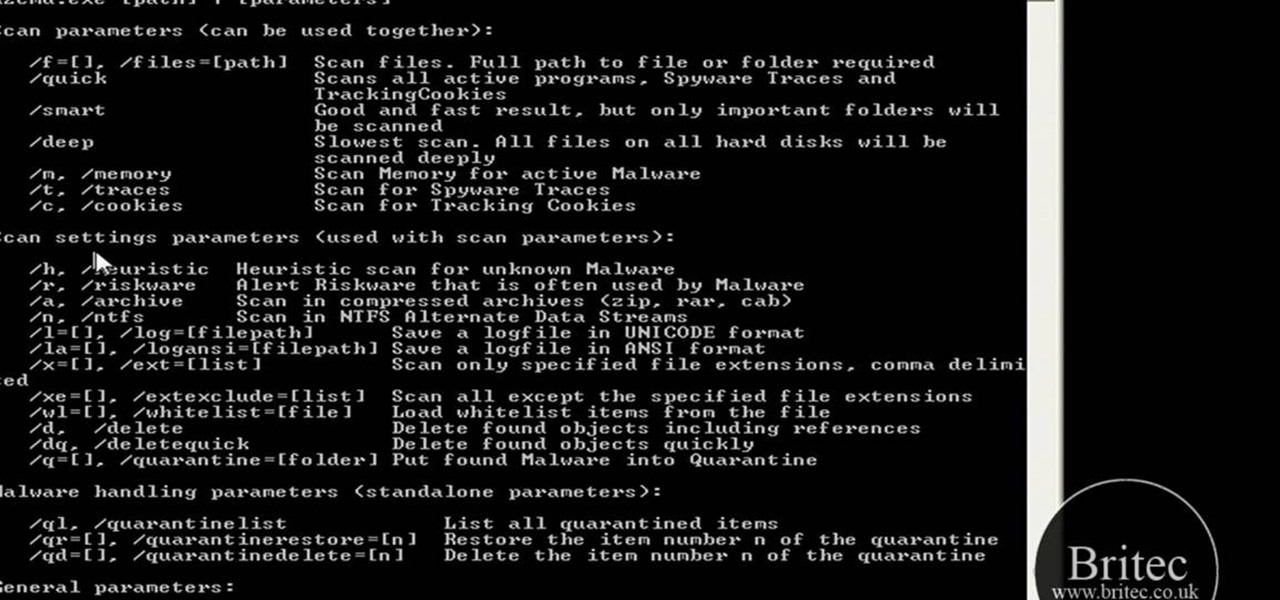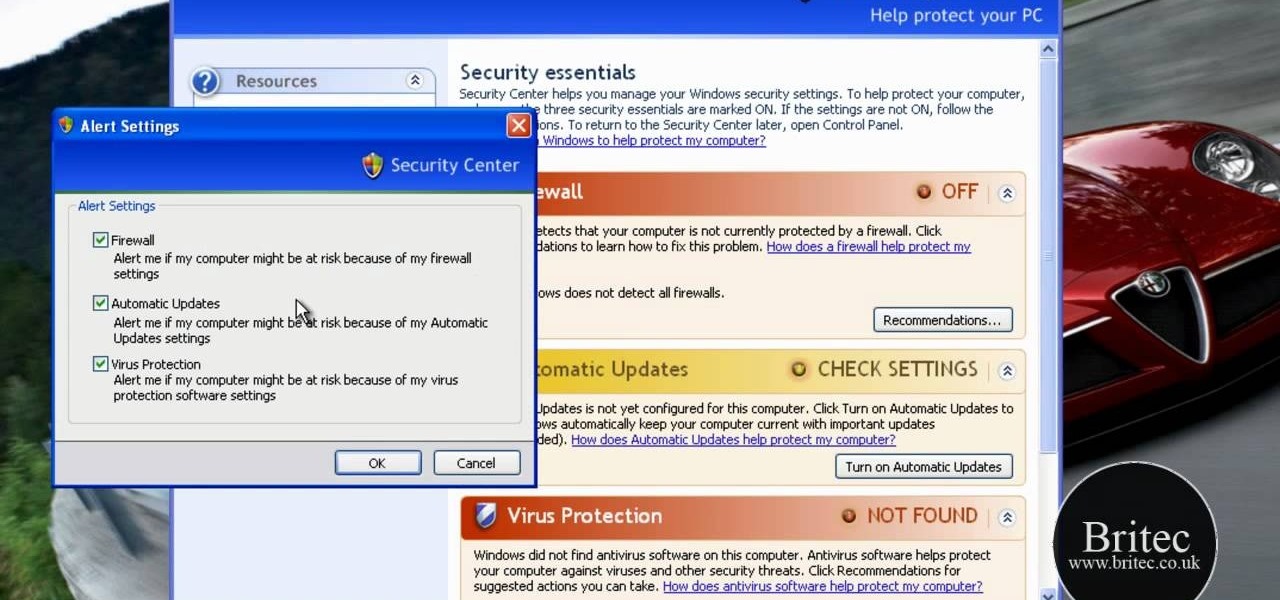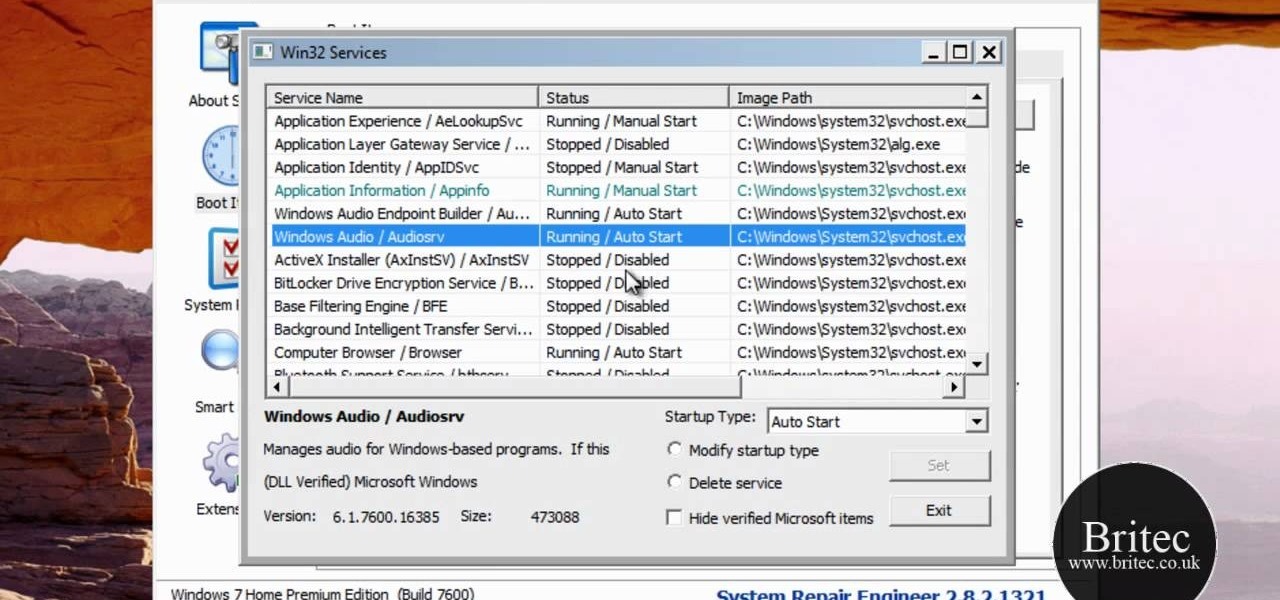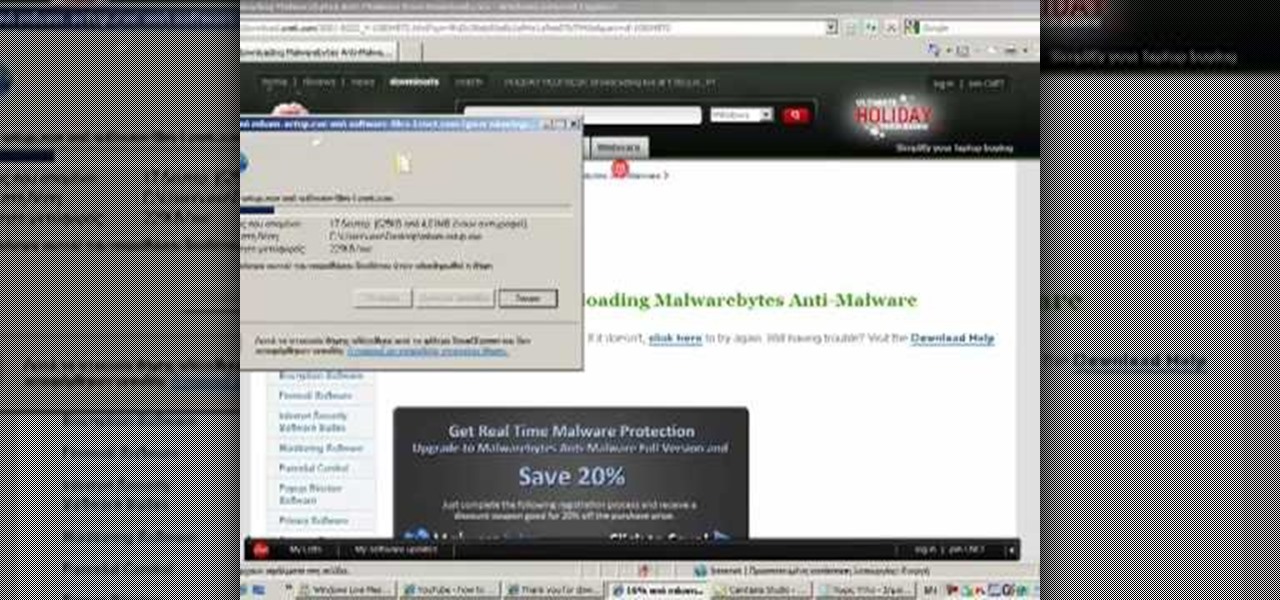
MS Removal Tool is the latest in the long line of malware programs that pose as official antivirus software and actually put virus and other tracking software on your computer. This video will show you how to remove MS Removal Tool from your computer and get it working good again.
Palladium Pro is one of the newest rogues making it's way around the internet, posing as antivirus software and then infecting your computer with all sorts of nasty malware. This video will teach you three different ways of removing Palladium Pro from your PC completely and getting your precious machine back.

