
How To: SQL Injection! -- Detailed Introduction.
Hello NullByte! This will be my first How To series.


Hello NullByte! This will be my first How To series.
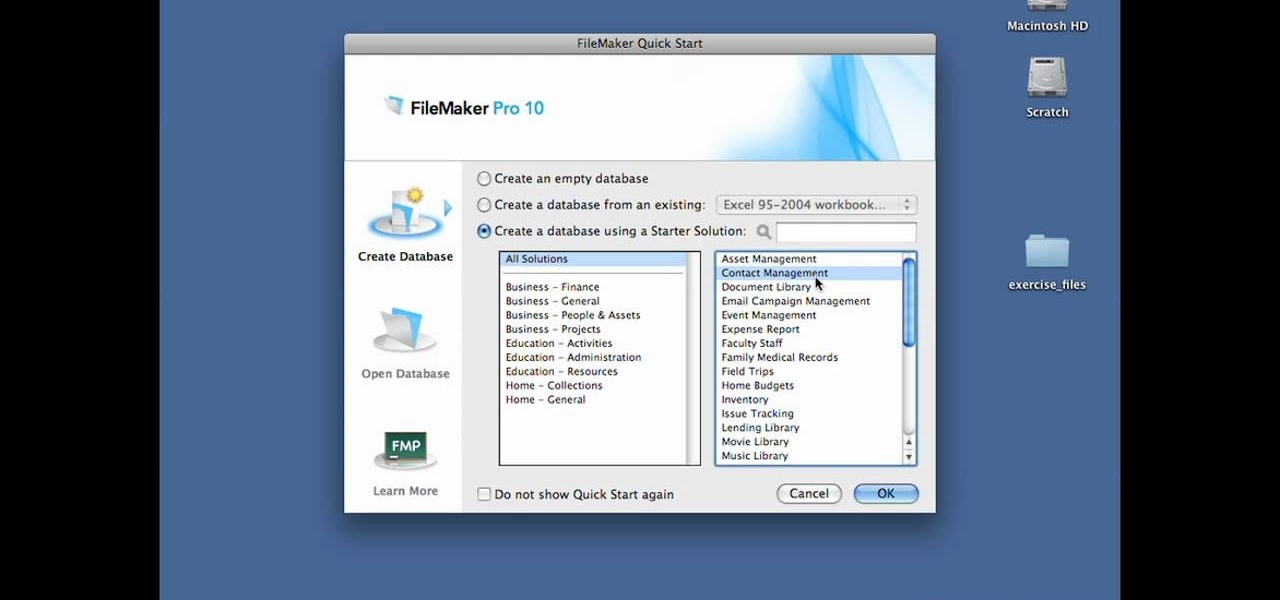
In this Lynda video tutorial, learn how to use FileMaker Pro 10 software to create databases with pre-made templates. FileMaker offers these templates in a package called Starter Solutions. To access these options, click open FileMaker. Then, go to New Database under the File menu. Click the option "Create a database using a Starter Solution." The templates are grouped according to the nature of their use. Some are for the home, while some are for business. All you do is open the template you...

Ever since we read "Rapunzel" as little girls, we've been enamored with long hair. Beautiful, neverending, and silky, it was the ultimate emblem of femininity and we've been rocking the long locks ever since.

