
How To: Protect yourself from the RIAA and malicious websites
Peerguardian2: Block the RIAA and Malicious IPs +Mac/Win. Doesn't block http traffic though, and it's not very accurate and won't make a difference.


Peerguardian2: Block the RIAA and Malicious IPs +Mac/Win. Doesn't block http traffic though, and it's not very accurate and won't make a difference.

Link shorteners like TinyURL and Bitly are great for Twitter (or anytime you're limited on space), but they're also great for hackers. It's easy to hide a malicious link in an innocent-looking shortened URL, which increases the chances that people will click on it.

Want to know how to make HijackThis, the popular malware scanning program, display only malicious registry entries? Learn how to use the Ignore List to acheive just that with this free home computing how-to from the folks at CNET TV, which offers complete instructions on how to tweak HijackThis to make removing viruses and spyware a breeze. For more information, and to get started protecting your own Windows PC from malicious software, watch this handy how-to.
Last week, NowSecure security researchers revealed that nearly 600m Samsung mobile devices are vulnerable to a type of MitM attack.

In this tutorial, we learn how to protect a Windows PC from spyware & malicious software with Dave. You can get spyware from downloading random things, so a great way to make sure you don't download these things, is to use Firefox and search your items before you download them. If you do happen to get these, use SpyBot to find and destroy the viruses you have downloaded. It's free to download, you just have to search it on Google, then download and install it. This will help save your compute...

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.
If your computer is working slow--or not at all, there could be some unsavory programs running amok in your system. Trojans, malware, viruses, and hacks are dangerous to the health of your operating system. This video tutorial demonstrates the measures to take in order to rid your PC of malicious programs. Stop being bullied by harmful applications and use such programs as AVG Antivirus and Malwarebytes to protect your computer. Once you've cleaned up your system, be sure to configure your se...
Veronica Belmont shows how to get rid of browser cookies. She starts with explaining what a cookies is, that it is a small file downloaded to the computer from the internet so that the website can remember more information about the users, which she says is quite helpful if you visit a website regularly. She also explains about some malicious cookies which track user actions and report to websites. She now explains how to open options in Firefox browser or settings in Internet Explorer and wh...
If you're concerned that your computer has been infected by spyware and other malicious programs, watch this informational video and find out how to clean and restore your computer back to a normal bill of health. This informative tutorial shows various methods that can be used to disinfect your computer and rid it of those nasty viruses once and for all!

