
How To: Easy Infinity Square Knot Yin Yang Friendship Bracelet Tutorial
To make this bracelet you will only need to know how to make a square knot. This is a good bracelet for beginners and it looks very interesting.


To make this bracelet you will only need to know how to make a square knot. This is a good bracelet for beginners and it looks very interesting.

Mastering the concepts of the BOOT.INI file (the boot loader) in Windows XP to better control your Windows configuration.

Make a yin yang paper box. It's really fabulous. It's kind of like origami, but not really.
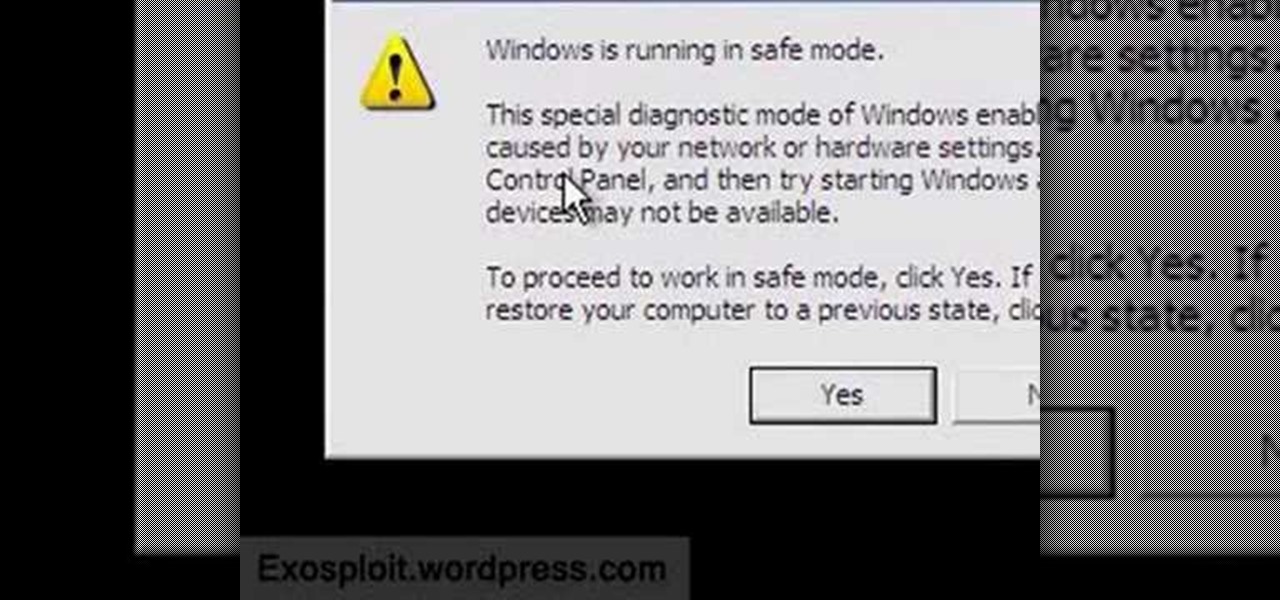
This video will show you how to boot in safe mode on Windows XP. Just follow these instructions from the video. Now go to Start -> Run and type in msconfig. and click OK. Now select the BOOT.INI tab and select /SAFEBOOT, click apply and close and then it will prompt you to restart. After you restart a message will appear. Click Yes and you will notice that your screen resolution is small and you will have the classic theme. To return to normal mode just repeat the steps and uncheck the BOOT.I...

