Trust can be a touchy subject in general, and is often required when sharing personal information—especially so when handing our phones over to others. You may not have a ton of secret or nefarious information on your device, but that doesn't mean you want your mom or snoopy coworker having easy access to your messages or Facebook app.
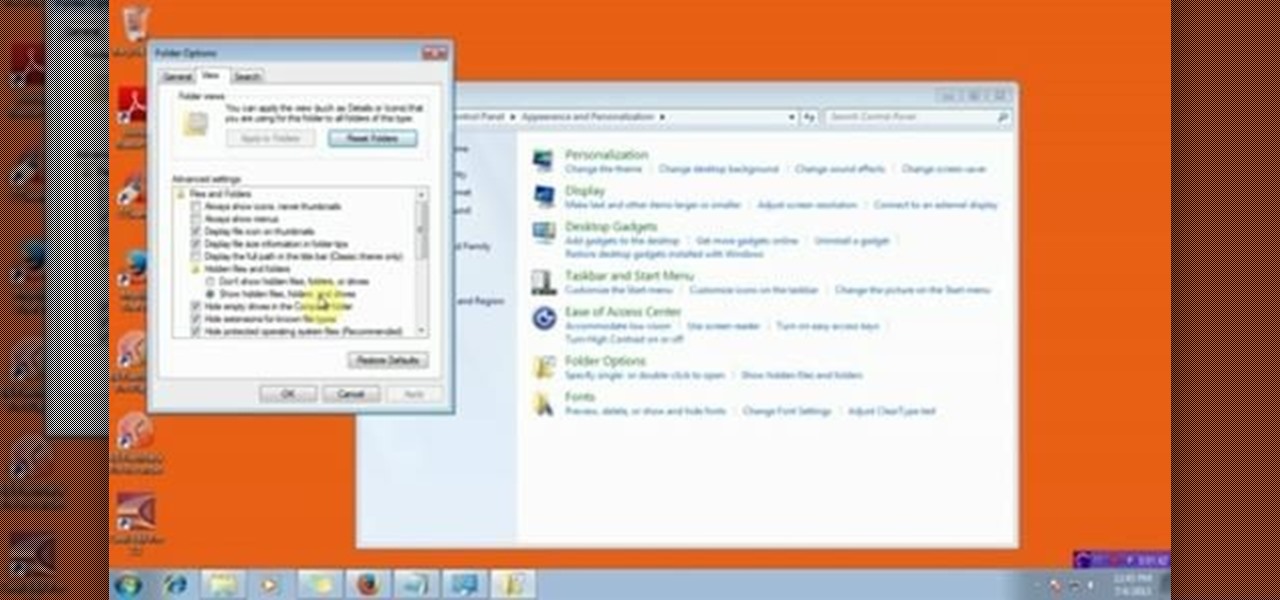
This video will describe you how to hide your important files, system files and folders hidden from common users in windows 7
Regardless of how great your friends and family are, they'll more than likely go through your photographs if they had the chance. Hell, if my friend were to leave his/her phone lying around, I'd go through it—no doubt.

This guide is a little humerous, but it details the way in which you can hide your chests in Minecraft so that you can stop people from stealing your items in the game. The trick involves a pretty crafty way to build your house.

This video shows you how to set up and hide mini wireless spy camera. Where you put it is up to you. Who you spy on is up to you. If you're wanting to keep an extra set of eyes on someone, watch and learn. Whether it's your bathroom or kitchen, put your eyes on the prize.

To get the Perfectionist trophy / achievement in Assassin's Creed Brotherhood you need to beat at least three of the virtual training challenges. There are a few to choose from, and this video will show you how to easily beat all three hidden blade challenges and earn your achievement.

Tired of endlessly turning hidden file visibility on and off on your Microsoft Windows PC? In this home-computing how-to from Tekzilla, you'll learn about a free application that makes the process as easy as a mouse click. For all of the relevant details, and to get started using this time-saving app yourself, just take a look.

Hide your valuables in plain sight! This tutorial shows you how to take an empty can of whipped cream and then add a few discreet mods. When you're done, it'll still look like a can of whippped cream, but now there will be a way to hide your valuables!

