In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

XSS Shell is a cross-site scripting backdoor into the victim's browser which enables an attacker to issue commands and receive responses. During a normal XSS attack an attacker only has one chance to control a victim's browser; however, the XSS Shell keeps the connection between the attacker and the victim open to allow the attacker to continuously manipulate the victim's browser. XSS Shell works by setting up an XSS Channel, an AJAX application embedded into the victim's browser, that can ob...
Different ways of using a proxy bypass to access blocks sites is shown with ease in this video. Many places explained to be blocked with internet security such as libraries and schools. Using a search engine such as Google you need to search for a proxy site. After a proxy site has been found you will use it to access the blocked websites through another servers internet provider. The narrator explains that proxies are just a way to bypass internet blocks by avoiding using the blocked compute...
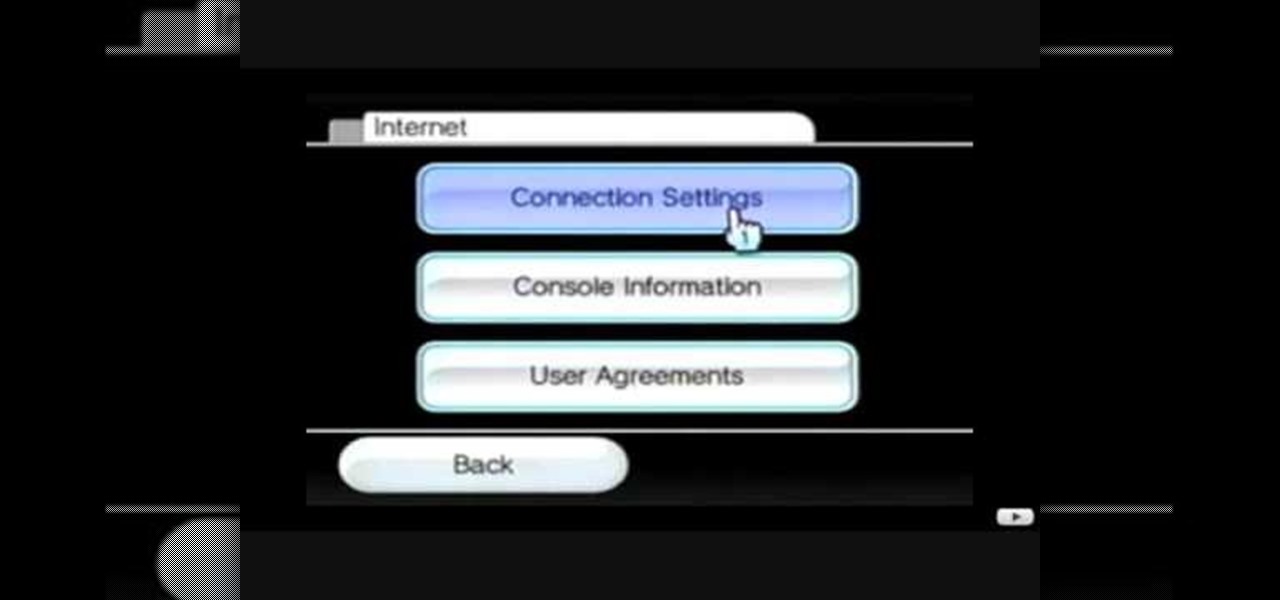
This video tutorial shows how to connect to the Internet using the Wii video game system. The advantage of connecting to the Internet with your gaming system is to play games, such as Animal Crossing or Call of Duty, with other players. You can also get the Internet Channel which allows you to watch YouTube videos and do other tasks you would normally do on the internet. You will need a wireless router to do this. On the Wii home menu, click on Options, Wii Settings, and scroll once to the ri...
Cookies serve their purpose in Internet Explorer 7. They let the browser know which sites you have visited so you don't have to get security prompts every time you back to them. However, they can also slow down your browser, which can be frustrating. This video will show you how to delete cookies in Internet Explorer and browse faster.
This tutorial on the companion Tech Ease for Mac site explains what podcasting is and shows you how to subscribe to podcasts using iTunes, a free program from Apple. Since iTunes is cross-platform, the steps shown in the movie will work on Windows as well. This movie defines podcasting, shows you the different types of podcasts you can create, and how to subscribe to podcasts using iTunes.

