
How To: Do the dance from Michael Jackson's "Smooth Criminal"
In this seven part tutorial, learn how to perform the exact dance from Michael Jackson's "Smooth Criminal". Keep the legacy of the King of Pop alive and well with these cool moves.


In this seven part tutorial, learn how to perform the exact dance from Michael Jackson's "Smooth Criminal". Keep the legacy of the King of Pop alive and well with these cool moves.

A renowned pop-culture icon, Michael Jackson revolutionized the arts of pop music and dance with his large body of work. Learn one of the most famous dance moves, his 'Smooth Criminal' move, in this step-by-step tutorial.

No matter how freaky and alien-like Michael Jackson got towards the end of his life, he made an unforgettable contribution to the music world. Leaving us pitch perfect songs like "Billie Jean," Thriller," and "Smooth Criminal," the dude knew how to rock in style.

One more business has decided that rewarding hackers to find flaws in their computer systems is a wise investment! As you know, a number of software companies offer bug bounties, and some of these can be quite lucrative. Google, for instance, offers a bounty of $150,000 for anyone who can hack their Chrome operating system, and many other companies are offering similar bounties, although, not quite as lucrative. Now, United Airlines has decided to offer frequent flyer miles to hackers who fin...

In this tutorial, learn the starting dance move from Michael Jackson's music video for "Smooth Criminal". This spicy song is one of MJ's greatest hits and in this clip, learn how to do the wave move he does in the beginning. Once you master this step, you will look amazing on any dance floor.

Want to master "Smooth Criminal" by Michael Jackson? See how it's done with this free video guitar lesson, which presents a complete breakdown of the song and its constituent riffs. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing MJ's "Smooth Criminal" on your own guitar, just take a look!

The Null Byte community is all about learning white hat hacking skills. In part, this is because I believe that hacking skills will become the most valuable and important skill set of the 21st century.
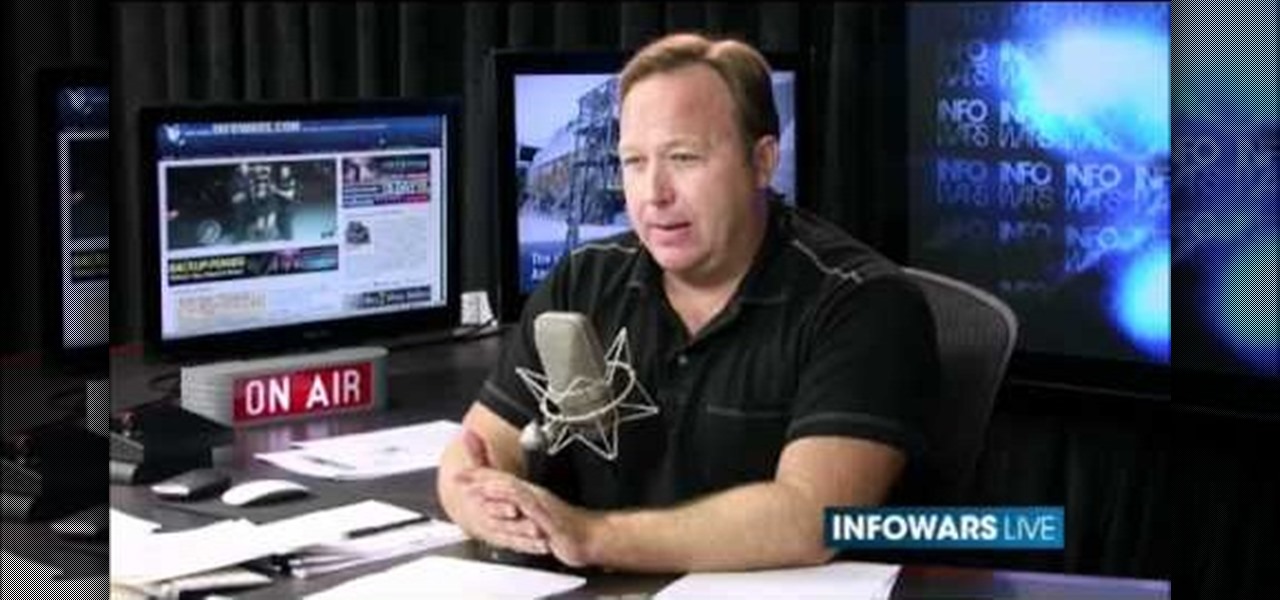
Tsa whistleblower calls alex jones and reveals the tsa are hiring harden criminals on purpose!