In Halo: Reach for the Xbox 360, there is so much to do! The campaign, the multiplayer, the achievements! But One tough one to get is all 19 hidden data pads. Luckily for you, the first nine can be acquired on any difficulty, and in this video you will learn the locations of all nine of the initial data pads on levels such as Winter Contingency and Pillar of Autumn!

TrueCrypt is a free open-source program for encrypting data and it's excellent for securing hard drives, but it also has the ability to hide a secret operating system inside another operating system. CNET shows you how this "insider secret" operating system is created. This operating system will be impossible to prove to people like the Feds.

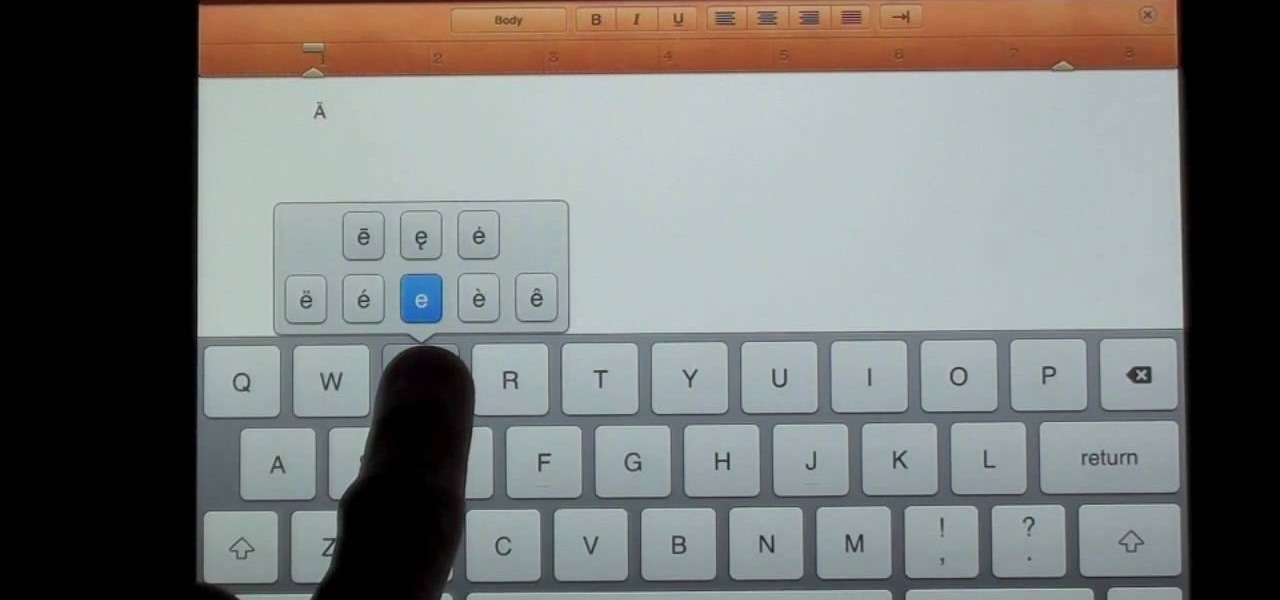
In this clip, learn how to access and use hidden and advanced functions on the iPad keyboard. Whether you're the proud owner of an Apple iPad or perhaps just considering picking one up, you're sure to benefit from this free video tutorial. For more information, including a detailed overview, watch this iPad user's guide.

Disable YouTube comments & keep your head from exploding. This clip will show you how to use a Greasemonkey script to automatically hide YouTube comments. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just over a minute and a half. For more information, including complete, step-by-step instructions, take a look.

In this tutorial, learn all about the difference between breads at supposedly healthy sandwich shop, Subway. Did you know that the new 9 grain bread actually has the same nutritional value as the plain white bread they offer? Find out what scary chemicals are hiding inside your lunch with this clip from Food Facts TV.