In this tutorial, we learn how to clear an internet cache with Don Schechter. First, you need to click on the start menu, then find the "run" link. Type in "Msconfig", then click "ok". Now, click on the "general" tab, then click on the button next to "selective startup". Now, unclick the check marks next to "process systyem.ini, process win.ini, and load startup items". Click "ok", then restart your computer. Now, go to the "system tools" program in your Control Panel and select the file you ...
In this tutorial, learn how to fix a missing or corrupt ntoskrnl.exe file on your PC. Cause:
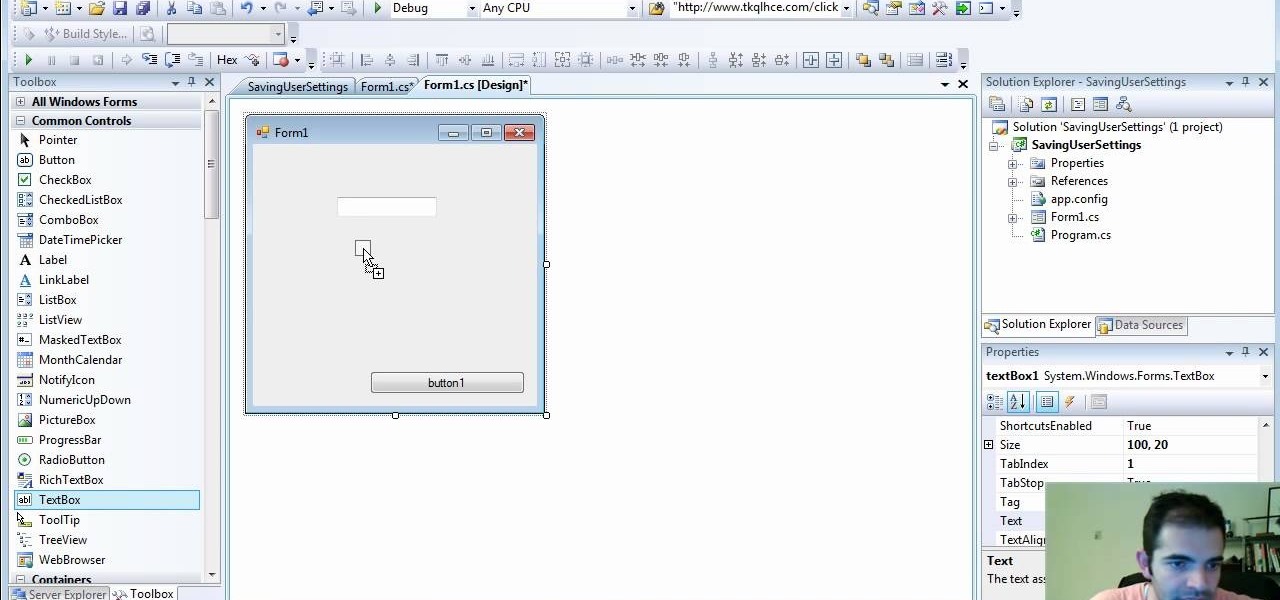
Check out how to save your user settings in Microsoft Visual Studio using C# programming, that way when you restart the program, it can remember some of your important information. This will specifically show you how to save your user settings using the .NET Framework instead of working with custom INI files.
If you have been looking for a way to get the popular Joomla Content Management system running on Windows with IIS, you may have run into many problems. In fact, many people spend days trying to get Joomla running on IIS and run into roadblock after roadblock. The problem is getting PHP, MySQL, Joomla and IIS to all play nicely together. As you search for solutions, it is easy to find part of the answer, but rarely do you find it all in one place... until now. In this video tutorial we start ...
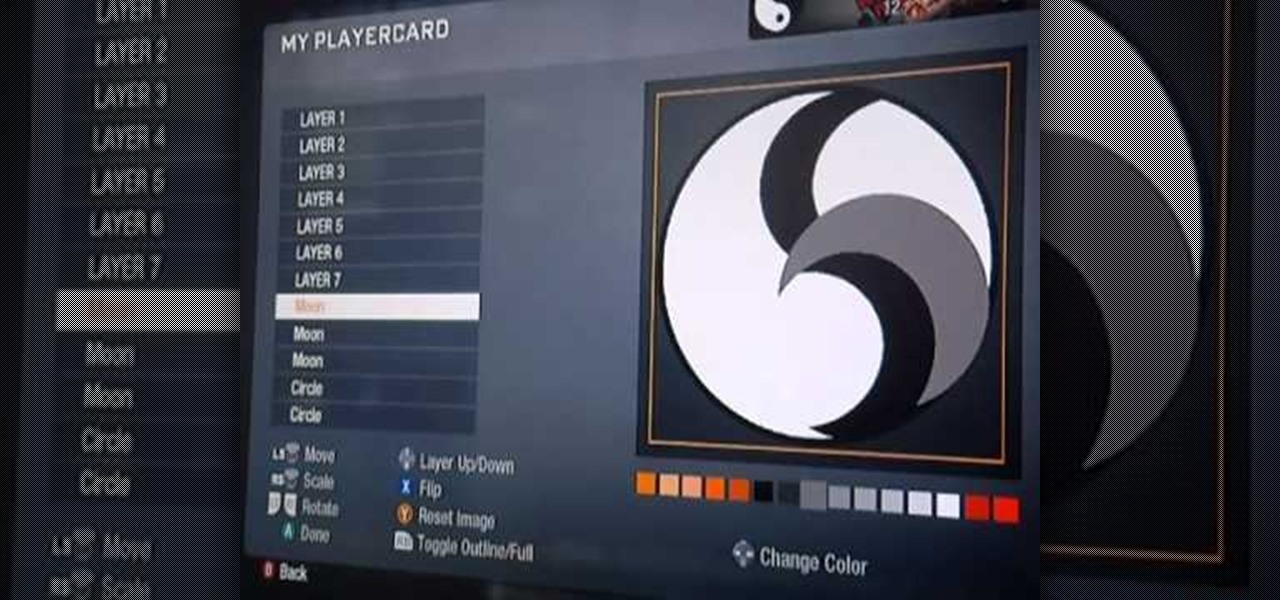
Learn how to draw and use a yin-yang as your playercard emblem with the Call of Duty: Black Ops Emblem Editor!

