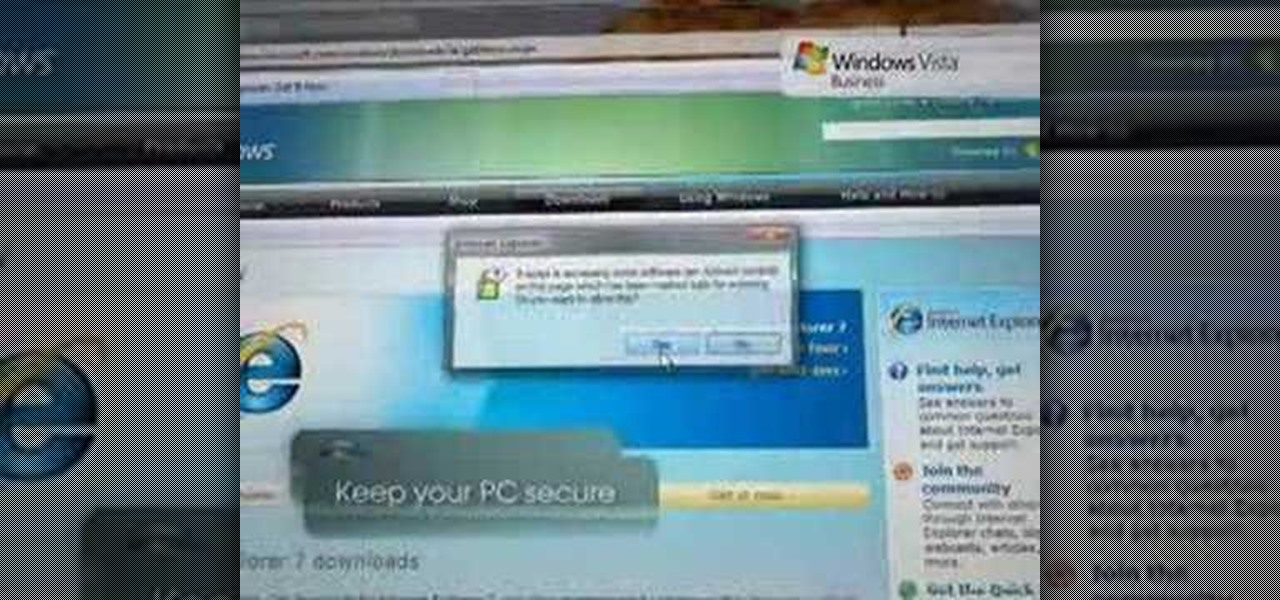
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

It seems like a new, dangerous Android exploit is uncovered every month or two. The latest headliners are NightMonkey and Chronos from the list of CIA hacks reported by Wikileaks, which have been billed as gaping security holes in the world's biggest mobile operating system.

Welcome back to a tutorial on malware. We'll be discovering a method to beef up our little trooper. Without further ado, let's jump right in!

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.

Hola my fellow hackers! I promised you the tutorials on setting up RAT's and Botnets, but before jumping into those, i want you to know about the precautionary measures and detection of RATs which might be on the system without your prior knowledge. Of course the Anti-virus do most of the job but there are some RATs which slips past the Anti-viruses (This is where Hacker's skill come into play).

Update 1: Evad3ers have released a statement to the jailbreak community, claiming that the safety and security of their users is the most important thing to them and that all speculations about malware being encoded into the jailbreak is simply not true. You can read the full letter over at Evasi0n's site.

Privacy has been a heated topic in recent months, with everyone now up in arms over unauthorized leaks and exposures. And guess what—tablet and smartphone users are just as vulnerable.

Welcome back my precious hackerians. Today i would like to promote an OS which i have been using for the past couple months. I'm not talking about Backtrack 5 or Kali Linux. Something even more promising:

One of the best things about the Nexus line of devices is the ease with which one can achieve root. Plug your phone into your PC, download a couple files, type a few commands, and you can be rooted within 30 minutes. No muss, no fuss, no carrier-locked bootloaders.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

Hi! Let me get started on this subject as it is a very "touchy" subject. We all want to "hack" these days, and that's logical. Te be real honest here, i was inspired once by the words someone from the Null byte community said. In the (near) future, wars will be ended by computers and not a nuclear missile. That's something i really do believe in. But let us take a defensive measure instead of the offensive one. Sure, Full frontal bryte forcing is an option, but when it'll come that far we'll ...

