Learn the basics of friendship bracelet making with this easy to understand video. You will learn what is known as the forward knot, the backwards knot, the forward-backwards knot and the backwards-forward knot. With these simple instructions, you can make countless bracelets for friends and family. There are numerous videos showing the how-to of friendship bracelet making, but this video gets back to basics. After you make the knots, you are free to pick a design of your choosing for your br...

Captioning your YouTube videos not only makes them more acessable for the hearing impaired, but they also make the contents of your video more accessible to YouTube. Once YouTube knows exactly what is being said it your video you will be more likely to rank when people search for related words or phrases.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.

Do you ever feel as if your mind is running away from you? What if you could map out all of those thoughts into a coherent map that helps you make sense of your reality? Well, now you can.

Samsung reintroduced its well regarded Good Lock app, so now you can tweak parts of your Galaxy's interface without the need for root or other labor-intensive mods. Thanks to an awesome add-on, you can even tidy up you phone's status bar — so if you've always wanted to get rid of that pesky NFC "N" icon or any other indicator at the top of your display, you're now just a few taps away.

Welcome back, my greenhorn hackers!

Seemingly lost in the fanfare of the numerous features and specs of the Nexus 5 were a few highly innovative and handy add-ons—a low-power step detector and step-counting sensor—useful for tracking fitness data.

Having trouble getting a strong Wi-Fi signal on your Samsung Galaxy S3? Does the signal drop out on you when changing rooms? Frustrating, isn't it?

Today, Facebook Messenger is rolling out Discover, a feature that helps you chat with companies and locate nearby businesses of interest to you. First discussed in April at Facebook's developer conference F8, Discover is finally available for public use.

Welcome back, my budding hackers! In this series, I have been trying to familiarize you with the many features of the world's best framework for exploitation, hacking, and pentesting, Metasploit. There are so many features, and techniques for using those features, that few pentesters/hackers are aware of all of them.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Welcome back, my hacker novitiates! In an earlier tutorial, I had introduced you to two essential tools for cracking online passwords—Tamper Data and THC-Hydra. In that guide, I promised to follow up with another tutorial on how to use THC-Hydra against web forms, so here we go. Although you can use Tamper Data for this purpose, I want to introduce you to another tool that is built into Kali, Burp Suite.

Welcome back, my amateur hackers! Many of you here are new to hacking. If so, I strongly recommend that each of you set up a "laboratory" to practice your hacks. Just like any discipline, you need to practice, practice, and practice some more before you take it out to the real world.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Samsung does a good job of making their devices fairly open, and the Galaxy S3 is no different. There are numerous way to root a device, but sometimes the jargon and steps can be a little intimidating for new rooters, and even pro rooters.

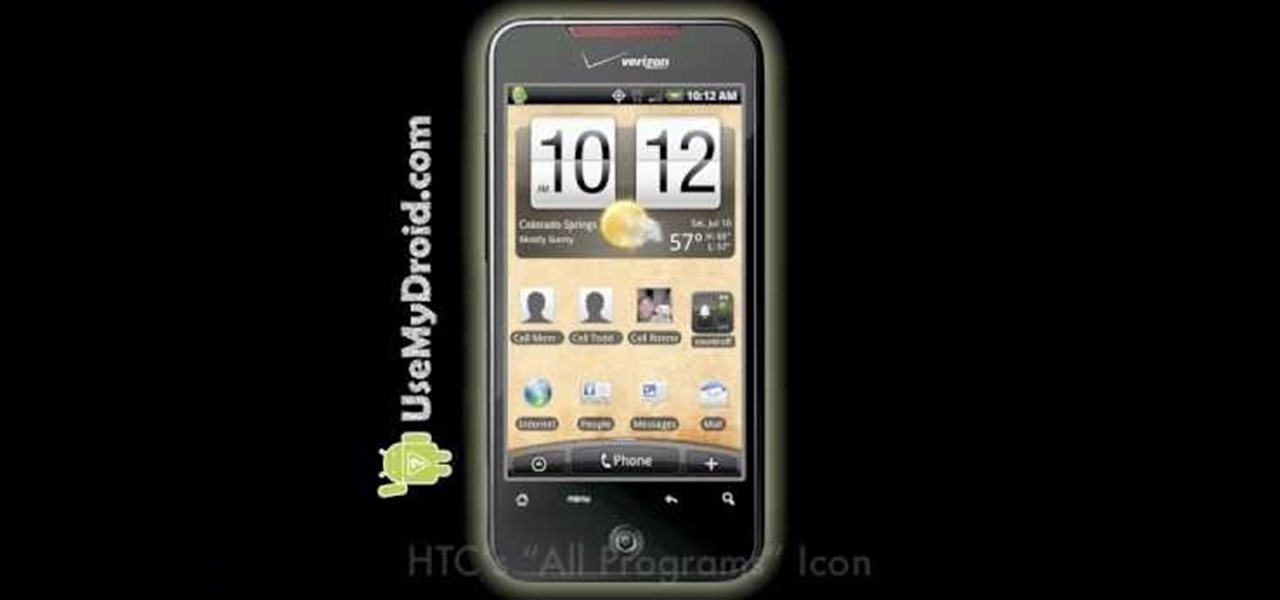
In this video tutorial, anyone who owns a Droid smartphone can learn how to better navigate their home screen. With this Droid phone tips, you'll be able to maximize your time and create shortcuts to your most used applications. The Droid's home screen in much like a computer's desktop; putting an icon on one of your Droid home screens allows you quick access to a program or app. There are numerous Android phones, but this video focuses on the "Droid" versions, but you may need to play around...

