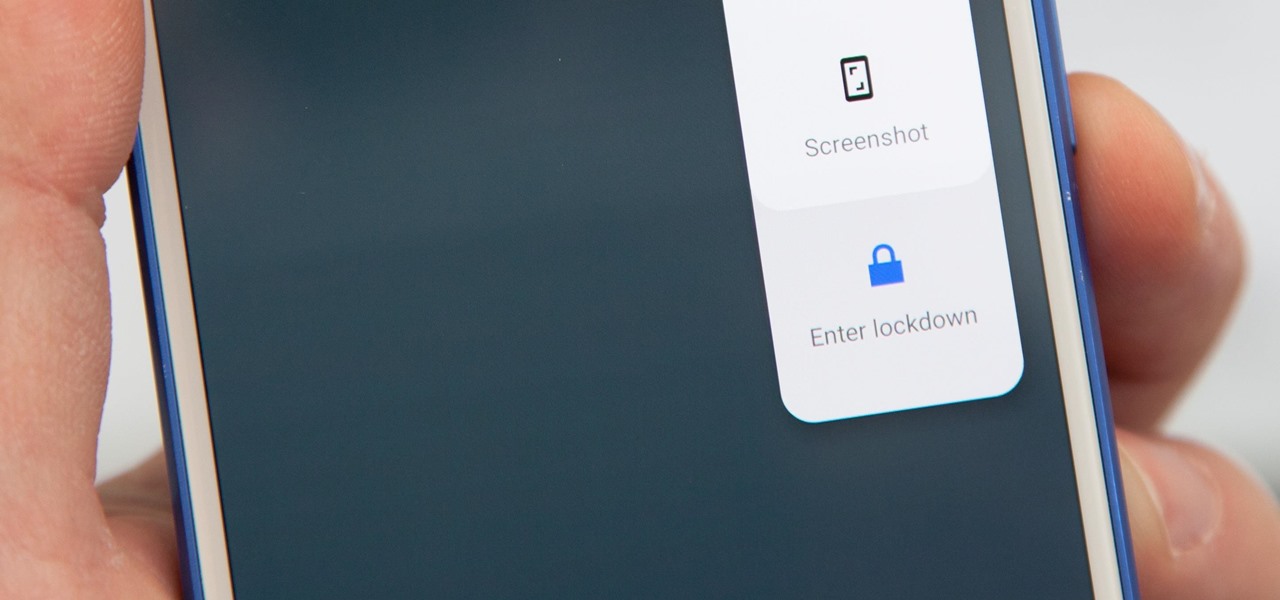
If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.

There has been significant debate over law enforcement's right to access our digital devices in recent years. New tools from Grayshift and Cellebrite are popping up faster than ever to help government agencies, as well as traditional hackers, break into iPhones. If you're concerned, you can take steps right now to beef up your passcode and prevent outsiders from gaining access to your device.

Hardware hacks are something I feel we don't get enough of at Null Byte, so today I figured I would introduce a fun one. I've always been a curious hardware hacker. Taking things apart and learning how their internals work has always been a part of my nature. Quite some years ago, my father showed me a really cool trick on how to hack normal radios to scan frequencies that are normally non-listenable. This little hack allowed us to scan frequencies belonging to law enforcement, and even frequ...

Careers in law enforcement range from police officers and state troopers, to FBI agents and crime scene investigators. Get a job in law enforcement with tips from a former highway patrolman in this free video series on law enforcement careers.

If you are law enforcement or find yourself in an emergency situation you may need to know how to properly conduct surveillance in a rural area. You will have to gather information without being scene and will need different techniques when out in the wilderness.

We use smartphones for just about everything, and while that may be beneficial to us in our day-to-day lives, it can also be used against us in the court of law.

NLP Lie Detector Eye Accessing Cues Explained. This technique is used by the Federal Law Enforcement Training Center FLETC.

During a Laneway Revitalization project some gang graffiti was encountered and replaced with vibrant art work. The event organizer is a Toronto Police Officer who volunteers for the not for profit organization-The Ontario Gang Investigators Association. In this video an explanation of gang graffiti is offered. The organization Notogangs.org is comprised of sworn members of all areas of law enforcement who network regularly in the mandate of the prevention, intervention and suppression of crim...

