In this Rhino video tutorial we cover how to make a sine and cosine curve with Explicit History (Grasshopper). The initial set up for this Rhino tutorial can be used to test any of the math functions. We set up a a simple interface to drive range parameters which can then connect to many of the scalar components. Get better at your math skills for modeling in Rhino with this 3D software tutorial. This Rhino video is best viewed full screen. Make a sine & cosine curve Rhino's Explicit history.

Grasshopper is a new plug-in that David Rutten is working on for Rhino. It has similar functionality to GC but at this point if not so component based. It is more like GC in that it uses features and stores them as nodes you can rearrange and change hierarchy’s. In this video David covers where to find the plug-in, how to install it and then the very (let me emphasize the VERY) basics of the interface. Learn how to install and get started using the Explicit History plug-in (also known as Gras...

The used video game market represents a huge portion of retail game sales. It's the only avenue in which most people can afford to buy AAA games. But game publishers aren't exactly big fans of used game sales, since they only benefit from gamers buying new ones. GameStop and Best Buy are huge corporate interests, so EA and the rest of the big publishers out there have not been able to push them around on the issue of used game sales... so far.

The Origami Spiked Pentakis Dodecahedron is an excellent Paper Christmas Decoration Star made out of 15 paper squares. In spite of the large paper size I was defeated by the last module after nearly 2 hours (!) of trying to lock the last unit in place each time another one dislodged. Never mind, it is still a remarkable sound structure once (nearly) completed and you can not see which one is not locked anyway.

Have you ever looked at a piece of fruit and thought to yourself, "you suck, fruit, sitting there all smug and happy, I wish I could just destroy you here and now?" If so, read on—your favorite Fat-man is going to show you how you can get your revenge on that happy smug fruit sitting in your fridge by breaking an apple in half with your bare hands.
If you're new to the Visual Basic IDE, looking to brush up on your VB programming skills, or simply have a burning desire to code a simple calculator, this three-part video lesson is for you.

This session is tailor-made for advanced Studio users aiming to achieve ultimate quality surface creation.

Apple has tools built into iOS to help parents monitor the iPhone habits of their children. However, those same tools can be used by everyday iPhone owners to both hide apps they don't care about, as well as restrict features they don't need or that infringe on privacy. Whether you fit into one category or the other, all iPhone users can benefit from the "Restrictions" feature.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

Weeks before the music video for Nicki Minaj's Sir Mix-a-Lot-sampled single “Anaconda” dropped, an internet frenzy was sparked thanks to the help of an extremely racy cover image, several promo pictures with her "dancing" with label-mate Drake, and a teaser clip that showed Nicki twerking that hypnotizing booty.

For the most part, Google Play Music makes it extremely easy to upload and organize your music library, as well as access it quickly using the default settings—but there are a few things it could do better.

YouTube is the first place I go to watch funny videos online—me and about a billion other people. But one thing that always annoys me is having to sign in time after time to view age-restricted videos.

If you bought the new iPhone 5 or upgraded your old one to iOS 6, you may be having issues when you try to upload photos to Facebook. After updating, the first time you try to share an image from the Facebook app, it will ask you to allow access to your Camera Roll.