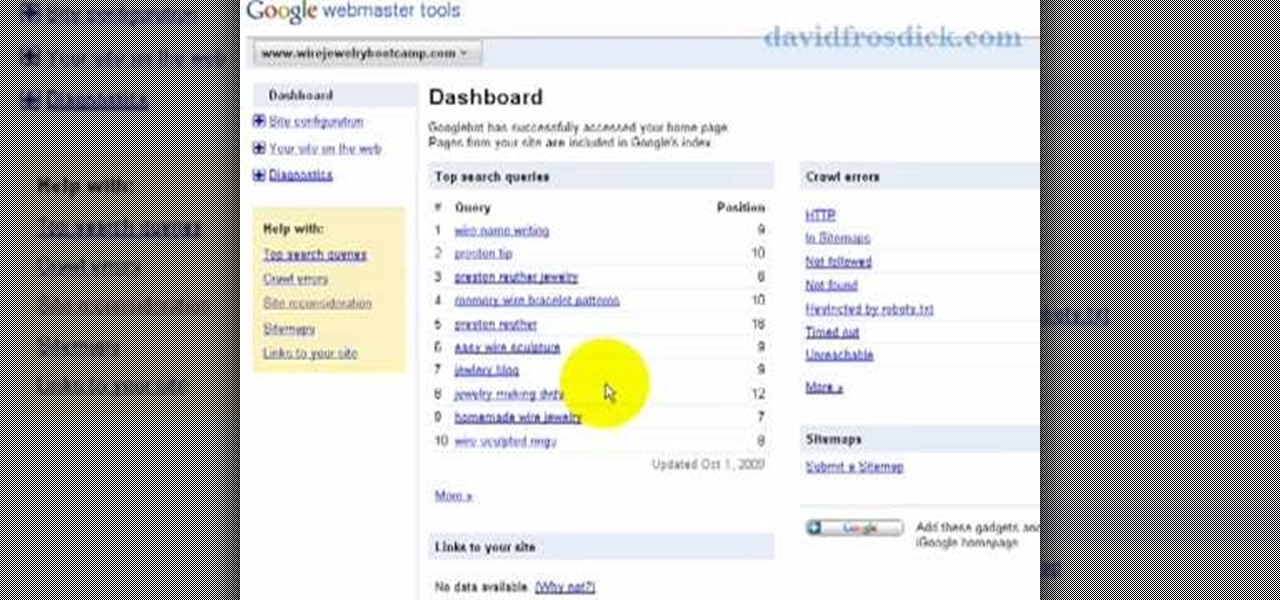
Freelance web developer and Internet marketer David Frosdick offers some tips and tricks in this video tutorial on how to add your site to Google Webmaster Tools.

Want to multiply three or more fractions or mixed numbers? It's easy: Turn the mixed numbers into improper fractions. Cross cancel where you can. Multiply straight across. (simplify and reduce if you did not completely cross cancel). This free video math tutorial presents a complete walkthrough of the process. From Ramanujan to calculus co-creator Gottfried Leibniz, many of the world's best and brightest mathematical minds have belonged to autodidacts. And, thanks to the Internet, it's easier...

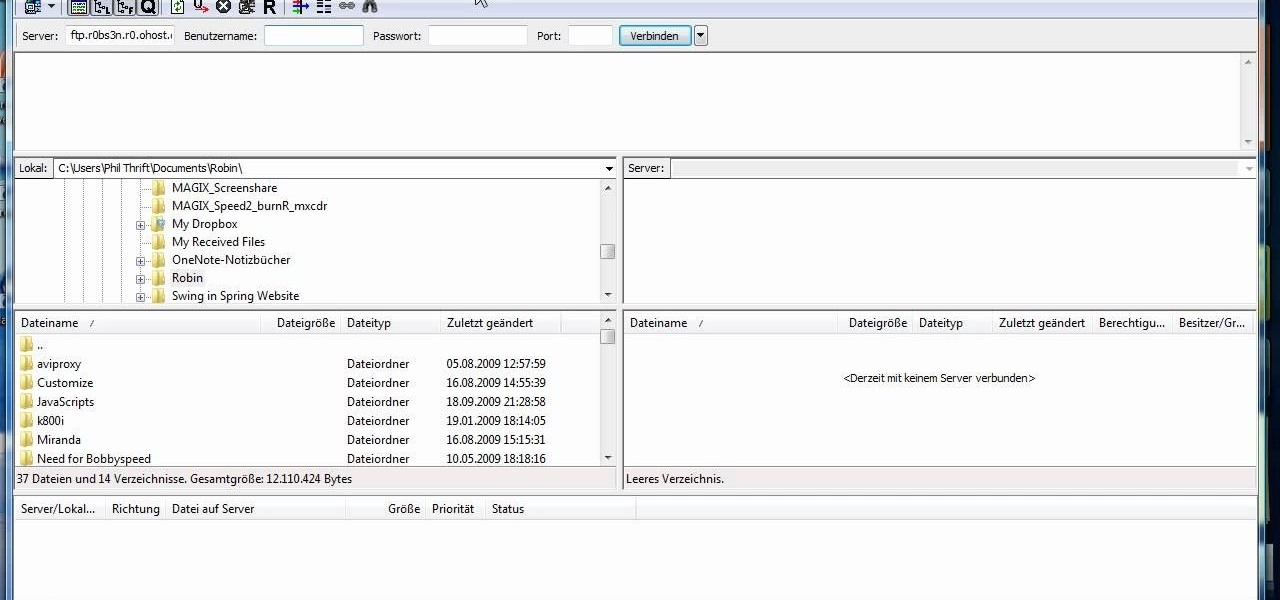
Need to send large files across the Internet? An FTP site is a great resolution to emails that bounce back due to attachment overload. By uploading your file to an FTP site, it will allow your recepient to download the file from the site with ease. In this tutorial, learn how to upload and download files using the FileZilla FTP client.

If your computer or web browser is running slowly, a good place to start clearing space is in your Temporary Internet Files. Temporary Internet files, as well as cookies, are collected every time you visit a site online. These files make it easier for your PC to remember your browsing history, and your log in information for various websites. However, sometimes all of these little files can add up into one big clog on your machine. If your computer isn't running up to par, follow along with t...

Bobthegrand demonstrates how to clear the search history on the Internet Explorer and Firefox web browsers. In Internet Explorer, click the star on the toolbar to see stored web browsing tabs. Click on the history tab to expose the search history. Right click on the site that you would like to erase and then hit the delete key. Click yes in the verification popup window. In Firefox, click the expandable search options on the left hand side of the browser. Your search history will appear in th...