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.
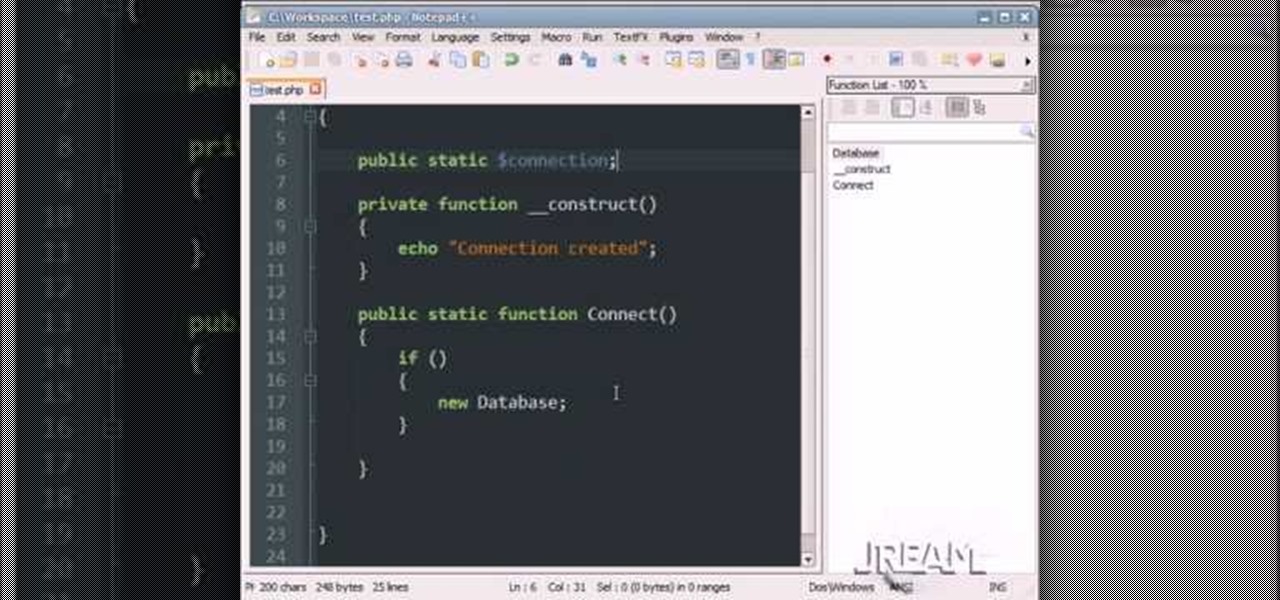
This PHP newbie video with teach you what a Singleton Pattern is and how to use it in your PHP programming. PHP OOP Singleton is great for a database connection when you only want one consistent connection in your application. So, to prevent wasting space accidentally by calling it twice in different areas, this is good way to protect it. Singleton is very popular and used often in Database Connections.
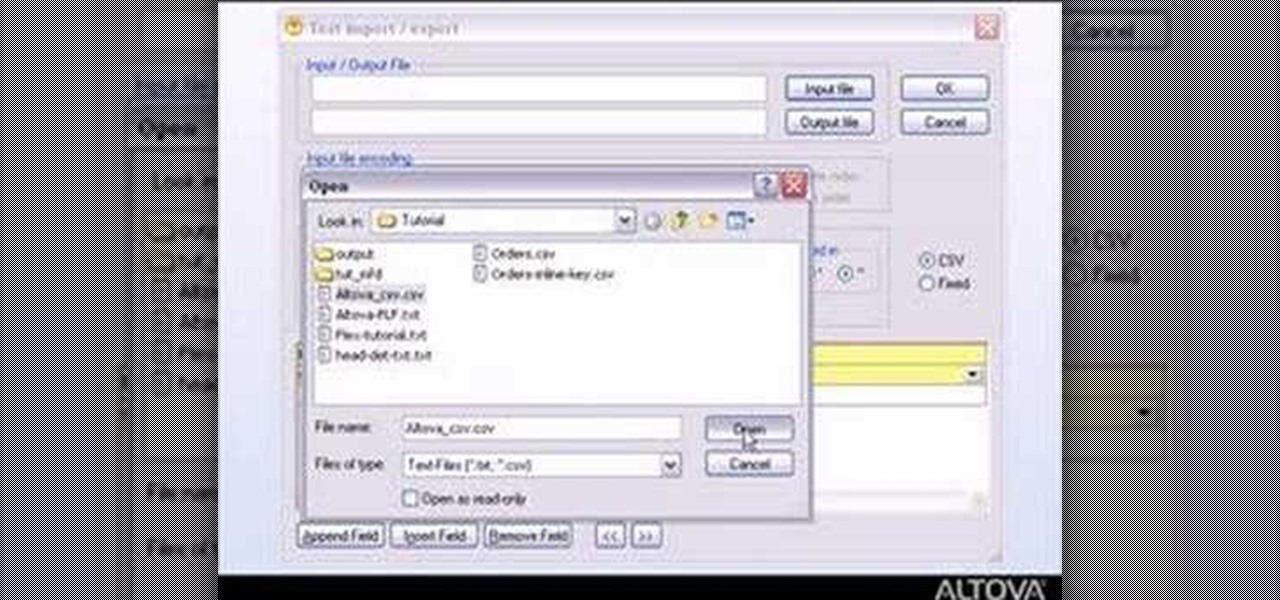
MapForce supports flat files as the source and/or target of any mapping involving XML, database, EDI, web services or other flat file data. In this how-to, you'll find instructions for mapping data from arbitrary text files (such as log files, CSV, fixed-width, and other legacy data sources) to databases and XML files.

