iTunes makes it easy to take all the music from your CD collection and add it to your iTunes library. ONce added, you can enjoy any song anytime without ever needing your CD again. All you need to do is import your music.

Ever wanted to solo over the chord progression from Carlos Santana's "Samba Pa Ti" on your ukulele? Who hasn't, right? This ukulele lesson presents a quick overview of a highly adaptable G scale pattern that works over the progression in Carlos' Santana's "Samba Pa Ti." For more information, or to get started soloing over Santana's "Samba Pa Ti" on your own ukulele, take a look.

Have you ever wanted to make your own lava lamp? If so, all you need are a few things from around the house:
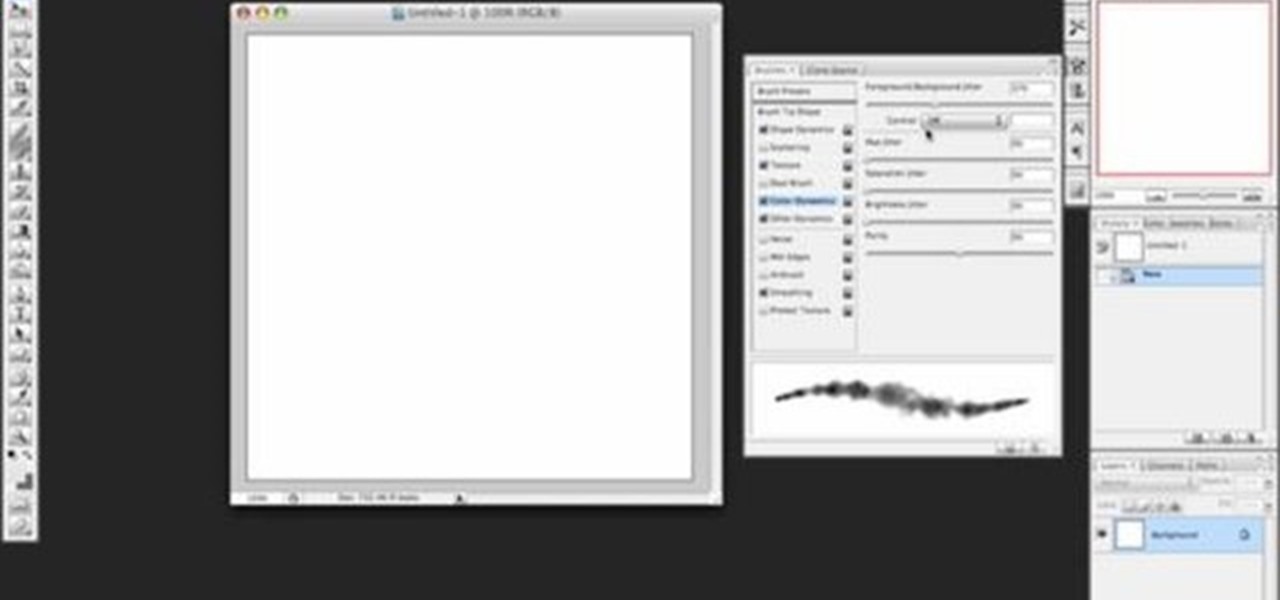
If you've ever wanted to make smoke using Photoshop you'll be able to watch this software tutorial and find out how. This smoke effect won't help your movie career but it will help you create cool photos.

In this how-to video you will learn what trout eat and what lives on the river bottom. Have you ever wondered what you have to do in order to properly fish for trout? This clip explains what you will need in order to find these trout.

Ever wonder what tree is which in the bush, or what each tree is useful for? This video tutorial will show you how to identify the various trees that are useful in Bushcraft. Andrew Price explains the difference between the trees, like Ash, Beech, Holly, and Elder trees, and their uses. If you need to survive in the wilderness, this is a great way to do it.

Going up? This video will teach you how to hack an elevator, making it go directly to the desired floor without stopping. If you're ever in a hurry or, heaven forbid, a genuine emergency and need to get to the bottom or top floor quickly, you'll be very happy you watched this how-to video. Learn how to enable the "express mode" in most any modern elevator with this great pushbutton hack!

Learn how to make the coolest and most professional cheat sheet ever! Warning -- this video is for educational purposes only. We are not responsible for any damage caused by cheating at school. You take the responsibility, because it was you who didn't study, right?

Sexy Playboy Cyber Girl Dana Dicillo has some advice for you in making your audition video for Holly's 55th Anniversary Playmate Search reality show. If you ever wanted to be in Playboy, you need to watch this.

Check out this video from Make Magazine! Watch Action Girl and Bre Pettis show you how to make a Rubik's Cube out of dice, magnets and epoxy. Interestingly enough, the first Rubik's Cube ever was made with magnets! We found inspiration in Gfixler'and Burzvingion's instructions.

