Exclusive to the Samsung Galaxy S6 Edge, "Information stream" is a screen feature that lets you see quick, at-a-glance information with a simple swipe while the screen is off. It also supports plug-ins, or additional streams of information that can come from third-party sources. So developers are starting to come up with nifty little add-ons for Information stream, and the team at 3C has some cool new system feeds that might come in handy.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

You probably already know that your digital pictures have quite a bit of information embedded in them. What you might not know is just how much personal information is included in that metadata, including your camera information, and in some cases, even the precise GPS coordinates of where you took the picture.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

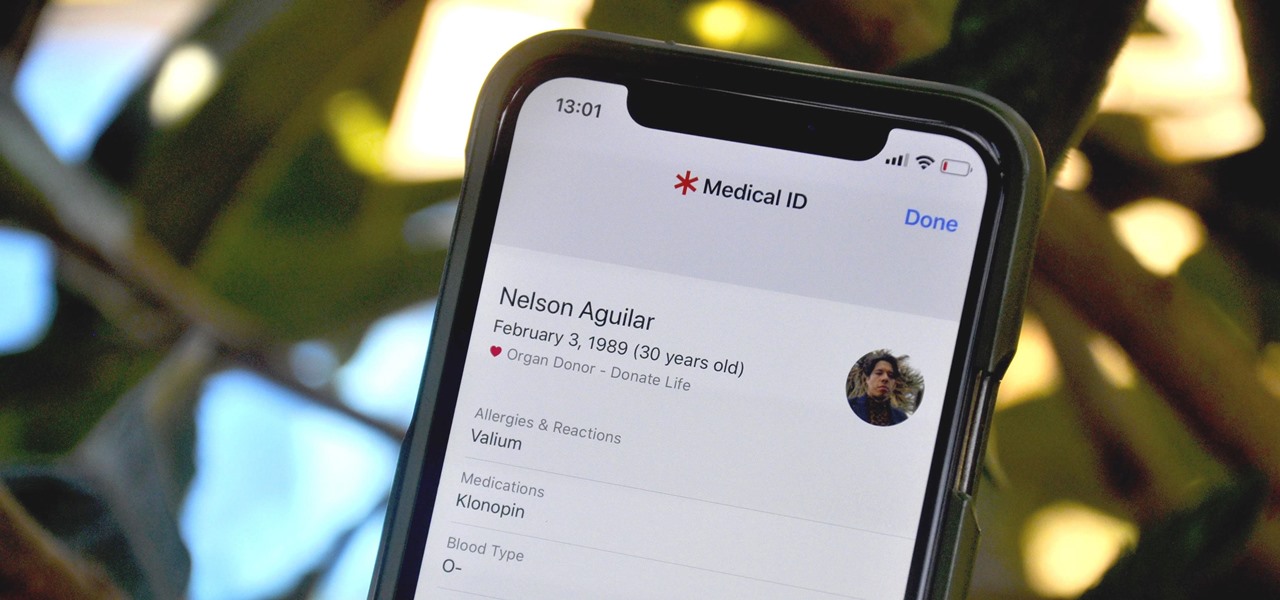
You can't predict the future, but you can prepare for it. On the off chance that you get hurt in a car accident, take a nasty tumble, fall down a cliff, have a seizure, or get struck by lightning, it's always good to carry up-to-date information about your health in case you can't speak for yourself. A physical medical ID wallet card or bracelet can provide the information, but so can your iPhone.

It seems like there's a cyber security scare every day. Consumers are growing increasingly concerned about the safety of their accounts, and they have reason to be. Hackers will maliciously attack you anywhere — and we mean anywhere — they can to get your private information.

continuing this series, I will now go in-depth on using advanced search queries. What Is Search Queries Again?

Business hours and addresses change, but they're not always updated on Yelp by business owners for the rest of us to see. Showing up when a business is closed or going to the incorrect address is a major annoyance, which is why the company allows us, the customers, to help update business information through the Yelp mobile app on iOS and Android. If owners won't do it, somebody has to.

Whether you're white hat, black hat, or some shade in-between, navigating through a network is a core part of hacking. To do that, we need to be able to explore a network to discover the addresses of gateways, interfaces, and other attached devices. When ifconfig just isn't enough, you can steer your way around a network with a convenient tool called Ship, the script for everything IP.