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...
If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.

The trick to winning a Gemini’s heart is to be the yin to their yang. Learn how to use astrology advice in dating, by watching this how-to dating video. Pick up tips on making a relationship with a Gemini work. Be coy when you meet a Gemini, they love a little mystery in their relationships.

User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

The bicep and the tricep are like the yin and yang — if you overdevelop one and not the other, it looks weird at the beach. You will need a dumbbell and a padded weight bench. Warning: In case you drop the weights, make sure no one is standing behind you, other than a spotter. Always consult a physician when attempting any exercise program.
When you try running Apache, Joomla, PHP and MySQL at the same time, you should expect a few hiccups. But there are ways to get them running smoothly and effortlessly together, and this video will outline the process of getting your Joomla Content Management system up and running correctly on Windows.
If you're a tech enthusiast, there's no way you're not watching HBO's Silicon Valley. So you surely know the Pied Piper crew's latest shenanigans involve an app that uses a phone's camera to find facts about food items — a sort of Shazaam for food, if you may.

No one likes to think about the possibility of natural disasters, but we all know they could happen at any time. Some of us are a little more paranoid than others, but wouldn't it be nice to know that you'd be protected if anything really crazy ever happened? Like the zombie apocalypse?

In this video, you will learn how to make origami stealth fighter. This origami model simulates a stealth aircraft.

In this video, I'm gonna show you how to fold a paper jet fighter call F-18 Hornet. This model is designed by Thay Yang.

Any artist who excels enough in his profession will create some sort of signature on his painting to notify other it's his work. Some painters, like Jan van Eyck, are cryptic with their inscriptions, putting it in almost impossible to see areas in the painting, while others, like Chinese painters, put their literal stamp on paintings with a carved seal stamp.

