How To: Use Call of Duty 4 cracked servers
How to Use COD4 Cracked Servers.


How to Use COD4 Cracked Servers.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.
Everyone knows how rough it can be to wait around for a GM while playing WoW. A World of Warcraft Game Master can be fairly busy during peak hours, and you may not want to wait around that long. Take a look at this legitimate trick to lowering a GM wait time to a few minutes.
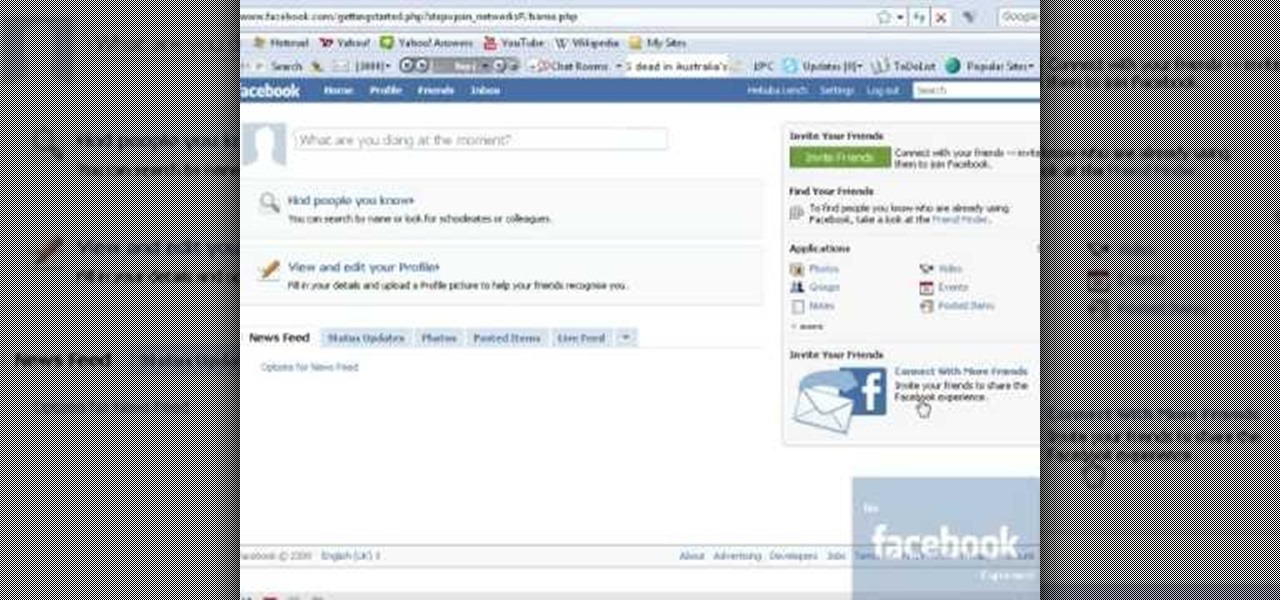
In this video, we learn how to change your name on Facebook. First, go to Facebook and log into your account. Once you are on here, click on the settings button. Now, find where it says "name" and click "change". Once you change this, enter in the name that you want to show and then choose the name that you want to display. Once you are finished, click "change name" and then you will have to certify that this is your real legitimate name. Once you do this, your page will refresh and your new ...

Are you secure when downloading security software? Sounds like quite the conundrum, but CNET has answers. See if you're really secure when getting that software, and telling the difference between a rogue antivirus website versus a legit site. See how not to get scammed and destroyed!

Looking for fast cash with no questions asked? There are legitimate ways to get it, if you're willing to pay the consequences. You will need a credit card with unused credit, a tax refund, a car, a small loan company, a signature loan company, or a payday loan. Watch this video tutorial and learn how to get money quickly by finding a loan shark.

This is the first installment in a new series that I am calling "Hacker Hurdles." These are things, methods, techniques that make our job as hackers more challenging and difficult. Don't misunderstand me, these items don't make our task impossible, but rather more challenging and, therefore, more gratifying when we are successful. One of the most important new hurdles for hackers is DEP and ASLR. Data Execution Prevention (DEP) and Address Space Layout Randomization (ASLR) are designed to pre...

Researchers at the University of California, Riverside and the University of Michigan announced recently that they have developed a hack that works 92% of the time on Google's Gmail system on Android, as well as with the H&R Block app.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Have you ever found yourself calling up a company, only to be denied due to not calling from the number listed on your account? Thanks to a website called Spoofcard, this is no longer an issue! SpoofCard let's you spoof the number you are calling from, as well as modify your voice (Male -> Female or vice versa). Best of all, it all looks completely legitimate.

Next time you don't want to make your bed, dry the dishes or clean the house there's no need to feel guilty. You may be doing yourself a favor. There are legitimate scientific reasons why some chores aren't always the best health choice.

