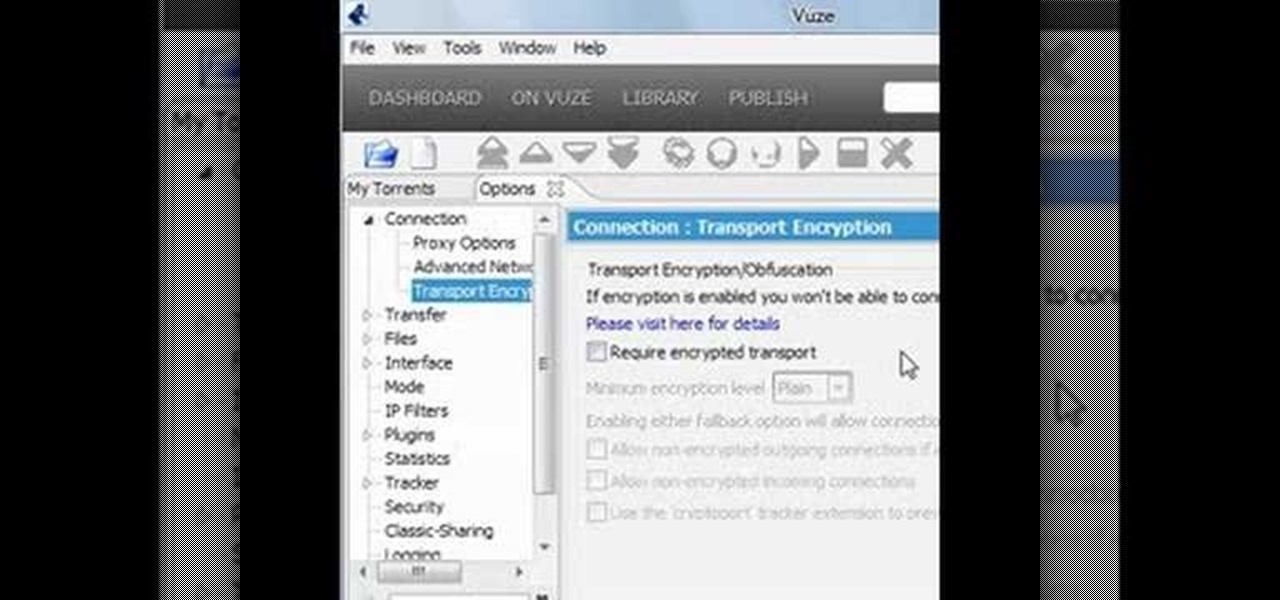
Torrents are a wonderful technology to share your files over the internet. If the data that you are sharing is confidential you may need to encrypt these files before sharing. To encrypt torrents in Azereus, go to tools and select options. From the left hand side menu select the connection option. Select the 'Transport Encryption' option from the connection sub menu. This section is intended for intermediate mode or higher and it is not available in beginner mode. So go to mode and select the...
This tutorial series shows you how to put up an Adobe Air Flex 3 Encryption System. One of the weak points of Adobe AIR and Flex is there is no encryption system built in, making your data and applications vulnerable. But that's ok, because this tutorial will show you how to remedy the problem by adding an AES encryption system.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.
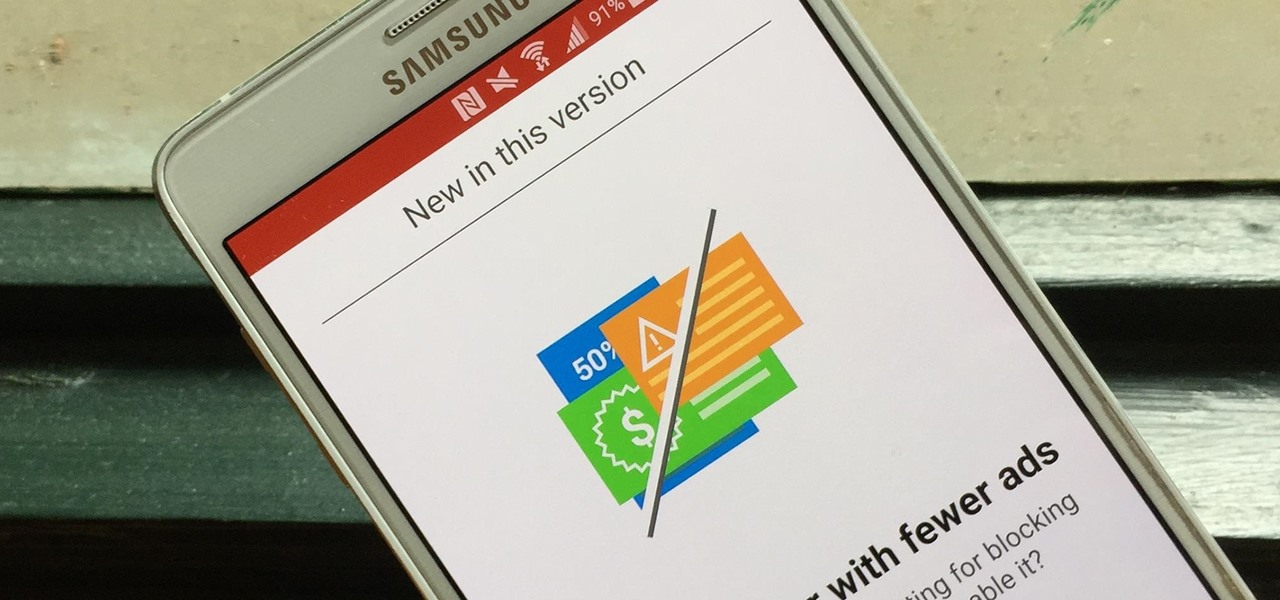
Opera's web browser for Android, Opera Mini, now comes with integrated ad-blocking technology for a less cluttered browsing experience. More importantly, it decreases the amount of data being loaded, which Opera claims increases webpage loading times by 40 percent. This is in addition to the 90 percent data reduction from Opera Mini's compression technology.

