
How To: Diagnose and treat a biceps tear
The biceps tendon attaches the biceps muscle to the radius. Learn how to diagnose and treat a biceps tendon tear in this medical how-to video. Usually the area is painful, swollen and bruised.


The biceps tendon attaches the biceps muscle to the radius. Learn how to diagnose and treat a biceps tendon tear in this medical how-to video. Usually the area is painful, swollen and bruised.

This video lesson introduces a basic philosophy on chicken pickin' or country playing. For country guitar playing, you don't need to use much in the way of effects, just a tiny bit of reverb and compression. Country isn’t dependent on one set of scales, like rock or blues. To play country, you must play over the chords much like a bluegrass or jazz player. It is no coincidence that many country players are also jazz players and vice versa. Every chord has different lines, chord shapes, or rif...

Ionian mode is the first of the modes, and in a way, is the major scale! It has the same steps as the major scale, for those of you playing from home that's whole step, whole step, half step, whole step, whole step, whole step, half step! In this video you will learn how to play and apply the Ionian mode on the guitar!

Don't wait for a full moon to unleash your inner beast. Get your growl on with these tips on creating the ultimate werewolf mask.
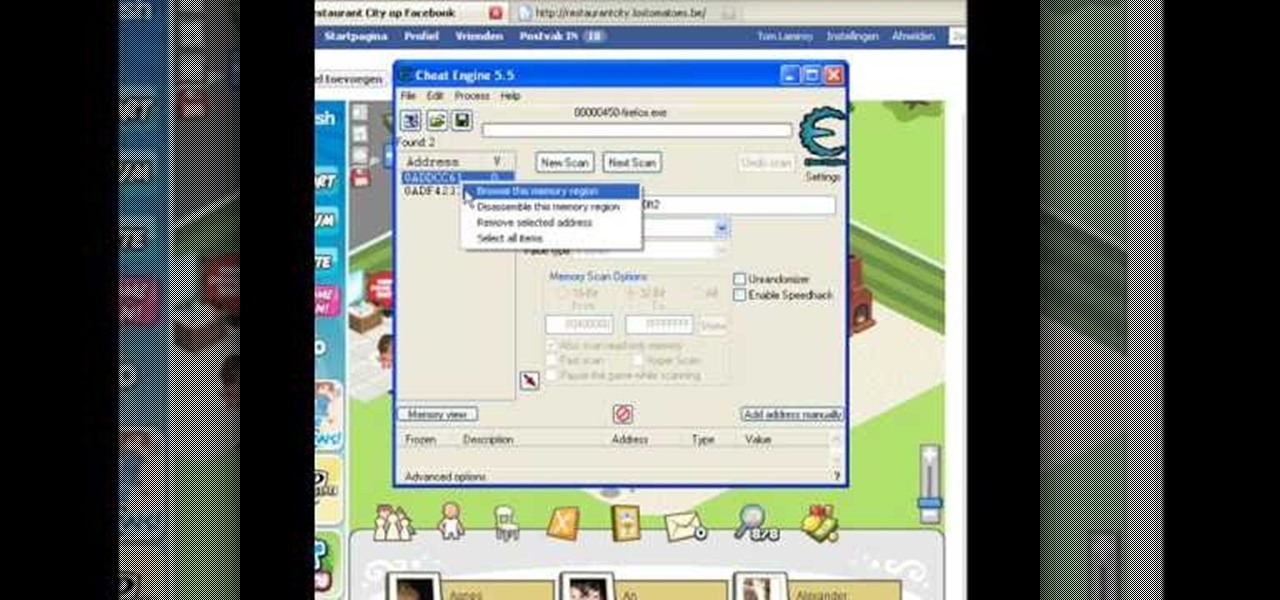
Make sure you use FLASH Player 9 First: Deinstall Flash Player 10

This instructional video teaches how to draw a variety of basic cartoon faces. Learn how to make simple changes to sketch different comic characters.