Every single photo you take carries with it a considerable amount of seemingly "invisible" yet important information known as metadata. Although metadata is usually helpful to sort your photographs by location and date, that same information could potentially be used against you, especially if the pictures are taken during a precarious situation.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

With presidential voting going down on Tuesday, November 6th, voters are beginning to anchor down on their choice for president. But with the way the media works, this may be difficult for some people because the news sites they listen to give conflicting and sporadic information on the candidates.

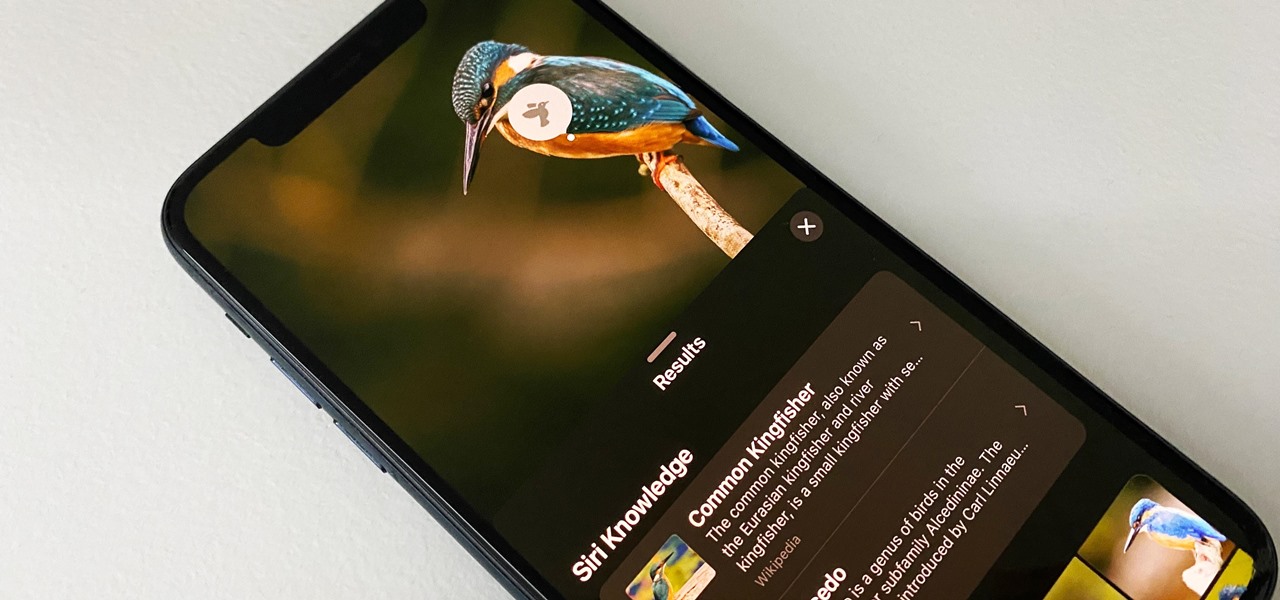
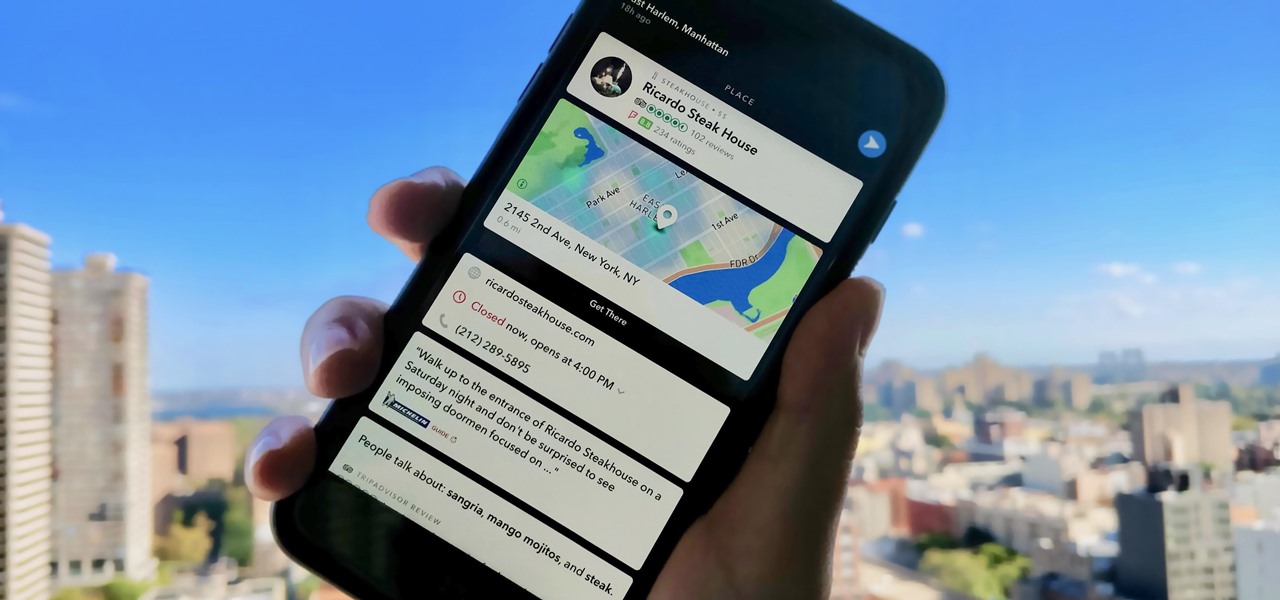
When you take a photo of something interesting, like a landmark, piece of art, animal, or plant, there's a good chance you'll also want to know more about that something than just what you see in the frame. When this happens, you can take advantage of Apple's content recognition service for iOS and iPadOS without having to install any third-party apps.