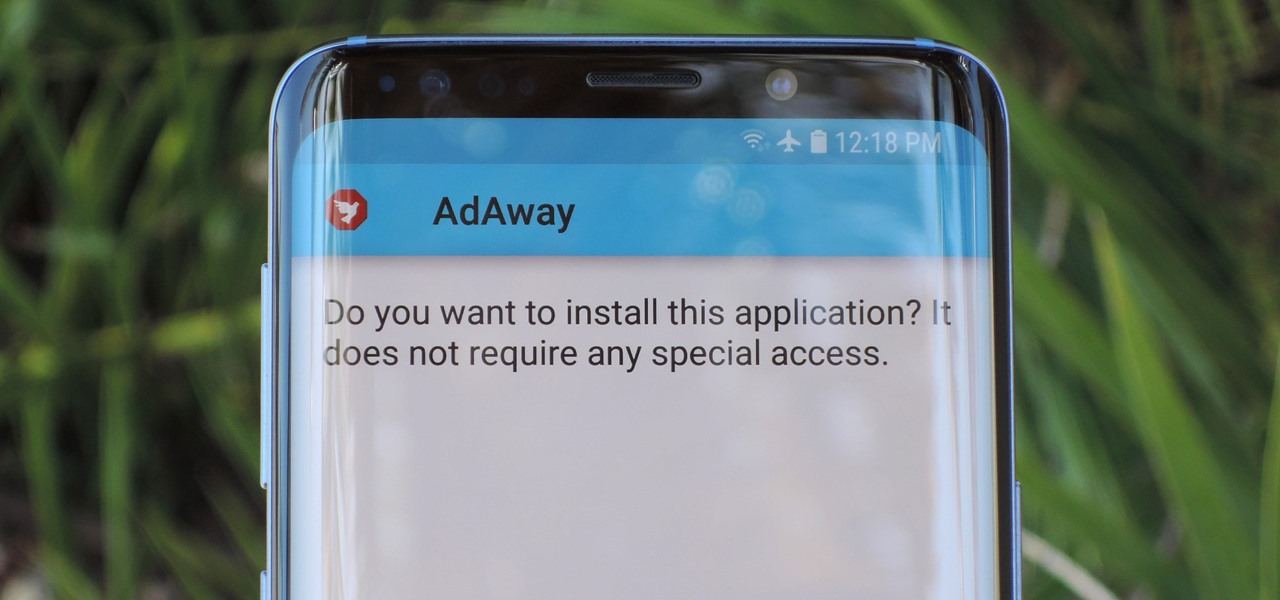
One of Android's biggest strengths relative to iOS is how simple it is to sideload apps that aren't on the official app store. Rather than having to sign IPA files or tell your phone you trust a developer every two weeks, you can just enable a setting and be done with it.

With significant advancements in the treatment and prevention of HIV, you'd think the stigma surrounding the deadly virus and AIDS, the syndrome the infection causes in the body, would have lessened. Unfortunately, a new project looking at conversations on Grindr — a social networking app for gay, bi, curious, and queer men — has shown that this stigma is very much present.

Texas has become the 18th state to pass a bill into law regarding autonomous vehicles, the third this month to do so.

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

Back in March, Samsung partnered with Slacker Radio to create a streaming service called Milk Music. For those of us who don't own a Galaxy device, this news was a non-starter, as it was exclusive to Samsung's flagship line of phones and tablets.

In direct competition with Pandora, iTunes Radio, and Spotify, Samsung has just launched Milk Music—a strangely named, yet completely free music streaming service for Android.

You really can't go wrong with Samsung Health when it comes to staying on top of fitness-related data. Its features help you keep track of workouts, track calorie and nutrition intake, and monitor your heart rate, just to name a few. And if you start exhibiting symptoms you've never had before, you can even use the app to find out more about what's wrong with you.

Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

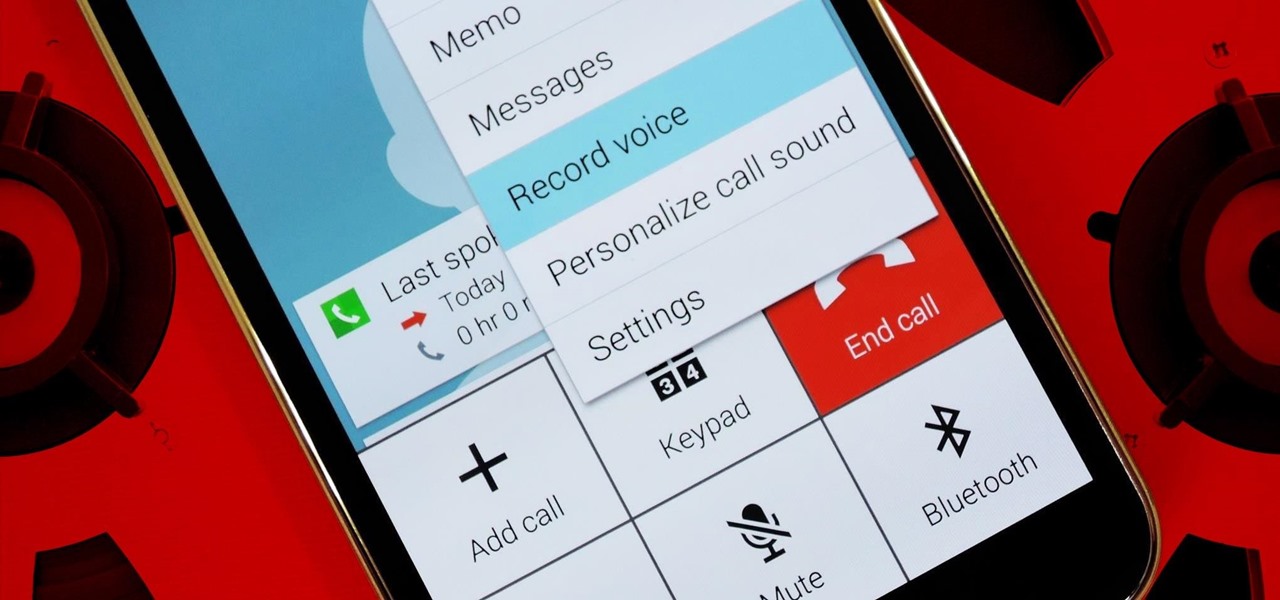
Before your carrier got its grubby little hands on your Galaxy S5, there was less bloatware installed and more functionality offered by the Samsung flagship device. Case in point: the GS5 that Samsung designed was capable of recording phone calls, yet the one that you own probably isn't.