Your Instagram feed is jam-packed with interesting and lively photos, videos, and stories that largely offset the iOS app's comparatively bland user interface. If the interface's dull colors have always bothered you, you can splash on some much-needed color to better reflect your personality and tastes.
Many apps claim to record phone calls on Android, but very few actually deliver. There's just too many different devices floating around out there for one app to be able to support them all — or so it would seem.
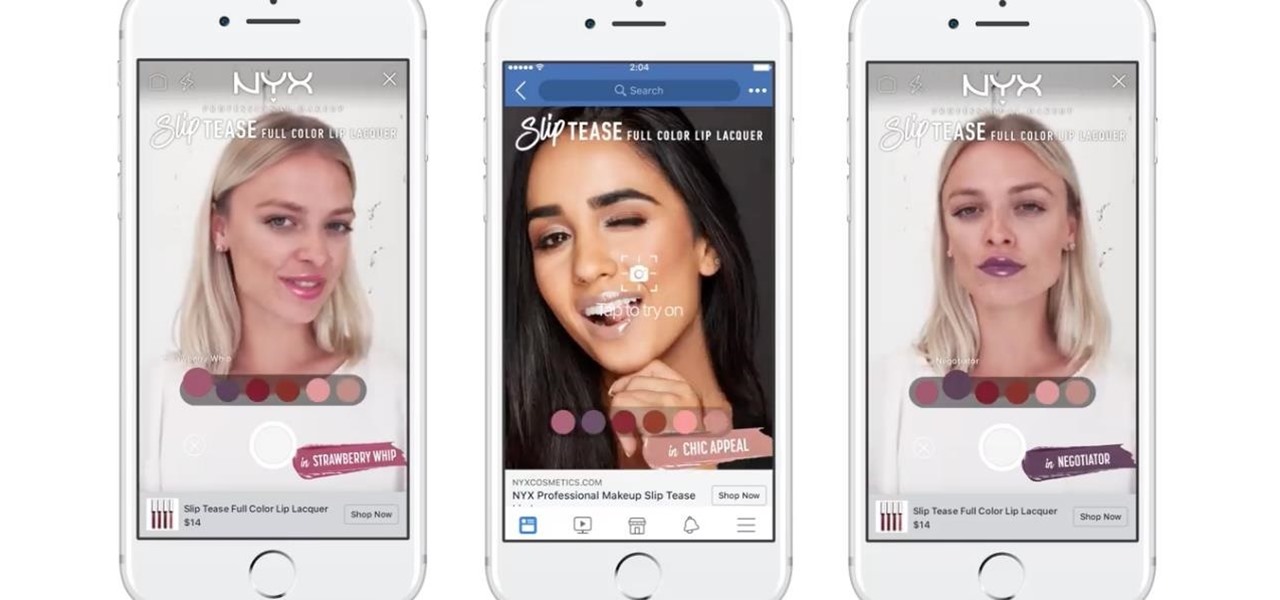
Already one of the leaders in augmented reality for cosmetics, L'Oréal is extending the reach of its ModiFace virtual try-on platform through a partnership with Facebook.