Learn the movements of the Yang form of Tai Chi Chuan, including the solo and partner movements of the ward off and roll back, in this free, Taiji expert video series.
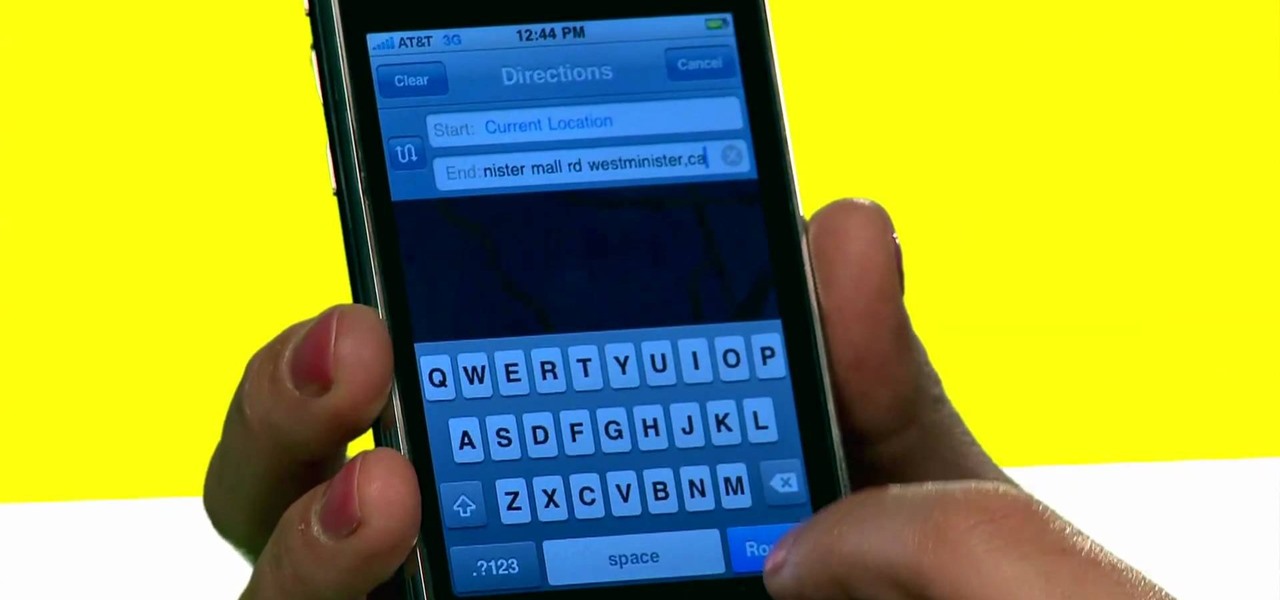
The iPhone is great. And so is Google Maps. And together, they define mobility. They go together perfectly. Like yin and yang. But how do you get the most out of Google Maps on the iPhone? Best Buy has answers. The Best Buy Mobile team explains how simple it is to use Google Maps on your Apple iPhone for directions.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.