A lot of commonly used household items are actually poison for your furry friends. In this clip, learn all about which items can pose a danger for your dog or cat. It's not only chemicals that are bad for your pets, innocent seeming items like fruit, veggies, chicken bones, chocolate, human medications and many other hidden dangers exist as well.

Check out this tutorial from IGN and learn how to find the hidden secrets in Fallout 3's "Point Lookout". You will learn tons of tips and tricks for this level so that you will always come out on top. These tips come straight from the expert gamers at IGN, so you know they're good.

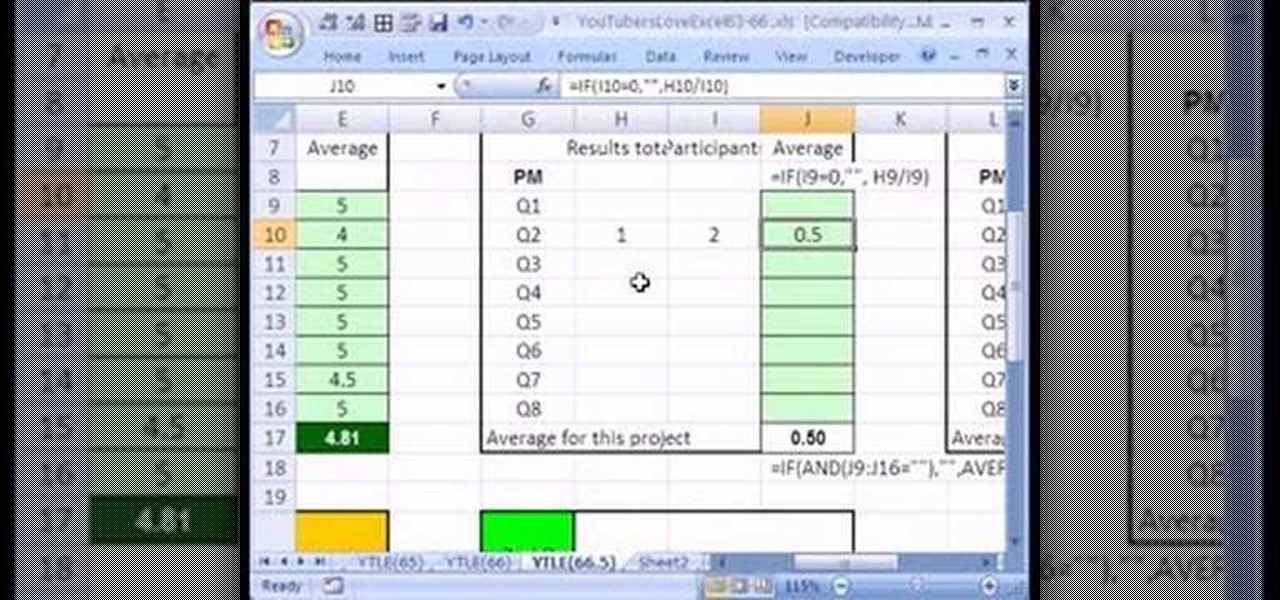
Love Microsoft Excel? This clip contains a tip that just might induce you to. With this free video tutorial from ExcelIsFun, the 66.5th installment of his "YouTubers Love Excel" or YTLE series of free video MS Excel lessons, you'll see 3 different ways to hide formula errors.

Facebook is overrun with all sorts of meaningless applications these days. It seems like there's no end to the amount of games people create for Facebook. Keep these games off of your news feed so you can see what really matters to you on Facebook. This video will show how to hide games on your Facebook news feed.