Ready to start your journey into the world of Magic: The Gathering? If so, there's no better place to start than with this five part tutorial. This tutorial comes straight from the pros at Magic and teaches you everything you will need to know about the Multiverse. So, go get some cards and get ready to dive head first into the Magic universe.
Spyware are programs that infect your system and / or at the same time collect personal information without your consent.
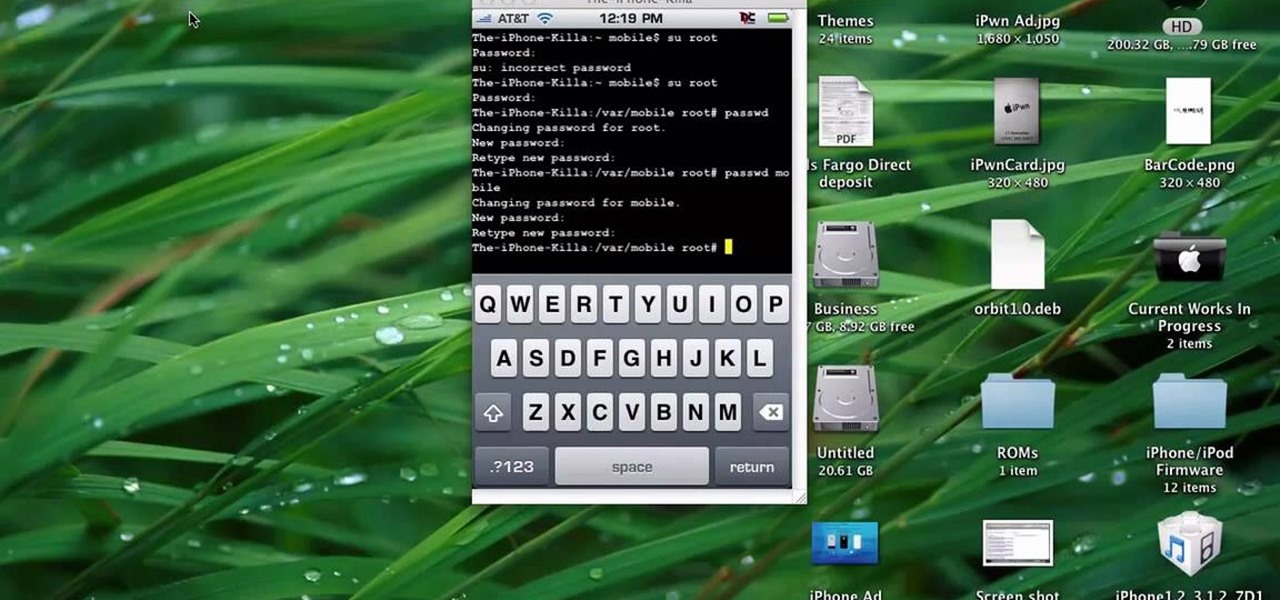
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.
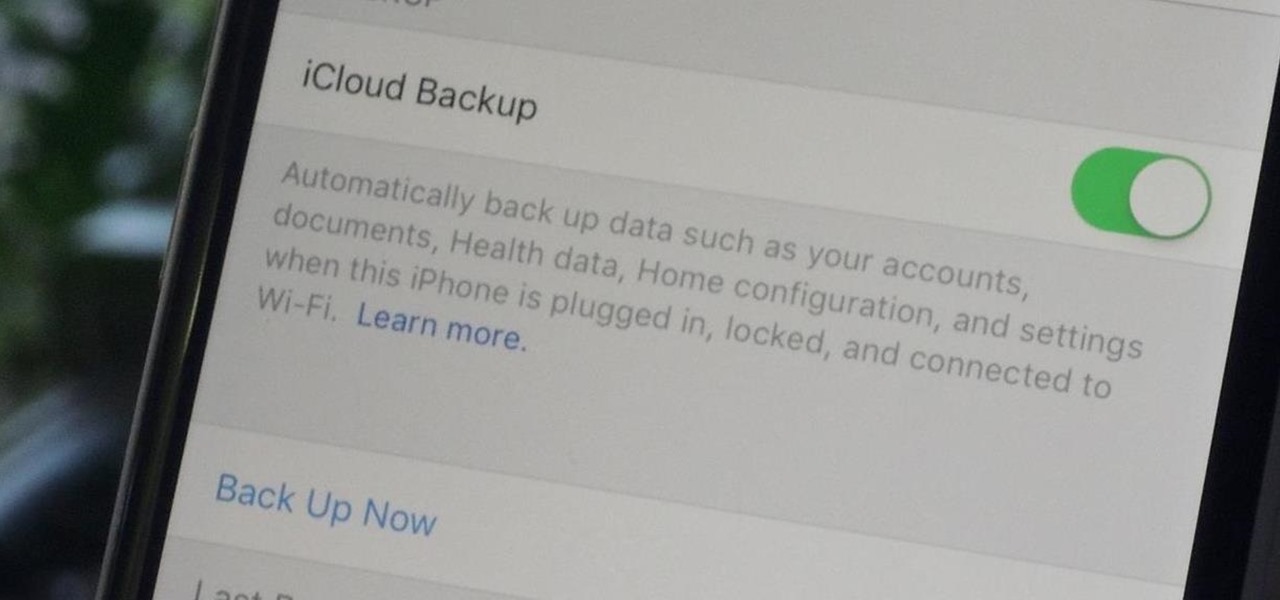
Enabled from the moment you first booted up your device, there's a feature deep in the iPhone's settings that automatically backs up your device in the background. As long as you're connected to Wi-Fi and a power source and your screen is locked, your photos, text messages, apps, and everything in-between gets safely stored to your iCloud account.

