In this tutorial, learn how to do a variety of very cool tricks. In the first, you will appear to solve a jumbled Rubik's cube in less than two seconds by jumping up and magically moving the pieces into place. In the second, learn how to stack dice like in a video game. The third will show you how to turn an ordinary playing card (no gimmicks!) into a boomerang and finally you will train a disc to return to you when you throw it, as well.

Are your Bingo pieces all jumbled and torn asunder after your weekly Sunday Bingo games? Do you always tell yourself to clean the mess up afterwards, only to end up with the same hodgepodge of game boards and pieces in a ziploc bag week after week?

Learn how to read the secret thoughts of three friends! This video is a great trick to perform at a bar or while sitting around with fiends. They'll be amazed when they think you are capable of reading their minds!

Perform a Criss Angel card magic trick in which you make two chosen cards instantly jump from the middle of a jumbled deck and into your hand.
Facebook is where a lot of people get their news. The problem, though? Your Facebook feed gets jumbled with random post times, which isn't useful for keeping up with new stories in real-time.
Lock screen notifications can sometimes be overwhelming and difficult to manage, especially in the morning when I receive a massive influx of emails, texts, reminders, and social media alerts. At some point it's not even worth scrolling through all of them on your lock screen when you can get a better grasp of everything by just checking out the Notification Center instead.

Word games can expand your vocabulary skills in all sorts of exciting and creative ways. Because of this, both the iOS App Store and the Google Play Store are awash with word games, making it hard to differentiate between good and bad titles. This is especially troublesome if you're looking to purchase a game, as everyone hates to waste hard-earned cash.

Badges? We don't need no stinkin' badges! That is, unless they have augmented reality content embedded in them and give us full access to Facebook's annual F8 developers conference — in that case, yes, we'll take all the badges.

Whether you've celebrated multiple cake days or you're just now getting your feet wet with Reddit, it's a rite of passage to choose your preferred smartphone client. Quick spoiler: Your best option most certainly is not the official Reddit app.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

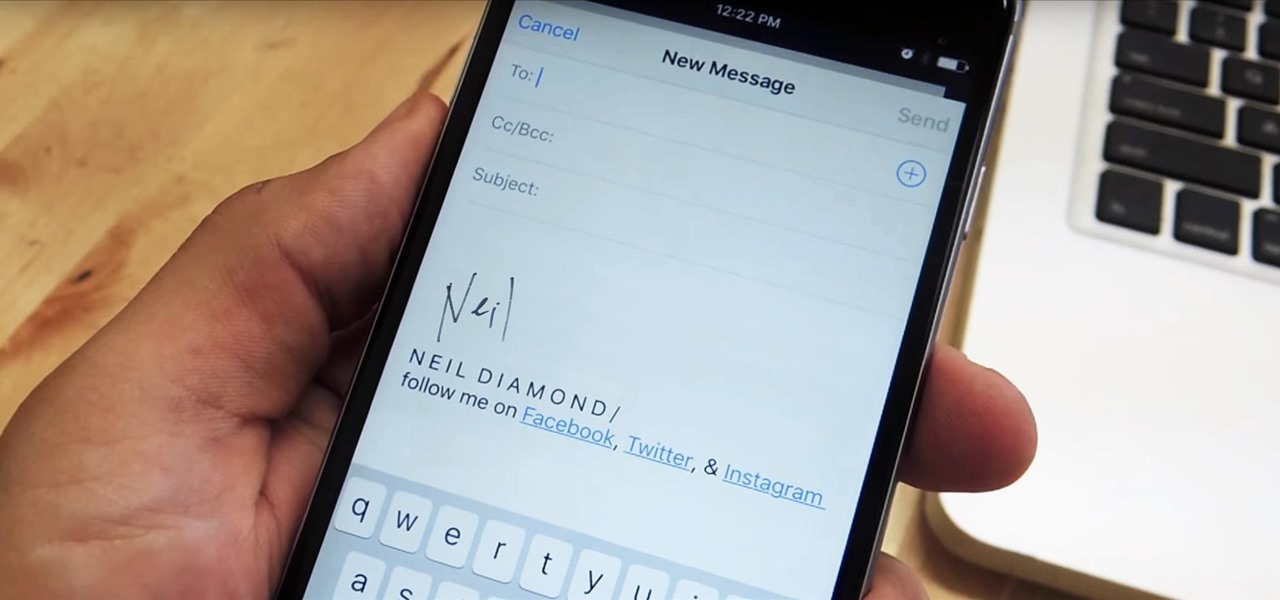
Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