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.
If your computer is working slow--or not at all, there could be some unsavory programs running amok in your system. Trojans, malware, viruses, and hacks are dangerous to the health of your operating system. This video tutorial demonstrates the measures to take in order to rid your PC of malicious programs. Stop being bullied by harmful applications and use such programs as AVG Antivirus and Malwarebytes to protect your computer. Once you've cleaned up your system, be sure to configure your se...

Is your computer spyware and malware that is slowing it down? There are people out there willing to help you for free, so have no fear. In this video, learn how to remove spyware and malware from your computer completely, leaving no sign it was even there!

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

Android enthusiasts have their own opinion as to whether you need antivirus software on an Android device. This debate will never end, provided that Android malware is in existence. This guide is not here to say, "Yes, you need antivirus," or "No, you don't." It's to give you all the facts, so that you can make a decision as to whether or not you need antivirus on your Nexus.

While you might suspect your MacOS computer has been infected with malware, it can be difficult to know for sure. One way to spot malicious programs is to look for suspicious behavior — like programs listening in on our keyboard input or launching themselves every time we boot. Thanks to free MacOS tools called ReiKey and KnockKnock, we can detect suspicious programs to discover keyloggers and other persistent malware lurking on our system.

Welcome to an introduction on writing basic malware, an optional sub-series in which I expose you to malware and its technologies. This is written for those who wish to seek a beginning in malware analysis or enlightenment on the subject. We will be justifying the writing and covering types of malware.

Let's say you got a little careless while installing apps from unknown sources, and now your Android device has been infected by malware. Or perhaps your friend has come to you for help after they had haphazardly installed random apps until their phone was filled with popups and garbage like that.

Worried about the MAC Defender that's been going around? Don't let your Mac get infected, watch this informative video to learn how to keep it virus free. If you are concerned with malware attacking your OS X Mac, you should watch this video.

Robert Templeman from the Naval Surface Warfare Center in Crane, Indiana and several of his friends from Indiana University recently developed an Android application that is capable of gathering pictures and videos from mobile devices in order to reconstruct a user's environment in 3D. The malware would come coded inside of a camera application that the user would download. The malware, called PlaceRaider, would then randomly take pictures throughout the day and carefully piece them together ...

If you've ever seen something called ThinkPoint Antivirus on your computer, you have gotten one ofhte most widespread and infectious fake antivirus malware programs out there. To get it off your PC, follow the instructions below, or watch this video for an alternate method if this one doesn't work.