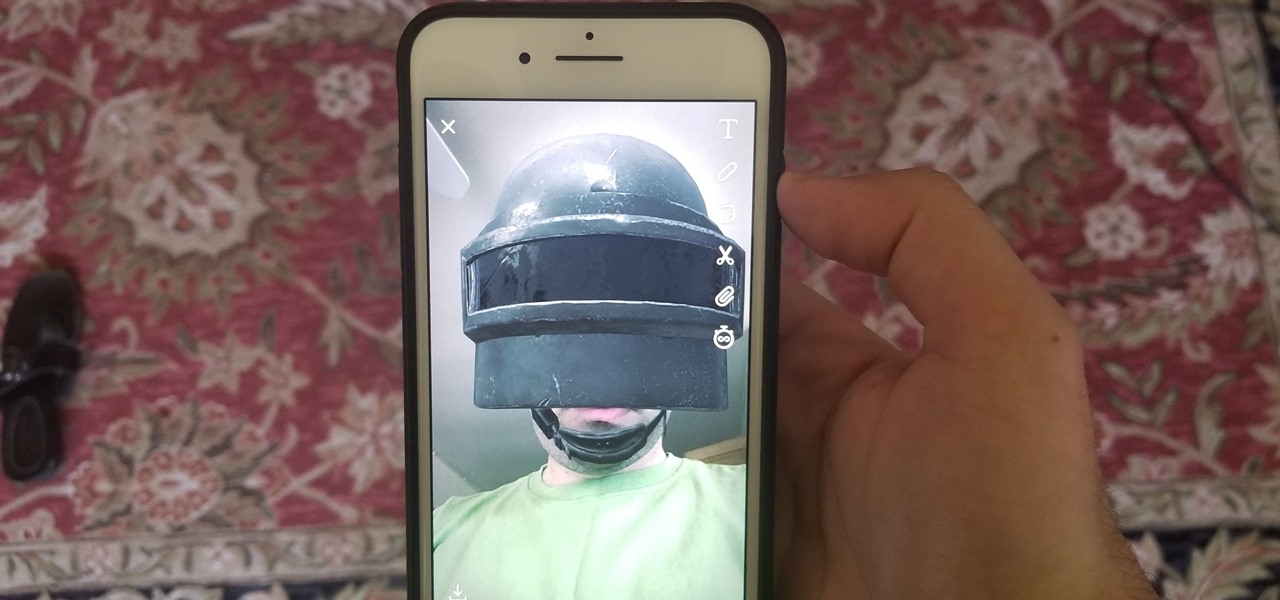
Spring is finally here (in earnest now), and a new batch of great augmented reality Snapchat lenses have come along with it. New life has been breathed into meme culture with the spring lineup of TV shows, Mark Zuckerberg's ongoing investigation, and college kids with too much time on their hands.
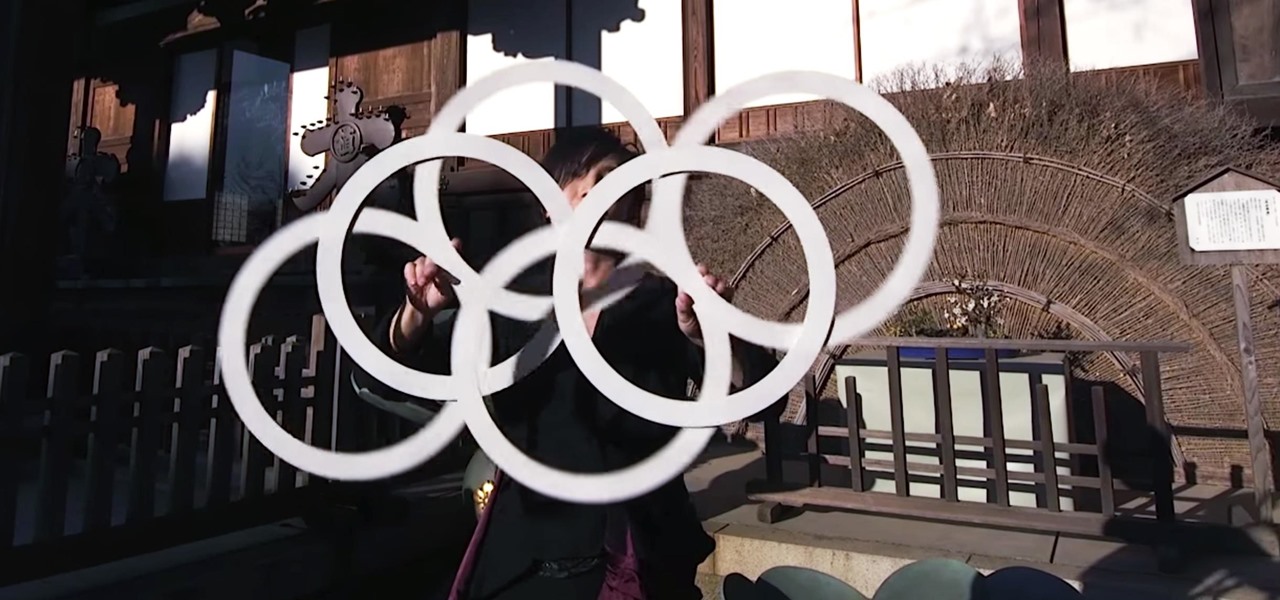
Heads up: the following videos and GIFs will definitely cause you to zone out and lose focus on whatever it is you're doing.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