No City would be a pretty awesome name for just about anything. Rock album, memoir, celebrity child, even a Yu-Gi-Oh! card / deck. This video will teach you how to make an awesomely powerful No City deck for Yu-Gi-Oh! and kick some ass with it.

Don’t let cyber bullies push you around, being nasty and spreading rumors about you online. Learn how to fight back against tormenters who hide behind a computer screen. Internet harassment is just as damaging and hurtful as any other form, and proper action needs to be taken to keep the victim safe. Watch this video tutorial and learn how to protect yourself or someone else from cyber bullies,internet harassment, or online rumors.

Grandmaster Alexandra Kosteniuk teaches you how to play a real game of chess in this video tutorial. From the game Onischuk vs Carlsen in Biel (2007). Black plays and wins, by first taking white's rook and checking the king. The white king then takes the black queen, and so on. This will show you how to keep a criminal pawn at bay in a chess middle game, causing your chess opponent to resign like the loser that he/she is.

Last week, the U.S. Justice Department issued criminal indictments against seven Iranian hackers. These hackers, working for private companies in Iran, are accused of orchestrating DDoS attacks against U.S. financial institutions from 2011-2013 as well as intruding into the control panel of a small dam in Rye, New York. It is thought that these attacks were a response to the U.S. tightening financial restrictions on Iran during those years and the NSA-based Stuxnet attack on their uranium enr...
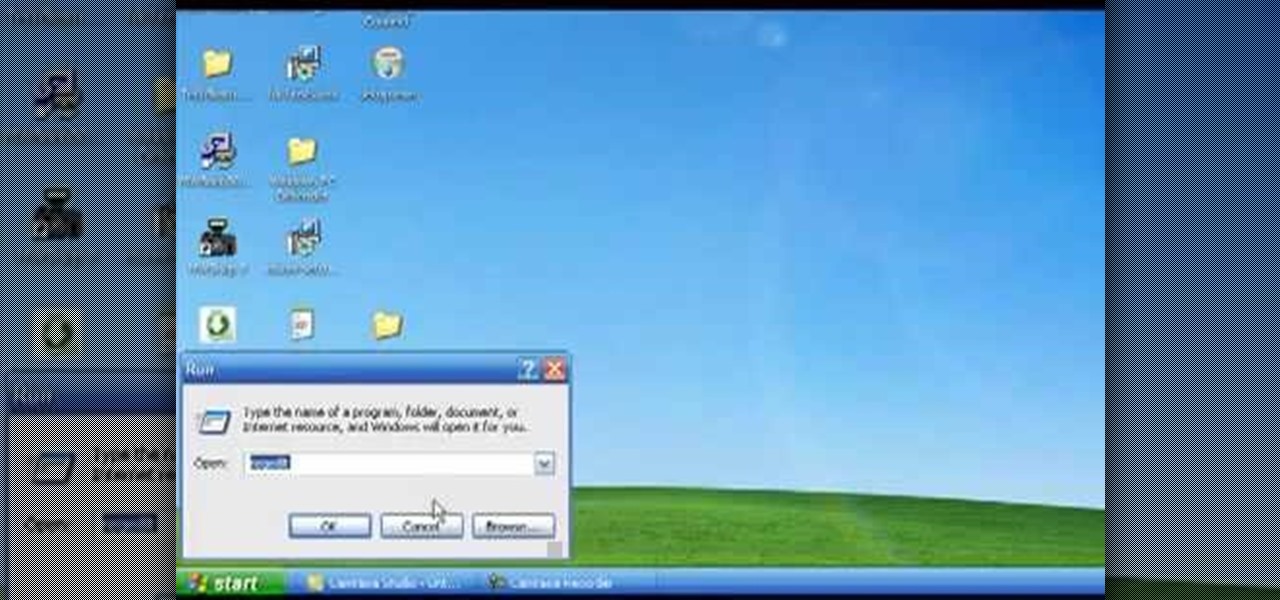
Cyber Security is a horrible computer virus. It mimics a virus protection program and invades your system, making it nearly impossible to remove. In this tutorial, learn how to remove this annoying trojan horse from your PC and save your computer.