Welcome back, my future hackers! After my first tutorial about doxing, I decided I would dive a little bit deeper into the world of social engineering. In this tutorial we will learn some basic social engineering techniques to get into a company building, find out more information about the company's security, and maybe even exploit the company's computers if you get the chance.

Sharing your personal information can come up for any number of reasons: you may want to get in touch with a colleague after work or you've been involved in a car accident and need to stay in contact with the other driver. Unfortunately, giving out information can be the key for others to find your social media accounts, such as Instagram, whether you want it to happen or not.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

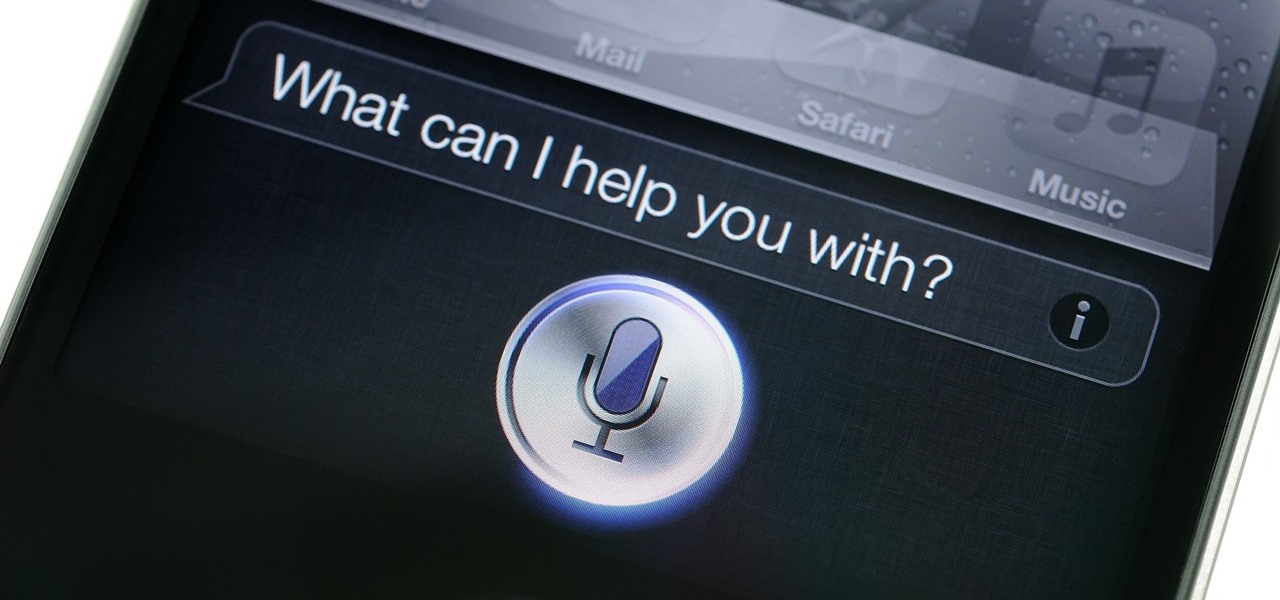
If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