Even if your body doesn't melt at the thought of Edward Cullen and you think the vampire fad is the most malicious prepubescent girl malady since N'Sync, you have to admit the CW drama "The Vampire Diaries" is pretty addicting.
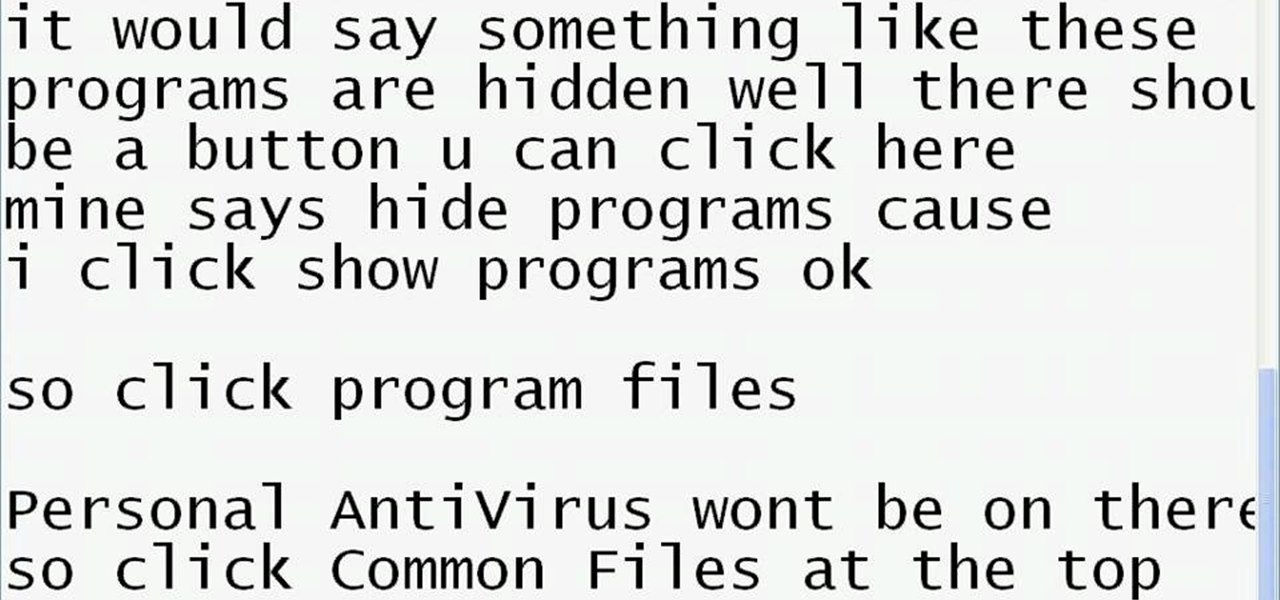
See how to remove Personal Antivirus from your Windows PC. The Personal Antivirus malicious software is a tricky malware to remove. This is the easiest way to remove Personal Antivirus from your home computer, so watch and get rid of it!
Did you know that malicious people can use scanners to read the Radio Frequency Identification (RFID) chips in your credit cards and identification documents and steal your personal information? Learn to protect your personal information from hackers and scammers with this simple method involving aluminum foil.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.
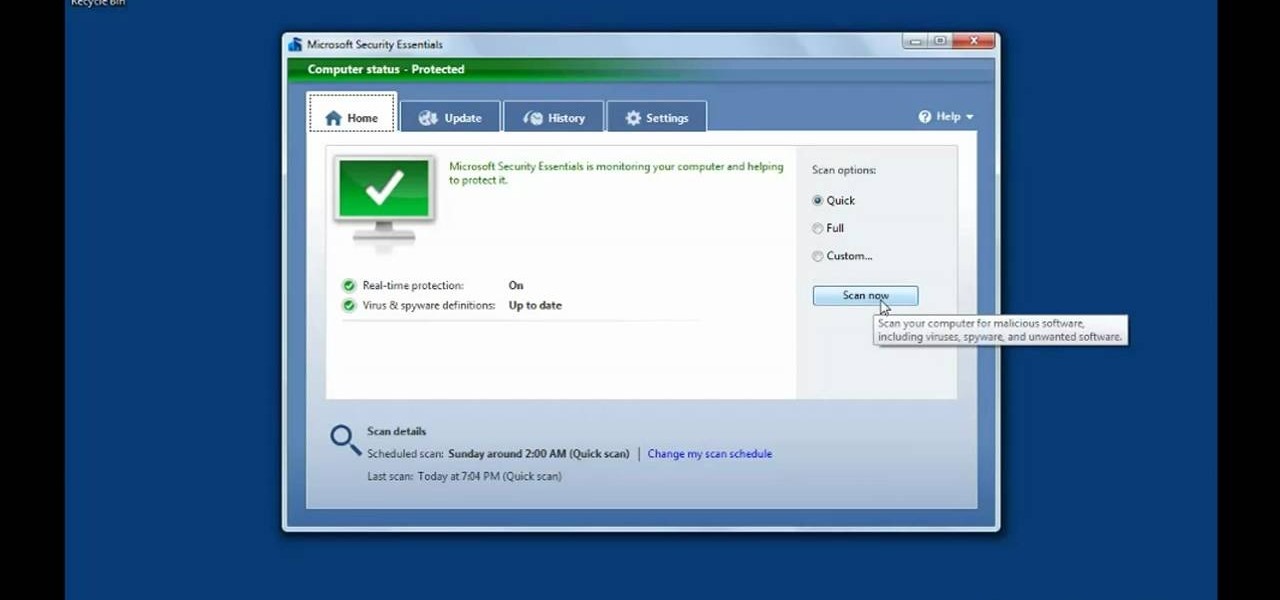
Looking for a guide on how to protect a Microsoft Windows desktop computer or laptop from viruses, spamware and other malicious software? This clip provides a very good starting point. For complete details, and to et started protecting your own Windows PC from viruses, watch this home-computing how-to.

See how to protect your home computer from spyware. This home-computing how-to from the folks at CNET TV will teach you what you'll need to know to do just that. For more information, and to get started protecting your Windows PC and your own privacy, watch this helpful video guide.