Simon Solotko outlines the steps necessary to get a desktop PC up and running from scratch using AMD Dragon platform technology. Fragon technology is a combination of AMD Phenom II processors, ATI Radeon HD graphics and AMD 7-Series chipsets. This technology allows you to build incredibly powerful PCs for multimedia entertainment, gaming and advanced multitasking.

HTPC. It stands for Home Theater PC. Some refer to it as simply a Media Center. But no matter what you call it, you're going to learn how to build one today. Why would you want to do that? Because one of the main advantages of creating your own home theater system is that you are control, not only of the cost, but the features and functions, as well.

In a letter dated February 16th, Apple CEO Tim Cook responded to the FBI's demand that Apple create a "backdoor" to bypass the encryption on an iPhone used by one of the perpetrators of last year's terrorist attack in San Bernardino, CA. Cook began the letter by stating that Apple has "no sympathy for terrorists" and has cooperated in giving the FBI all of the information that it has available.

Here is an educational video for ART (Advanced Robotic Technology) Plasma customers. The HDP Plasma SX Profile Cutter is designed for heavy duty manufacturing environments where power, precision, speed, quality low cost, productivity, and durability are demanded by business owners. See in these sixteen videos how it works, from the inside out, and another video on what it actually is.

TrueCrypt is a free application that lets you encrypt designated programs on your Ubuntu system to prevent unwanted access. Provided you select a strong password, intruders will not be able to open your personal files and documents. This instructional video walks you through the process of installing TrueCrypt on your Ubuntu operated machine and demonstrates an example on how to create an encrypted volume within a select partition.

Watch this video to learn how to configure and use the new Samsung TruDirect DVD burning technology

For years, Skype has been synonymous with video calling and messaging. However, as the industry moved toward encryption and privacy, Skype usage was discouraged by experts due to its murky encryption. To combat this, Skype has introduced true end-to-end encryption.

Welcome back, my rookie hackers! "How can I travel and communicate over the Internet without being tracked or spied on by anyone?" It's a question many Null Byteans have asked me, so I have decided to write a comprehensive article addressing this issue.

Learn about the history and technology of batteries in this informative video, and learn how to make your own voltaic cells at home, along with other scientific experiments. Jeri Ellsworth demonstrates how and provides several informative facts about the history and technology about the battery.