If you're new to DreamCoder for MySQL, one of the first things you may want to know how to do is export data from a remote MySQL database. Happily, this tutorial will walk you, step by step, through the process. To get started exporting MySQL data with DreamCoder, take a look!

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.
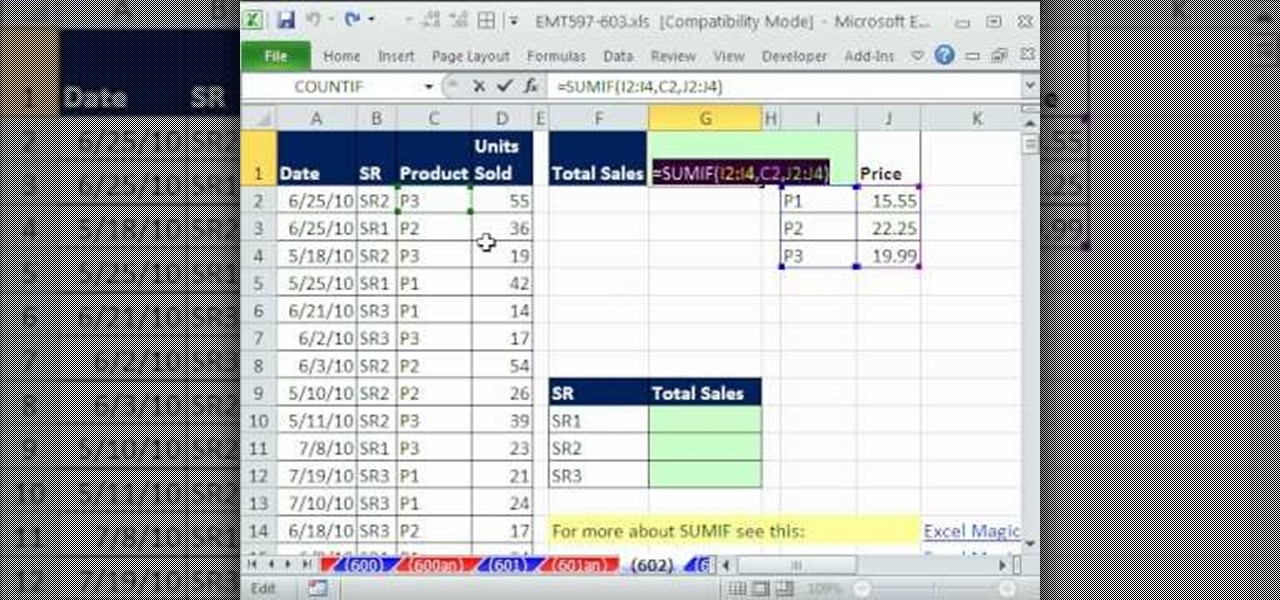
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 602nd installment in their series of digital spreadsheet magic tricks, you'll learn how to create a compact array formula that can total sales with 1 criteria when the database does not have a price or total sales column. See how SUMIF can be used to lookup values and simulate a missing column from a database.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.
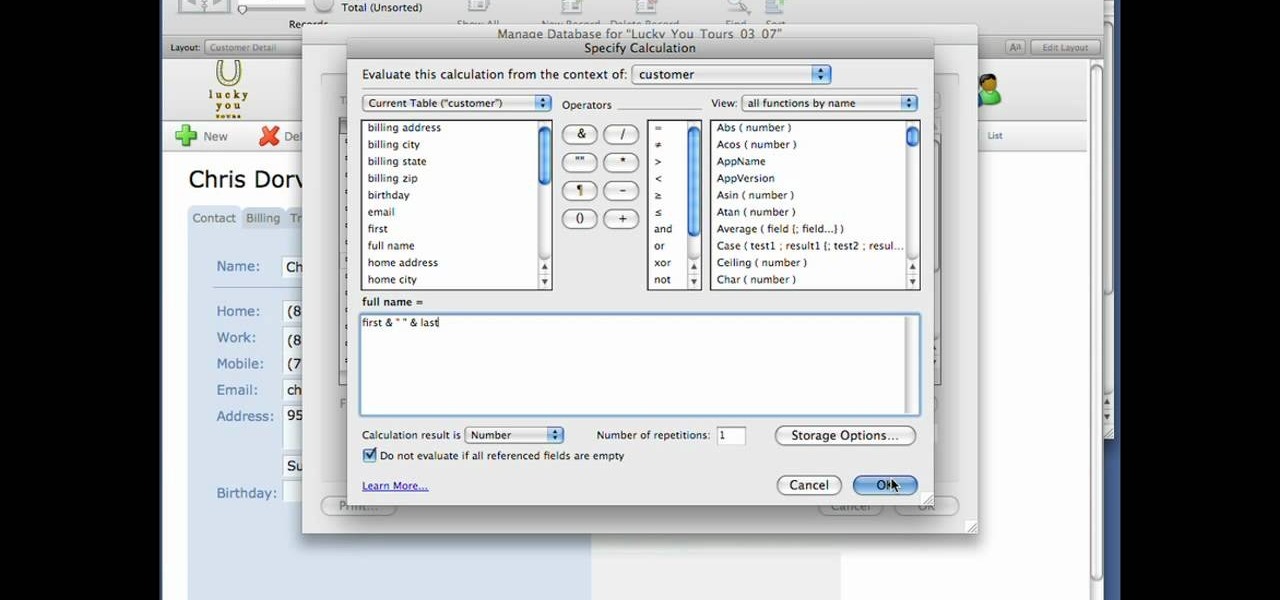
If you are a user of FileMaker Pro then this video teaches you how to use calculation and summary fields in it while making new files. In Filemaker you can create a various kind of fields that you want your file to contain. In Filemaker a calculation is a data that gets computed depending up on the formula that is set in the Filemaker database settings. Calculations are very critical in file management. Open the Manage Database and there you can find some of the calculation fields. There in t...