The Nokia N900 smartphone suffers from a lack of quality games due to Nokia's restrictive OS, but fortunately you can get WebOS games from the Palm Pre loaded onto it pretty easily by following the steps outlined in this video tutorial.
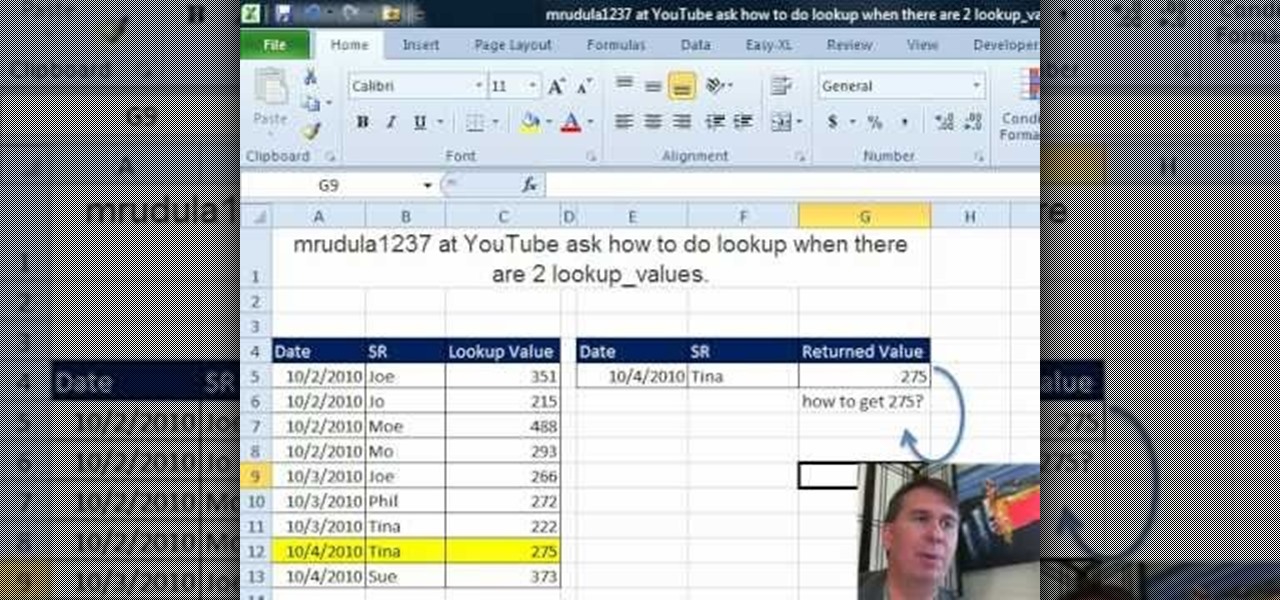
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun and Mr. Excel, the 52nd installment in their joint series of digital spreadsheet magic tricks, you'll learn how to use the INDEX function to turn a Ctrl + Shift + Enter array formula into just an Enter array formula. Avoid Ctrl + Shift + Enter by using the INDEX function and a blank as the row argument.

