
How To: Combine traditional and digital media in art drawings
Watch this video tutorial as artist Merrill Kazanjian show you how to combine traditional and digital media in art drawings.


Watch this video tutorial as artist Merrill Kazanjian show you how to combine traditional and digital media in art drawings.

Last time in how to train you python, we covered the basics of variables and output. While we were covering variables, we talked briefly about strings. "String" is just a fancier way of saying "Word". A string is simply a set of characters encased in quotations, this lets python know that it is a word. Sometimes when we do things with strings we'll need to change them in order to do something. Python is case sensitive, for example "Null-Byte" is not the same as "null-byte". This is where mani...

This video from Do as I do presents a simple card trick. Cut the deck in half.

The previous owner chose this view. The trunk is naturally hollow. Dead wood is coming toward us. Branches are coming to the back so we will have to do some manipulation. The two parts of deadwood play together in an interesting dance. The piece of deadwood can be improved and the branches can be moved more to this side of the tree as a front. This is what we'll go with. (Using various tools, the bark is removed from the left side deadwood). Height has been added to the branches. Lots of torn...

You should always try to reduce a fraction until it can't be reduced anymore. To do this, look at your fraction and figure out the greatest number BOTH the numerator and denominator can be divided by. This is called the GCF - the greatest common factor. In the video, the problem you must solve is (15/18). What number can be divided into both 15 and 18 evenly? The answer is 3.
Photoshop is an excellent software program for adjusting and manipulating photos. Learn how to use Photoshop in this free graphic design tutorial from an image manipulation expert.

Photoshop is a great computer software program designed to help people manipulate images and text. Learn a few easy steps about Photoshop image manipulation from a Photoshop expert in this free video series.

As the week of the Game Developer's Conference hits the mid-point, we've already had some major announcements hit the AR space. The specific timing of these announcements are thanks in part to a conference within a conference called VRDC, aimed at VR, AR, and MR developers. And while the week is hardly over, the announcement that is still having a big effect on the developer population is the reveal of the Creator Portal for the long-awaited Magic Leap One device.

While Meta Company has agreed to a settlement in its lawsuit against a former employee and his company, they find the tables have now turned on them in the form of patent infringement allegations from another entity.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Roughly half of all Americans believe in extra sensory perception... Are you part of that statistic? Ever get the feeling you have a paranormal ability? You can investigate your psychic abilities and hone your skills with these tips.

Create works of art wtih Polaroid transfers, Polaroid lifts and Polaroid collages. Learn about manipulation of Polaroid photographs in this free photography lesson from a professional photographer.

It appears that the Project Aero 3D content development tool isn't the only augmented reality project that Adobe has in the works.

Perhaps it's a coincidence that the Vuzix Blade smartglasses look like the sunglasses that a police officer would wear, but a new partnership with an AI software company makes the wearable a perfect fit for law enforcement.

Theorem Solutions, a company that helps engineering and manufacturing companies reduce their costs, has taken the next step with their mixed reality technology. The company has now added their own app, called Visualization Experience, to the Windows Store for the Microsoft HoloLens

Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?"

As we all know, our attention spans are much shorter now that we're accustomed to getting information and news in tiny snippets via text messages, tweets, instagrams, and other constant updates.

Here is another cool photo manipulation you can do using Photoshop CS3. You can take a normal photo you’ve taken and really make it look unique by giving it harder edges and some more texture to the shot. Mix up your photos with this effect.

3D with one camera? With no computer manipulation? With one lens from some sunglasses? How is this possible? Pulfrich Time Parallax, my friends...

A tutorial on an Extreme Card Manipulation (XCM) cut / flourish.