Pixel Perfect is the "perfect" show to help you with your Photoshop skills. Be amazed and learn as master digital artist Bert Monroy takes a stylus and a digital pad and treats it as Monet and Picasso do with oil and canvas. Learn the tips and tricks you need to whip those digital pictures into shape with Adobe Photoshop and Illustrator. In this episode, Ben shows you how to build an Egyptian Pharaoh's room in Photoshop.

Check out this strength trick from Revision3, Brian Brushwood and Scam School. We're back with another dirty trick, designed to teach you how to FAKE your way into (almost) duplicating the feats of the world's strongest men.

We've all been hit by inopportune screen rotations at some point or another. Having the display orientation suddenly go from portrait to landscape when reading an interesting article in bed is one of the biggest irritations that come with using a smartphone (at least, for me). Thankfully, there are apps out there for your Android to help alleviate this inconvenience.

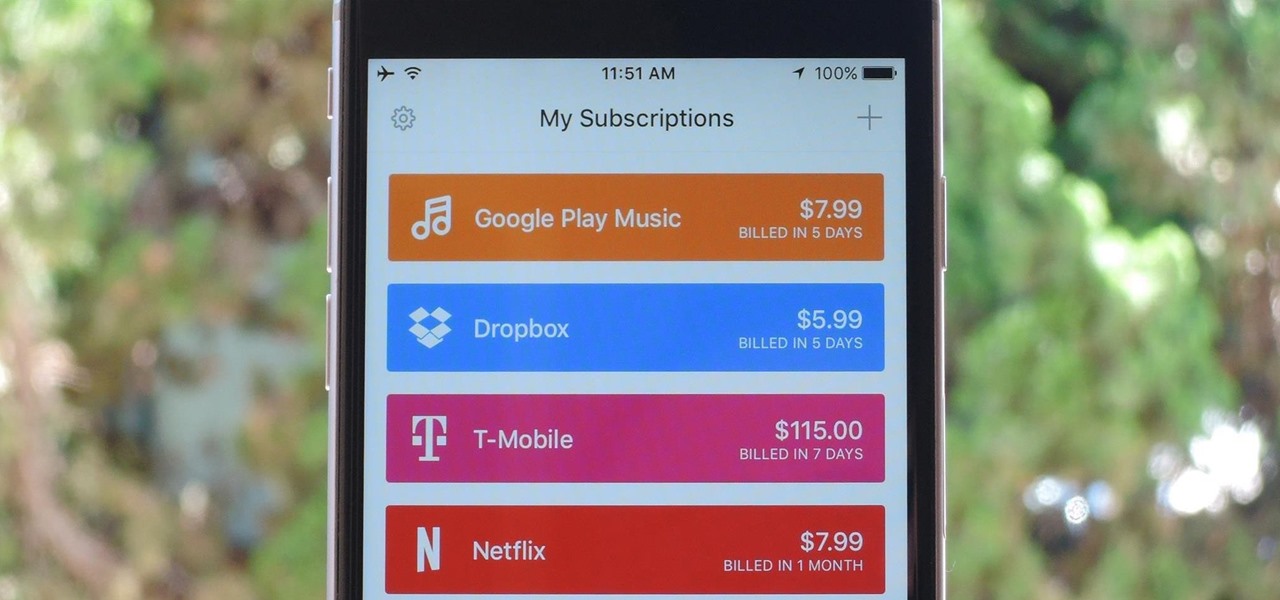
As the internet continues to become a bigger part of our day-to-day lives, we slowly but surely start to rack up a bunch of web-based subscriptions. These internet subscription services—Netflix, Hulu, and Amazon Prime, just to name a few—may seem innocuously cheap individually, but when combined, they actually comprise a significant portion of our monthly bills.

I'm a firm believer that a sandwich is the ultimate food. It's filling, but not heavy; it has carbs, protein, veggies, and sauces; and it's easily customizable. Add that all up and you've got the absolutely perfect lunch.

Welcome back, my neophyte hackers! In previous tutorials, we learned how to steal system tokens that we could use to access resources, how to use hashdump to pull password hashes from a local system, and how to grab password hashes from a local system and crack them.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Welcome back, my tenderfoot hackers! In some of my past articles, I've shown numerous ways of embedding a listener/rootkit on a remote system, including buffer overflows of the operating system, getting the victim to click on a link to our malicious website, and sending a malicious Microsoft Office and Adobe Acrobat file.