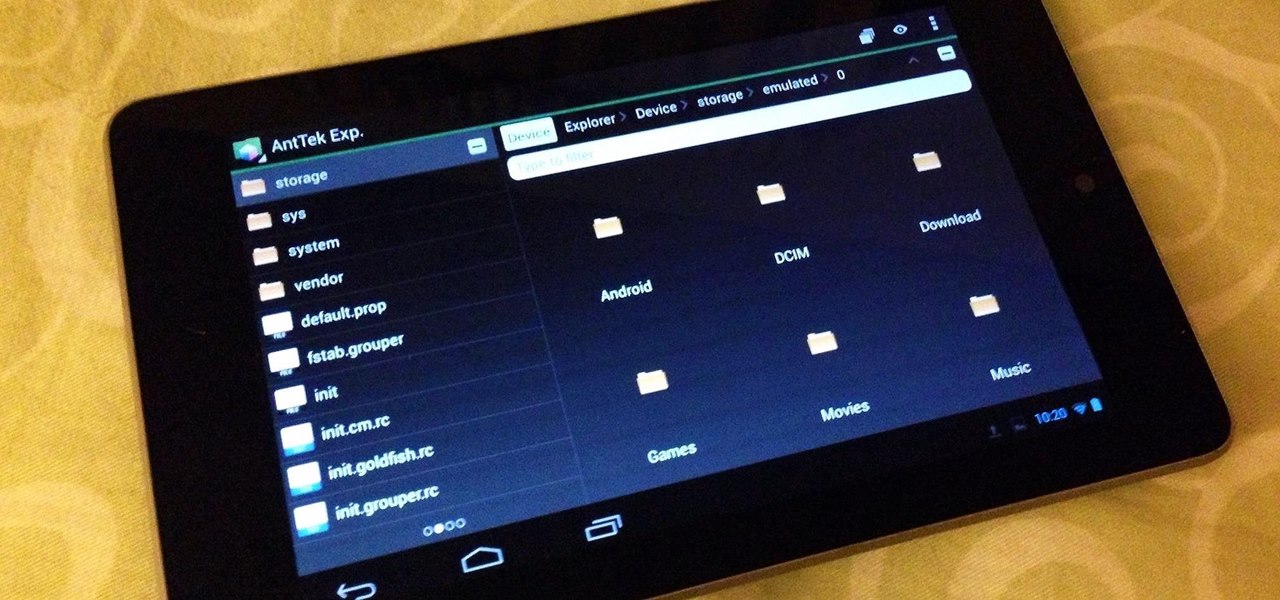
If you're always on the go, the Nexus 7 is a godsend for having everything you need at the tip of your fingers—music, videos, text documents, photos, and more. Unfortunately, as good as that is, it also means one hell of a messy tablet.

Apple's Reminders app has never been particularly sexy or appealing, but that changes in iOS 13. Although the productivity tool has always been useful for quick to-dos, it now has an overhauled user interface with several new features, including grouping lists together for improved organization.

NetBIOS is a service that allows for communication over a network and is often used to join a domain and legacy applications. It is an older technology but still used in some environments today. Since it is an unsecured protocol, it can often be a good starting point when attacking a network. Scanning for NetBIOS shares with NBTScan and the Nmap Scripting Engine is a good way to begin.