Augmented reality is really picking up steam as a tool for marketing departments to pitch their products.
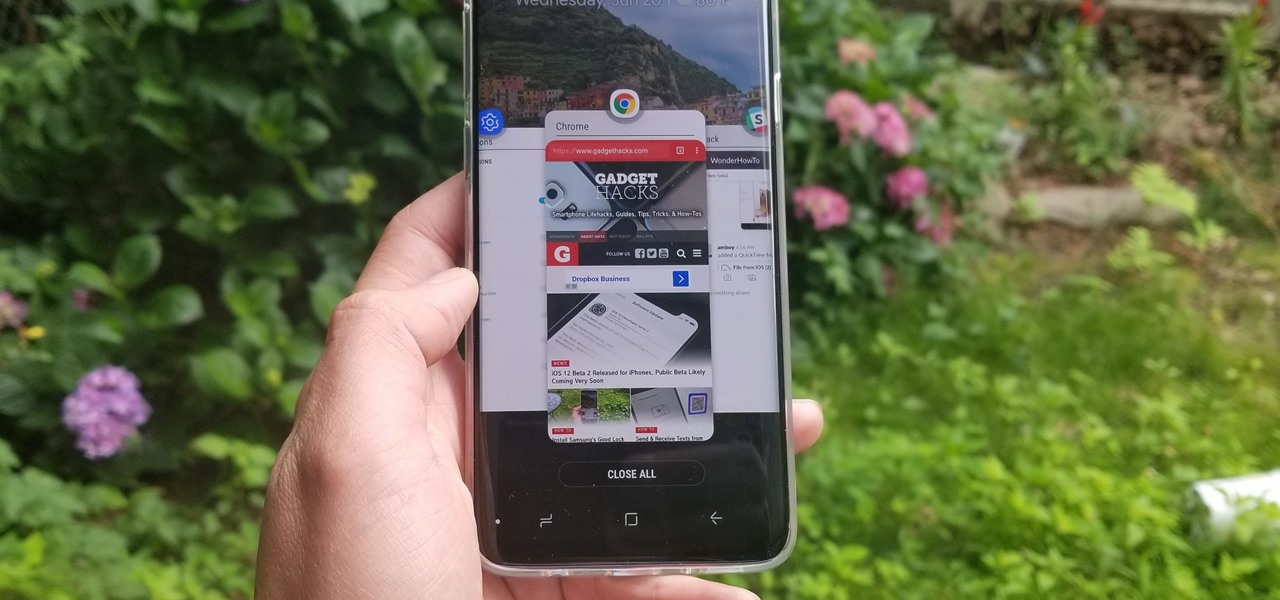
A revamped Recent Apps overview is one of the most significant changes set to arrive with Android P when it touches down later this year. Incredibly, Samsung has beaten Google to the punch, and has made this feature available for all its Oreo-based Galaxy handsets courtesy of its Good Locks app.
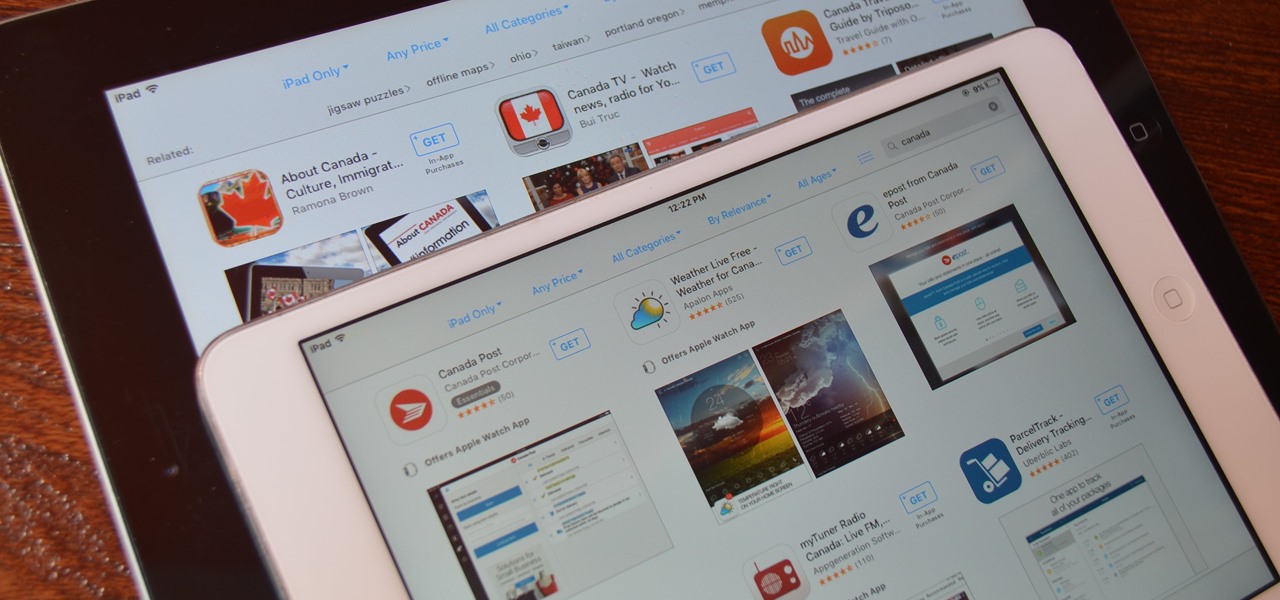
Before many games make it to the US-based iOS App Store, they get "soft launched" in a smaller country to get real-world testing for bugs. It's a pilot program, so to speak, as countries like Vietnam or the Philippines have far fewer iPhone users than the US, thus offer a more controlled environment for developers to get feedback and zero-in on issues that may occur in a game's early development phases.