To delete Internet Explorer 7 or 8 from you computer, search for "unlocker" in the Google search engine. Click on the first search result to go to the unlocker site. Click download to access the unlocker application. Click the save me option when prompted. Next, find the downloaded files and install the unlocker application on your computer. Go to the local disk C, open the program files and find Internet Explorer. Right click on Internet Explorer and then click on the unlocker. Select the ap...

You want to use the websites you want to use, regardless of any school blocks or other hindrances, so how? This video tells us by using the IP addresses of your favorite sites. To find this IP address, at your home, or an other unblocked location, in your start menu, you must access Programs, then Accessories, then Command Prompt. When the window pops up, then type in "Ping http://www.myspace.com" without the quotations, for instance. Write down, then, the string of numbers that appears, whic...

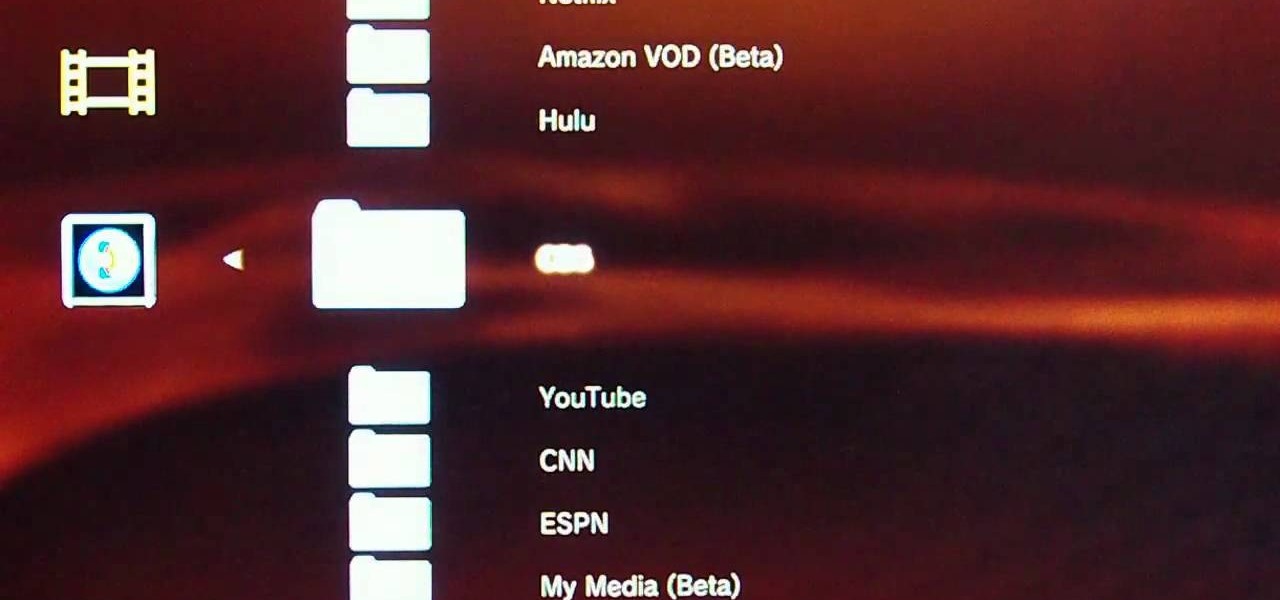
It's easy to watch Hulu on your Playstation 3 console. Using a free trial version of PlayOn, you can watch a variety of internet TV & movie sites on almost any game console - including your Wii. Who needs cable anymore? This video will show you how to set up your PlayOn account and use it to watch your favorite media sites on the console of choice.

The Newstweek might be the coolest new device of 2011 that no one is talking about. It's a pocket-sized device that allows you to access the data streaming through a wireless internet access point and change the news being read by fellow users at the hotspot, from any site, however you want. It allows you to do some amazingly inspiring and sinister things, like any really progressive technology, and this video will show you how to use it.

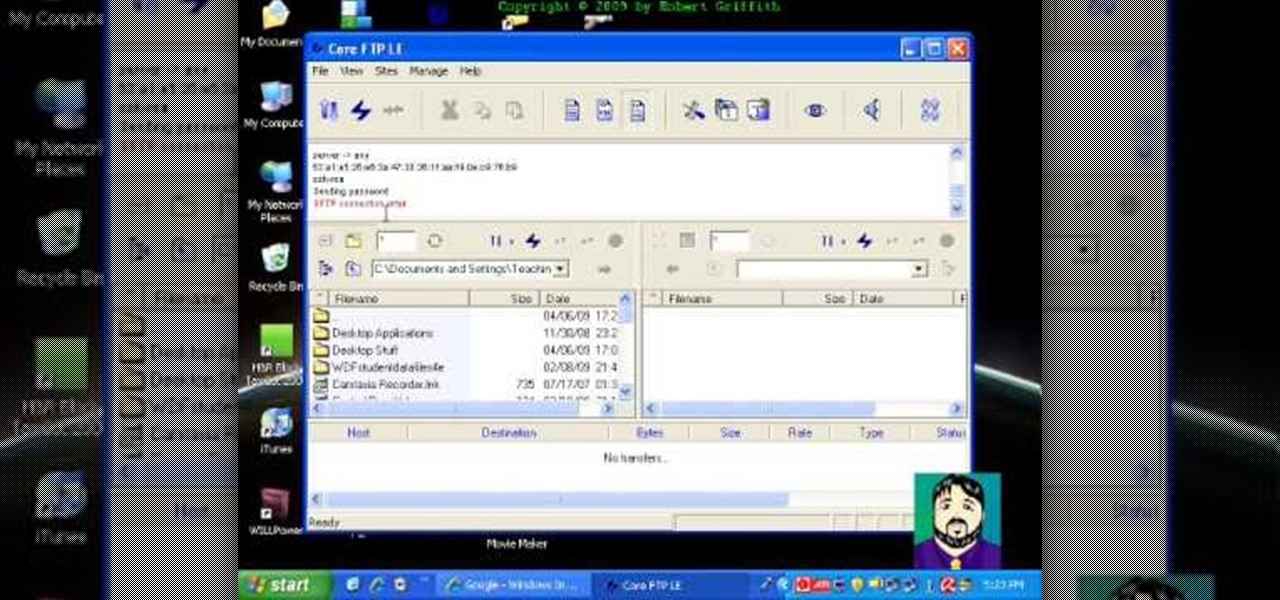
Select an FTP client that allows you to connect to the webserver. Download a free Core FTP Le software. Install the program. Use the site manager to name the internet site. Create a host/url, a user name, password and a connection. Connect to the web server. Create an index file to make files viewable. Open the Core FTP LE software. Drag files from the desktop (left side of the dialog box) to the internet server (right side of the dialog box.)