You've probably heard a lot about computer viruses — but how do you stop them? This home-computing how-to from the folks at CNET TV will teach you what you'll need to know. For detailed information, and to get started protecting your own Windows PC from malicious code, watch this helpful video guide.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.
Firesheep! It's a good reason to be cautious when using public Wi-Fi. But is it reason to stay off of open networks altogether? Certainly not! There are, in fact, a few simple steps you can take that will make you invulnerable to the malicious Firesheep Firefox addon. Learn how to protect yourself against Firesheep with this video guide.
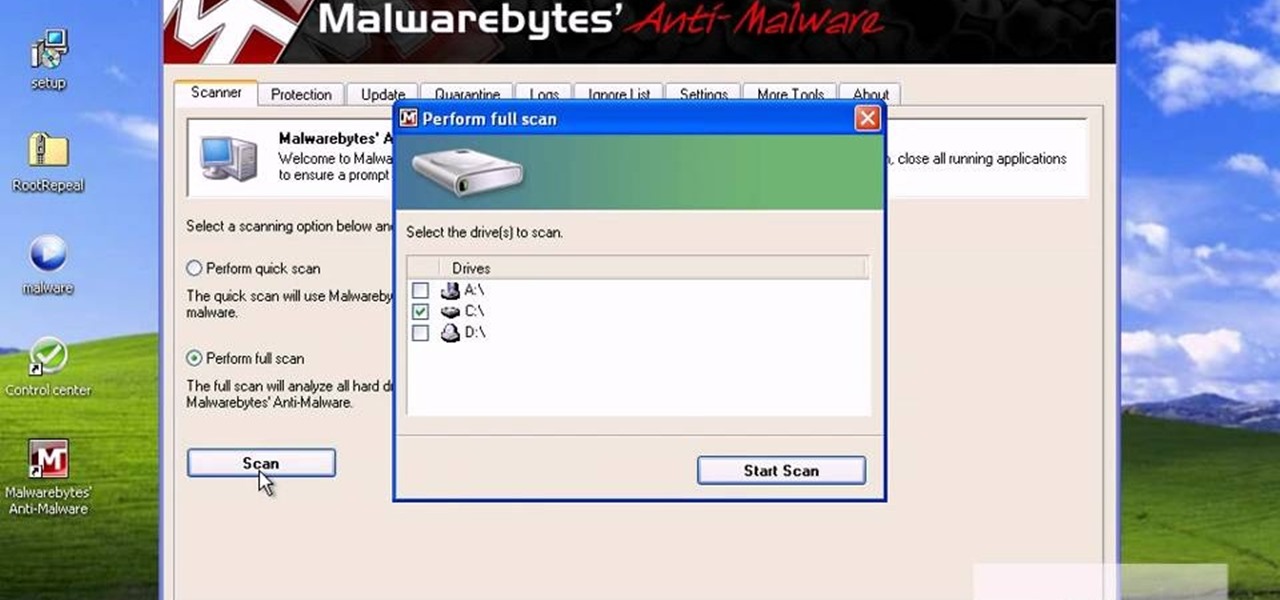
Trojans, viruses, and malware can be more than a simple nuisance to your computer--they can destroy data and ruin your system. This video tutorial shows how to get rid of malicious software on your computer. When combating a virus, it's best to use multiple applications to insure system extraction.

If your iPhone is rebooting or your Messages app is constantly crashing, you might be the victim of an iOS exploit or just a buggy software update. While one problem sounds worse than the other, they both can get annoying real quick when you can't send any messages or even read new ones.

While clicking random links on the internet probably isn't the best idea to begin with, now you can rest easy knowing that your iPhone won't repeatedly dial 911 after tapping a malicious link in Twitter, Facebook, or other apps that use iOS's WebView.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Hello everyone. I'm Calypsus and i've been around for a while learning from various tutorials, expanding my knowledge and this is one of the best platforms for newbies to sharpen the skills. Today i decided to register myself and contribute to this wonderful community. Since this is my first post, any kind of feedback is appreciated.

Malware often disguises itself inside of seemingly non-malicious files, such as installer packages, where it can then gain root access to your computer to track activity or steal your information.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