In the Godfather II you will need every advantage you can get to climb your way to the very top of your own criminal empire. These strategies from the experts at IGN should help you take over crime rings with ease. This video includes multiple tips and tricks in order to get going on your trip to becoming the number one Don.

Black Friday and Cyber Monday are becoming almost synonymous these days, but there are still plenty of awesome deals that you can only get starting on the Monday after Thanksgiving. Amazon, for instance, will be hosting a week-long Cyber Monday sale, and of course, most big-box retailers will follow suit with their online stores.

Kristin Holt is here show you some cheat codes that will make defeating the criminal underworld of Gotham City a downright breeze in LEGO Batman: The Videogame.

Keep warm and stay cute this winter! Make your own pair of trendy cyber fluffies! All you need is some faux fur in a color and style you like, thick elastic, plus a few basic sewing supplies (like a measuring tape and sewing machines).

If you're looking for outdated magician's hat tricks then you've come to the wrong place. But if you're looking for a way to move like a smooth criminal and impress the ladies, then you've just met your guide to your next date.
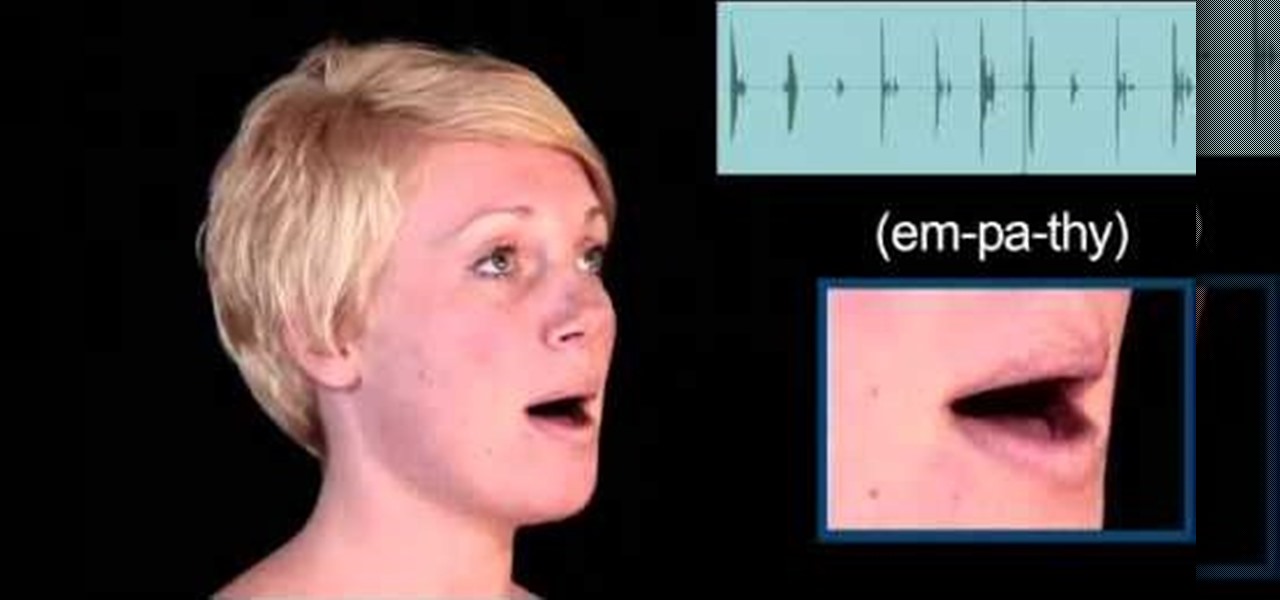
Today's word is "empathy". This is a noun which means the capacity or ability to understand the feelings of people.

I was bored when I found this piece of literature: ==Phrack Inc.==

Welcome back, my budding hackers! People often ask me, "Why are you training hackers? Isn't that illegal?" Although I usually give them a short version of this post, there are MANY reasons why YOU should be studying hacking.

In an article published in early-2015 by Peninsula Press, it was reported that the demand and the salaries for cyber security professionals are exploding! They cite that 209,000 cyber security jobs were unfilled last year, and that job postings have increased over 74% in the last 5 years. Job opening are expected to grow by another 53% over the next 3 years. You are definitely in the right field, my tenderfoot hackers! Some researchers are expecting information security jobs to continue to gr...