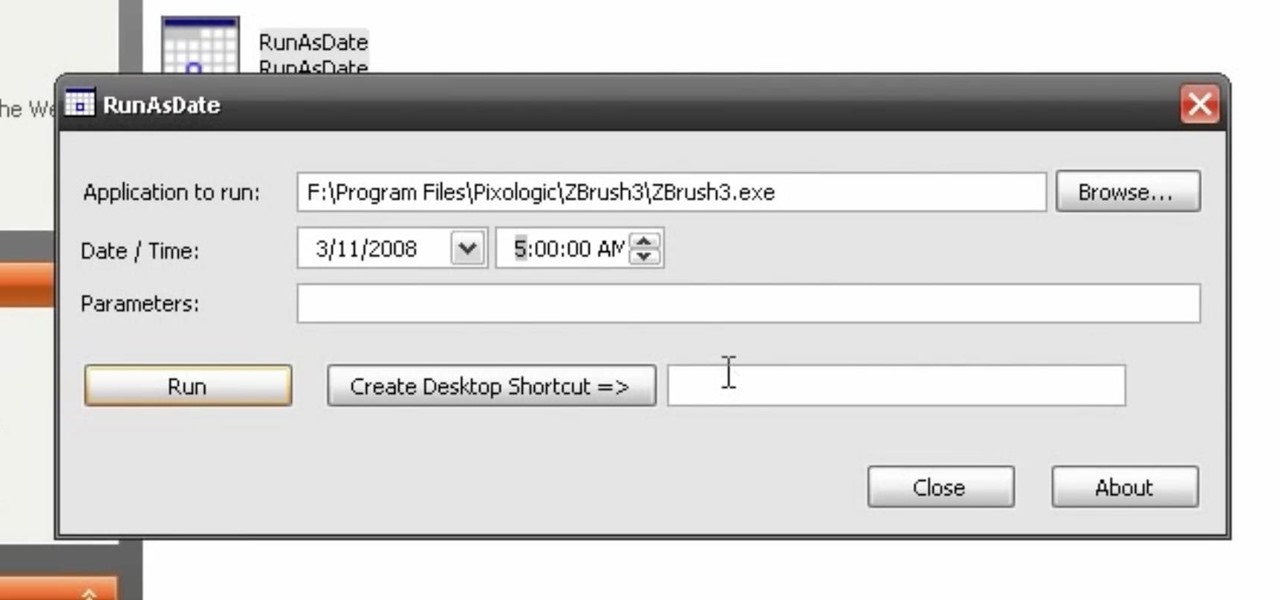
With this video tutorial, you'll learn how to hack demo versions of applications such that they'll run indefinitely. You'll just need to modify the date and time on your computer. Learn how to use trials of programs without them ever expiring instead of buying the real thing with the hack outlined in this how-to video.

Ever wonder how a tree gets water all the way up to the top? Ever thought about how a stream of air can hold a ping pong ball in place? This simple how-to shows you a few experiments to try with air and water.

Hitting up Tao in Vegas to celebrate the New Year? How about attending your super trendy friend's Christmas Eve party in New York? If you're destined for glitzy occasions, then it only makes sense that you should be dressed to the nines and look the part.

Need an outrageous and beautiful look for Halloween or attending one of Ke$ha's concerts soon? Then you'll definitely need to amp up your makeup game with lots of color and a Claire's store worth of glitter.

Smoky eyes are all the same, right? Wrong. While it's true that 99.9% of smoky eyes consist of some form of smoked out black, brown, silver, and sometimes purple, you can make your smoky eye interesting by adding an unexpected pop of color.

If you've ever suffered from acne you've probably also suffered from choosing an acne product that actually works. Some cleansers and moisturizers are too drying, others are harsh and stinging, and some feel good on skin but just don't work. But if you've ever stumbled upon tea tree oil, then you know that this natural oil both moisturizes and helps relieve acne with no unpleasant side effects.