Welcome back my, tenderfoot hackers! Many people come to Null Byte looking to hack Facebook without the requisite skills to do so. Facebook is far from unhackable, but to do so, you will need some skills, and skill development is what Null Byte is all about.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, my tenderfoot hackers! Web apps are often the best vector to an organization's server/database, an entry point to their entire internal network. By definition, the web app is designed to take an input from the user and send that input back to the server or database. In this way, the attacker can send their malicious input back to the servers and network if the web app is not properly secured.

Welcome back, my tenderfoot hackers! A number of you have written me telling me how much you enjoy the Mr. Robot series on USA Network. I am also a huge fan! If you haven't seen it yet, you should. It may be the best show on TV right now.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!

Welcome back, my hacker novitiates!

Welcome back , my fledgling hackers! Lately, I've been focusing more on client-side hacks. While web servers, database servers, and file servers have garnered increased protection, the client-side remains extremely vulnerable, and there is much to teach. This time, we'll look at inserting a listener (rootkit) inside a PDF file, exploiting a vulnerability in Adobe's Reader.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Successful public speaking is a product of numerous considerations. Become a successful public speaker with tips from an award-winning speaker in this free communication video series.

Is it just me, or are the thumbnail in the Samsung Gallery app a bit small? I spend quite a bit of time looking through rows of images, one at a time, to find the right photo. Wouldn't it be so much easier if the thumbnails showed the entire image instead of a cropped square? Well, there's a way to do just that.