The Mac OS's Disc Utility allows for the encryption of files. To open Disc Utility click on the magnifying glass (spot light) up in the top right hand corner, and search for Disc Utility. Click on the first result in the list. Once Disc Utility is open, click on "create a new image" in the top tool bar. A new window will drop down, where you choose what you want to save the new image as. Give it a name, and choose the size you want it to be. Moving down, choose the encryption you want to use ...

New updates to the journaling app Day One include more security for journal writers' data. For example, users can now enable end-to-end encryption. The encryption does not happen automatically; however, users must go to Settings — within Journals — then select each journal they want encrypted.

WhatsApp sneakily made some security changes to iCloud backups without your knowledge, ladies and gents. Not that strengthening security is a bad thing, but still!

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Whether you're new to Adobe Photoshop or a seasoned graphic design professional after a general overview of CS5's most vital new features, you're sure to be well served by this (17-minute) official video tutorial from the folks at Adobe TV. In it, you'll learn how to do each of the following: realistically blend colors on canvas with the new Mixer Brush; create superior composites for print or web layouts with new technology that makes it easy to select even the trickiest image elements, like...

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

It may sound like deja vu, but neural interface startup CTRL-labs has closed a $28 million funding round led by GV, Google's funding arm, for technology that reads user's nerve signals to interpret hand gestures.

In this tutorial I will be explaining the purpose of unique encryption/decryption scripts ( I will be referring to these at "UEDS" for this tutorial). Then, I will show you how to make one. Finally I will talk about the downsides to the method I use. I will also provide links explaining the concepts and algorithms used in encryption to anyone who wants to see what is going on under the hood.

Herbie the Mousebot is a very quick, easy-to-build, light-chasing robot kit, perfect for beginners. This little robot is so quick, you have to run to keep up with him! This is from make magazine.

The Federal Communications Commission (FCC) has cleared a path for Google to move forward with hand-tracking technology that could pose a major threat to Leap Motion.

Waveguide manufacturer DigiLens has closed a $25 million Series C round of funding from automotive technology company Continental, which uses the technology in its heads up displays.

Two companies behind a number of augmented reality devices have joined forces to develop a 3D depth-sensing camera system that will facilitate computer vision capabilities for augmented/virtual reality experiences and more.

If you have personal information stored on a Kindle Fire tablet, be warned that Amazon has removed encryption support for Fire OS 5. So if you have stuff on these devices...maybe a risque book, or private notes, or pictures you'd rather not let out to the world, now would be the time to remove them. And unless Amazon changes its mind and re-enables encryption, don't use your device for anything personal, as anyone who gets a hold of it will be able to gain access to everything on it.

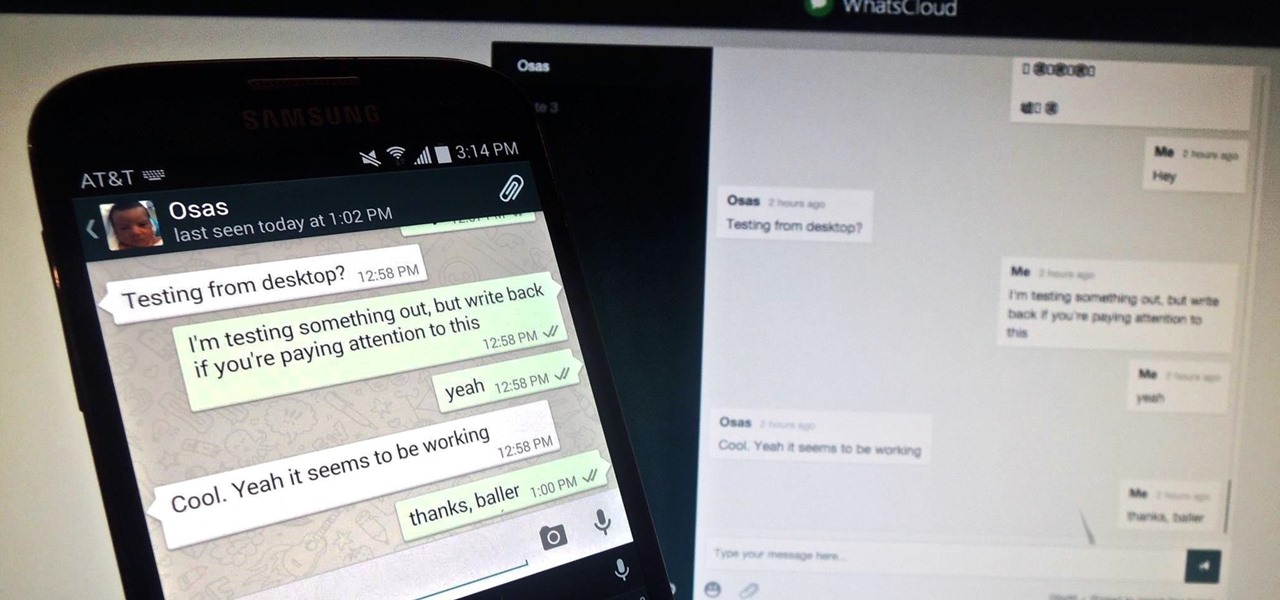
Pretty much my only gripe with computer-side messaging clients like Mighty Text is that they don't allow you to send and receive messages shared through WhatsApp, the popular third-party messaging application, which was purchased earlier this year for $19 billion by Facebook.