In this tutorial, we learn how to make your first graph in Microsoft Excel. First, open a new graph and enter in your data. Click and drag down from the original date you enter to have the other dates automatically entered in. Enter the rest of your information, then highlight all the data. Go to the menu and click "insert", then "chart". Now, go through the chart wizard to select what kind of chart you want to make. When you are finished entering all your preferences, change your values so t...
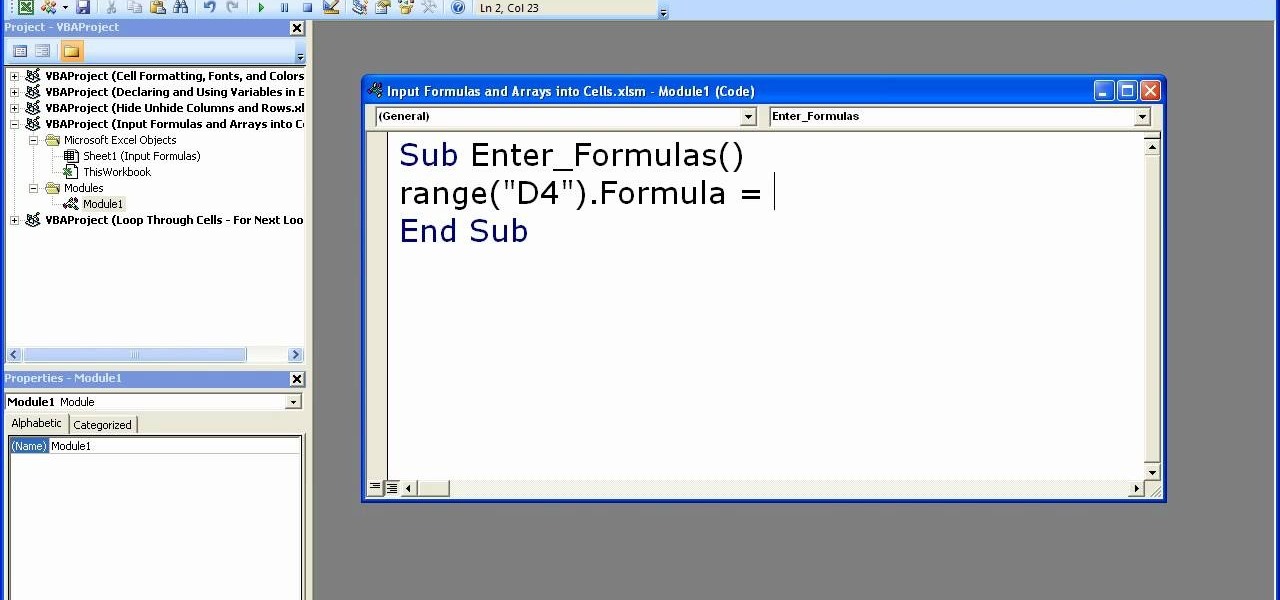
In order to enter formulas in Excels with a macro, you will need to open your spreadsheet. Formulas are used to do calculations. Go to the field, where you want to enter a formula. Type in the formula. Then, highlight the formula. Press Control + C to copy the formula. Next, delete the contents of the cell. Press Alt + F11.

In this video, learn how to enter mail-in sweepstakes, what supplies you need, tricks and tips for filling out entries, how to organize your entries, and how to not get disqualified. This clip will walk you through the entire process so that you can increase your chances of winning and getting one of those oversized checks delivered to your door. So, follow along and enter those contests the right way to maximize your opportunities to win.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

This video tutorial is in the Education category which will show you how to calculate standard deviation with TI graphing calculator. First you got to enter the data in to the calculator. Go to stat and click on enter. This will edit a list. Now you type in these numbers: 50, 20, 33, 40 and 55. Then press stat and click on enter. This will bring up the 1-var stats page. Press the "2nd" button and L1, because all our data is in L1. Click on enter and you will get all the data that you will nee...

In this video, we learn how to play "Enter Sandman" by Metallica on electric guitar. This will be ten riffs, the first will be E, B, G, D, A, and E. The second one will be E, B, G, D, A, and E. The same will follow with the rest of the riffs. Once you finish playing all of them separately, start to play the entire son all together until it becomes one song with no stops in it. After you reach the end of the song, you will have completed this and can move on to a more advanced one with more ch...

This tutorial will show you how to hide files on your computer using an image file. The first step is to get an image file and edit it with Microsoft Paint or Adobe Photoshop. The next step is to save the image file as a jpeg file. Now create a WinRaR archive file and copy the files that you want to hide in the archive. The next step is to open Command Prompt: Click the Start button and click Run. Now enter "cmd" and hit enter. Now just enter the same commands from the video and hit Enter. Fo...