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

Just 94 days after the release of iOS 7, the team over at evasi0n have once again gifted us with their latest jailbreaking software for the newest version of iOS. The first iteration of evasi0n7 contained Chinese malware, but the subsequent release removed the malicious Chinese app store, so this evasi0n7 jailbreak should be just as safe as previous evasi0n jailbreaks were for iOS 6.

If you ever wondered how you could make your internet web browsing faster, then this video will give you a crucial tip. The loading speed of web pages and web sites is greatly influenced by the type of web browser you are using. The narrator in this video suggests that you search for other types of web browsers besides Internet Explorer or AOL. The main web browser that is advocated by narrator in this video is Firefox. He explains how Firefox is able to load pages faster than Internet Explor...

Just yesterday, Google announced that it is banning all apps that contain any form of lock screen ads. Today, they posted a list of the Best Apps of 2017 for the Play Store. Given the new policy of cracking down on apps with advertisements on the lock screen, you wouldn't expect to see one of those in the list of top apps. Unfortunately, that's exactly what happened — Google is promoting obvious adware in their list of best apps.

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Samsung's 2016 line of smartphones has a new update, at least for the devices on AT&T. The update brings the Galaxy S7 to version G930AUCS4BQL1 and the Galaxy S7 Edge to version G935AUCS4BQL1. Here's what's on the table.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

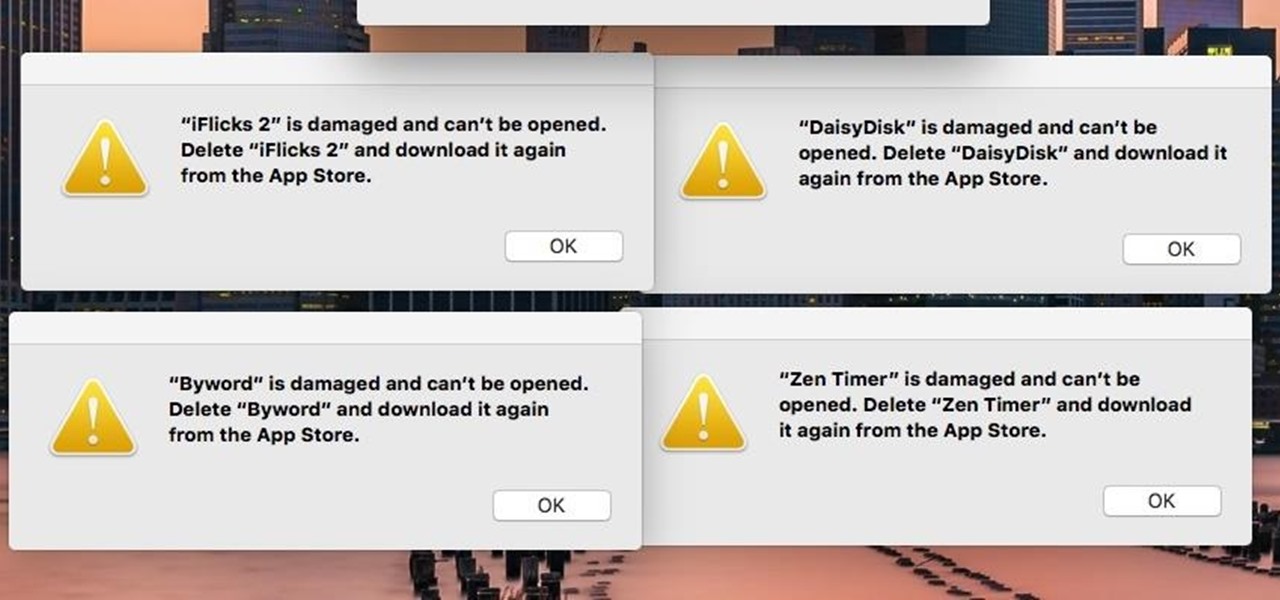
If you're seeing "damaged" apps on your Mac, you're not alone. A huge digital rights management blunder in Apple's Mac App Store on Wednesday, November 11th has rendered some apps unusable. When opening certain apps, the following message could be displayed:

I'm always looking for the best apps and services for my Android, and that means sticking strictly to the Google Play Store is a no-go. If you're like me and tend to install a lot of APKs (application files), you're probably tired of seeing the "Install" confirmation that always pops up.