This video demonstrates how users of the FileMaker Pro 10 software can easily start using this software from the quick start menu. It is demonstrated to users how to create a database or open an existing database from this quick start page. Also demonstrated is how users might be able to find further information using the "Learn More" option at the bottom of the menu. This option shows users the basics via videos, tours, and tutorials. A must see for those new to this software.

Ever think to add flowers to your butter? No? Well, you're missing out! In this tutorial, learn how to make Nasturtium butter with fresh picked flowers. This makes the butter beautiful, colorful and gives it a unique flavor. These flowers grow easily in most any backyard, so add this interesting twist to your meal tonight and impress your partner.

For an easy way to lookup and connect with people and companies across the web (and all of its many social media outlets) check out the Firefox extension Tabble. Tabble provides you with access to all of an individual's relevant online information and can even show you relevant e-mails in your Gmail account if applicable.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to optimize your deep web content, like databases and forms, to be crawled by Google using a few simple tricks.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.
Full-Text search allows you to save large portions of text – even Microsoft Word documents, or other file formats – into your database and perform complex queries based on this textual data while expecting great performance. This lesson demonstrates how to set up Full-Text search paying particular attention to the nuances of setting it up within SQL Server Express. Enable full-text search in an SQL database.

Google just unveiled it's biggest search product in recent memory, except this time the search giant is looking to take over the world of virtual objects.

This is my first How-To on Null-Byte, so I hope it's not too complicated written, because I am not a native english speaker. I don't use pictures, but this Tutorial is a good supplement for my updated Tutorial here.

In this tutorial, we learn how to cite articles from online library databases in MLA. Make sure you have all the information available so you can include all of the information for the citation. The citation will be written in the following order: author, article title, publication title, volume and issue numbers, date of publication, and page numbers. Make sure you use only italics and do not underline. URLS are optional and depend on instructor preferences. Make sure you include the publica...