With HoloLens 2 (hopefully) just around the corner, Microsoft has announced that it will no longer be providing any major operating system updates to the original HoloLens.
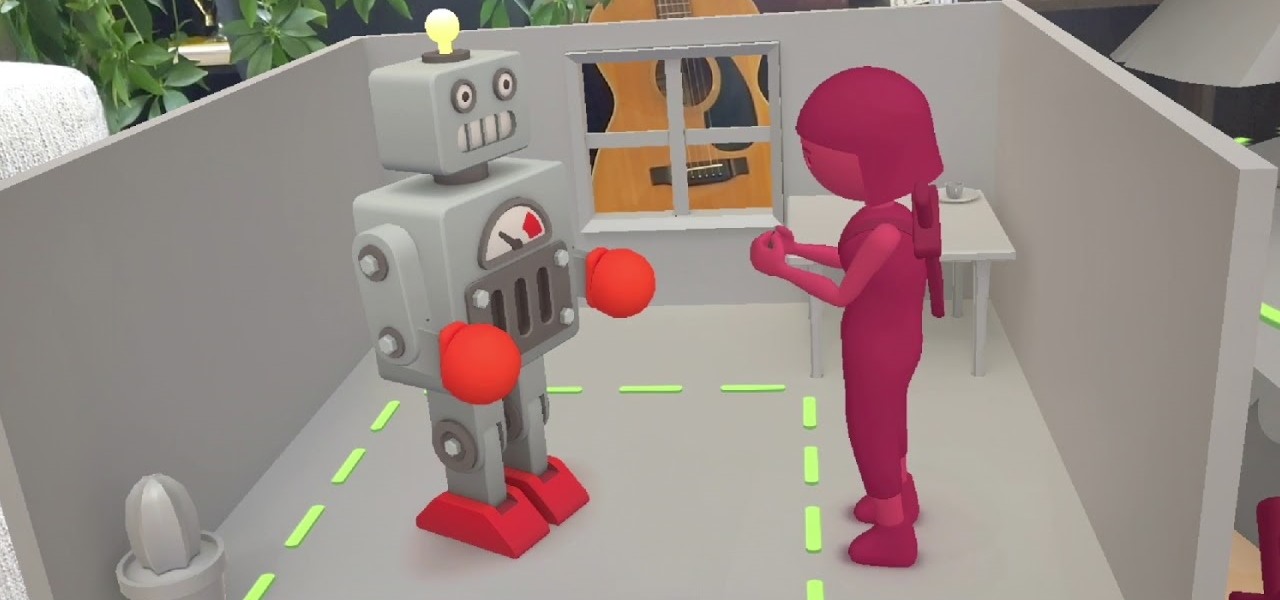
Snapchat made augmented reality selfie effects famous, with Facebook copying the feature across its mobile apps. Of course, others have followed, but their face tracking apps often pale in comparison to the original.