Protect your Windows desktop or laptop computer from malicious software with anti-virus applications. This handy how-to presents a complete overview of the process. It's easy! So easy, in fact, that this video guide can offer a complete overview of the entire process in just over four minutes. For more information, including step-by-step instructions, take a look.
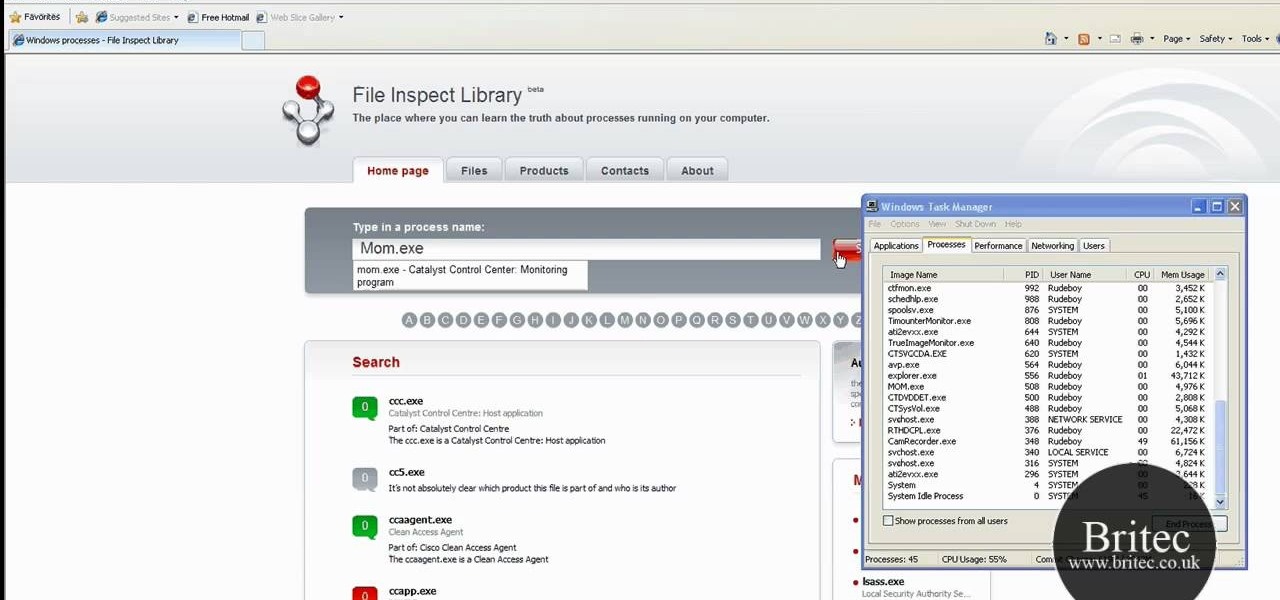
Need help figuring out what a suspicious process is up to on your Microsoft Windows PC? With FileInspect, it's easy to figure out whether a given process is benign or malicious. So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For complete details, including step-by-step instructions, watch this video guide.

Protect your Windows PC from malicious software by disabling AUTORUN.inf & autoplay. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over two minutes. For more information, including detailed, step-by-step instructions, take a look.

Watch this software tutorial video to learn how to use HijackThis to make sure you've deleted a malicious file for good. The tips in this how-to video will help you delete malware from your computer permanently.
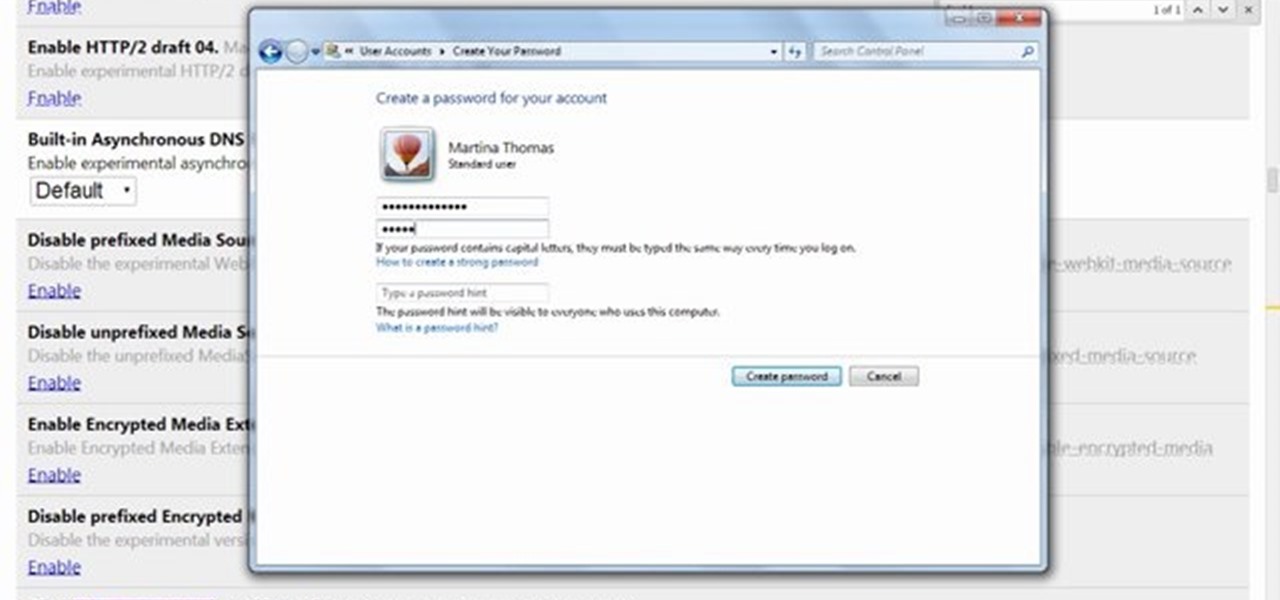
This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

