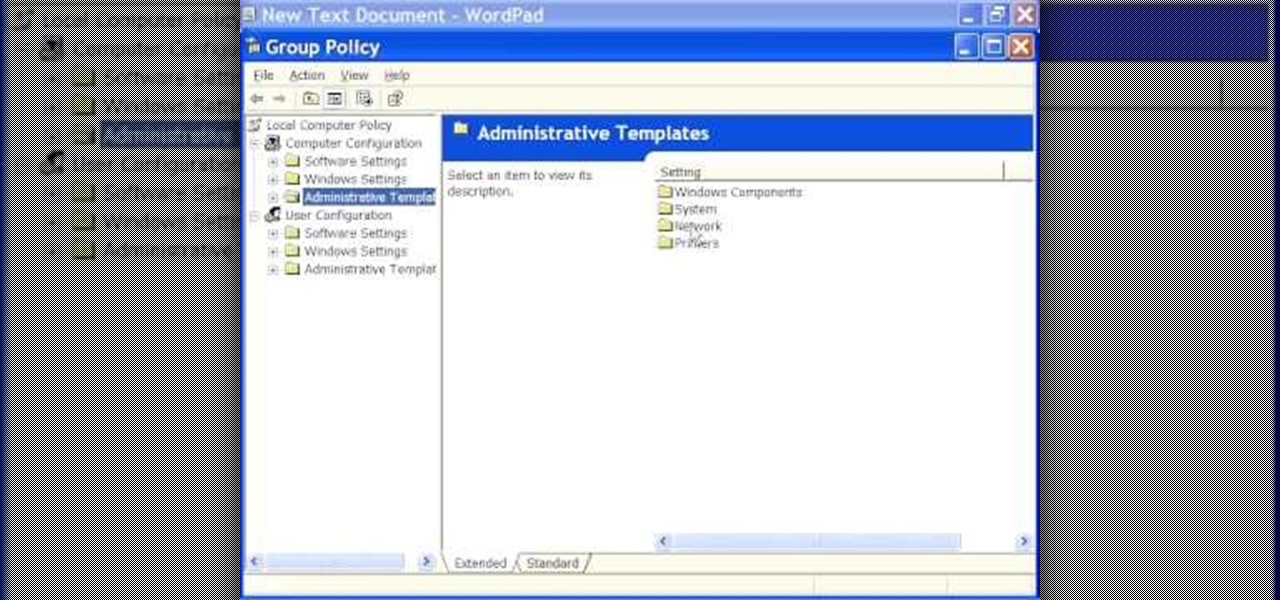
It has been a while since my last Raspberry Pi tutorial , but now I am back with another tutorial. This one I should note isn't your typical tutorial, but as always lets boot up our Pi and wreck havoc.