In this tutorial, we learn how to set a passcode for your iPhone or iPod touch. First, go to your main menu and then find the "settings" button. Then, click on "general" and find "passcode lock". You will now be prompted to enter a passcode into your phone, then re-enter it. Now, you will be directed to a menu where you can decide how often you will have to enter your password, and if you want your password to be turned on or off. Now, when you turn on your phone you will be prompted to enter...
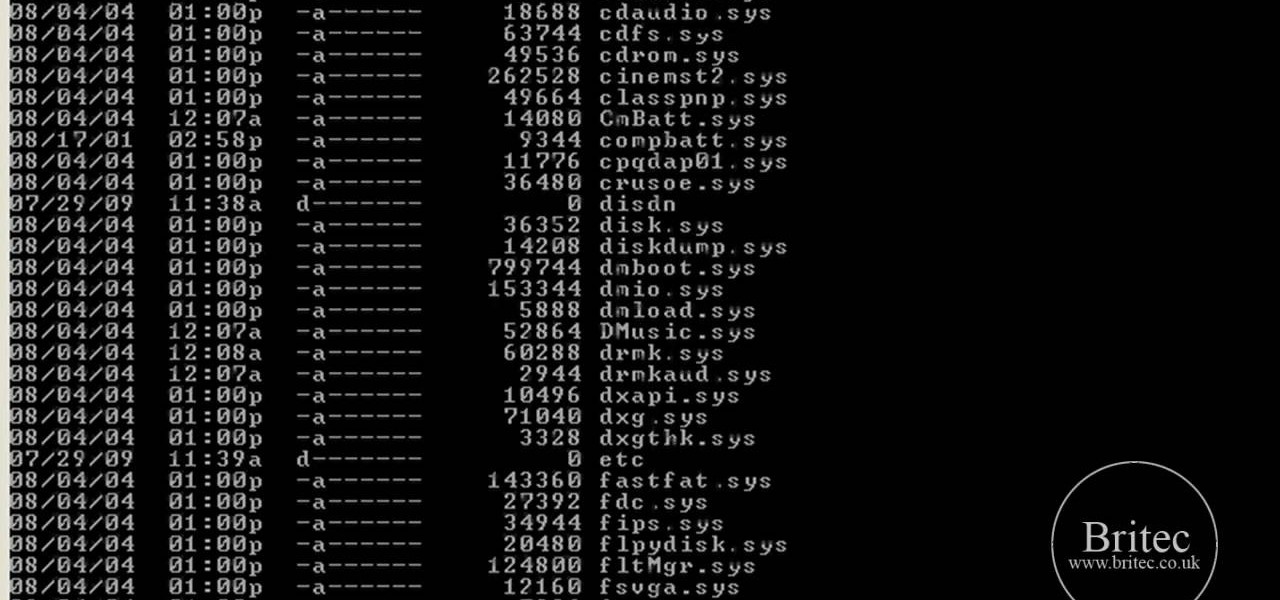
In this tutorial, learn how to fix a missing or corrupt error message "System32\Drivers\Ntfs.sys" Step 1:

'Enemies Among Us' is one of the longest, most involved quest in Dragon Age 2, and this walkthrough of it spans a whopping five videos. Stick with it, it's really goods stuff and great viewing even if you aren't stuck on this quest.

