First off, don't be frustrated. YOU CAN DO IT! Contrary to the message in the image above, it's NOT over. It's just beginning. And when it comes to solving the New York Times crossword puzzle, the old cliche does apply: practice makes perfect.

With the CDs and DVDs you want to do less purging and more organizing. A good way to unclutter your DVDs is to dedicate a bookshelf to your collection. Put the adult movies on top and alphabetize them so that they are up away from the kids reach. Put the movies for the family and kids down lower so that they can get to their movies and watch them. For the CDs a binder will hold a lot of them and allow you to get rid of all the hard plastic cases. You can put hundreds in just one binder. A gre...

Playing hard to get doesn't work with a Scorpio; they only respond to slavish devotion. So drop everything and dedicate your time solely to the Scorpio in your life. Learn how to use astrology advice in dating, by watching this how-to video. Pick up tips on making a relationship with a Scorpio work.

Praying the rosary is one of the Catholic church’s most popular devotions and enduring images. You may want to dedicate the Rosary to a specific intention, like a sick friend or relative.

Wondering how you can allocate more RAM to Minecraft? Watch this video to learn how to dedicate more of your computer's RAM to Minecraft. This video contains the code to enter into your computer to change the allocation of RAM for Minecraft.

Learn how to play "Single" by New Kids On The Block Ft. NeYo, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

In this video you will learn how to build a retaining wall to flatten a sloped lawn. He says that if someone wants to garden but their yard is sloped and they know they can't do it, they should know that this is a lot of work. So be prepared to dedicate a lot of time and effort. You start by getting a building permit. If you're looking to build a low retaining wall you start by digging a trench a little wider then the stones and a few inches deep (the higher the wall the deeper the trench). F...

Looking to cut your monthly expenses down? Brown-bagging is one of the easiest ways to save money, especially if you stock several key items. In this video, ways to pack a lunch for a dollar a day are gone over.

Google and eight top Android partners have just signed the Android Networked Cross-License, nicknamed PAX. On the surface, this looks to be a peace treaty of sorts that could end several patent wars.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

LG literally rolled out a prototype of its cutting-edge flexible display at CES 2016 in Las Vegas. The company showed off an 18-inch screen with 1,200 x 800 pixel resolution that you can roll up like a magazine or newspaper and take with you. And while an 18-inch HD screen that rolls up is already pretty impressive, LG plans to build them up to 55 inches and beyond, with 4K resolution.

Mobile gaming, in case you haven't noticed, is huge. From the astronomical popularity of Candy Crush Saga, to the ease of using old school emulators, we love gaming on our mobile devices. The future is also bright, just take a look at the Oculus Rift, an immersive virtual world that just might change the way we view and play games.

Why are people so afraid of risotto? Contrary to what a lot of home cooks seem to believe, it's really not a difficult dish to make yourself. Sure, there's a lot of stirring involved, but it's not nearly the culinary beast it's made out to be. The real deterrent to making homemade risotto isn't that it's hard—it's that it requires a lot of attention. Risotto needs a lot of babying. Part of the process involves standing over it for 20 to 30 minutes at the stove, stirring almost constantly whil...

If you have information technology or computer science aspirations — even white hat hacking — then Python is a programming language you absolutely have to be familiar with. According to a recent survey of industry experts, Python is the fastest-growing language in the developer field. It's also one of the most sought-after skill sets among employers and is responsible for some of the best hacking tools.

Despite Huawei's ongoing battle with the US government, the Chinese company has continued to release phones in the US under its Honor brand. The Honor X series has been consistently released for several years, offering midrange specs at ridiculously low pricing, and the Honor 8X is no exception.

On August 1, Google Play started requiring new app submissions to target at least Android 8.0 Oreo's API. Then, as of November 1, all updates to existing apps were required target the same API. While at first glance, this change may mean little to you, it will have a profound impact on Android. Now, your favorite apps will be getting better.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Welcome back, my novice hackers! It has become clear from some of your questions that quite a few of you are unfamiliar with the hexadecimal system, or simply, hex. The hexadecimal system is used throughout computing and if you have never studied this Base16 numering system, it may appear relatively opaque.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

The coming year promises to be a good one for those of us watching the augmented and mixed reality world. And the Consumer Electronics Show (CES), starting Jan. 5 in Las Vegas, Nevada, for its 50th year, is bringing 2017 in with a bang—we're expecting a ton of great announcements on the horizon.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Welcome back, my hacker apprentices! Several of you have written asking me how you can check on whether your boyfriend, girlfriend, or spouse is cheating on you, so I dedicate this tutorial to all of you with doubts about the fidelity of your spouse, girlfriend, or boyfriend.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