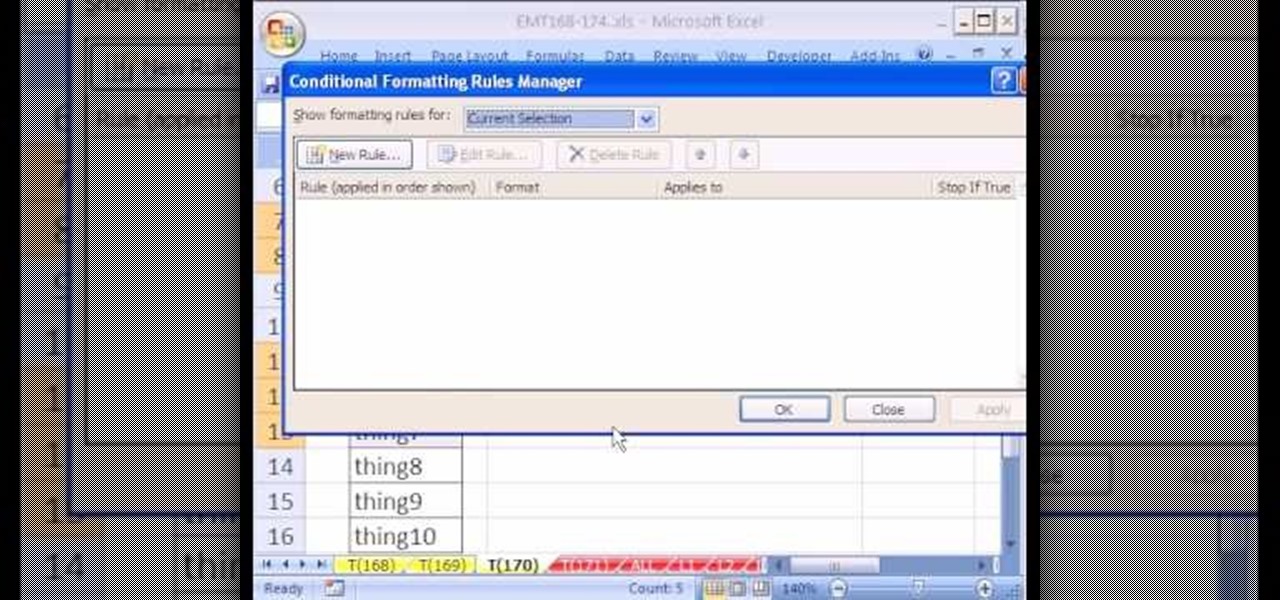
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 170th installment in their series of digital spreadsheet magic tricks, you'll learn how to use conditional formatting to hide or show items in a list using a TRUE/FALSE formula.

Darci Larocque, Blackberry Expert, explains a quick way to hide sent messages from your inbox folder with a few simple clicks, leaving clutter and needless distractions behind. This easy-to-understand tutorial is fully complete from start to save with visible screen shots and clear concise directions. There is even a simple two-button solution to see your sent messages again as needed. With a few easy steps, your inbox clutter can be a thing of the past.

Follow the steps in this how-to video to finally master the art of hiding these unsightly red spots. Try a little bit of Visine to take out the redness and then cover up with concealer. Watch this video makeup application tutorial and learn how to hide a blemish.

Need a way to hide your small pricey or memorable objects? Well, what better place to hide those cherished items than in a burning candle? Unless your robbers have a thing for scented and aromatic candles.

On your MobileMe Gallery Homepage, your visitors can see all of the albums that you posted for them to view, but if there are photo albums that you don't want everyone to see, you can simply hide the album from Apple's MobileMe Gallery Homepage. This video tutorial will show you how to do it, right from your Mac or PC, with Internet of course.

Blogger Jimmy R. demonstrates how you can embed hidden files into an innocent-looking JPEG image using the free 7-Zip and the Windows command line.

Network mapping lets PC users organize multiple computers into a system that provides informational data access. This video tutorial shows how to set file sharing permissions and assign users designated privileges within a network. Establishing a network provides functionality within a workplace and facilitates virtual communication among users.

The Nessus vulnerability scanner, is the world-leader in active scanners, featuring high speed discovery, configuration auditing, asset profiling, sensitive data discovery and vulnerability analysis of your security posture. Nessus scanners can be distributed throughout an entire enterprise, inside DMZs, and across physically separate networks. In this network security video tutorial, you'll learn how to hack a network using Nessus 3.