While it's easy enough to ask websites not to track your browsing activity in Safari, they do not have to honor your request. Plus, some of the third-party content providers that websites use can actually invasively track you across other websites. Thankfully, iOS 11 includes a way to minimize companies from tracking you across the web on your iPhone.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

What's the point of having a browser on your Android phone if you're only seeing part of the internet. Visit the full versions of your favorite web sites by configuring your Android browser to show nonmobile websites on your mobile phone.

This video demonstrates how to discover the dating history of people by searching on the website www.rateabull.com. The site searches their own dating database, as well as several other social networking sites.

The Internet is full of information, accessible with a web connection and a few strokes of the fingertips. The web is perfect for doing research for your college essays, or term papers, or thesis statement.

In this clip, you'll learn how to make a call to an external website from within a Silverlight app. Whether you're new to Microsoft's popular web application framework or a seasoned web developer merely looking to improve your chops, you're sure to find benefit in this free MS Silverlight programming lesson. For more information, including a complete demonstration and detailed, step-by-step instructions, take a look.

This video shows the method to turn off pop-up blocker in Internet Explorer and Firefox. Firstly, open Internet Explorer and go to 'Tools' option. Go to 'Internet Options' and click on the 'Privacy' tab. You will see an option of 'Block pop-ups' at the bottom of the window. You must uncheck it and hit 'Apply' to turn it off. For Firefox, go to 'Tools' and 'Options'. You will see 'Block pop-up windows' as the first option. Uncheck it and the pop-ups will not be blocked. You can also set except...

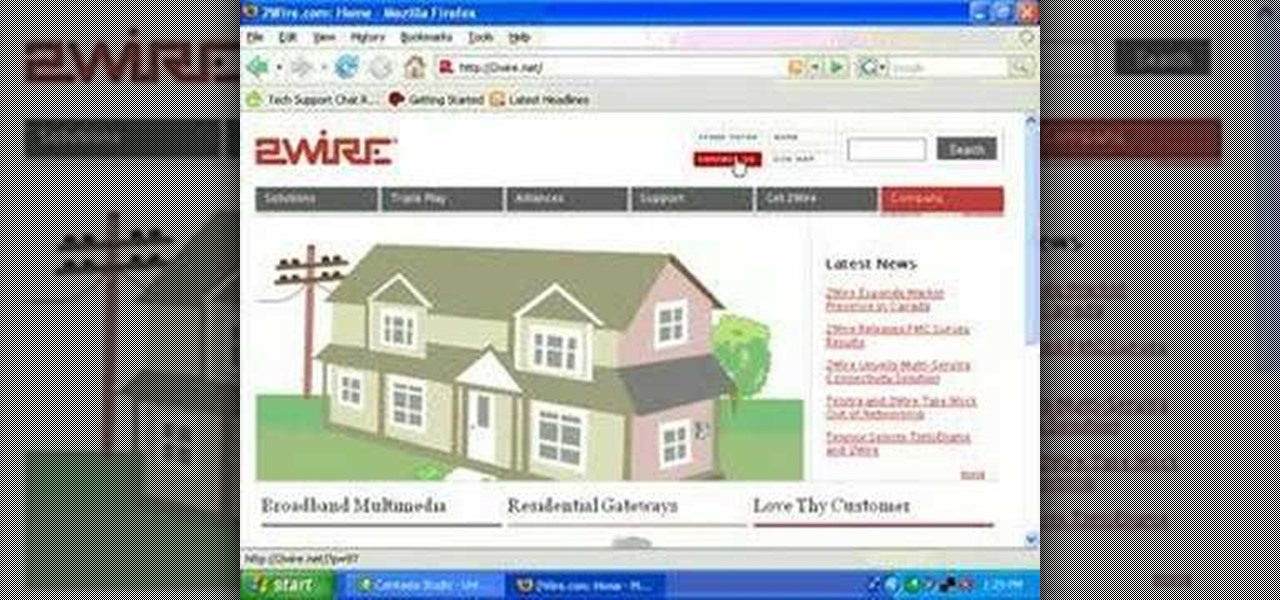
In this video, you will learn how to test your internet speed. In order to do that just follow this easy and quick steps and instructions. The first thing that you need to do is to go to this site:2Wire. Now click the Speed Meter located on the top of the page. A test will start and it will show you how fast your internet speed is. If you have followed this quick and simple steps and instructions correctly, you will not have any problems in testing you internet speed with the tool from 2Wire....