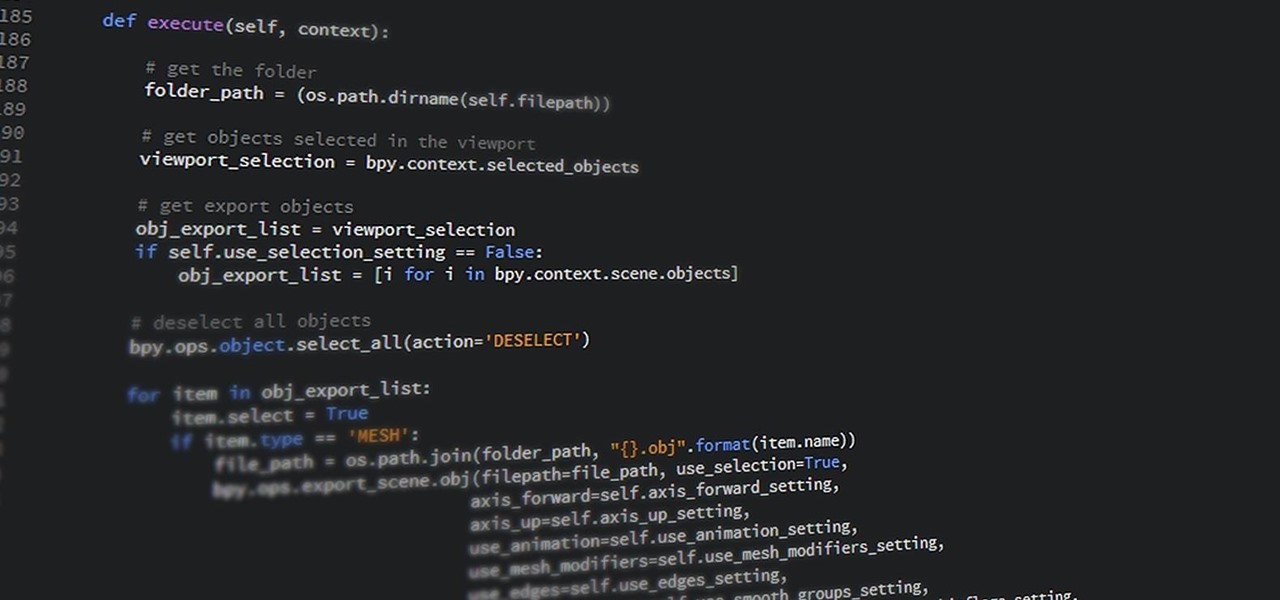
In this simple tutorial you will be shown step-by-step how to write local shellcode for use on 64-Bit Linux systems. Shellcode is simple code, usually written in assembly that is used as payload in exploits such as buffer overflow attacks. Payloads are the arrow head of an exploit: though the rest of the arrow is important for the delivery of the attack, the arrow head deals the killing blow. In reality, payloads are slightly less exciting yet far more interesting and intelligent than medieva...

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Tommy and Al dedicate this podcast to answering the question of the week: What is the best way to attach legs to a column? With explicit instructions, they demonstrate how to use dovetails to get the legs and columns to fit together “nice and tight.”

Hi everyone and welcome to my first ever blog about yummy food! I want to thank you in advance for your support and for reading my articles.

I recently posted a link to what seemed to be a very useful guide on Lifehacker for creating a TOR button in Chrome. However, when I tried it myself, it did not work. Also, it lacked a warning on the limits of Tor, which I think are important. Therefore, I decided to create an updated and more comprehensive tutorial.

Smartphones are crazy awesome. You can do your banking, track your children, find directions, and even pretend to have a mustache. The only thing that these personal supercomputers are missing is physical interaction with the environment.

The philosophy of street art is a long and complex one. This is just the first in a series of the individual street art philosophys i have come across.

You wouldn't think that something so simple as a "suggested users" list would create so much controversy, but Google+ seemed to have accidentally ignited a firestorm when they introduced a new feature over the weekend: the "Suggested People to Follow" list now appears when a new user joins Google+.

Now that it's been a week since Google+ rolled out pages, we've gotten over our euphoria at finally getting the feature after a long wait, and reality is starting to sink it. It's not as flexible as a Facebook page, it seems to be time consuming, and you can't even get a unique URL. On the other hand, your Google+ page will show up in Google searches, and help bump you up a bit. Here's how the search stacks up when I search for "WonderHowTo" in Yahoo! vs. Google (Note: I've turned on private ...