Watch this software tutorial video to learn how to use HijackThis to find malware hiding in the alternate data stream. This how-to video will make finding hidden malware easy and help you protect your computer.

Want to know how to make HijackThis, the popular malware scanning program, display only malicious registry entries? Learn how to use the Ignore List to acheive just that with this free home computing how-to from the folks at CNET TV, which offers complete instructions on how to tweak HijackThis to make removing viruses and spyware a breeze. For more information, and to get started protecting your own Windows PC from malicious software, watch this handy how-to.

Don't just click X when closing pop-ups! You might be installing malware. This internet tutorial video will show you how to close pop-ups safely without installing spyware, malware, or viruses on your computer.

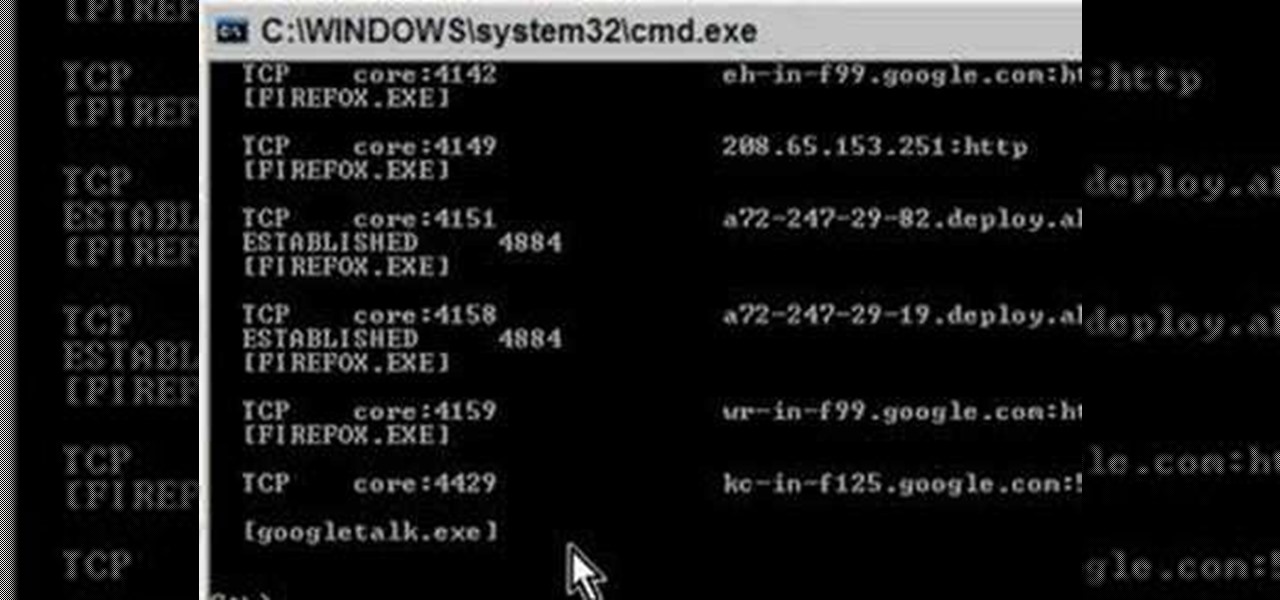
Learn how to use the NETSTAT.EXE function in Windows/DOS to help detect spyware and malware on your computer.

Chrysaor, a zero-day spyware believed to have been created by the Israeli "cyber war" group NSO, is an even greater threat to Android phones than it ever was to iOS.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