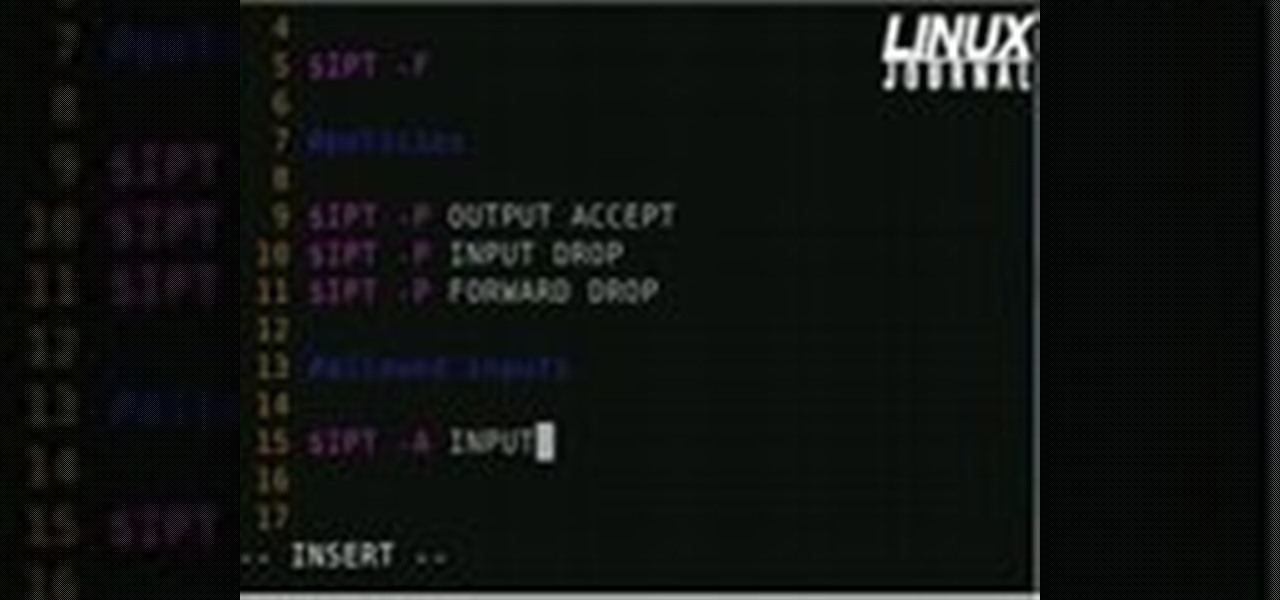
Linux comes with a powerful built-in firewall, although the interface can be a little intimidating. With this multipart GNU/Linux networking video tutorial, you'll master basic and not-so-basic IPTables functionality and create the perfect firewall for your home network. For detailed, step-by-step instructions, watch this Linux how-to.

A DeAuth hack attack against a wireless network, as shown in this how-to video, will disconnect any and all users on a given WiFi network. The attacker does not need to know the WEP or WPA key or be connected to the network. For step-by-step instructions on running a DeAuth hack yourself, watch this simple how-to guide.

Looking for a fun, educational game to play with your children? How about a game of "Hot & Cold"? Played indoors or out, this game helps children refine their listening skills and learn the idea of opposites.