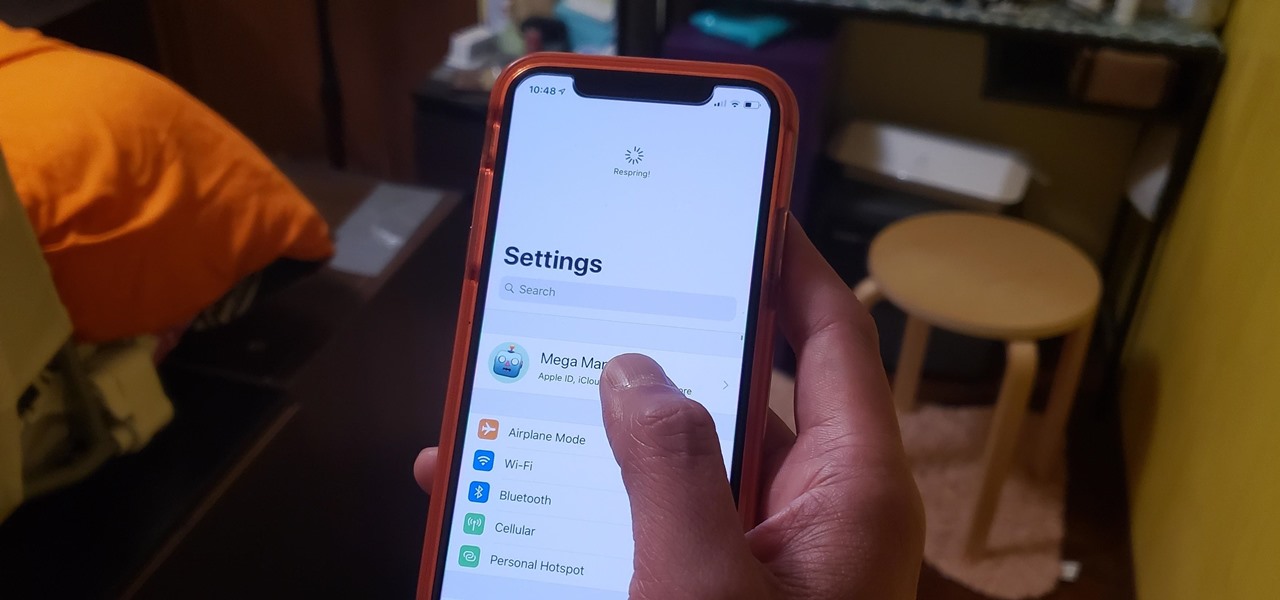
Restarting your iPhone can cure software glitches, but it should only be done as a last resort if your device has a semi-tethered jailbreak, because it will disable any tweaks you've applied. Luckily, your jailbroken iPhone has a faster alternative to rebooting to help you troubleshoot and make changes on the fly.

Apple might be a secretive company, but it's showing its hand these past few weeks. The release of iOS 13 was met with much excitement for its hundreds of new features but also frustration over the numerous bugs. Apple soon released iOS 13.1, then iOS 13.1.1, as a patch for some of those bugs, but clearly they weren't enough. How do we know? The company just released iOS 13.1.2 today, Monday, Sept. 30.

The promotions around last week's release of Stranger Things 3 have been numerous, with Netflix at one point even taking over an entire baseball field via augmented reality.
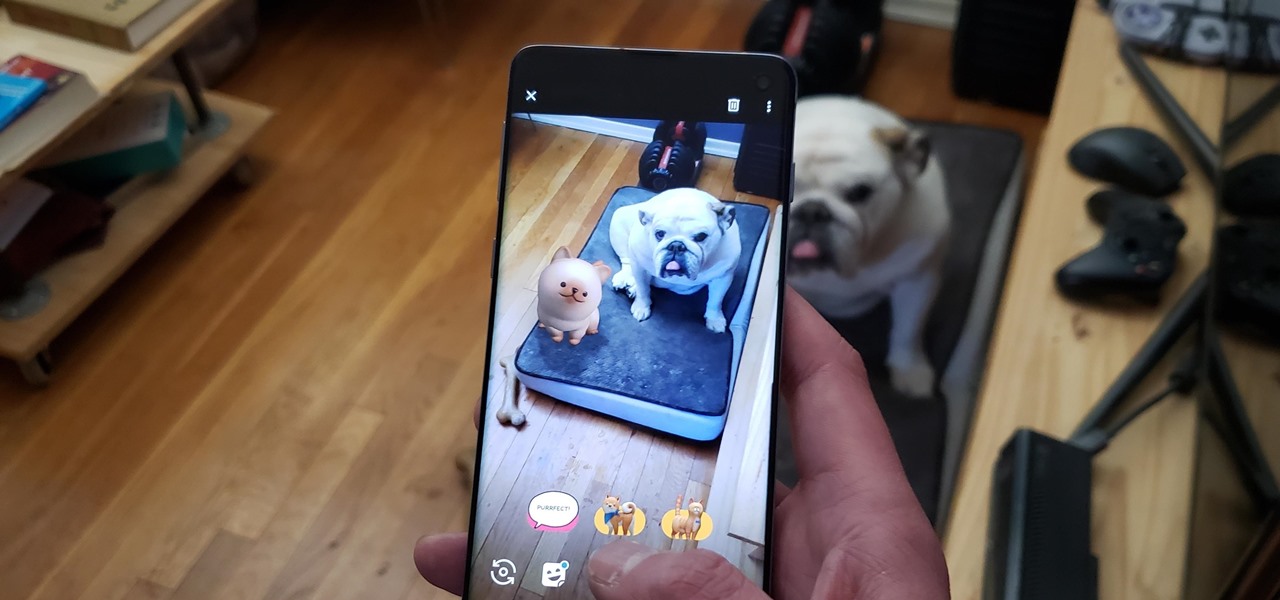
Google's has expanded ARCore support to numerous Android flagships like the Galaxy S10, so if you have a compatible device, you get access to all the cool new apps that can augment the world around you. One of ARCore's most sought-after features, AR Stickers, is normally exclusive to Google's Pixel lineup, but by sideloading the Google Camera app, you can try it on any ARCore device.
Thanks to Samsung's One UI, we can now experience firsthand what Android 9.0 Pie has to offer flagship Galaxy devices like the Note 9, S9, and S8. Perhaps one of the best features is something we've all been clamoring for: a system-wide dark theme that gives numerous apps and UI elements a custom look without having to resort to using a third-party theme.