Looking for a guide on how to enter data into nonadjacent cells in MS Excel 2010? This clip will show you how it's done. Whether you're new to Microsoft's popular digital spreadsheet application or a seasoned professional looking to become better acquainted with the features and functions of Excel 2010, you're sure to benefit from this free video software lesson. Take a look.
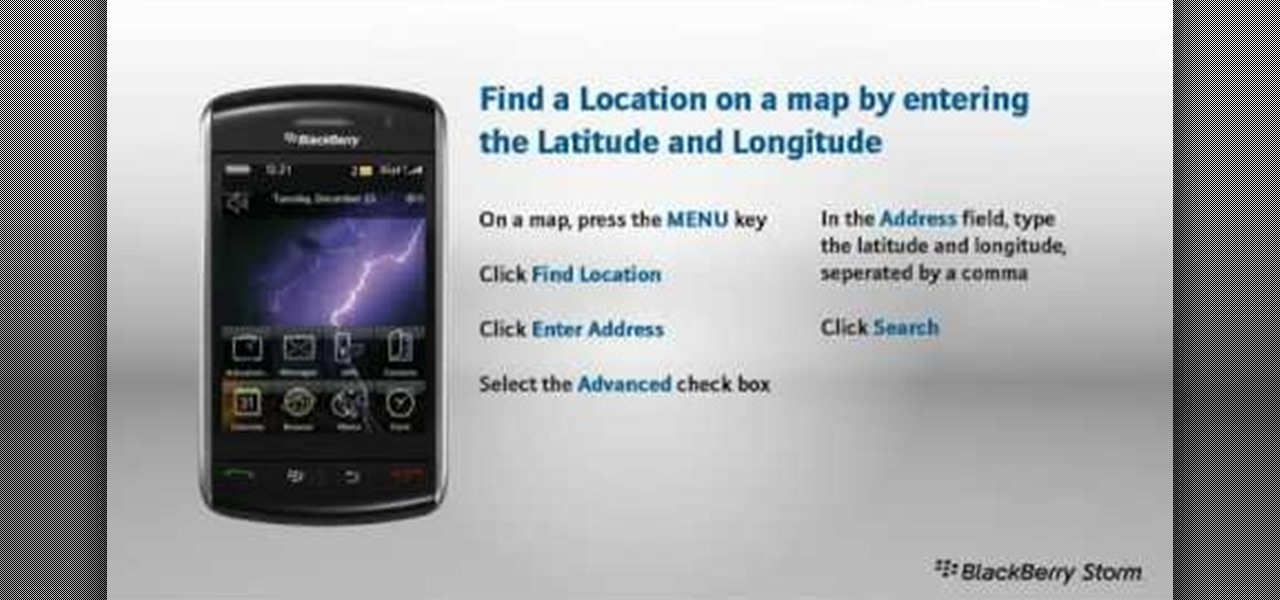
Learn how to find a location by entering its coordinates . This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.
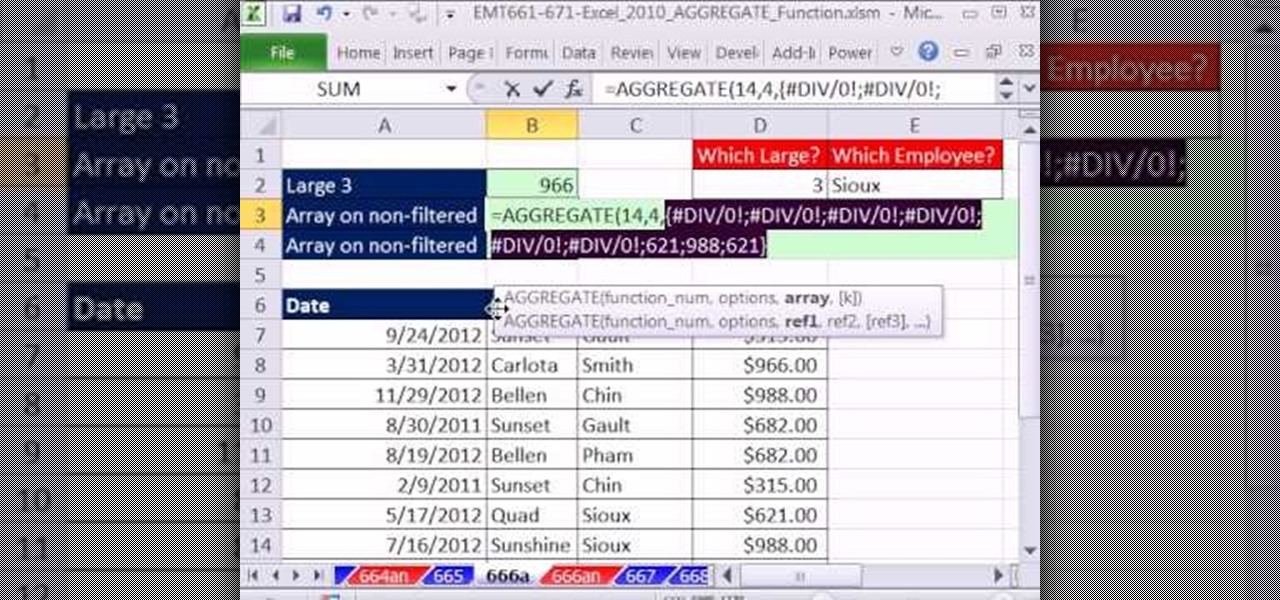
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 666th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the AGGREGATE function to avoid Ctrl + Shift + Enter for normal array formulas.
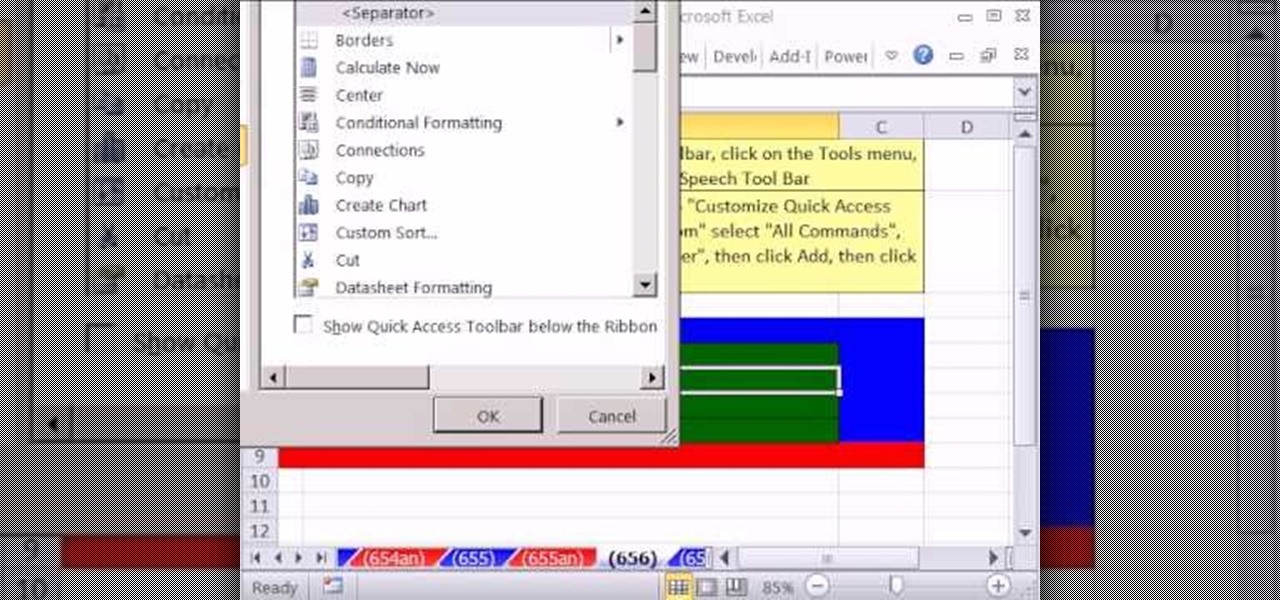
New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 656th installment in their series of digital spreadsheet magic tricks, you'll learn see how to use the Speak Cells on Enter function.
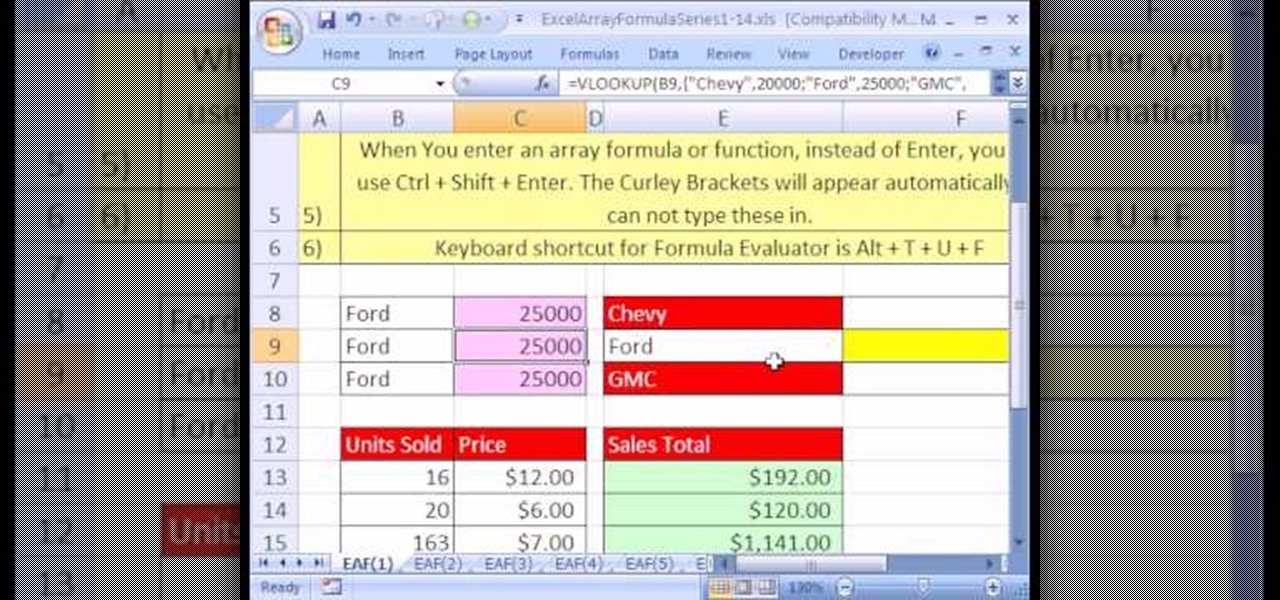
Looking for a primer on how to create and work with arrays in Microsoft Office Excel? You've come to the right place. In this free video tutorial from everyone's favorite MS Excel guru, YouTube's ExcelIsFun, the very first installment in his series of Excel array formula series, you'll learn how to create a basic array formula. Learn about the syntax, the Ctrl + Shift + Enter method of formula entry and the curly brackets that get entered automatically by Excel.