Dying to try online dating, but worried that the guy that you're digitally winking at is really a cyber stalker? Then watch this Dating Advice how-to video to learn how to date and decode online dating profiles. With this online dating translator you are sure to keep all the cyber stalkers out of the running.

In a world increasingly regulated by computers, bugs are like real-life cheat codes. They give you the power to break the rules and do good or bad without ever leaving your seat. And government agencies around the world are discovering and stockpiling unreported bugs as cyberweapons to use against anybody they see fit.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Whether you're the kind of gamer who likes to fight the law or fight for the law, you probably shouldn't pass up this sidequest line in Dragon Age 2. Accessible after completing the 'Birthright' quest you can pursue 'Magistrate's Orders', which these videos will give you a walkthrough of.

This video is a useful ex-offender resource that will help people with felony convictions get employment by teaching them to properly put together a resume. A poorly written resume can hinder your employment.

During a Laneway Revitalization project some gang graffiti was encountered and replaced with vibrant art work. The event organizer is a Toronto Police Officer who volunteers for the not for profit organization-The Ontario Gang Investigators Association. In this video an explanation of gang graffiti is offered. The organization Notogangs.org is comprised of sworn members of all areas of law enforcement who network regularly in the mandate of the prevention, intervention and suppression of crim...

Sexy Playboy Cyber Girl Dana Dicillo has some advice for you in making your audition video for Holly's 55th Anniversary Playmate Search reality show. If you ever wanted to be in Playboy, you need to watch this.

Yu-Gi-Oh! represented the third wave of collectible card gaming, taking the mantel from Pokemon and Magic and bringing the style of game to a new generation of kids. This video will teach you how to build three awesome decks for one of the video game versions of the game, Yu-Gi-Oh-Gx! Tag Force 2! They are called Cyber End, God, and Blue Eyes respectively.

Most gals put on makeup to fit into the norm: You know, to look professional and "put together" for work or to look desirable on a date or when clubbing with the girls.
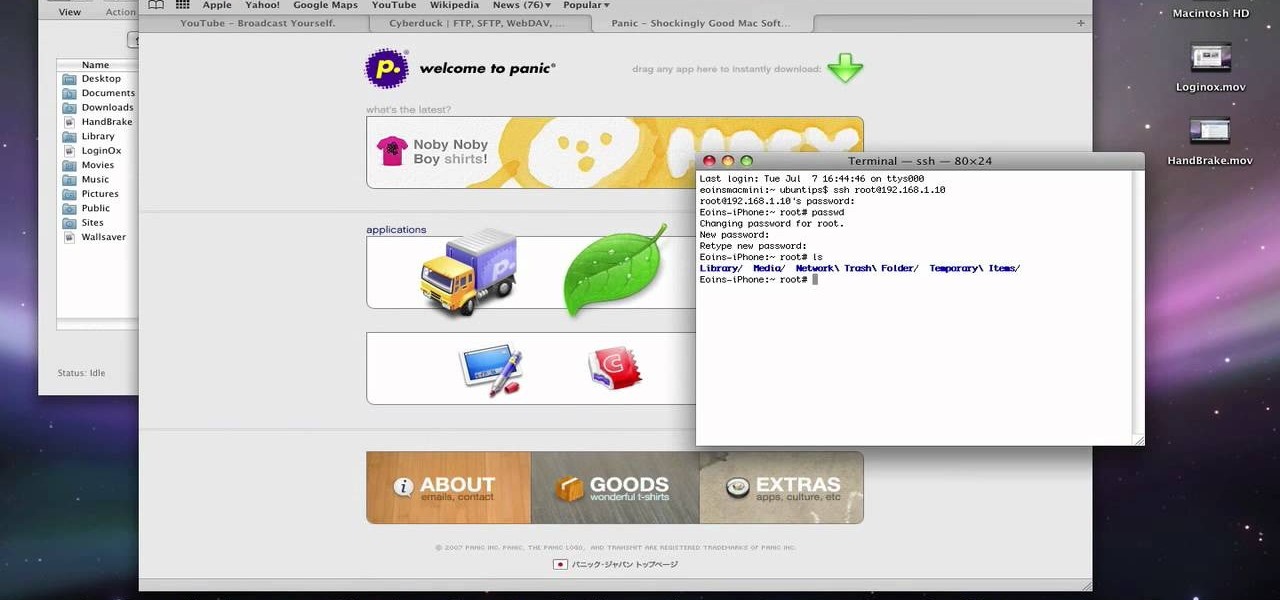
This video describes about accessing an iPhone in Ubuntu using open SSH, cyber-duck, Netatalk. For accessing using SSH, make sure your iPhone's Wi-Fi connectivity is on. Now open your terminal and type "SSH root@'address'". Here address refers to the IP address of your iPhone. You have to type a password to access the iPhone contents. Once you are authenticated type "ls" and you will be shown with the contents of the iPhone. The second method is using cyber-duck. In it, choose SFTP as the con...