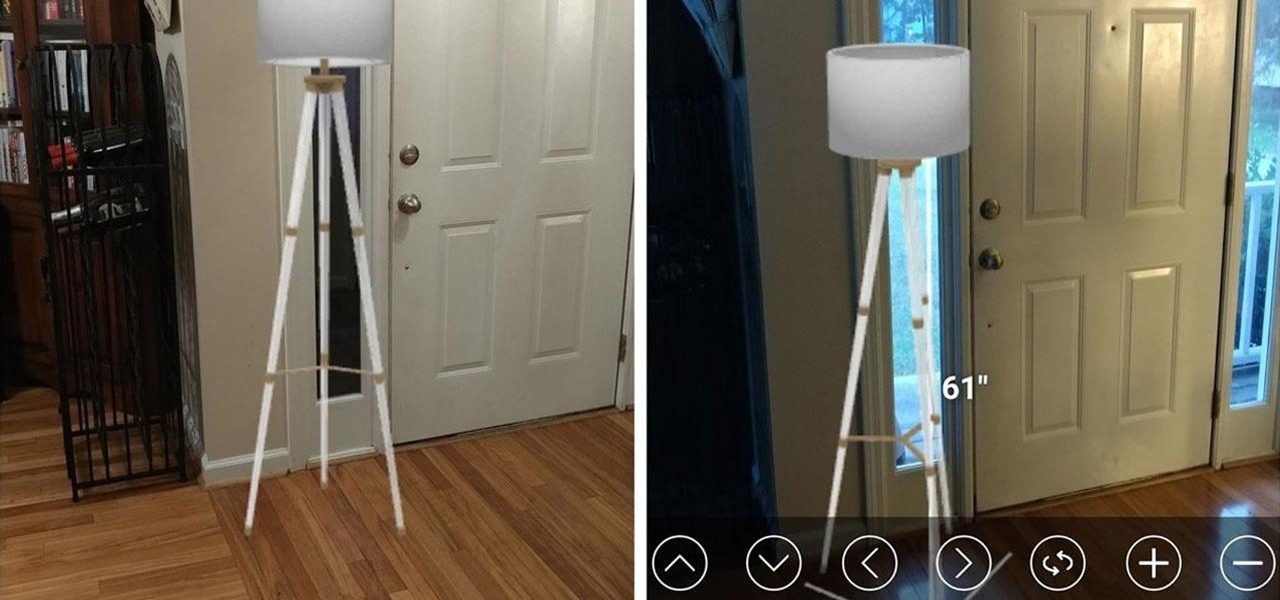
While some companies like IKEA and Lowe's zig towards ARKit to entice shoppers, Target has opted to zag to broader appeal with an augmented reality see-before-you-buy tool for its mobile website.
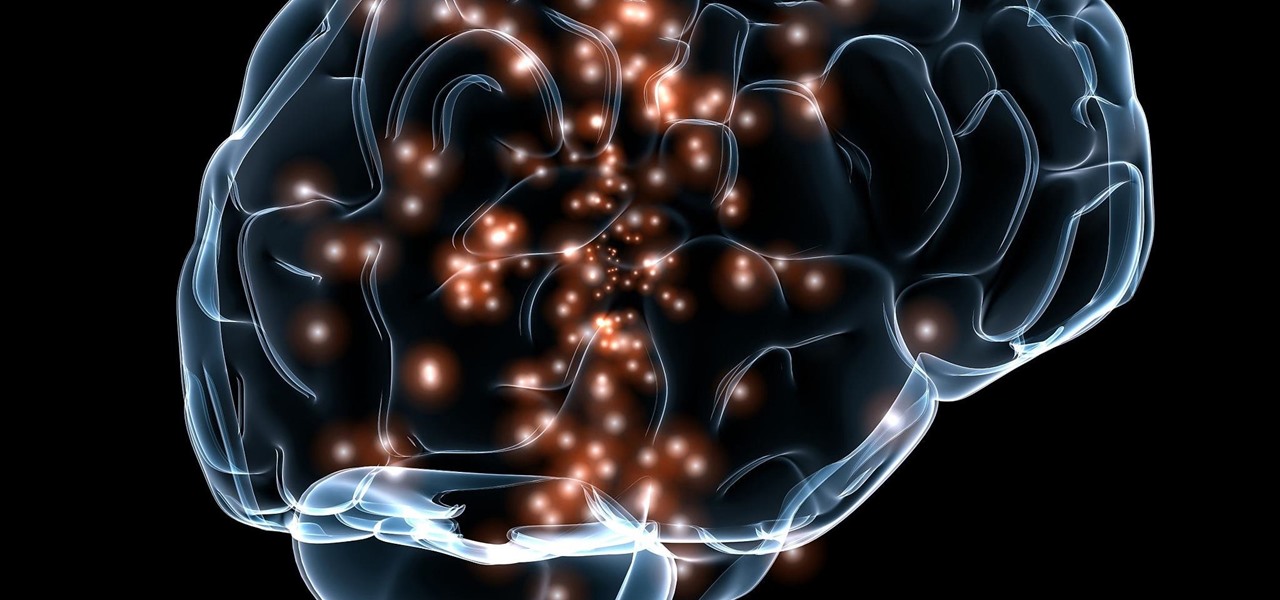
Despite mounting scientific evidence that viruses can cause changes in learning and memory, the reasons have remained elusive.