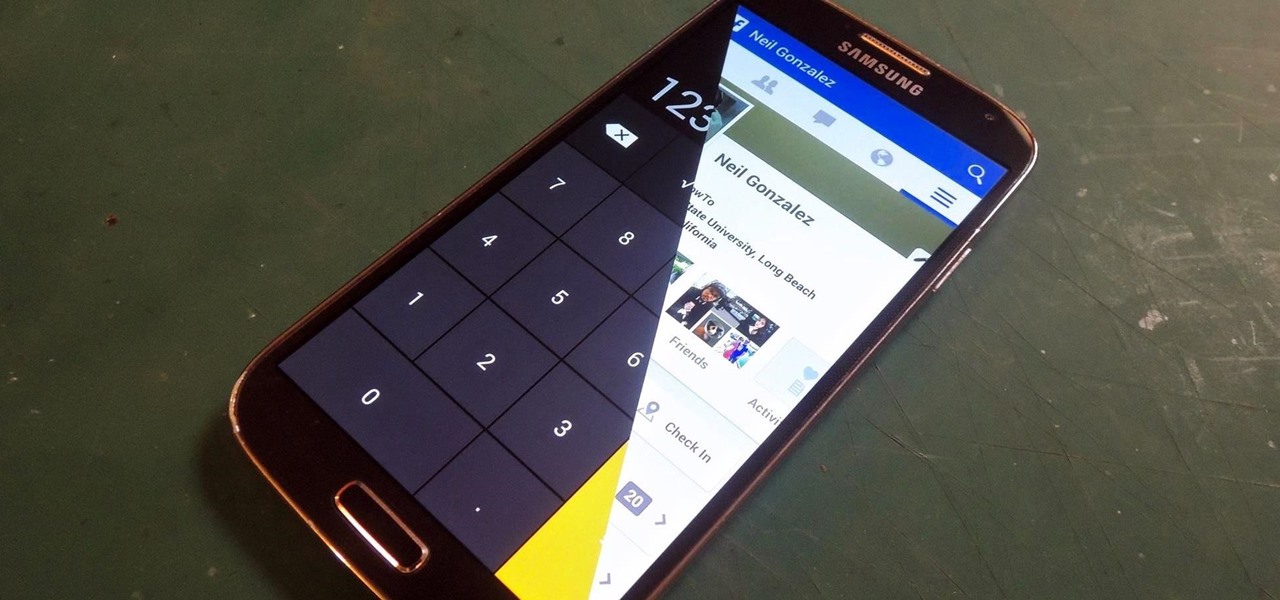
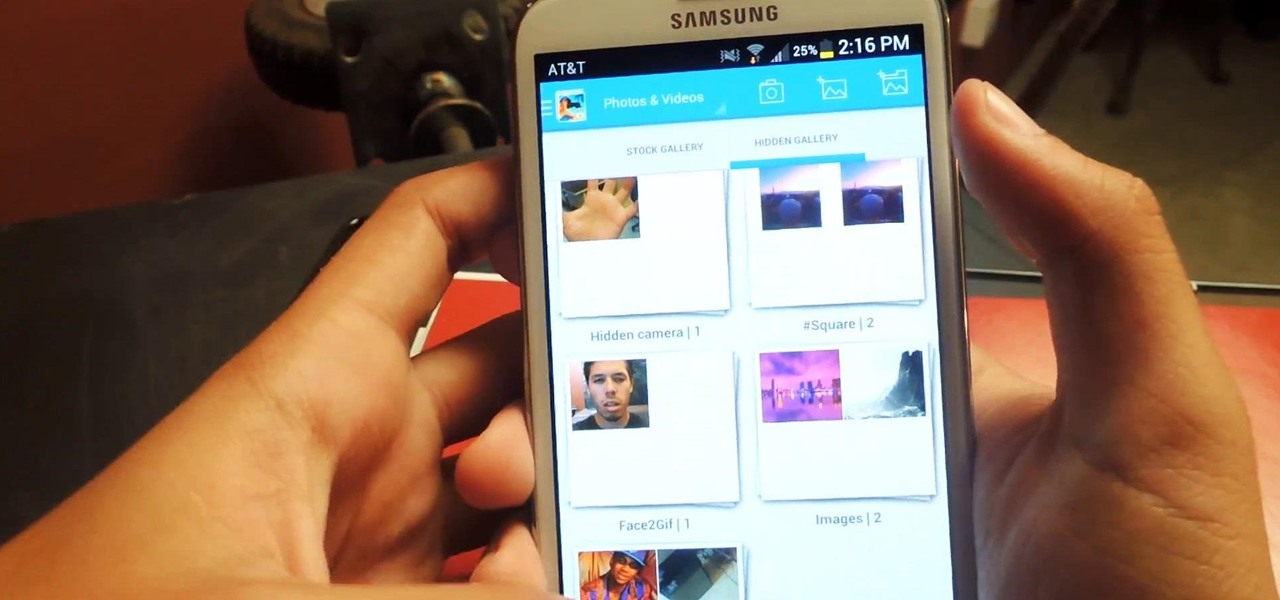
Smartphones have so much sensitive information attached to them. If you share your home with others, then you know the pains of trying to keep anything private. Photos are surely among the things you'd prefer to keep to yourself, so OnePlus has you covered.