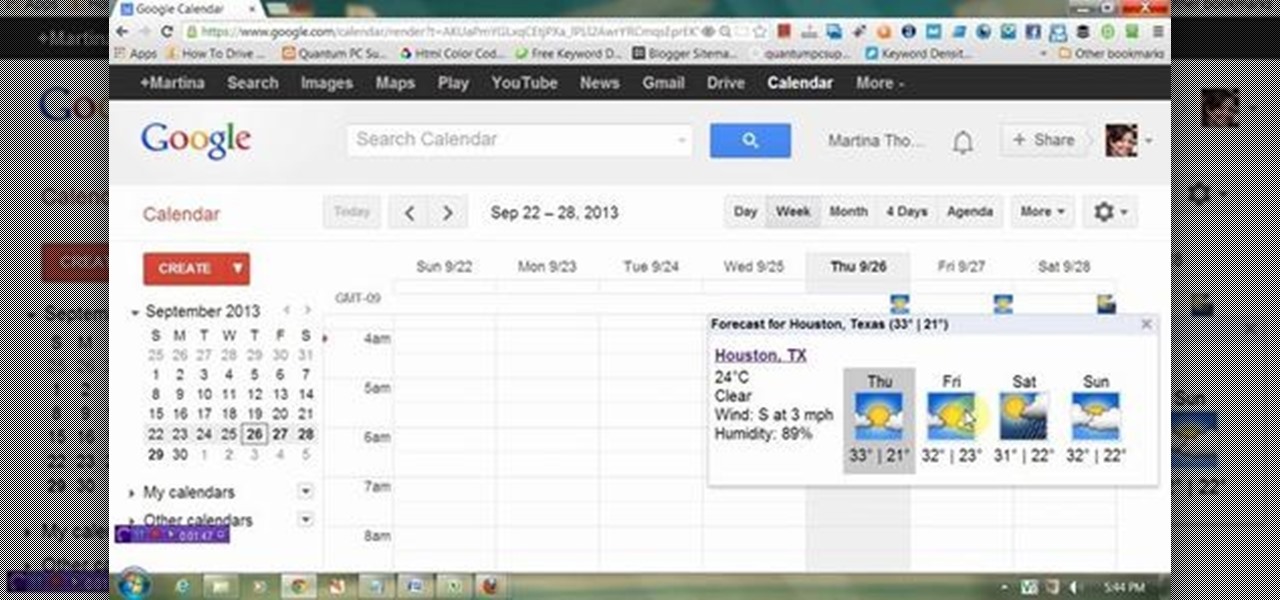
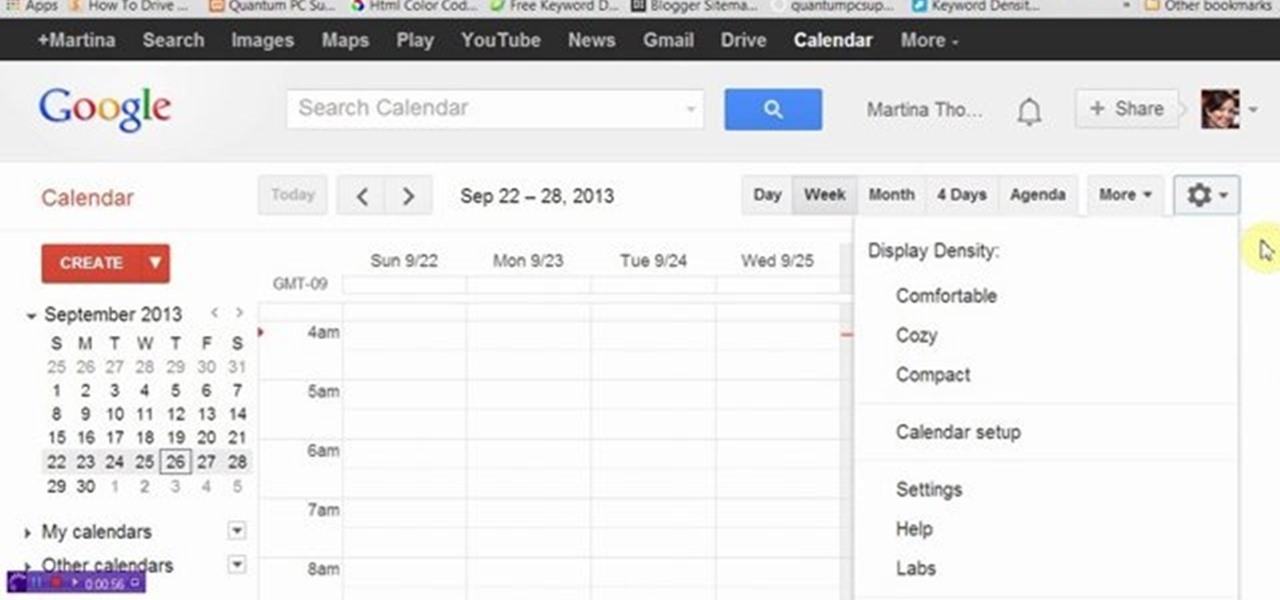
This video will show you how to display weather information about a particular place in Google calendar. You could see the present date weather and coming 3 day forecasting. So enjoy your Google calendar.