Samsung's exclusive music streaming service, Milk Music, has been making waves across the web thanks to its peculiar name and ad-free stations.

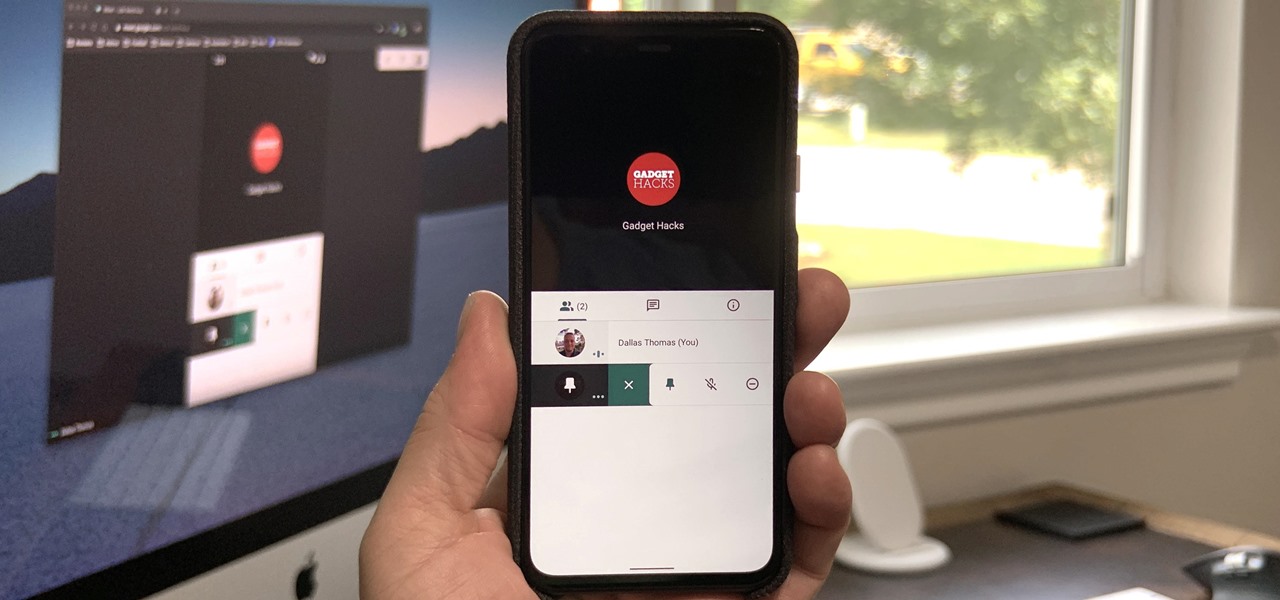
Now that Google Meet is free for anyone with a Gmail address, you can expect to see invites from Google's service alongside Zoom calls.

In a disturbing turn of events, Uber has been tracking oblivious iPhone users even after they removed the application from their phone. Two years ago, the situation escalated to such an extent that CEO Travis Kalanick earned a slap on the wrist from Apple mogul Tim Cook.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Put yourself in Google's shoes: You know that business is becoming increasingly mobile, but the mobile operating system you maintain is wide open by design, and it's garnered legions of loyal fans that love to explore and exploit every aspect of it. There's a clear conflict of interest developing.

