Watch this video tutorial to learn how to use hand signals on a bicycle. Bicycles don't come with turn signals and brake lights. Fortunately, there's already a universal language for indicating turns and stops on a bike.

Watch this video tutorial to learn how to prevent swimmer's ear. Don't let this painful infection of the ear canal keep you out of the water! A few simple precautions can combat the excessive moisture that causes bacteria to fester.

Learn how to keep your hair healthy. Having healthy hair is easier than you think. Follow these simple steps for lustrous locks.

Are you constantly battling chapped lips? The right prevention methods can restore lip moisture in no time. Watch this Howcast guide to learn how to prevent chapped lips. Nobody wants chapped lips - lips should be soft and kissable.

Everyone who owns or runs a website needs to know how they can improve traffic, and search engine optimization is the answer. This 13-part video series on SEO basics and strategies will give you more traffic for your site. It's jam-packed full of tons of great SEO tips! Check out each video in the series:

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Waze is the go-to navigation app for millions of drivers, and it's easy to see why. Benefits such crowd-sourced traffic data, police trap locations, and road work avoidance are just the tip of the iceberg. It can almost be overwhelming, but with these simple tips, you'll master Waze and start navigating like an expert in no time.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

Crazy Taxi is a Facebook game that allows you to drive crazy in a cab. Watch this video tutorial to learn how to cheat and remove the traffic on Crazy Taxi (08/17/09).

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will explain how stripping file extensions from URL's affects both Google rankings and user behavior, information that will help you design your s...

jQuery is a popular and powerful Javascript that is easy to use and heavily extensible. Have you wanted to learn how to use it, but lacking in the Javascript skills expected of you by many tutorials on the subject? This video for beginners will introduce you to the basics of using jQuery, from downloading it to making your first projects. Now you can take advantage of this powerful library to make your websites more dynamic and increase traffic.

Trying to get more traffic for your Wordpress blog? Looking to connect with the people who visit you online? This video will show you how to facilitate web interactions by adding social media icons to your blog's header. This video uses the 2010 theme to demonstrate. CSS may be intimidating, but this video will show you exactly what to do.

In this clip, you'll learn how to get started using Blue Coat PacketShaper on your Microsoft Windows PC. It's easy! So easy, in fact, that this helpful how-to can present a complete overview of the app in just under four minutes. For more information, including detailed, step-by-step instructions, take a look.

Brake fluid is important, we all should know this. If you're in the city, then you know that once that stop and go traffic hits, you're going to want some good response out of your brakes. An in-depth look at checking the brake fluid and how to add more.

Customize your directions on Google Maps. Drag and drop the default directions to your preferred roads or highways, get walking or public transit directions, route around traffic, or add multiple stops on your way.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

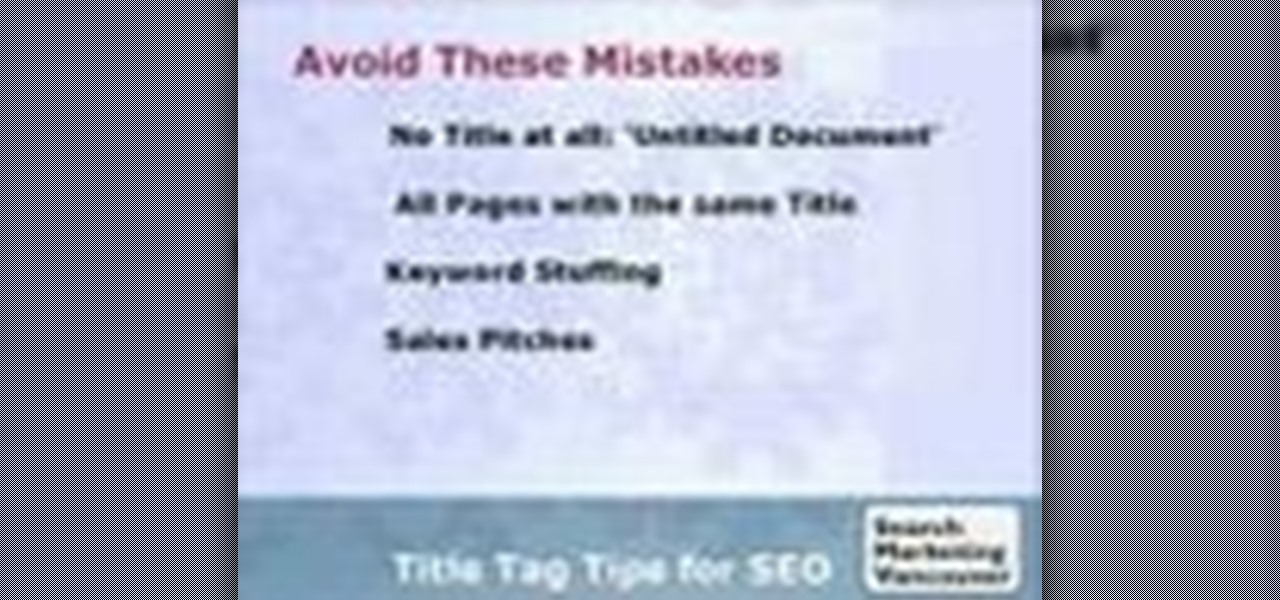
How to write Page Titles for your Title Tags from Search Marketing Vancouver. Learn how effective Title Tags can improve your SEO Results on Google and increase traffic to your website.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

As was mentioned by the great OTW last week, TOR, aka The Onion Router, has had its integrity attacked by the NSA. In an attempt to reduce the anonymity granted by the service, the NSA has opened a great many nodes of their own. The purpose is presumably to trace the origin of a communication by compromising some entrance and exit nodes. Once both are compromised, it is much easier to correlate traffic with a particular individual.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Here is a manoeuvre that you won't see every day. It is intended for drivers in commercial vehicles who cannot see to the rear. By reversing with the flow of traffic it is possible to see approaching vehicles through the front windscreen and the right hand kerb by looking down over your shoulder. This manoeuvre sometimes occurs on the ADI, Part 2 Test of driving ability.