This video will provide an idea how you could hide your friend related information on Facebook and list from the public or your friends also. Especially the list is hidden from those who are not your friends in Facebook.

This video will provide an idea how to display weather information of a particular place in Google calendar. You could see the present date weather and coming 3 days forecasting. Watch the video carefully and employ the technique.

Your privacy is important, especially online. Almost anywhere you go on the internet, you leave a trail of data that companies can use without your permission. VPNs are the easiest way to keep your browsing private and your information safe. Ivacy VPN is one such service, and it's one of the best deals you can get on a VPN because it will cover 5 of your devices for a lifetime, and this is a two-account bundle, so you'll be able to cover 10 total devices for $49.99.

If you're in the Windows Holographic community of developers, make sure to mark your calendar and set your alarms for February 8, 2017 because it's Windows Developer Day.

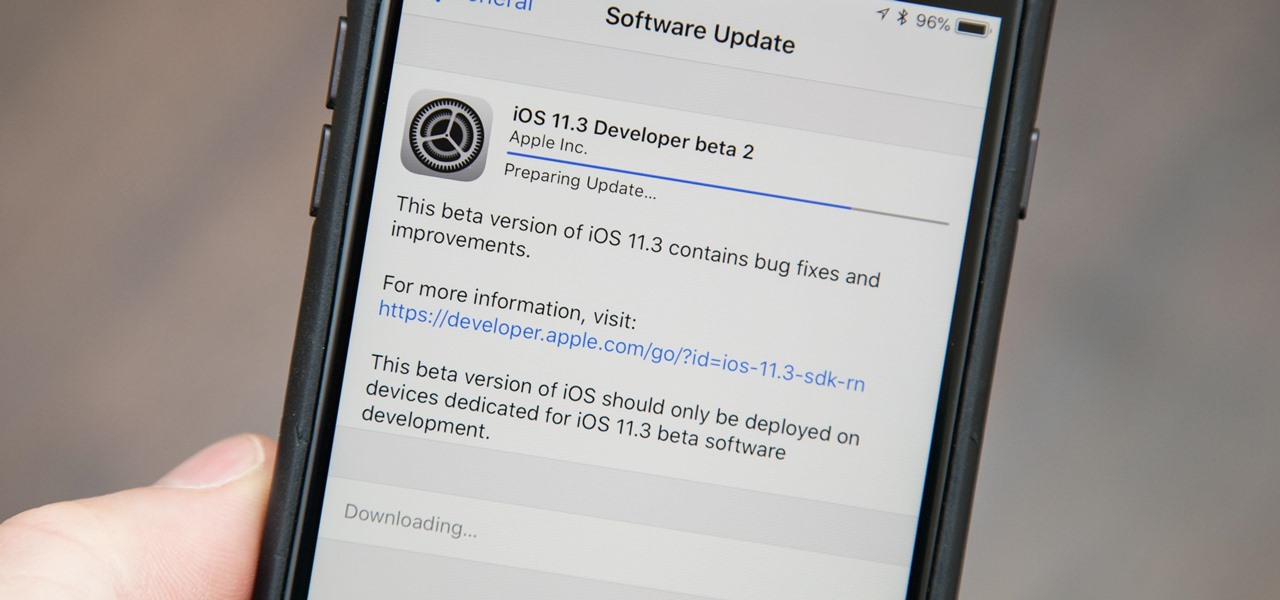
Apple released the second beta for iOS 11.3 on Tuesday, Feb. 6. The update comes two weeks after the original announcement and release of the iOS 11.3 beta, which brought new Animoji, Messages on iCloud, and Apple Music Videos, among other features. One glaring omission was the promised battery health tool, but iOS 11.3 beta 2 just introduced it.