Hashes are commonly used to store sensitive information like credentials to avoid storing them in plaintext. With tools like Hashcat, it's possible to crack these hashes, but only if we know the algorithm used to generate the hash. Using a tool called hash-identifier, we can easily fingerprint any hashes to discover the right Hashcat mode to use to retrieve a password.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Starting your morning right is an essential first step to a productive day. Whether you're running late, rushing to catch up on the day's news, or lagging behind with early emails, little hiccups like these can have a trickle-down effect and ultimately ruin your day. Like with many problems, though, your smartphone can help.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

Though many students spend four years of high school learning a foreign language, most of us probably retained very little. Chalk it up to the carelessness of youth, but chances are you've since been in situations or places that left you wishing you paid more attention in class or had continued practicing long after you graduated.

There was recently a case that came to national attention where a gentleman was arrested at an airport for having a watch that looked like a bomb, among other things. As it came out, the watch was, in fact, not a bomb, and the man was just an artist who was probably trying to make a statement of some sort. Well, that message was lost amongst the hail of people shouting that either he had been stupid for bringing that watch on the plane and so deserved to be arrested, or that it's a free count...

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

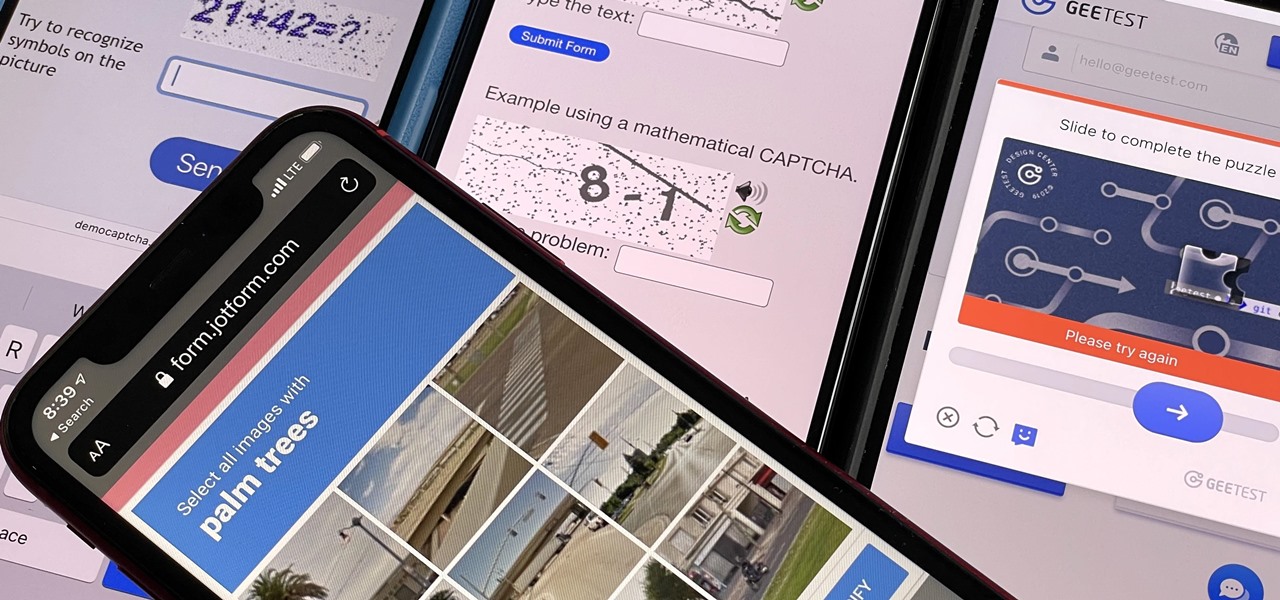
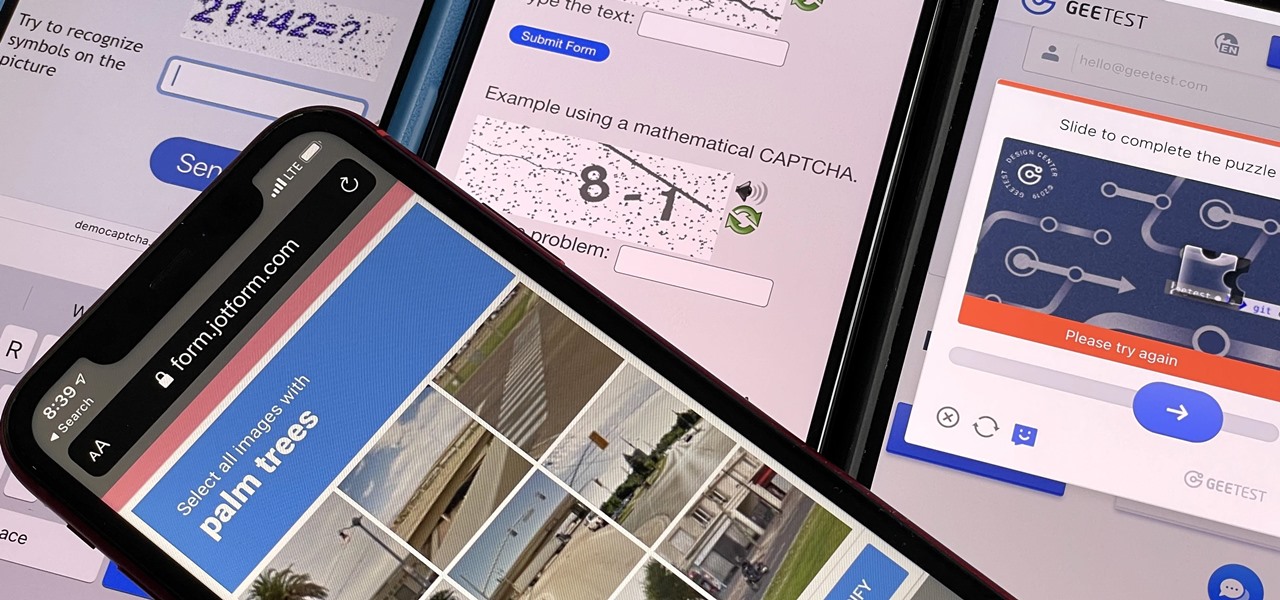
If you hate matching images, typing letters and numbers, solving math problems, and sliding puzzle pieces for CAPTCHA human verification, you'll love Apple's newest privacy feature for apps and websites.