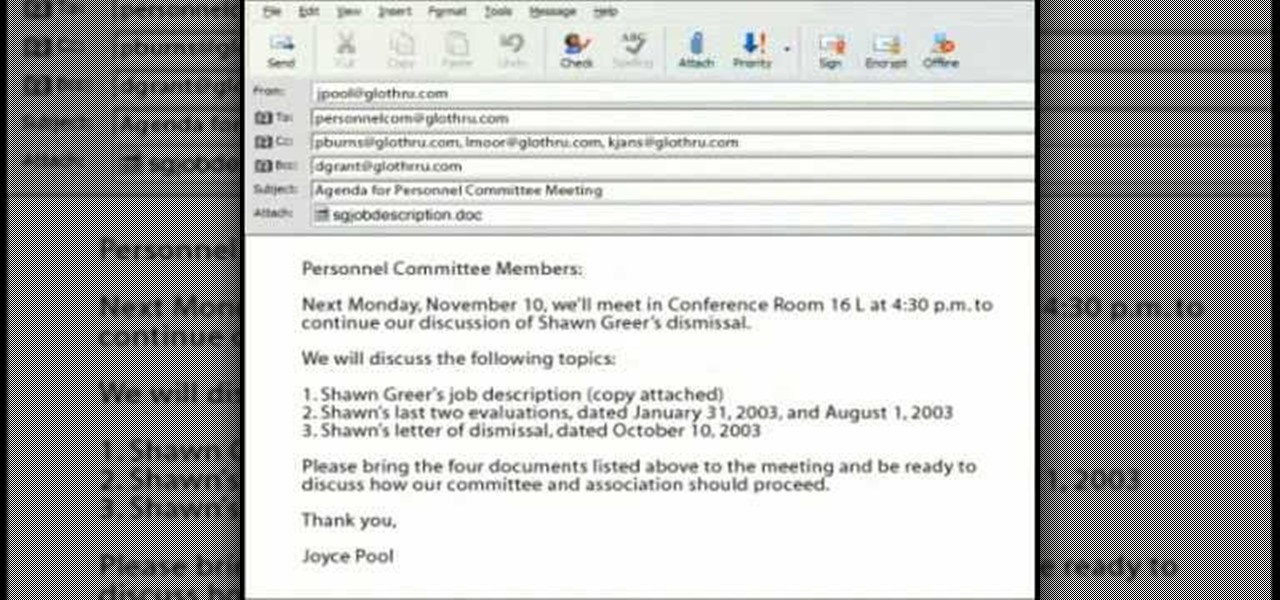
Now, more than ever, many companies rely on using emails to send bits of information around faster than normal. Not only does it save paper, but allows work to get done faster than it ever has. But, if you don't know how to write a proper business email, it can be tricky. That's why this tutorial will show you how to write them so you don't have to worry about a lack of professionalism. Enjoy!

Most of the home wireless networks are not set up by professionals and hence they might lack in security features. People just set up the wireless networks by connecting the devices and powering them up and never care to apply security settings to the network. This may result in your wireless network being compromised by unwanted external entities. How ever you can do a web based configuration settings and secure your wireless network by password protecting it. This settings differ from the m...

This video teaches you to use a flat iron to make gorgeous curls in your hair. The video shows the benefits of using a flat iron as opposed to using a curling iron. She takes you step by step through the process of using a flat iron to make some of the best curls in your hair you have ever experienced. Everything you need to know about curling your hair with a flat iron can be found in this video. This technique make it simple to make the best curls you have ever seen and felt, yes felt! This...

Watch Princess Pinkcat as she shows you how to touch of the roots of your hair in a hurry. Have you ever been heading out the door when you realized your roots were showing? Have you ever been asked out at the last minute and left without time to dye your hair or touch up your roots? Here's a quick tip to help you take care of those roots in less than 2 minutes flat.

There are good magic tricks, and there are bad magic tricks. The host of this video tutorial might not be the most skilled magician around, but he's a pretty good judge of card tricks. Check out how to perform the best math card trick ever! With just a little math and a little magic, your spectators will be astonished. See the reveal and explanation. This card counting trick will always work and it will amaze your best friends.

While the big names in augmented reality demonstrated the breadth of opportunities in the industry's landscape this week, one new startup showed off what is possible further in the future.

As demonstrated by holographic experiences for the Microsoft HoloLens and the Magic Leap One, volumetric video capture is a key component of enabling the more realistic augmented reality experiences of the future.