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 312th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the DATE, MID, LEFT and TIME functions to extract dates and times from a database field that stores dates and times as a text string.
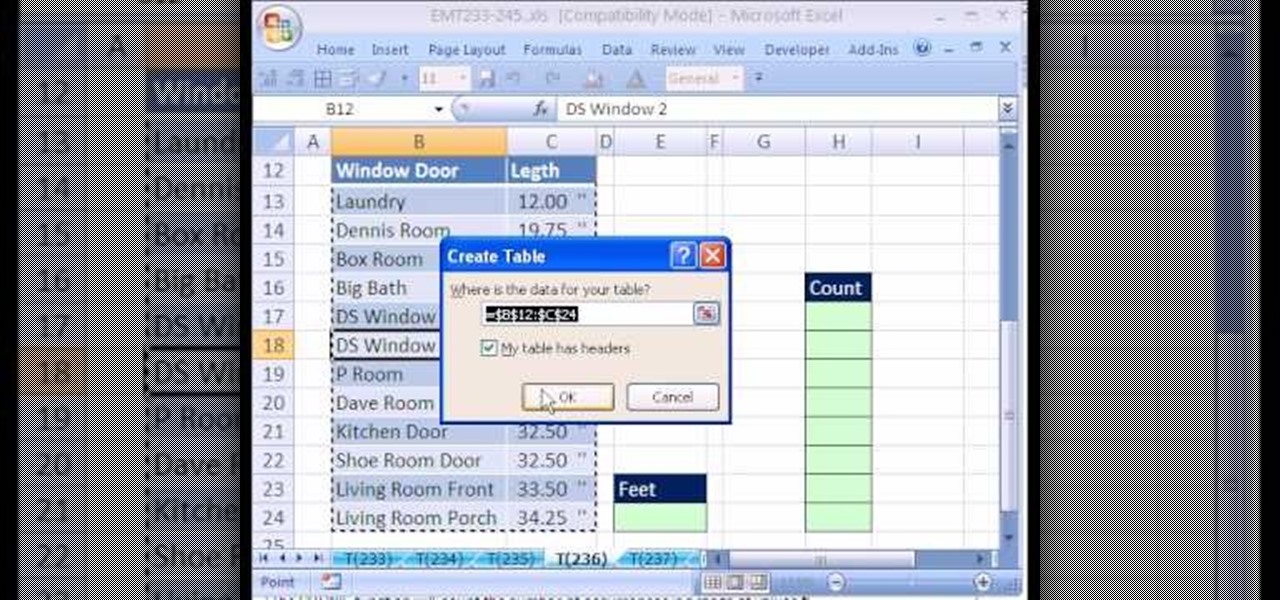
New to Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 236th installment in their series of digital spreadsheet magic tricks, you'll learn how to create a database for keeping carpentry measurements as well as how to use a COUNTIF function formula for calculating how many lumber pieces you'll need to cut for your home improvement project.
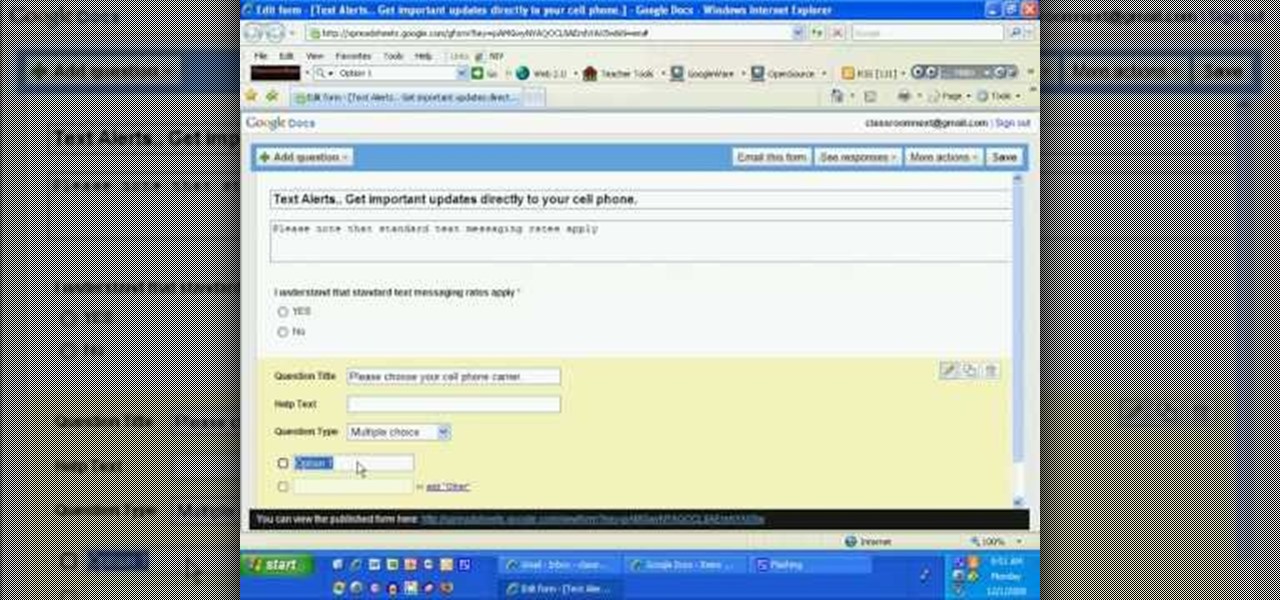
This video explains how to create a database text alert using Google Forms. In Google documents click on new, then form. After naming the form and typing in that standard text messaging rates apply, our presenter selects multiple choice yes or no options. Select it to be a required question so that the user can make sure they understand terms. You can choose to select any or all of the questions to be required. You can then type in various questions for the user to answer-our presenter wants ...