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

Some websites require you to perform a verification task so they know you're human and not a bot. It helps websites curb spam, abuse, unauthorized access, and cyberattacks but also adds an obstacle for anyone trying to visit their content. If you find it more of a nuisance than a necessary evil, there's an easy way to reduce the number of human verification prompts you receive on your iPhone, iPad, and/or Mac.

Apps can learn a lot about you just by reading information about your smartphone. They can easily track what device model you have, your phone number, and in some cases, your hardware MAC addresses. Many third-party apps will only track your device values for advertising purposes, but some might be trying to snoop on your data for ill intentions.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

During the video tutorial, you'll learn how to simply solve the easy and fun fifteen number puzzle. You'll learn a couple different moves to help you solve the 15 puzzle, which are called the curl and the box and twist. The curl is easy, but the box and twist is a little more complicated.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

Many of the indie games featured at PAX Prime have been in development for years. That's how long it takes to make a great game. But the two-man development studio in eastern Europe called Stabyourself has existed for less than a year and has already created two games—three more are on the way. They may be spitting out games left and right, but they've got a few to be excited about.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

In our media-enriched world, past and present, SCRABBLE has made a name for itself, whether deliberately, subconsciously, or influentially. You may have a read a book that had the popular word game within a chapter, watched a movie that showed your favorite characters bringing out the SCRABBLE board, or even listened to a rap about this word or that word. SCRABBLE is everywhere, even if you don't realize it.