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Want to fulfill your dream of becoming an ice cream truck driver? If the idea of rolling around in the sunshine selling ice cream sounds good to you, here's what you need to do.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

Welcome back, my rookie hackers!
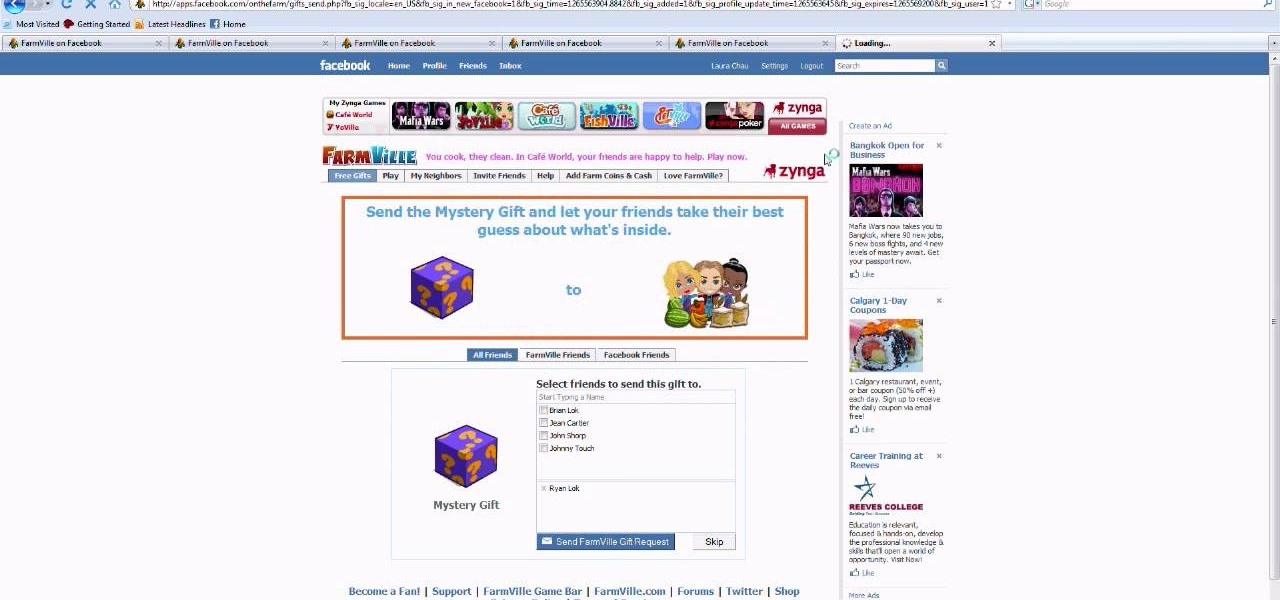
In Zynga's uber popular web game Farmville, you really do receive as much as you give out. Being a good neighbor to your cyber friends means you score lots of loot - via Farmville "gifts" - but you gotta send a few, too.

If you wait for the newspaper to come out with all the Black Friday deals, you'll have lost out on several hours of valuable shopping time! The best way to stay updated this Black Friday and Cyber Monday is by using smartphone apps!

This video would be very interesting for those seeking careers or those interested in the field of criminal science. This field involves forensic science. The video explains to us how to use gentian violet in order reveal latent fingerprints. He explains to us the experiment he is about to do before he does it. Genetian violet is a type of dye solution that can be very helpful in retrieving fingerprints. Safety goggles and gloves should be worn at all times.

Who likes to buy apps? The answer is no one, of course. Unfortunately, as in life, the best apps and games don't come free. That's why it makes sense to wait until those apps go on sale before handing over your hard-earned cash. And what better day to find discounts in the iOS App Store than Cyber Monday?