In Access 2010 you can now create a navigation form (like a home page) for your database without writing a single piece of code or logic! Great for busy people who need to organize their database quickly, but who don't have code writing skills. It's just drag and drop. There are predefined layouts which help you design the form and then simply drag the information you want into the form. Reports can be added and accessed quickly from the navigation form so you can analyze the data simply and ...
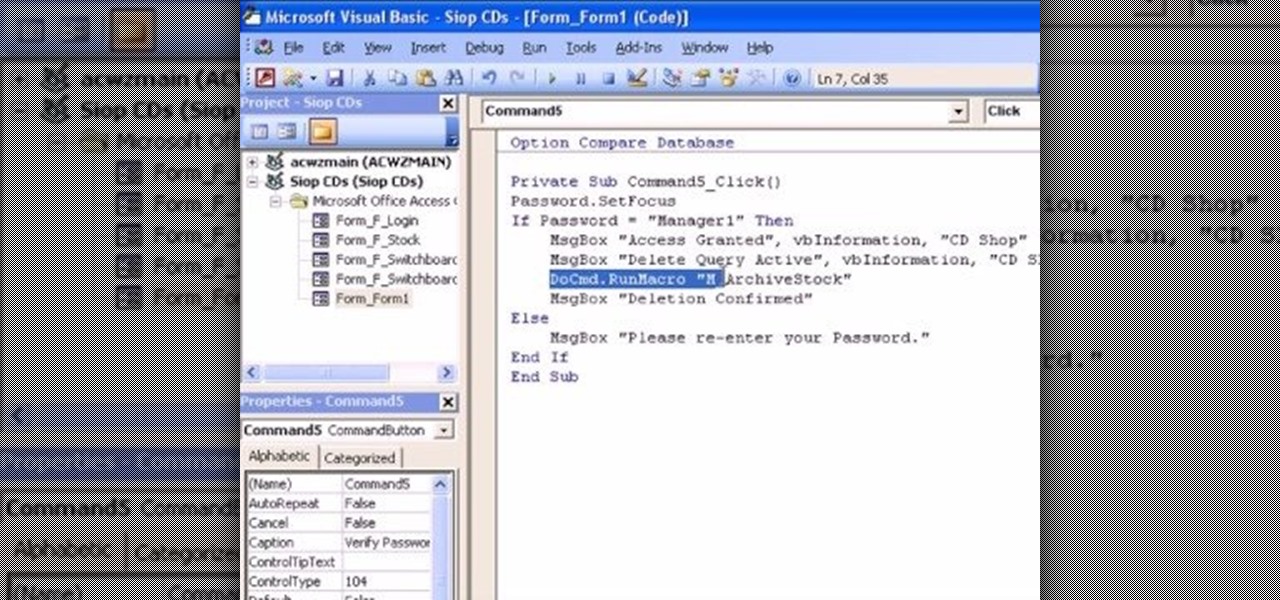
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn how to force a password to be entered in order to run a query.

If you're of the older generation (and by older we mean you're completely not feeling the Justin Bieber thing, so let's say mid twenties), then you probably grew up watching a slew of happily ever after Disney movies.

Every one knows what ivy is, but most think of it as the poisonous ivy that gives a horrible itchy rash, but poison ivy isn't the only kind out there. There's beautiful ivy that can make your home more elegant than ever. Growing the prolific ivy plant will convince you that you have a green thumb while adding fresh beauty around your house, indoors and outdoors.