Not that long ago, Snapchat was an app with only one purpose — to send and receive self-destructing picture messages. The app has clearly grown since, adding many features that both adhere to its original function as well as ignore it. One of these new features is Context Cards. You may have heard about them, but what exactly are they?

I wonder if Best Buy has any Note 3's for sale?? When trying to figure out when something is in stock, we usually either check online or call the store to talk to someone. If certain products are out of stock the process might be tedious, with having to find phone numbers and calling several stores.

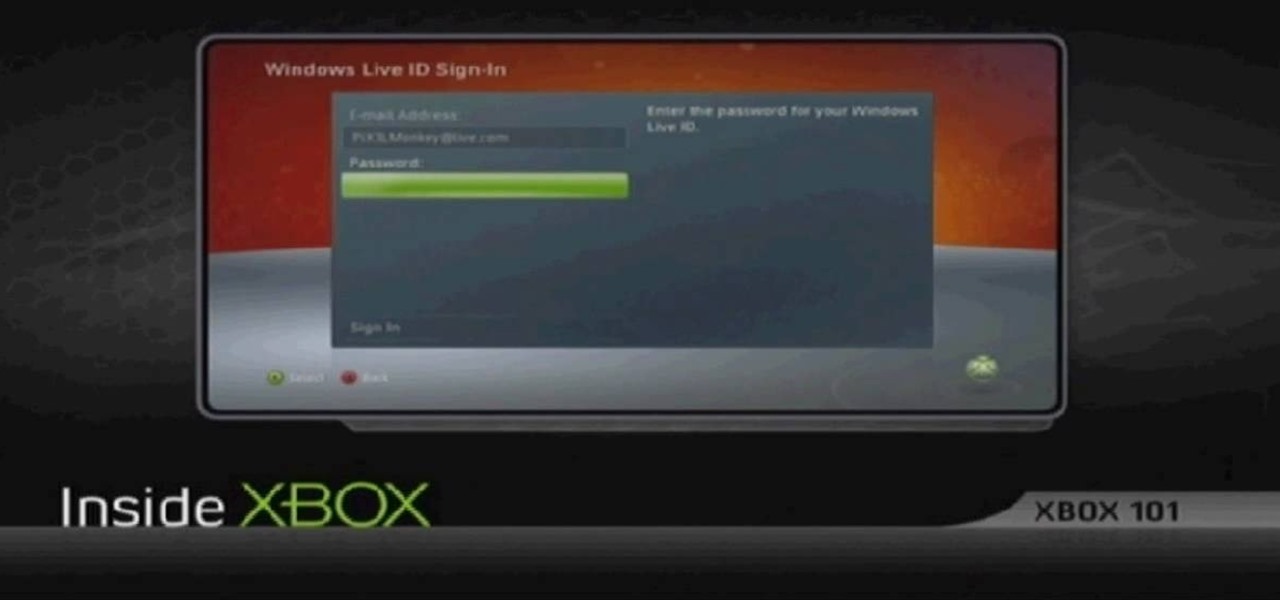
Learn how to update your contact information on your XBox 360 in simple steps. First to update your information through the XBox website go to My XBox and select 'Manage profile'. Now click 'Contact information' and update you information and details. To do it from your XBox 360 console go to My XBox and select 'Manage account'. Now click on 'Contact information' and then update your details. Do not give fake details because if you are selected for any offers you cannot be contacted.