In this video tutorial, Chris Pels will show how to configure an ASP.NET web site to use a specific version of ASP.NET/.NET Framework. First see how to identify what version of the .NET Framework a web site is associated with by viewing the script map in Internet Information Server (IIS). See how a script map is associated with the root in IIS and then with individual web sites. Next learn about the ASP.NET IIS Registration tool (aspnet_regiis.exe) used to configure IIS or an ASP.NET web site...

Violin Lesson #7, 9-10 -- String Crossing Techniques. Todd Ehle teaches some string crossing techniques for you beginners in this 3-part lesson.

Both your Wii and your PC need to be connected to a router that has an internet connection. If you have a wireless router, the Wii can connect to it without any additional hardware. Instructions are provided with the Wii.

This is the GetNetWise video guide on how to set up Internet Explorer 6.0 for Windows to allow cookies from some sites. This is useful if you wish to block cookies by default, but allow for certain sites. The procedure is simple; firstly, select "Internet Options" from the "Tools" menu. Then select the Privacy Tab of the Internet Options menu, and under the Web Sites section click the Edit button. In the text box labeled "Address of Web site", type in the address of the site from which you wa...

Check out this instructional kickboxing video that demonstrates how to do a right cross or a cross punch. The cross is considered the power shot. The cross is a reliable kickboxing punch, and is great in competition. Learn the skills of kickboxing in this video on competitive kickboxing moves.

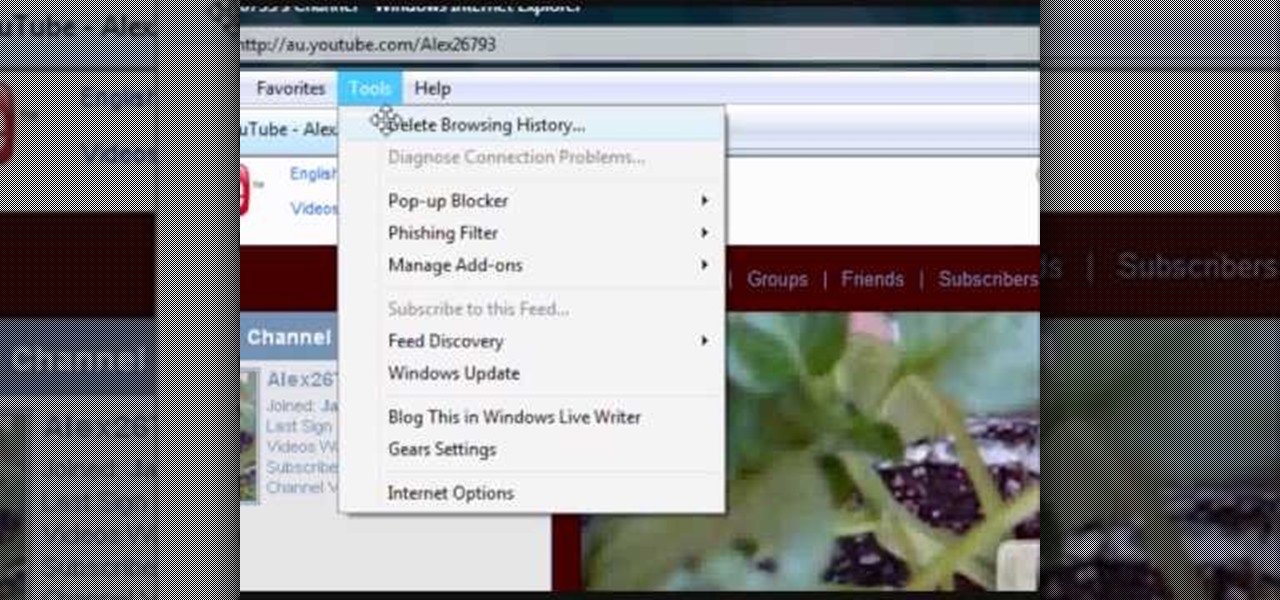
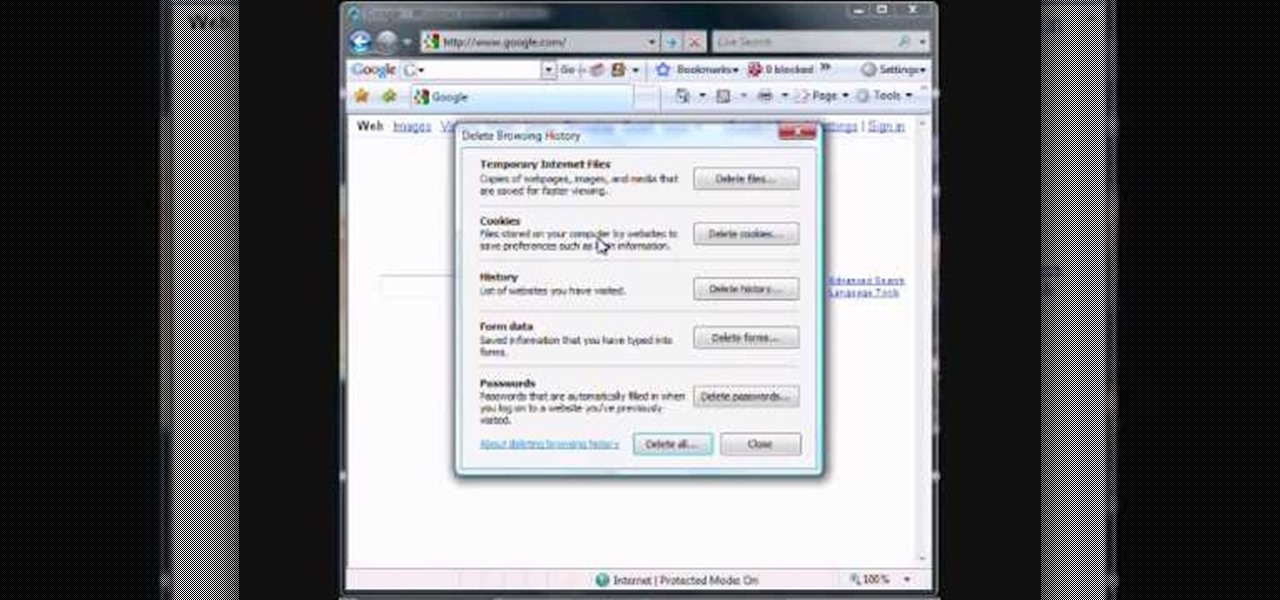
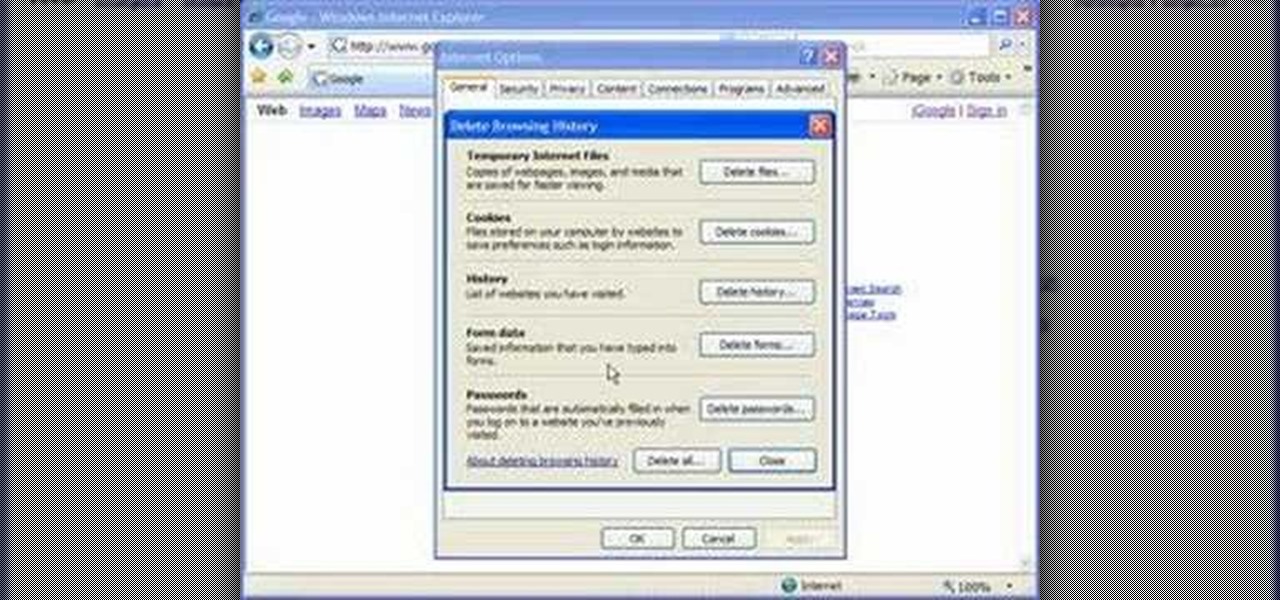
In this tutorial, we learn how to clear your browsing history in Internet Explorer. First, go to the tools button and then click on 'delete browsing history'. Click that and then a new window will pop up. If you want to clear everything, click 'delete all' and then 'yes'. The temporary internet files are fine to delete, this is just info that is saved after you visit a website. Cookies are bits of information that a site stores on your computer to remember who you are. The history is simply w...