Today at the Unite '16 conference in Los Angeles, Unity's Timoni West and Amir Ebrahimi showed off its new virtual reality authoring and world editor, EditorVR, using the HTC Vive. Coming in December to Unity is a version of its editor that works inside a VR headset, which will change the way developers interact with the worlds they build—even if they aren't building for VR.

What's up guys! It's time to discuss strings in more detail. Review
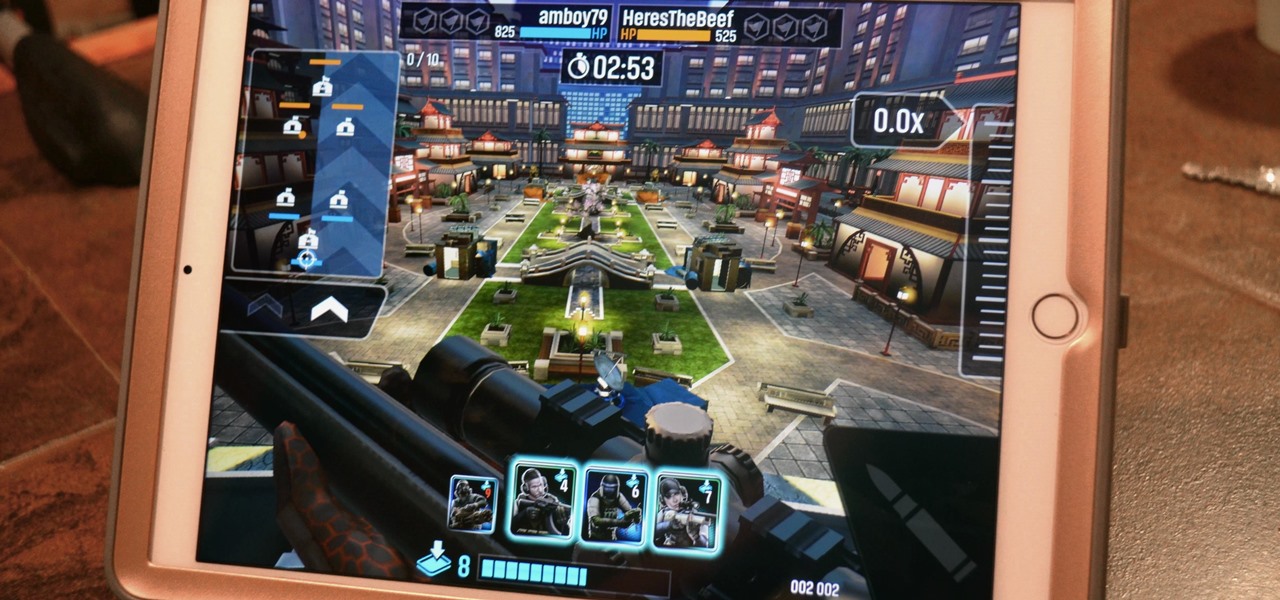
Tom Clancy games, like Rainbow Six and Ghost Recon: Wildlands, are famous for their realistic and immersive gameplay that focuses on covert, low-intensity warfare. Ubisoft now appears to be testing the overcrowded waters of mobile gaming with the release of ShadowBreak, and has soft released the game for both iOS and Android in Canada for further development, which means that with a little tinkering, you can play ShadowBreak in any country.

According to Electrek, Tesla CEO Elon Musk, in a covert conference call with a select few investors, commented in detail about his plan to have Tesla's Model 3 driving on the road earlier than we all expected.