UPDATE: A patch to fix the exploit has been released. Download it here.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

It's officially the holiday season, which means everyone will soon be traveling home to spend time with loved ones. And anyone who has any knowledge whatsoever of computers knows what else that means—family members left and right asking you to fix their various technical woes.

Welcome back, my budding hackers! One of the most time-consuming, but necessary, activities in hacking is reconnaissance. Before we can hack a system, we need to know what operating system it's running, what ports are open, what services are running, and hopefully, what applications are installed and running.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

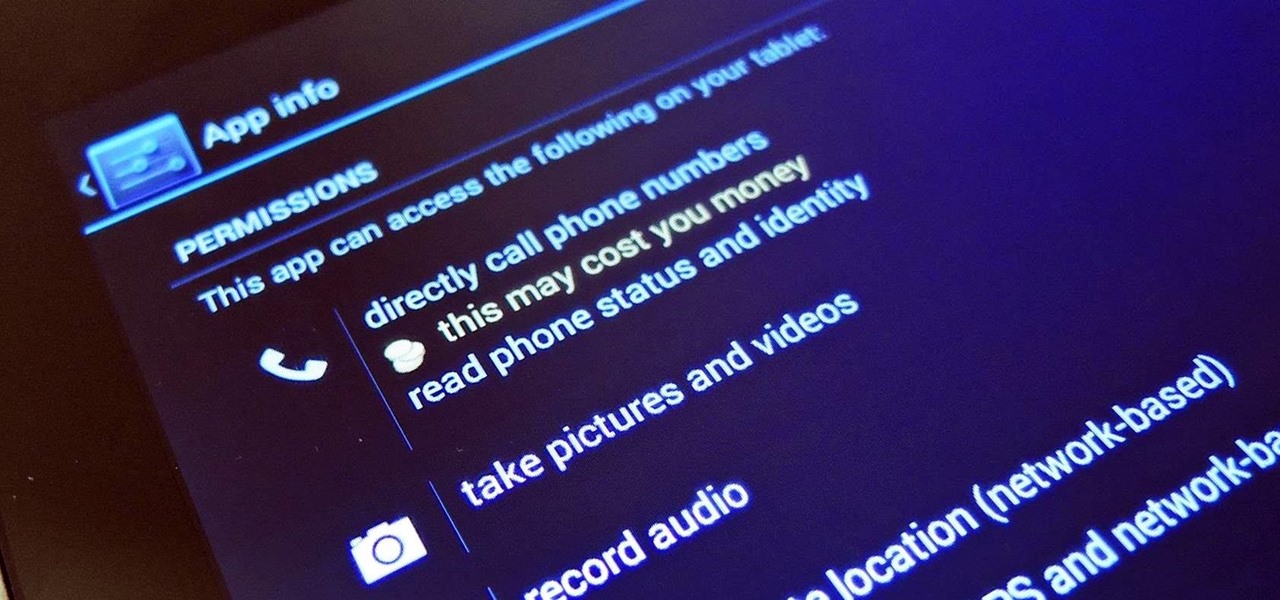
As of 2016, there are approximately 1.85 billion Android smartphones worldwide. This growing popularity has led to an increasing number hacks and cyber attacks against the OS. Unfortunately, Android users need more protection than what is offered by Google. The good thing is that there are a number of options available.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

The Cloud Security Alliance (CSA), a leading IT trade association, has published its first report on risks and recommendations for connected-vehicle security, ahead of when driverless cars are about to see volume production in the near future.

What's up guys? Welcome to a sort of general walkthrough on how one might approach a reversing and analysis on a crypted malware. This is by no means a universal technique so don't assume that this will occur in every scenario, it's more of a demonstration than anything really.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.