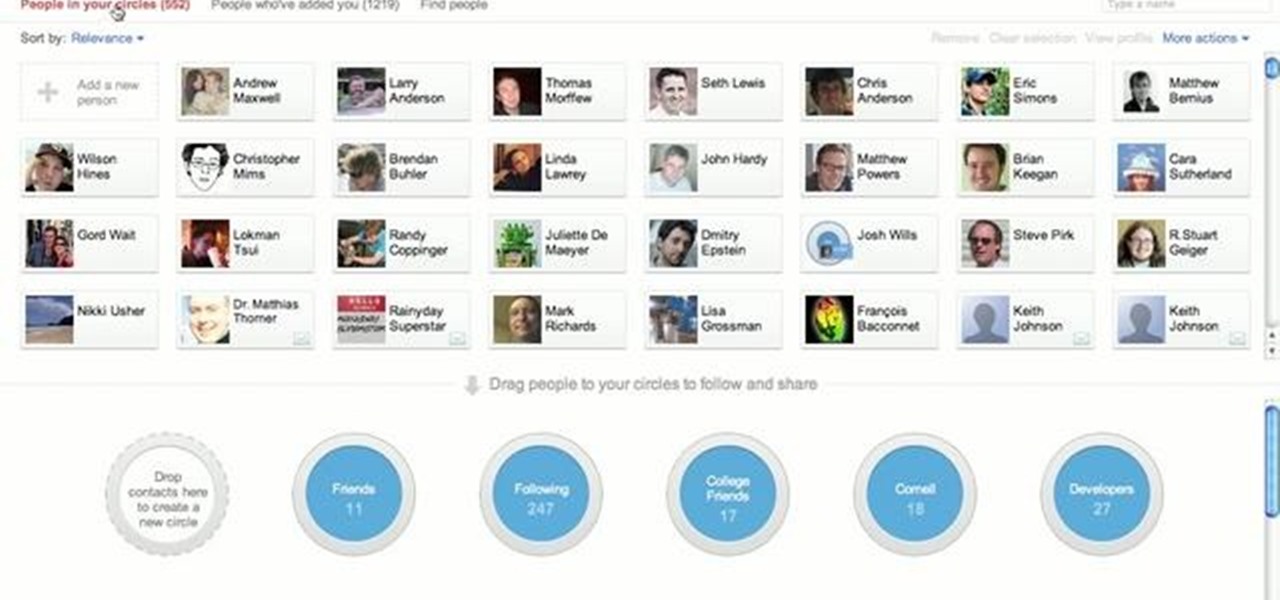
In addition to being a great way to share content and information that are also using Google+, additional sharing features in Google+ allow you to send content and information to other individuals who do not use the service. You can even import your address book to make sharing even easier.

Greasemonkey scripts allow Mozilla Firefox and Google Chrome to be augmented in powerful ways. Take these two Greasemonkey scripts will help add information to your favicons when using Google Calendar and Gmail - now you can see the current date and unread message counts on their respective favicons.

This video speaks about removing sensitive information in Adobe Acrobat 9. The viewer might get a very obvious idea of removing sensitive information by redaction. Redaction is the process of permanently removing sensitive information from a PDF file. This is done by opening the Advanced menu, clicking "Redaction" and then clicking "Show redaction tools", which can be in any format, images or text. The viewers will definitely get a clear idea of removing such sensitive information by redactio...

Before you sell your Blackberry on eBay you may want to erase all personal data on the device. This video will show you exactly how to reset your Blackberry and erase all personal information.

Learn how to quickly import data into Microsoft OneNote 2010 with the Quick Filing tool. Whether you're new to Microsoft's popular note-taking application or a seasoned MS Office professional just looking to better acquaint yourself with the OneNote 2010 workflow, you're sure to be well served by this video tutorial. For more information, and to get started quickly importing data into your own OneNote projects, watch this free video guide.

Want to forget about always pulling out your credit card to purchase something on your BlackBerry? There's a little application that can do it all for you? But how? Best Buy has answers. The Best Buy Mobile team explains how to use the BlackBerry Wallet application. This application can store personal information such as credit card information and shipping addresses on a secure website for easy access when shopping online.