Are you a messy burger eater? Ants and fruit flies invading your home? Hate drinking warm drinks? Find out the quick and easy DIY solutions to these problems with these 10 amazing tips and tricks for the summer.
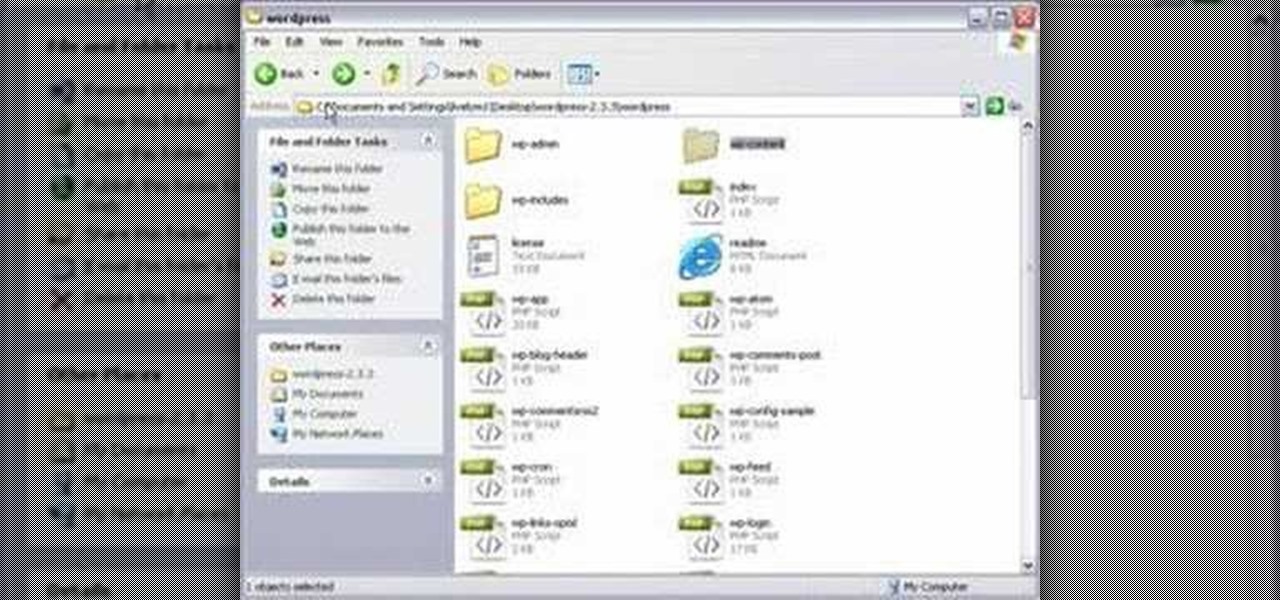
In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

In this next video tutorial, you'll be finding out how to beat the Xbox 360 and PS3 title, Singularity. The game takes place on a fictional mysterious island known as Katorga-12. It's a place where Russian experiments tooks place including an experiment titled E99, during the Cold War era. Fast forward to now, you're playing a Block Ops soldier who is sent to help investigate some strange things that are occuring at the island. After some digging up and gun fights, you acquire a powerful weap...

In 1987, two brothers, Thomas and John Kroll, began work on an image editing software, which was eventually acquired in 1988 and released to the world in 1990 by Adobe. That software was Photoshop 1.0, initially exclusive for the Macintosh platform. Over the years, Photoshop became a great wizard of image editing and gained application rockstar status.