While numerous examples exist of hospitals deploying the HoloLens to assist doctors, surgeons, medical professionals, and students while treating patients, California's Lucile Packard Children's Hospital Stanford is actually using the augmented reality headset to improve the patient's experience.

Hip-hop artist Drake once rapped that "goin' online...ain't part of (his) day," but that's not stopping him from promoting his new double album, Scorpion, via augmented reality on Snapchat.
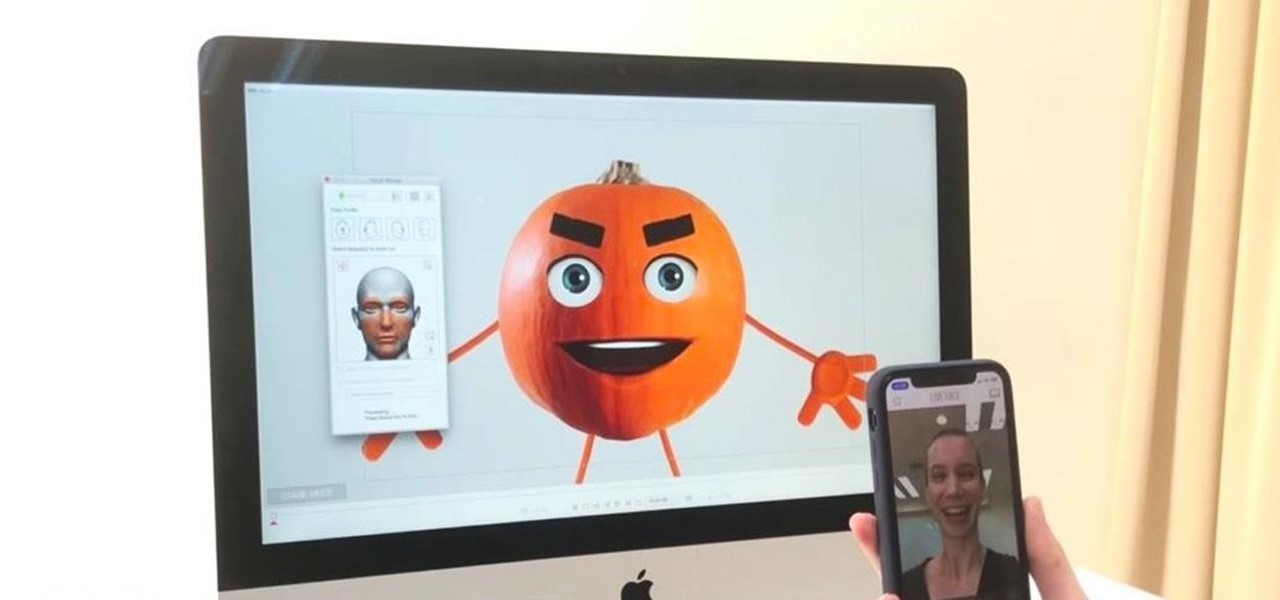
While 3D motion capture via iPhone X is coming soon from Unity, software maker Reallusion offers similar functionality to 3D model animation producers today.