Everyone has a favorite superhero. It doesn't matter how old or young you are, there are probably some heroic characters out there that you wish you could be. And in Call of Duty: Black Ops 2, you can be them, as long as you've got some emblem editing skills.

Welcome back my social engineers/hackarians! Today we'll be looking into a fantastic piece of software, The Social-Engineer Toolkit or just SET for short. SET is designed, Developed and used by several Social-engineers. So... Let's get started!
Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.
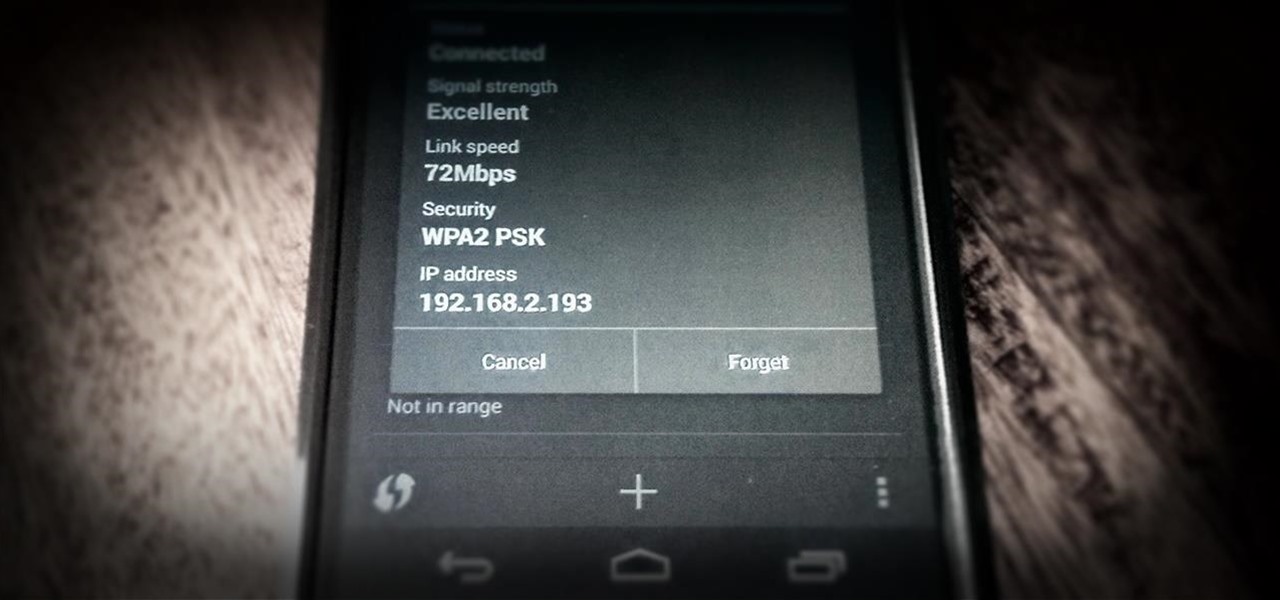
One of the most common complaints that people have about the Nexus 4 would have to be its intermittently poor Wi-Fi performance, a problem that for many, persists through the installation of updates and even custom ROMs.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

It turns out that attending the L.E.A.P. conference last month may have mostly been best for demoing the Magic Leap One in person, as the company has now uploaded the majority of the insider panels held at the event in Los Angeles.