New to Microsoft Excel? Looking for a tip? How about a tip so mind-blowingly useful as to qualify as a magic trick? You're in luck. In this MS Excel tutorial from ExcelIsFun, the 208th installment in their series of digital spreadsheet magic tricks, you'll learn how to use the keyboard ctrl-enter keyboard shortcuts to speed up common tasks in Microsoft Excel.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.
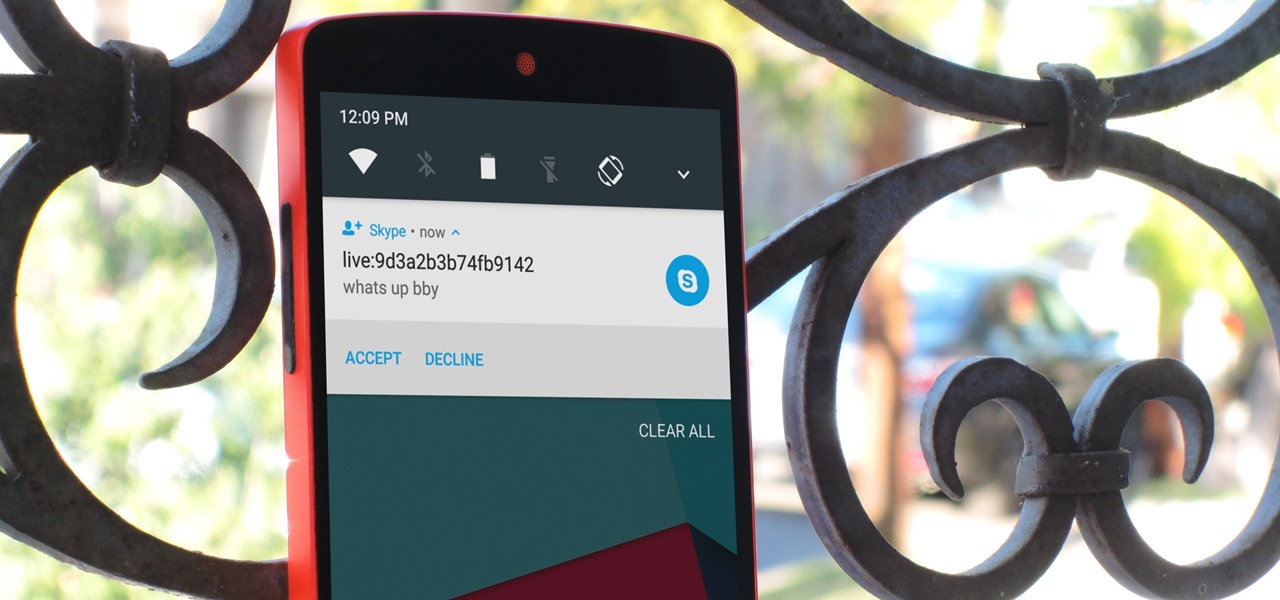
Skype is one of the most popular messaging and video chat services for a good reason—it's packed to the brim with tons of cool features. But one bit of functionality that Microsoft left out is the ability to block friend requests from people that aren't in your contacts, which can lead to a lot of unwanted notifications from spammers and bots.