Beloved toy maker Lego is returning to the realm of augmented reality, this time with an experience that explores supernatural fun.
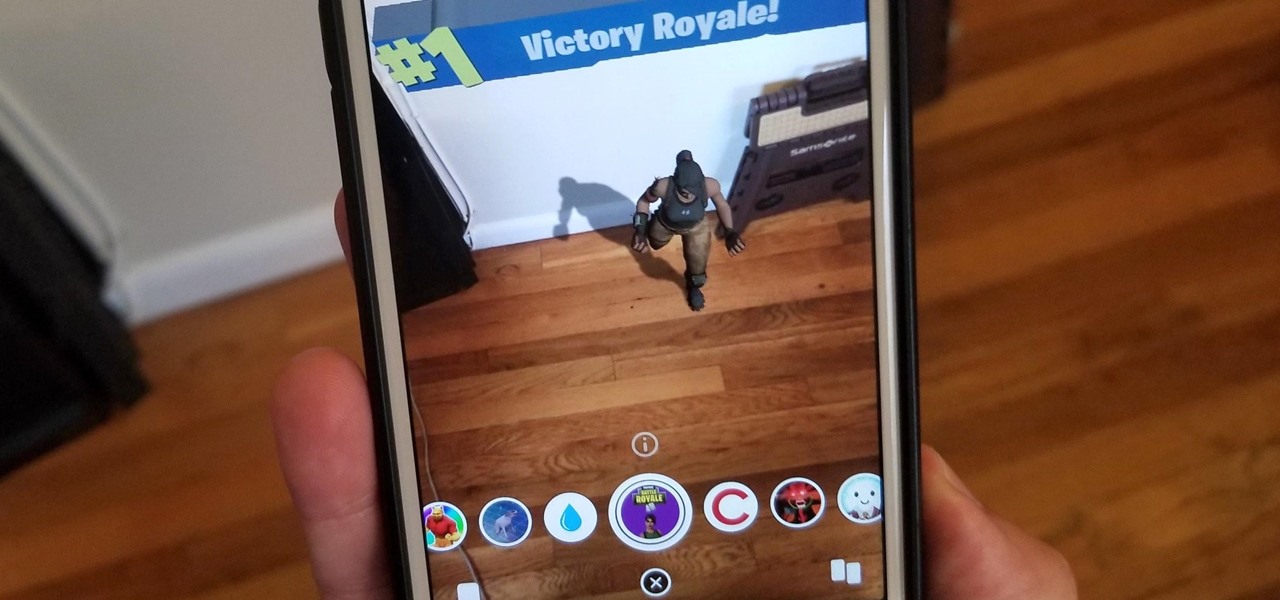
With April coming to a close, there's a fresh group of augmented reality Snapchat lenses you should try out while they're still hot. We've got a prank lens, gamer-oriented ones for Fortnite and Fallout, and ones for the memesters out there.
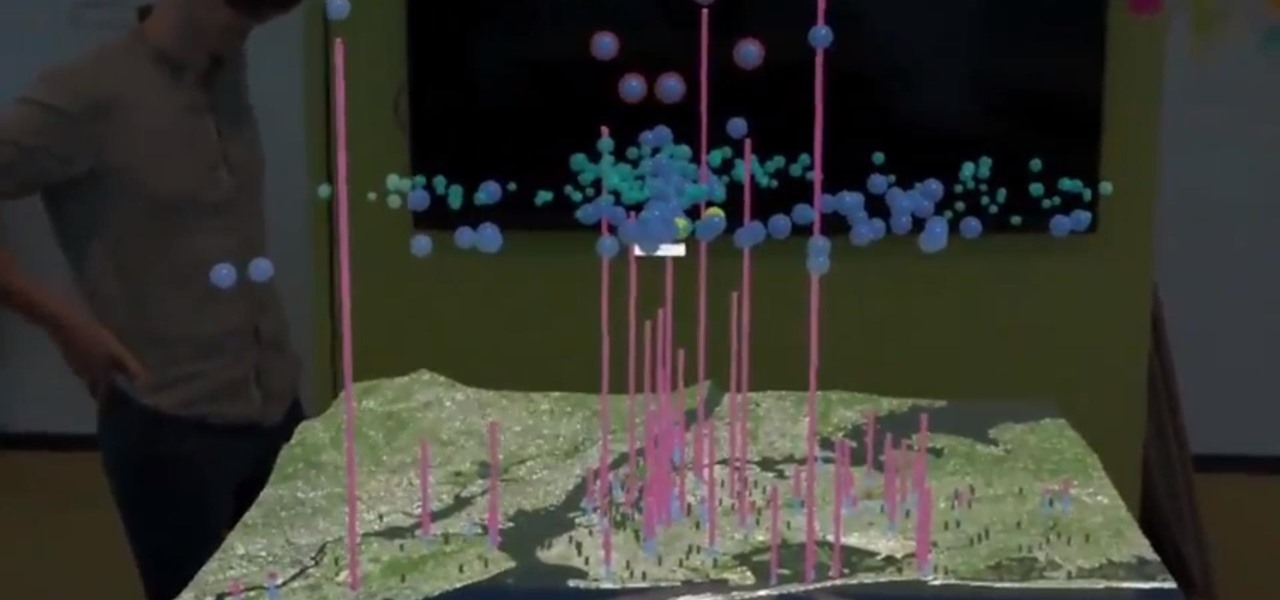
This month, the power of artificial intelligence will be coming to more augmented reality developers as a leader in the game and 3D software development space and a major force behind the current school of cloud-based AI have officially announced a new partnership.