This video tutorial from KaBoom215 presents how to use Xbox 360 Internet browser with NXE update.First you need to turn on your computer and make sure you have Windows Media Center on your Xbox 360 and your computer (preferably using Windows Vista operating system).From your computer, open Internet browser, search for mce browser, choose search result that says Anthony Park Software.Download MCE Browser from this site.Back to your Xbox 360 console connected to your computer, open Windows Medi...

Embed Facebook directly into your Internet Explorer or Mozilla Firefox browser's toolbar using this nifty new add-on directly from the people at Facebook themselves. This addon shows you on the toolbar the number of pokes, friend requests, unread messages and upcoming events that you have, in addition to quick links to various sections of the Facebook site. In this demo video, Patrick from Tekzilla explains the cool new features and details.

Google is one of the most powerful forces on the Internet, and their technology can be the key to helping you find success in whatever your online endeavor might be, from web design to filmmaking. This video is a part of their Google Webmaster Series, offering help to webmasters the world over on how to best utilize Google in their work. This video will show you how to ensure that Google crawls a particular section of your site without using any robots.txt.

In this tutorial, learn how to make a heart on your computer for such social Internet sites as MySpace and Facebook. It's very simple! Show your friends you care about them with this decorative love bonus!

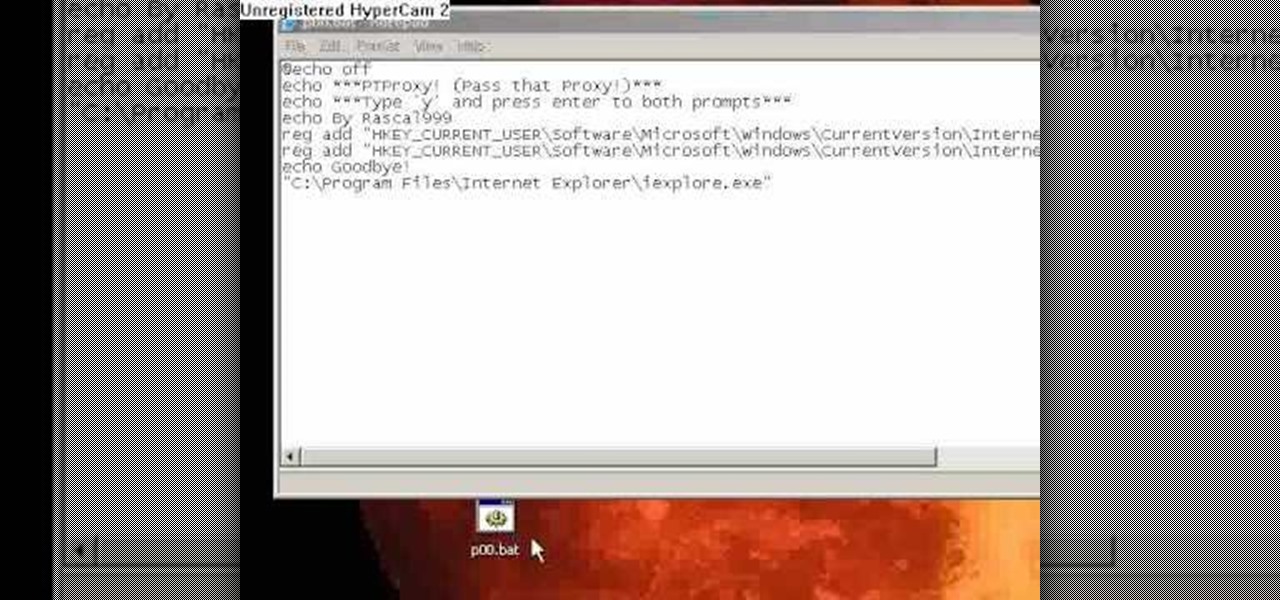
Some governments and organizations employ proxy servers to filter web content, permitting access to some web sites while blocking others. Here are several ways to get around these censorship policies. This is employed in China with YouTube and many other voices of anti-goverment ideas.

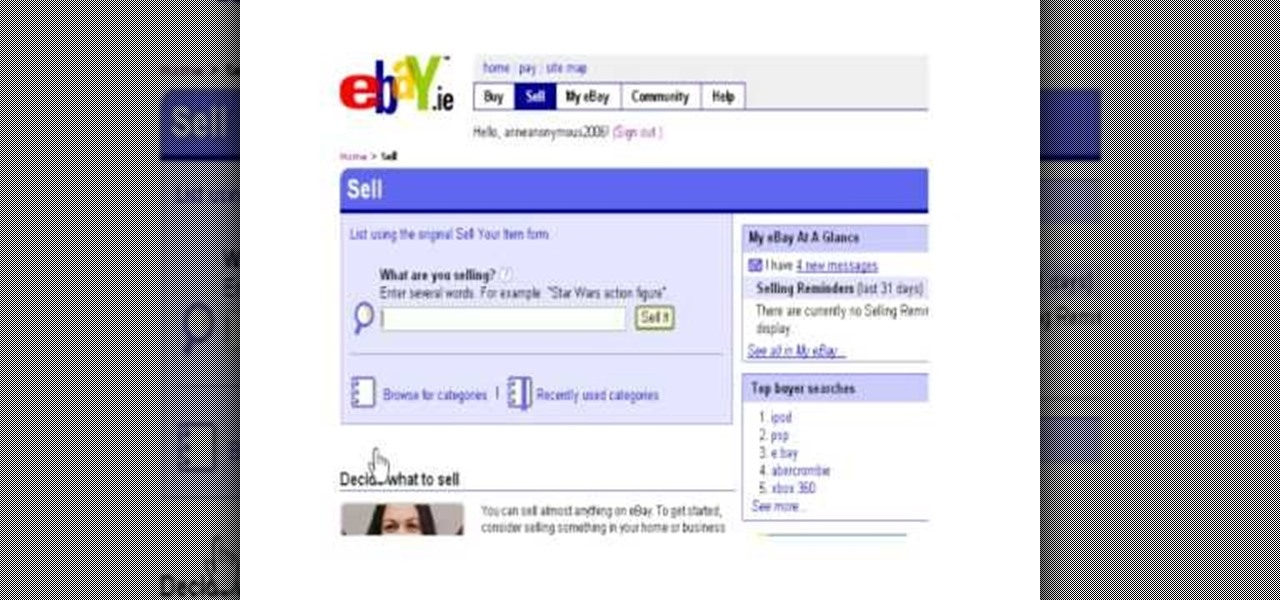
Experts say that every house has around 1500 dollars worth of merchandise that could be sold on eBay. eBay is a great alternative to the traditional garage sale these days, and with more and more people joining the site every day - why not get in on the action? eBay is an exciting Internet tool that allows anyone to sell anything. Check out this tutorial, for information and tips on how to start your own eBay seller's account. This is a great video to check out if you are new to eBay or have ...