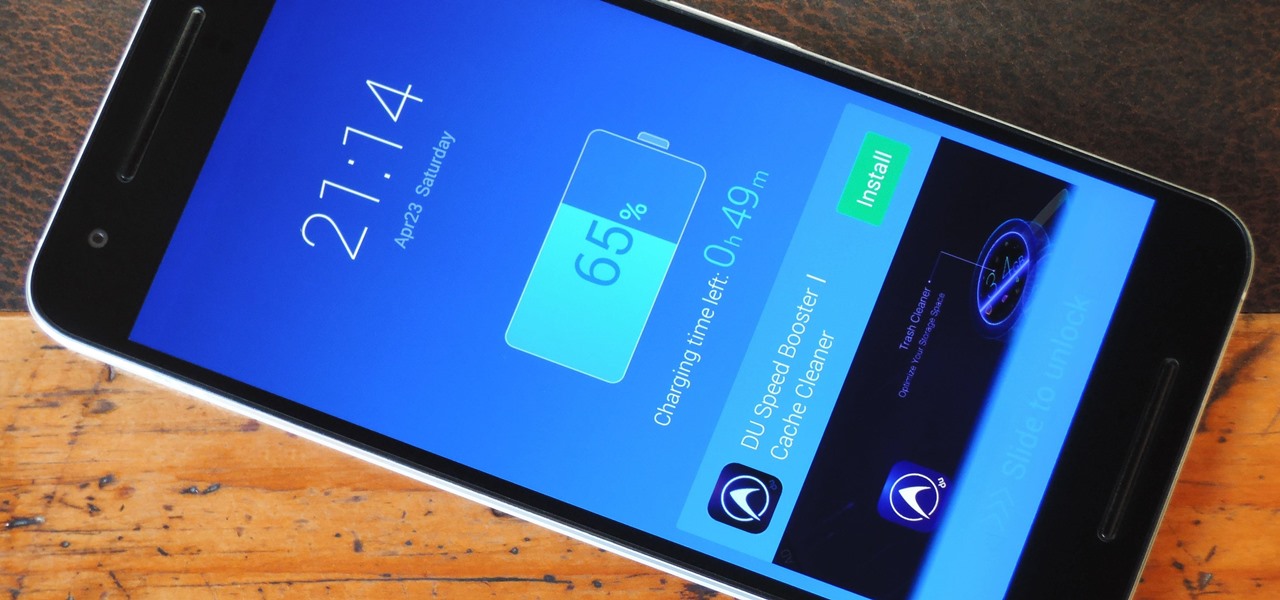
There was a somewhat recent outbreak of malware on Android, and it came from an unlikely source—the Google Play Store. Several established apps have received updates a few months ago that contained an unwanted add-on called either DU Quick Charge, DU Battery Boost, DU Boost Charge, DU Speed Charge, DU Speed Booster, or another name starting with DU.

Restore your iphone from disaster with this handy tip. If your phone is acting strange, and you need to restore it, you should place it into DFU mode. DFU will help you restore your phone from any malware or hiccups in downloads you've experienced.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Welcome back, my novice hackers! One of the most common questions that Null Byte readers ask is: "How can I evade detection by antivirus software on the target?" I have already talked about how AV software works, but to obtain a deeper understanding, what better way is there than opening up and dissecting some AV software?

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

Want to know how to remove viruses, adware and other sorts of malware from the Windows command line? It's simple! So simple, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over four minutes. For more information, including step-by-step instructions, watch this video guide.

Looking for a primer on how to use the SuperAntiSpyware and Malwarebytes anti-malware apps on a Microsoft Windows PC? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over ten minutes. For more information, including step-by-step instructions, take a look.

Watch this software tutorial video to learn how to use HijackThis to make sure you've deleted a malicious file for good. The tips in this how-to video will help you delete malware from your computer permanently.

Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Super Mario Run was released for iOS on December 15, 2016. Even though it debuted as a "free" app, almost all of the playable content was hidden behind a ridiculous $10 unlocking package. Despite coming with such a hefty price tag and receiving a two-star rating on the day of its release for iOS, Android users are still very much interested in giving this game a whirl.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

Welcome back, my budding hackers! In this series, we are trying to understand how AV software works so that we can learn to evade it. To that end, we are working with the open-source AV software, ClamAV. I had previously introduced ClamAV in Part 2 of this series. If you have not installed it yet, go back to that and install it.

Your Windows computer may be experiencing some issues, and those issues may be a direct result of computer viruses and malicious software from the internet. One of the simplest ways to find these issues and repair them is by using a freeware program called System Repair Engineer (SREng). But that's not all it can do… check out the video to see a basic overview for using SREng.

This video tutorial from ballader1 shows how to remove viruses, trojans, adware, spyware from your computer.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

This video tells us the method to remove Trojan Virus from the computer. This can be done in a couple of steps. The first step involves the downloading of a specific application from the web. We have to search this application in Google. Type 'malwarebytes' in the search engine and press enter. Go to the third result starting with 'Malwarebytes Anti-Malware'. Click on 'Download Now' on the resulting page. Open the application and select 'Perform quick scan'. This will scan the computer for Tr...

According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.