Now that we've learned about keeping all our data safe with encryption, it's time to continue progressing through getting your Mac set up for hacking.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.
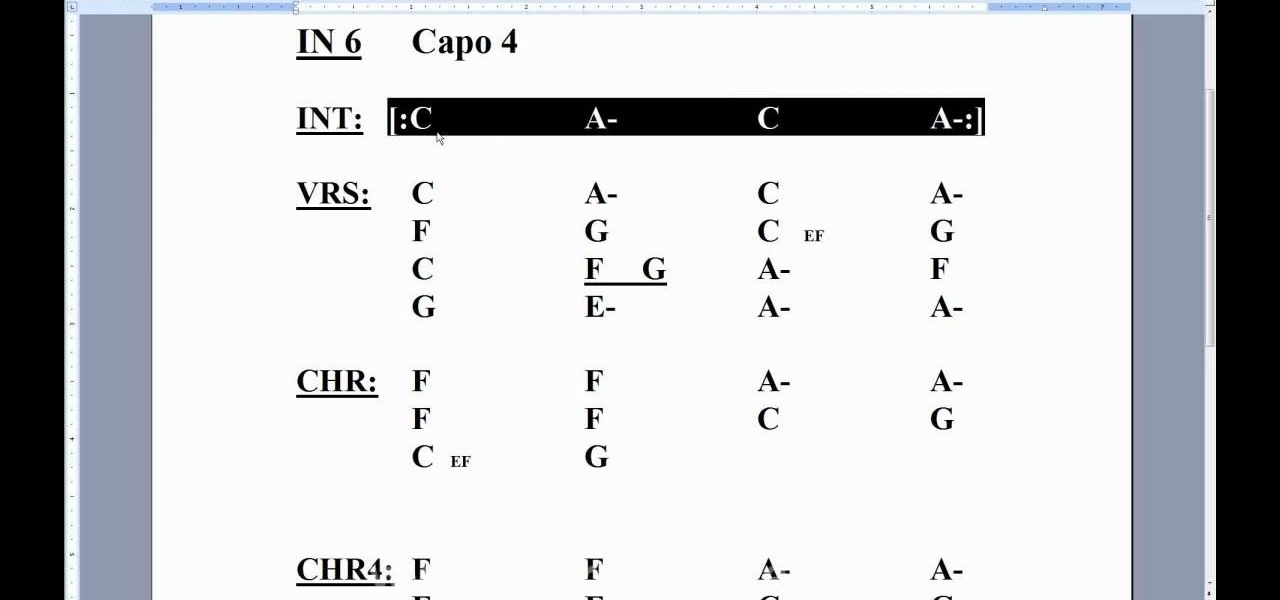
In this clip, we learn how to employ chord charts when playing the uke. Thinking about learning the ukulele? Well, you're in luck, as, thanks to WonderHowTo's ever-growing library of free video ukulele lessons, it's never been easier. For more information, including detailed, step-by-step instructions, and to get started tuning your own ukulele by ear take a look.

In this clip, we learn a number of simple uke strumming patterns. Thinking about learning the ukulele? Well, you're in luck, as, thanks to WonderHowTo's ever-growing library of free video ukulele lessons, it's never been easier. For more information, including detailed, step-by-step instructions, and to get started tuning your own ukulele by ear take a look.

In this clip, we learn how to tune a uke by ear. Thinking about learning the ukulele? Well, you're in luck, as, thanks to WonderHowTo's ever-growing library of free video ukulele lessons, it's never been easier. For more information, including detailed, step-by-step instructions, and to get started tuning your own ukulele by ear take a look.

Martinis, though timelessly classic, are experiencing a resurgence of popularity. Some prefer the traditional gin martini, while others dabble in the ever-growing field of sweet, fruity, and specialty drink martinis. Watch this video mixology tutorial and learn how to make a chocolate martini, a classic gin martini, and an appletini apple martini.

Introduction In this post we will look at how to access a PosgreSQL database in your C/C++ application. It's not as hard as you might think, but you need to understand the procedure and the functions used.

Whatever your reasons for doing it, if you are trying to hack passwords, it helps to have the right software for getting the job done. With the Cain and Abel program, you will be well on your way to hacking even the toughest personal passwords.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.