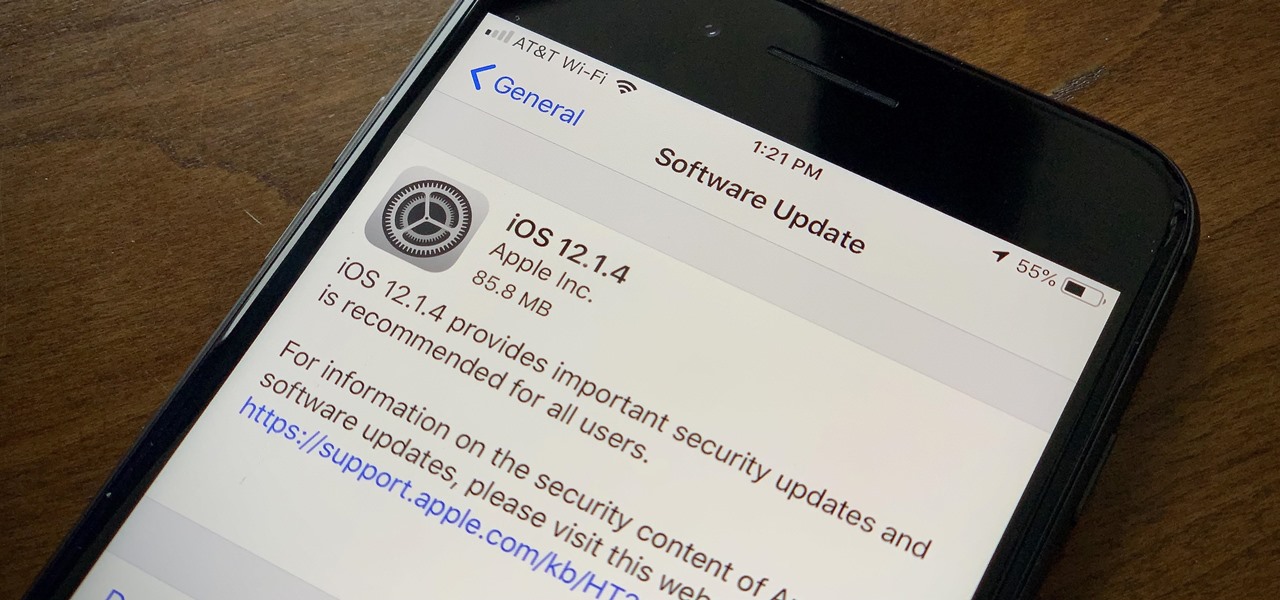
Apple found itself in serious trouble last week when a teenager discovered a critical FaceTime bug that threatened the security of nearly every iPhone user. The bug enabled a user using Group FaceTime to access either the microphone or the camera of a recipient before they answered the call. According to Apple, the issues have been fixed in an iOS 12.1.4 update released Thursday, Feb. 7.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds.

Getting root is considered the Holy Grail in the world of Linux exploitation. Much like SYSTEM on Windows, the root account provides full administrative access to the operating system. Sometimes even a successful exploit will only give a low-level shell; In that case, a technique called privilege escalation can be used to gain access to more powerful accounts and completely own the system.

One of the most critical bugs to come out in the last five years was Shellshock, a vulnerability which allows attackers to execute arbitrary code via the Unix Bash shell remotely. This vulnerability has been around for a while now, but due to the ubiquity of Unix machines connected to the web, Shellshock is still a very real threat, especially for unpatched systems.

Transparent display maker Lumus has reached a deal to license its augmented reality optical engine models to Quanta Computers for mass production of displays for consumer smartglasses.

A potentially groundbreaking new app targeting retail financial services hopes to bring augmented reality to your local bank and credit union.

What do Leo Tolstoy (writer), Beethoven (composer), Paul Gaugin (artist), and Adolf Hitler (politician) have in common? They are all considered to have suffered from the sexually transmitted disease syphilis.

Here is the World's Funniest Cat video!

Check out one of the greatest pranks ever, by professional pranksters.

There's absolutely nothing better than seeing the look of pure and utter shock on someone's face, and that is why I absolutely love this. It is by far one of the best pranks ever, and one of the best videos that I've seen in a while. Seriously. If you've ever used the drive-thru, you've gotta watch this.

This is quite possibly the most disturbing Halloween costume ever. Seriously. It nailed creepy down to a tee. A friend of Redditor YouHadMeAtBacon did this gory unzipped zipper face makeup, and it's by far the best I've ever seen. Unzipped Zipperfaces in Action

Learn how to play "She's Everything" by Brad Paisley, an acoustic guitar tutorial. Follow along with this demonstration, lyrics here:

Learn how to play "Don't Forget" by Demi Lovato, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Maybe you're tired of receiving annoying messages from apps or people on Facebook? Why not block them so you don't have to deal with them ever again? Take a look at this guide for information on how to block online games and apps on Facebook from sending you notifications, requests, or other information. You can even stop people on Facebook from sending you event notifications or posting on your page by blocking them too.

If you're a Little Monster, than surely you've seen the single cover art for Lady Gaga's new hit "Born This Way". On the cover, she looks as crazy as ever, and in this makeup tutorial, you'll learn how to mimic the look, right up to the protruding horns. Surely, this is a look for the stage and not one you're likely to wear outside on a normal day—but it's fun to play around with and perfect—Gaga-style!

Are you a fan or Star Trek or Star Wars? Have you ever imagined flying on a G6 (thanks in no small part to Far East Movement)? Then this origami spaceship project is perfect for you.