Ipad is a revolutionary device from Apple with some amazing features. One of the major functions of Ipad is to serve as a E-book reader. Apple provides an application called Ibooks using which you can read ebooks on your device. You can also browse and purchase new ebooks using this applications. Launch Ibooks from your applications menu and it will take you to the collection of books that you already have on your device. Click the store button to visit the books store. From the store you can...

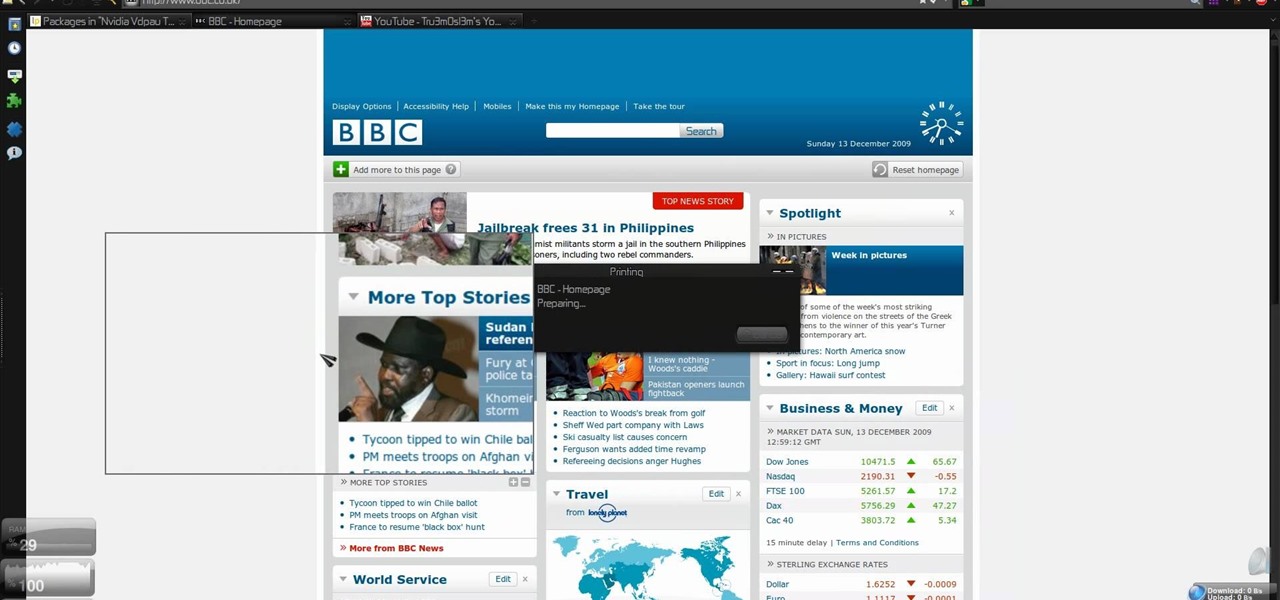
There's plenty of reasons why one would want to convert a webpage to a PDF document. And there's numerous ways on how one can convert that web page (HTML) into a PDF file. Check out this video tutorial on how to convert webpage HTML to PDF on Ubuntu Linux.

Check out this Scam School video on leanring the ultimate strength tricks. Bend frying pans and horseshoes with your bare hands! Watch Brian make you think he can use his bare hands to bend a horseshoe and to roll a frying pan!

Essential just dropped the Oreo Beta Program for their flagship PH-1 phone. Users have been eagerly awaiting this update as the early Nougat builds of the PH-1 software have suffered from numerous performance issues and lag. The good news is that you can grab the Oreo update today with a few simple steps.

I was fortunate enough to be visiting one of my college classmates in Columbus, GA last spring and saw two large bags of onions in his kitchen... but not like the ones you get at the grocery store. Two standing 50 lb. bags!

Here's a fact that everyone knows: avocados are delicious in guacamole, salads, and sandwiches. Here's a fact that's less commonly known: avocados are delicious in desserts, too.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

With all of the different websites we use in our day-to-day lives, keeping track of our numerous login credentials can start to become a hassle. This has created a market for password managers that aim to centralize these account credentials and generally streamline the process of logging into our favorite sites.

With over a million apps available in the App Store, you'd think that Apple would have come up with a better way to organize them on your iPhone.

In this how to video, you will learn how to draw Broly. First, start out with an oval shape for the face. Next, add another for the ear. From here, you can add the neck, shoulders, and chest. Next, draw numerous spikes for the hair. The basic outline is complete. Go into the drawing with more detail by adding lines inside the spikes to simulate hair strands. Add the eyebrows, eyes, nose, and mouth. Next, draw in the muscles of the shoulders and chest. Add the outline of the necklace. Now you ...