Speeding tickets are one of the worst things a driver fears on the highway, aside from wrecking, of course. But you can get home safe without getting a ticket. You just need to keep your vehicle off the radar by following these stealthy driving techniques.

Brickbiys518 here, teaches you to make a LEGO cabinet. You need one 2x6 thin, two 1x6 chunkies, six 2x1 thins with the dot in the center and 12 traffic light bricks. To start off, take the 12 traffic light bricks and put them into stacks of two. There are 6 stacks in the end. Lay them out horizontally one below the other. Take the 1x2 with the dot in the center bricks and put them on two stacks at a time thereby joining the two stacks. In the end, you have three stacks. Put them aside and tak...

The experts at Bunning's have come up with a few tips for the consumer to consider when they are next in the market for paving equipment. Find out if the job needs a solid block paver or a thinner grade paver. Preserving the tools once they leave the store is in your hands. Last, but not least, watch the weight!

You see someone doing something illegal and there are no police officers around. Do you have the right to play cop? Here’s the lowdown.

This video gives you the lowdown on making a lag switch for gaming. But why would you want a lag switch? What is a lag switch?

Inspired by the glittery, flickering lights she saw as she drove through the city at night, Michelle Phan came up with a luminous and sexy makeup look, which she presents here in this tutorial.

You don't have to be a frequent flyer to know how indispensable navigation apps have become. Many of us rely on these apps for traveling from state to state and getting around in foreign cities, but even more of us count on these apps to beat rush hour traffic and find the quickest routes to school or work. So naturally, we all have our favorite mapping apps, but which one is truly the best?

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Your best chance of getting to a destination on time during rush hour is to drive through relatively empty HOV lanes. Thankfully, if you're using Waze to navigate through traffic, you can easily locate HOV or HOT routes to optimize travel times by adding your toll passes in the app's settings.

From Instagram bot farms in China all the way to vending machines in Moscow that promise to sell you fake followers — the Facebook-owned empire is attracting the attention of the world around. When it comes to Russia especially, the country seems to be developing a little crush on the glorious IG queen.

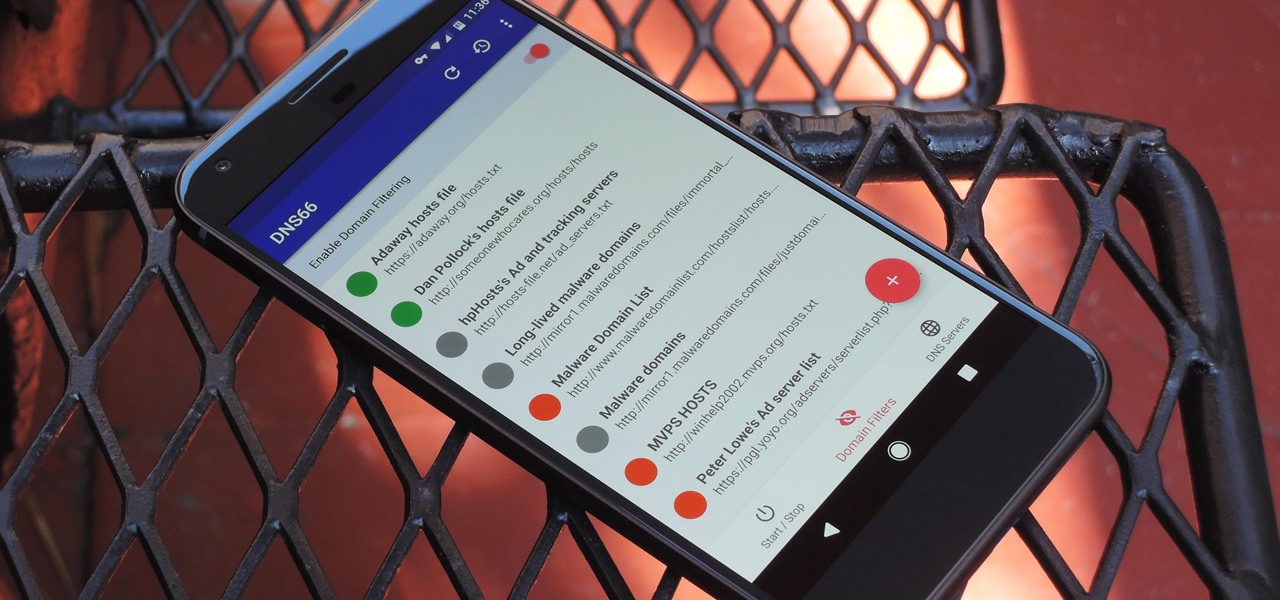
If you're in the market for a non-root ad-blocker, developer Julian Klode has an app that you'll definitely want to check out. It uses Android's VPN system in a similar manner to alternative apps like NetGuard and AdGuard, but it's got a new twist that should save lots of battery life in the process.

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

A VPN service is almost an essential these days. Good ones can block ads, prevent tracking cookies, encrypt your internet traffic for better security, and even spoof your device's location to bypass geo-restrictions — all things you should be concerned about in the age of NSA snooping and Facebook data mining.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.