Because of Apple's iron grip over iOS, hiding stock applications is a topic we frequently like to cover. While not everyone may think that Apple's preinstalled iOS apps are bloatware, that's exactly what some of them are. For instance, the Apple Watch app; it's basically just an advertisement on your home screen unless you actually have an Apple Watch.

Whether it's embarrassing pictures and videos on your smartphone, or files you just don't want anyone reading, there are plenty of ways to hide them. For most devices, that means installing third-party apps like Gallery Plus - Hide Pictures, Sectos - Photo & Video Vault, TimeLock, or Hi App Lock.

In this Windows 8 tutorial, you will learn how to show and hide desktop application icons. The benefit of this is it allows you to quickly hide desktop icons and show them again when you need to have access via desktop.

The villain Scarecrow reappears in Batman: Arkham City after his first appearance in Arkham Asylum. If you want to find a hidden easter egg involving him, you'll need to use your decrypter. Keep your eyes out for an invoice with a familiar name on it.

The Endor DLC that was just recently released for Star Wars: Force Unleased has three holocrons hidden! This tutorial shows you where each of these collectibles are, including the one in the indoor station that can be tricky to find.

The 1991 Suzuki Sidekick is quite vintage at this point, and they're fun little cars. If your Sidekick's check engine light is on and there's nothing wrong with the engine, use the hidden switch you'll learn about in this video to turn it off.

Interested in finding out just how secure your WEP-protected wireless network is? Let this video be your guide. It's a simple process and this home-networking how-to will teach you everything you'll need to know. For specifics, including detailed, step-by-step instructions, and to get started cracking WEP networks with BackTrack yourself, watch this helpful video guide.

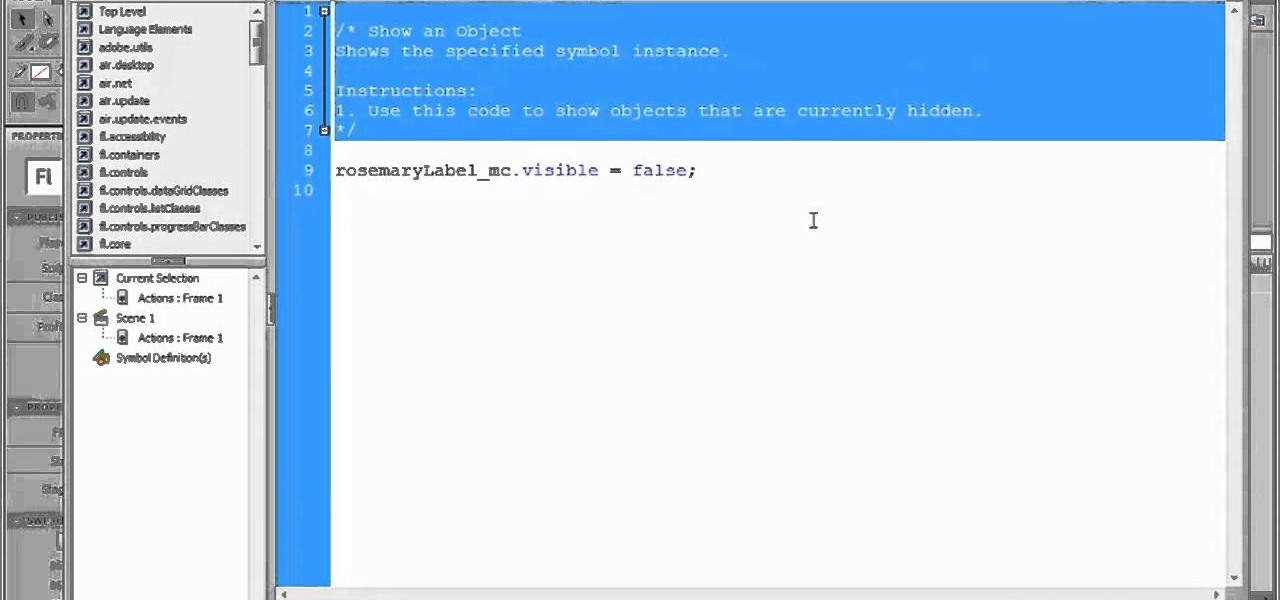
In this clip, you'll learn how to use Code Snippets to display and hide movie clips in Flash CS5.. Whether you're new to Adobe Flash or merely unfamiliar with Flash Professional CS5, you're sure to benefit from this free video software tutorial from Lynda. For more information, including detailed, step-by-step instructions, take a look.