When a new version of iOS comes out, everybody gets caught up in the craze of finding features and playing around with new functionality. But this generally leads to a lack of coverage on the finer aspects of the update—things like bugs, minor tweaks, and pain points that users discover along the way.

When Microsoft release an update to the HoloLens Development Edition at the end of May, there were a bunch of cool new features added in. Among them: New voice controls that make working in the HoloLens operating system much easier.

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

Gboard is one of the best third-party keyboards available for iPhones, but you probably don't know everything you need to know about it to become a real Gboard pro and stop using Apple's stock keyboard for good.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Apple's iOS 13 for iPhone includes new features in Safari that make browsing the web a little bit better when compared to iOS 12. Some changes are small while others add functionality that just wasn't there before. Plus, there are more security enhancements.

Every summer for the last 26 years, hoards of hackers have descended on the Las Vegas Strip for DEFCON, the biggest hacker conference in the US. There's a wealth of talks every season (DEFCON 27 has at least 95 scheduled), and there have been some essential topics to learn from in past discussions. We've dug through the last ten years and found the 15 most popular talks you should watch.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

Apple offers many ways to customize the Home Screen on your iPhone, from adding widgets and scheduling rotating wallpapers to hiding apps and entire pages. But some of the best ways to customize your Home Screen are options Apple won't even tell you about, either because they haven't become official features yet or because Apple is OK with the workarounds.

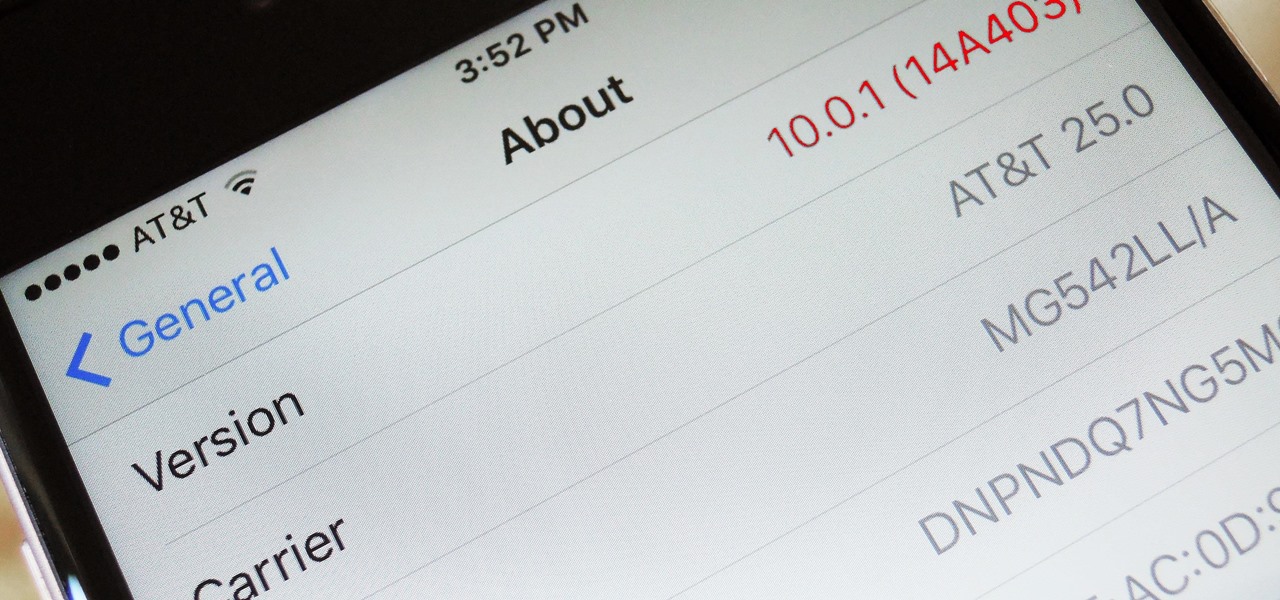
Apple just seeded the fourth public beta for iOS 13 to software testers today, Tuesday, July 30. AppleSeed participants saw this beta one day early, alongside the release of developer beta 5. Now, developer and public testers alike are up-to-speed with the latest in iOS 13.