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

While Apple's tech used for Face ID on the iPhone is impressive, it's debatable whether it's more convenient than Touch ID. There are also concerns that your face could be used to track shopping patterns or be seen during mass surveillance by intelligence agencies. More importantly, it could be easier for law enforcement, and even thieves, to force you to unlock your iPhone.

This is kind of scary! This video demonstrates just how easy it is to hack into an iPhone to access the data on it - including recovering deleted photos. You only think you've deleted those naughty photos you sent to your girlfriend.... Fortunately, there is a way... However, this particular process requires software available only to law enforcement. But that's never stopped a hacker - or a jilted ex - before!

Have a Cambox portable/professional DVR? Well, if you're one of the lucky few, then this video tutorial from Vofoo could help you out.

By Zech Browning Shihan of Gyodokan Martial Arts. Step 1: "Storm Within the Calm - Putting It All Together - Part 1"

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

Video: . HOPEWELL, Va. (WTVR) -- A Hopewell circuit court judge has ordered that a Marine veteran detained over anti-government Facebook posts be released from a psychiatric hospital.

In the US, law enforcement officials can make you unlock your smartphone with a fingerprint, but they can't force you to input a password or PIN, which would violate your Fifth Amendment rights. To help you from ever being in a scenario where you're forced to put your finger on the Touch ID sensor, Apple has a built-in way for you to disable biometrics on your locked or unlocked iPhone in mere seconds.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.

Before you go out to protest, understand what you are facing. Sometimes these demonstrations become infected with looters and rioters, which could mean interaction with law enforcement and potentially arrest. And if your phone is on you, it can be used as a tool against you.

Following in iOS 11's footsteps, Android 9.0 Pie will include a security feature that lets you immediately disable the fingerprint scanner as well as extended Smart Lock features. After initiating the feature, you will be required to insert your PIN, pattern, or password before any other unlock methods will work again.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

NASA -- the National Aeronautics and Space Administration, the United States government's most infamous agency, the powerhouse of space exploration -- teaches you the basics of Isaac Newton's Laws of Motion. Who better to learn motion theory from than NASA?

Much work needs to be done before laws and regulations no longer block driverless' rollout in the US, Rob Csongor, vice president and general manager of Nvidia's automotive division, said today during a US Senate committee hearing.

Daniel Martin, a magician and escape artist, explains his technique for getting out of thumbcuffs. Disclaimer: We're pretty sure it's not illegal to know HOW to escape from thumbcuffs... but we're 100% sure it's illegal to actually escape when detained by law enforcement (just sayin').

The second law of motion. Force equals mass times acceleration. F=MA. Learn the facts about Newton's second law of motion from the National Aeronautics and Space Administration, otherwise known as NASA. The United States government's most infamous agencyand the powerhouse of space exploration explains motion theory.

Demystify Newton's first law of motion with none other than NASA -- the National Aeronautics and Space Administration. The United States government's most infamous agency and powerhouse of space exploration teaches you the law of inertia… Newton's first law of motion.

Learn Newton's laws of motion from the utmost authority on aeronautics -- NASA aka National Aeronautics and Space Administration. See how Newton's laws apply to aircrafts from the powerhouse of space exploration. They talk about thrust force as applied to aviation.

Learn everything you need to know about Newton's third law of motion from none other than NASA. The National Aeronautics and Space Administration is the United States government's most infamous agency and powerhouse of space exploration. Why wouldn't you want to learn Newton's laws of motion from them?

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

Welcome back, my nascent hackers!

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Learn the basics of airplane landings and how Newton's laws of motion apply. NASA -- the National Aeronautics and Space Administration, gives this quick, informative video on Newton's laws pertaining to aircraft landings, specifically the approach. The powerhouse of space exploration explains all.

See how Newton's laws of motion apply to an aircraft's cruise performance with this educational video from NASA -- the National Aeronautics and Space Administration, the leading resource for space exploration. There's no better place to learn about aerospace and Newton's three laws of motion and how they apply to aeronautics than NASA.

Understand the concepts of drag force and how Newton's laws of motion apply to an aircraft's take off with help from NASA -- the National Aeronautics and Space Administration. The juggernaut of space exploration lays everything out on the table for you. Learn from the best, learn from the pros, learn from NASA.

The powerhouse of space exploration, NASA (National Aeronautics and Space Administration), sheds light on Newton's laws of motion as pertaining to drag force on aircrafts. This is a great source for any aeronautics major. The infamous government agency breaks drag down for you.