While Apple has generally been more bullish on augmented reality as opposed to virtual reality, the latest whispers about its purported AR headset suggests that it may be giving VR another look.
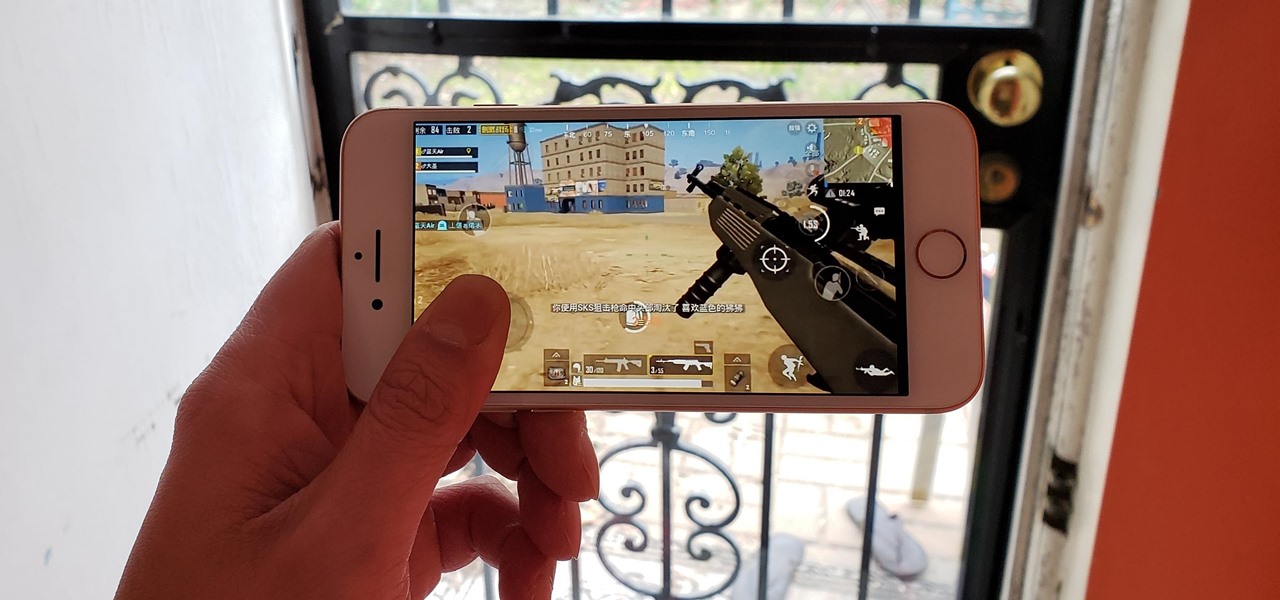
The recent 0.4.0 update for PUBG Mobile brought us a host of welcome features like the training ground and arcade mode. Sadly, one highly sought-after feature remained out of our reach: The ability to play in first person perspective, or FPP mode. Our wait may soon be over, as this gameplay mode could be out as soon as the next update hits for both Android and iOS.

With numerous insider reports, patent awards, acquisitions, and hires over the past few years, augmented reality smartglasses from Apple appear to be an inevitability.

Location services provider Mapbox is giving developers a means for building location-based AR apps and multi-user experiences with its new Mapbox AR toolkit.