Some times malicious programs can infect your registry and fill it with lots of unwanted information. You may need to clean it to prevent the virus from causing any further damage to your computer or to even disable the virus. It is a very lengthy and complex process to do this manually. So you will need to use one of the powerful free tools available online. Hijack This is one of the most powerful program that can be used for this purpose. So go the website and download this free tool. Insta...

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

After about 40 days of beta testing, Apple pushed out iOS 11.4.1 to everyone as a stable build on Monday, July 9, exactly one week after the final beta appeared.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my hackers apprentices! To own a network and retrieve the key data, we only need to find ONE weak link in the network. It makes little sense to beat our heads against heavily fortified systems like the file and database server when we can take advantage of the biggest weak link of all—humans.

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?
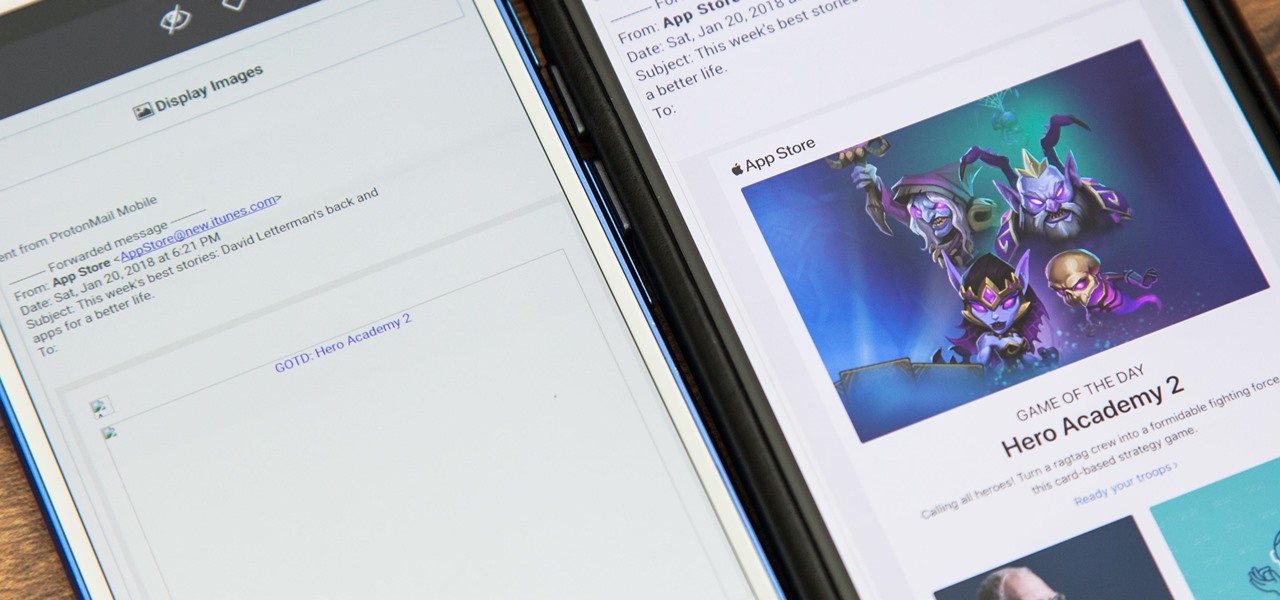
By default, images embedded using external links will not automatically load in any emails that you get with ProtonMail. This is a security mechanism that can prevent malicious code from being executed on your system, but it can also be fairly annoying to have to manually load images in email after email.