When the mosquito that carries the malaria parasite (Plasmodium falciparum) bites someone, the parasite must travel to the liver where it undergoes part of its lifecycle before infecting red blood cells and spreading to its next host. Until now, the first step of how the parasite gets to the liver hasn't been clear.

Baidu's self-driving car unit has had a tough week. Today, the company's leading artificial intelligence (AI) expert, Andrew Ng, announced in an optimistic blog post that he would be leaving the Chinese search engine company to pursue AI research on his own.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

Samsung's big reveal of the Galaxy S9 and S9+ at Mobile World Congress revolved around its "reimagined" camera and augmented reality capabilities.

Even before we are born, our immune system is hard at work. New research shows how the developing fetal immune system takes advantage of the time and opportunity of gestation — in the presence of mom's cells and tissues — to develop a sense of self.

While you can do a lot of things on your smartphone that were once only done on a computer, having a laptop is still necessary and critical for many tasks. Often times, the two devices work very well together.
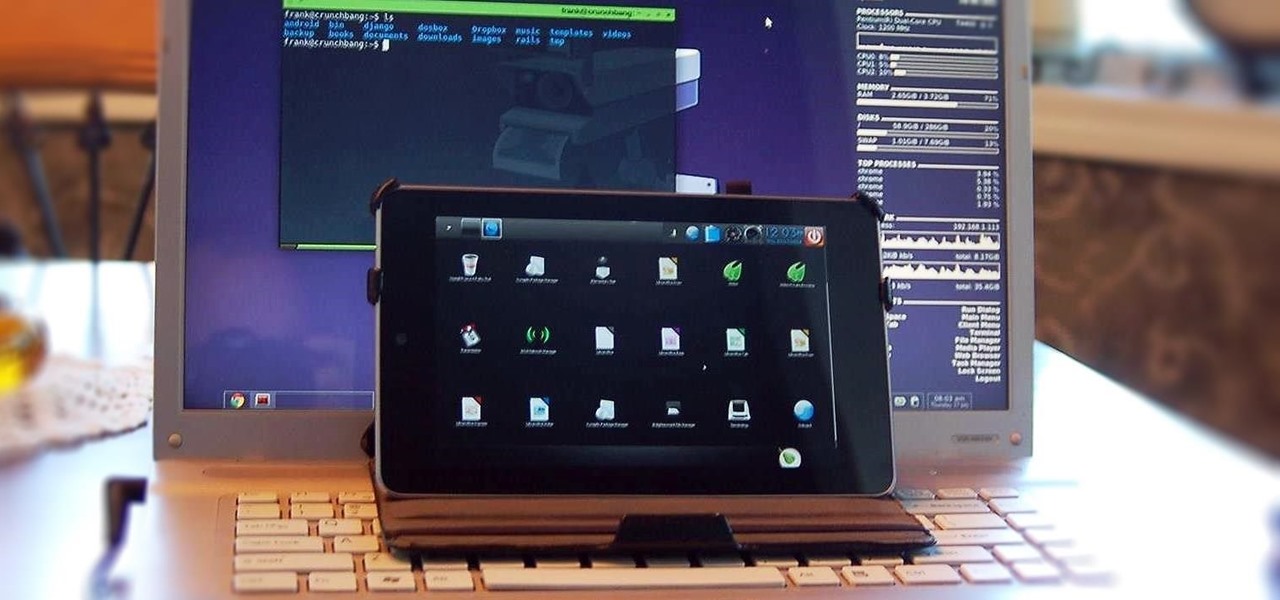
When people first learn that their Android device is capable of dual-booting different operating systems, e.g. Linux, they almost universally respond with, "That's so cool." And for those of us ambitious enough to actually try one out, we are typically filled with glee as we see Ubuntu, or something similar, boot up for the first time on our tablet or phone.