This past weekend, one of the most notorious hacker organizations in the world, Hacking Team, was hacked by some unknown organization. The Hacking Team is an Italian company that sells it software and services to companies and governments (yes, my rookie hackers, there are legitimate companies who sell their services to governments—Vupen, being one of the most famous and lucrative).

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

The video shows you how to calculate capital budgeting with a Texas Instruments BA2+ financial calculator. Capital budgeting will help you determine cash flows for given investments for a certain number of years in the future, thus helping you determine if the investment is worthwhile. The buttons you will use are the CF (cashflows) button, the NPV (net present value) button, and the IRR (internal rate of return) button. The video uses the example of a $10,000 investment that will return $5,0...
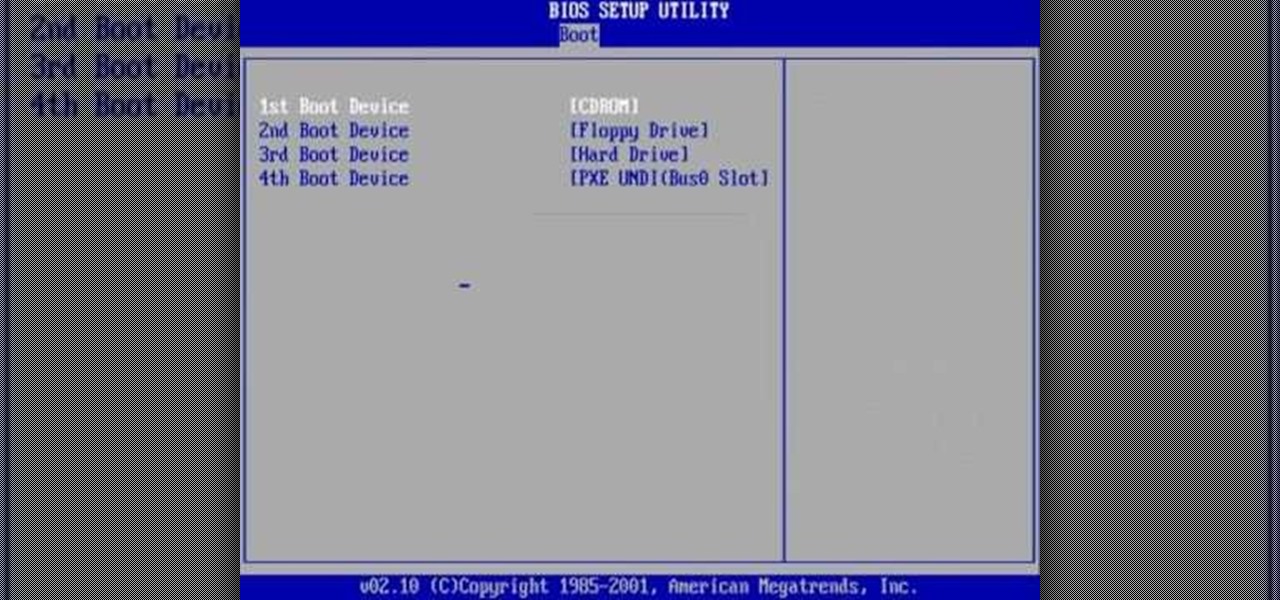
The video shows users how to change the boot sequence in a computer with an older AMI (American Megatrends, Inc.) BIOS to boot from the CD/DVD drive. This is required, for instance, if you need to reinstall an operating system, or fix a corrupted windows installation by running Windows Setup from the installation CD. Users should first enter the BIOS setup by pressing the delete key when prompted shortly after powering the computer on. Once the Bios Setup screen has loaded, users may navigate...