Have you ever wanted to control a swarm of robots? Well, now you can! Robotics researchers at New York University (NYU) have created an app which controls 'bots from your smartphone, using augmented reality. This AR app would certainly come in handy when you want to make a coffee from the comfort of your couch, but let's not get ahead of ourselves!
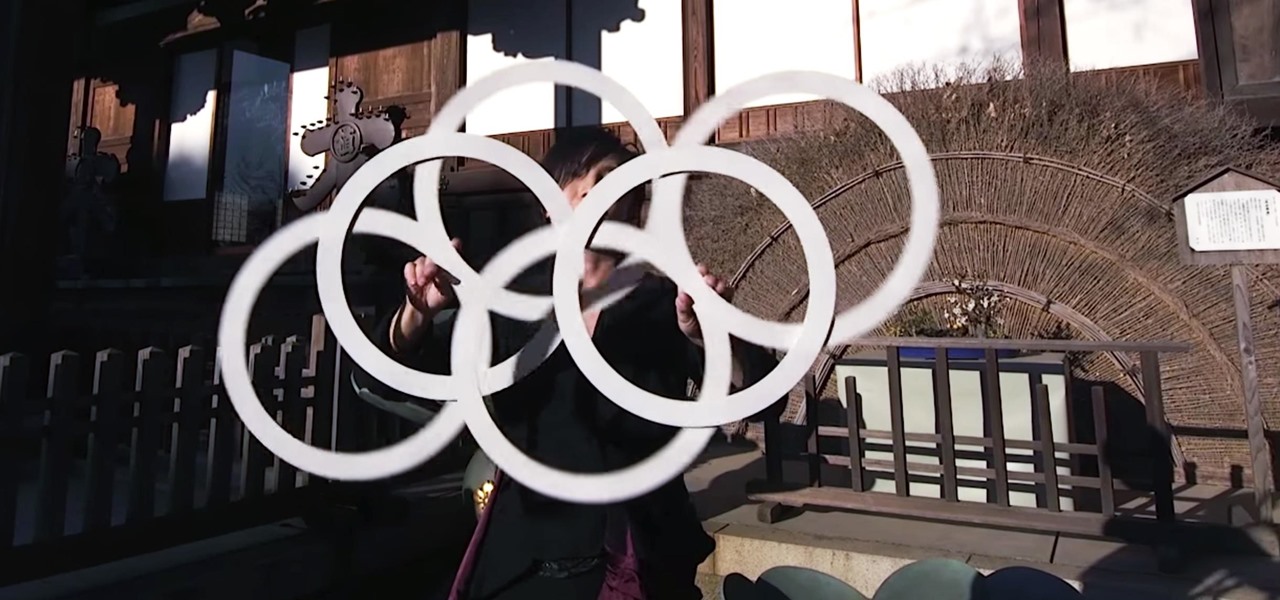
Heads up: the following videos and GIFs will definitely cause you to zone out and lose focus on whatever it is you're doing.

Hello again, folks! I'm back with another (final) guide on runtime crypters which is an extension on my previous runtime crypter guide. If you have not read it yet, I highly recommend that you do since the fundamental theory of the PE format. Again, this will be a Windows-specific guide, so I'll repeat this: If you're a hater and cringe at the slightest sound of Microsoft's grotesque baby, feel free to close this tab, delete your history, exit your browser, pour some oil onto your machine and...

Hello again! In this tutorial, we are going to go over something called "operators" which will help us build upon conditions of control structures and also some variable manipulation. Without further ado, let's dive in!
Hello everyone! I'm glad to post my first tutorial and hope you will appreciate it.