Does someone keep drinking part of water bottle and leaving them around your house or office, taunting you with their wastefulness? Thanks to forensic technology, it is possible to catch the culprit with easy household materials. This video will show you how to use super glue to lift fingerprints off of a water bottle where normal fingerprint-lifting technology would not be sufficient. Plus, you get to use a heat gun! Always fun.

This video tutorial is in the Computers & Programming category which will show you how to hack a wireless network with WEP encryption. This video is intended only as a means of testing the security of your own network. Go to Backtrack Linux, download the backtrack4 and burn it to a DVD. Now put it in a computer with a wireless card and restart the computer so that it boots to the DVD. When it boots up, type "startx" to start the interface. Bring up the command prompt and type in "/etc/init.d/...

Do you worry that if your PC is stolen someone can copy all of your data? Then you should encrypt your hard drive and removable USB drives too. In this video tutorial, you'll see how Windows 7 has beefed up Bitlocker, its built-in encryption program, and learn how to use it. It's simple! So simple, in fact, that this home-computing how-to can present a complete, step-by-step overview of the process in just under two minutes of your time. For more information, including complete, step-by-step ...

NTFS? What is it? It stands for New Technology File System, but what does that mean? Well, it's the standard system for filing in Windows NT, including all later versions, up to the current Windows 7, but Mac users can take advantage of this file system, too. If you’re confused when it comes to your hard drive’s format, this guide will show you the way to get the most out of your system.

Encryption is the process of converting you data in to other obscure form so that no one can read it. Encryption can also be done using batch files. Batch files are scripting programs in windows which can be used to program small automatic operations. To do this open a notepad to write the batch program. First turn of the echo by inserting the command '@echo off'. Now write the rest of the program as shown in the video. Now save the image as a bat file. Now you can encrypt this batch file. To...

Check out this instructional science video that demonstrates how to detect disease using Nanotechnology. From the Oregon Museum of Science and Industry, this is a demonstration about a new technology that lets us detect diseases earlier and faster than we could before. Science has invented this new technology that can test for several diseases at the same time.

Thomas Maiorana of Boot y Amor gives tips on how to make your own shoes like the ones from craft magazine. DIY (do it yourself!) by hacking into the shoes!

It appears that the Project Aero 3D content development tool isn't the only augmented reality project that Adobe has in the works.

Influenced by the growth of augmented and virtual reality technology as well as 3D computer vision, Ericcson Ventures invested in Matterport, whose hardware and software help companies create AR/VR experiences.

A few years ago, the Hilton hotel group unrolled the Digital Key, a feature of the Hilton Honors app that allows you to unlock your hotel room with your smartphone.

A new survey shows that the majority of companies have an interest in using augmented reality, though adoption remains low. Meanwhile, two companies with support roles in the augmented reality industry are seeing positive financial results.

While two augmented reality companies were recently recognized for their innovative technologies, other companies have turned to augmented reality to innovate in their respective fields. Over the past week, use cases have ranged from selling snacks and video games to raising awareness for public health issues.

We are in a pretty major technology boom at the moment. One that will likely make the industrial revolution look tiny. And one of these technologies that are building up to lead the way is something called augmented reality.