Want to know how to hide the Menu and Status Bars in VirtualBox? It's easier than you'd think! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over four minutes. For more information, including step-by-step instructions, take a look.

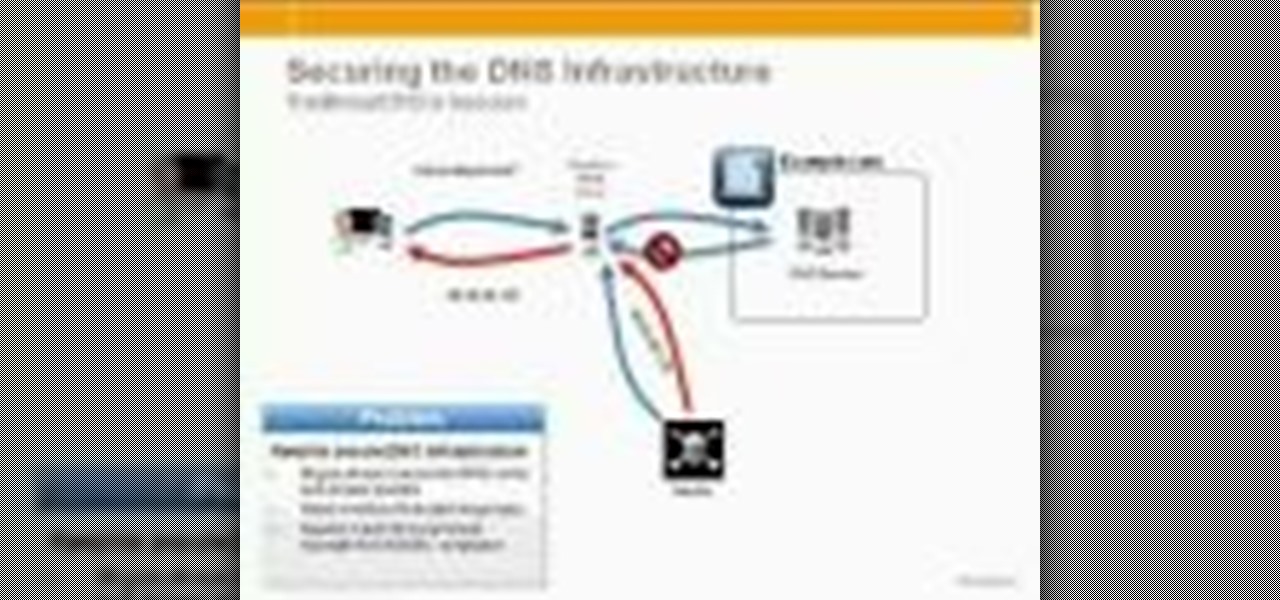
This clip discusses how authorization roles work and their role in the security of the latest release of the F5 Networks Management Pack suite. It also touches on the creation and use of user roles within Operations Manager console and how to apply the authorization tasks to those roles. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with F5 Networks Management Pack suite, you're sure to benefit fro...

In this tutorial, Peter Silva talks with F5's Sr. Field Systems Engineer, Michael Falkenrath about the new BIG-IP GTM v10.1 DNSSEC feature. Whether you're new to F5 Networks' popular network appliance or are a seasoned network administrator just looking to better acquaint yourself with BIG-IP, you're sure to benefit from this free video software tutorial. For more information, including detailed instructions, take a look.