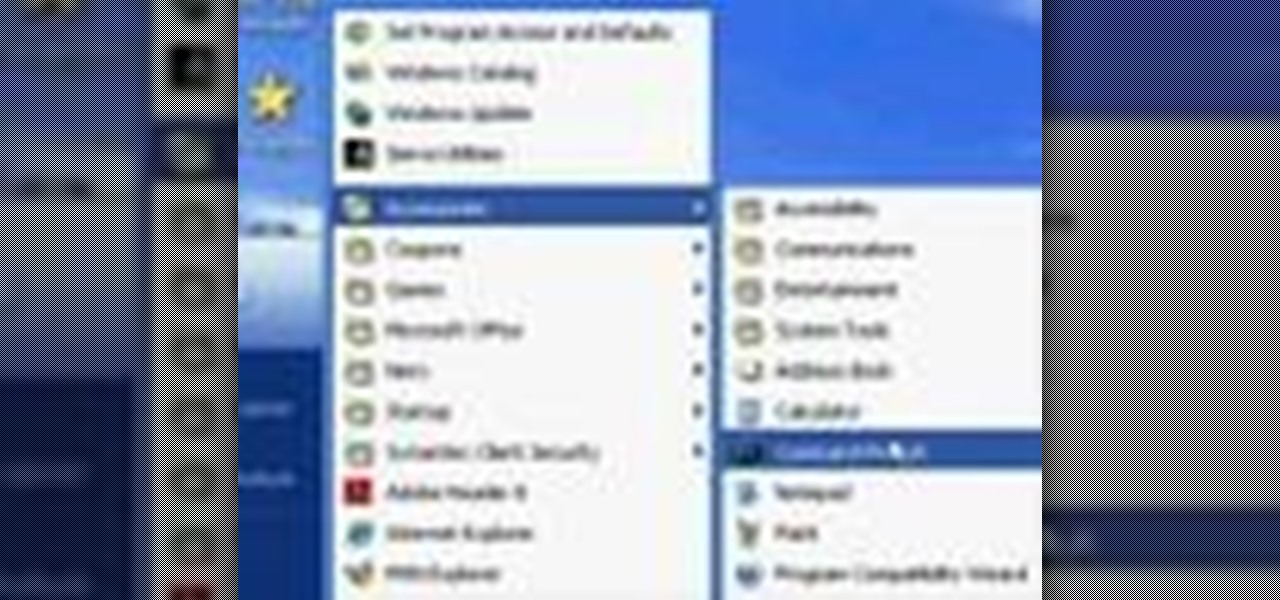
Whether you are protecting your children or hiding personal information, there are ways to block unwanted websites from your computer. Follow this tutorial and learn how to accomplish this on a Windows PC easily.

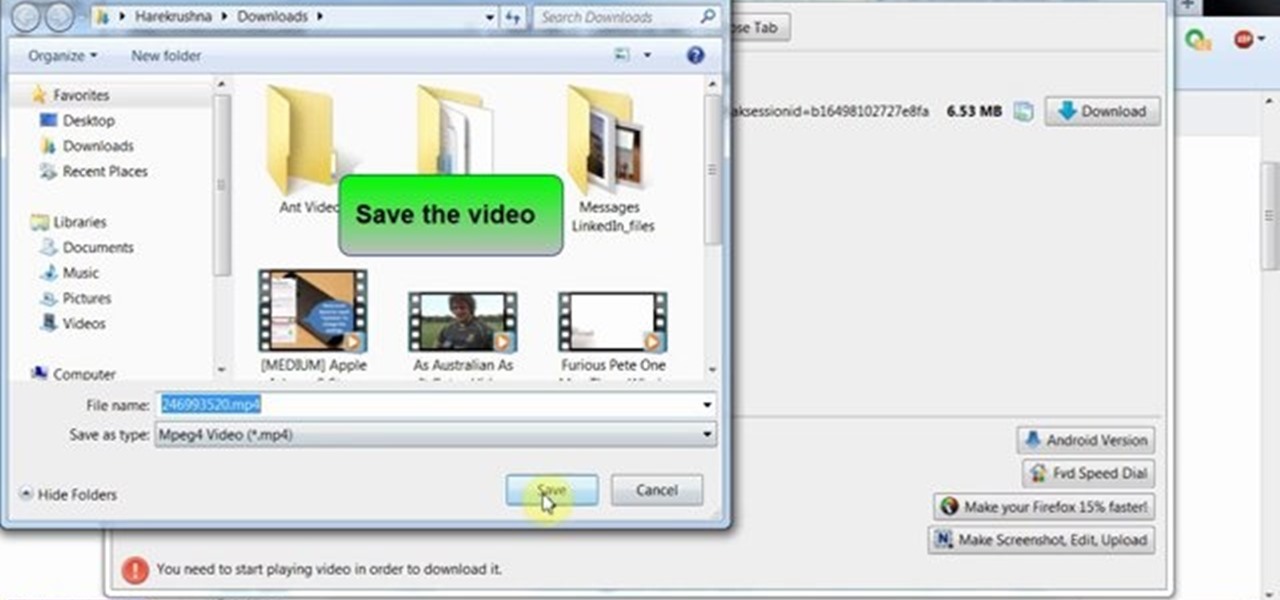
This video will guide you how to download any video from the internet through your Firefox browser. This add-on is also available in other browsers like Google chrome and internet explorer. Watch the video and follow all the steps to do it yourself.

Spice up your repertory of knitting stitches with the twisted cross stich demonstrated in this clever crafter's how-to. The stitch, though it might sound difficult, is much simpler than you would think and can be used anywhere a traditional cross stitch might be. Learn how to do twisted cross stitching with this free knitting lesson.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them