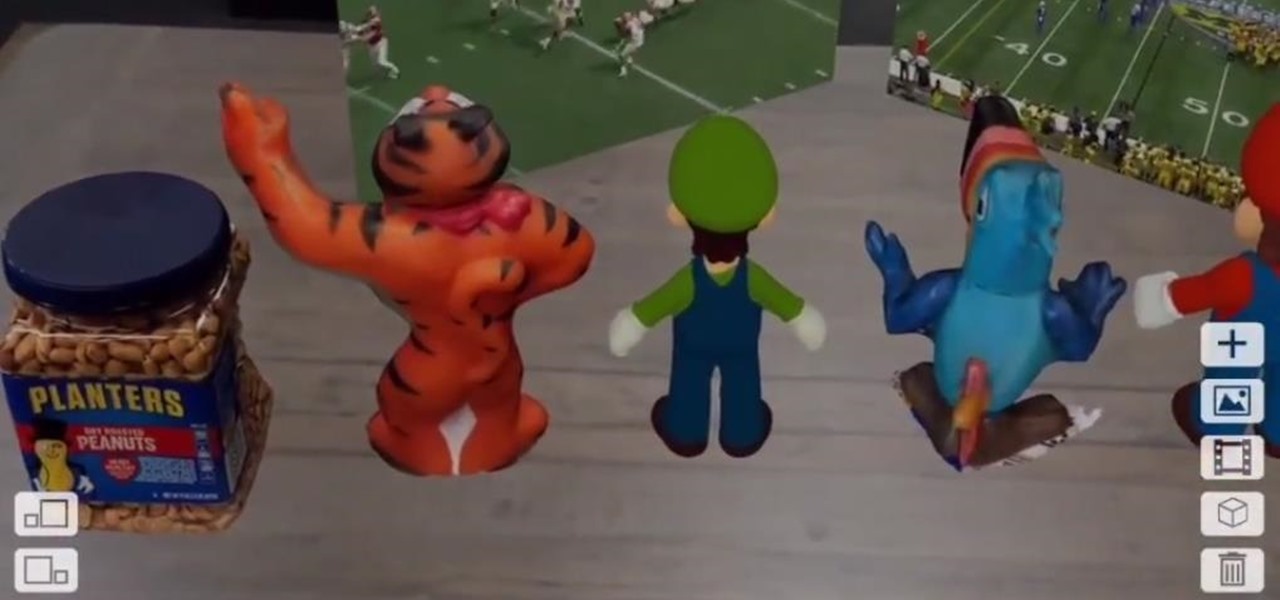Google, the company that rules the internet, is now testing a method to leverage its machine learning with its ubiquitous presence on mobile devices. The new model they're employing is called Federated Learning, and it hopes to apply artificial intelligence to Google's services on Android without compromising user privacy.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.
Today, BitTorrent Inc. released the SDK for uTorrent Apps, which will allow software developers from around the world to create Apps for uTorrent, the popular bittorrent client. This video will show you how to download the SDK, install it on your computer, make an app, view that app in a browser, and then package the app and view it within uTorrent without compromising uTorrent's famous lightness. This is a big day for bittorrent fans around the world; download the SDK and start making uTorre...

When the weather gets warmer you have two options: Tie your hair up into a super boring ponytail, or become more adventurous with your hairstyling and create a romantic updo that gets hair out of your face without compromising style.

Well, you've shot one too many compromising photo and it's time to wipe your iPhone photo library. But, for some reason, this isn't the easiest thing to do. Well, with this how-to video, you'll learn how to get rid of those 212 photos of your niece in her sailor suit you thought looked adorable. Those cat climbing photos. Gone. That girl/boy you were recently dating. Bye bye. Delete at will and clear your iPhone photo library.

In this tutorial, learn how to disable the annoying UAC or User Account Control on your Windows Vista computer. This clip will show you how to do this without compromising your security.

This video shows you how to change the background color and watermark in your Word 2007 document. Both settings are found on the Page Layout tab. The background color can be chosen from a wide palette. The most frequently used colors are immediately applied to the current page as a preview. You can also choose to add a fill effect, like a color gradient, by clicking the Fill Effects item in the Page Color list. The watermark feature allows you to add either a predefined notice, an image or a ...

If you've ever participated in a Anonymous protest against scientology or celebrated Guy Fawkes day, you probably know that drinking through a Guy Fawkes mask is tough, especially if you're keeping your identity a secret. Watch this video to hear an Anonymous member explain how to drink water without compromising your anonymity.

You know he cares more about you than his precious video games; he just needs a little help showing it. This video gives tips for luring a boyfriend away from video games, by compromising his love of competition and skill-based games with other activities you can enjoy together as a couple. Watch this video dating advice tutorial and learn how to compete with a video game for your boyfriend's attention.

Lee T. Dresang, MD of the University of Wisconsin School of Medicine and Public Health from the Deaprtment of Family Medicine give a discussion and demonstration of suturing techniques. Before beginning a procedure, you will need consent. One should irrigate lesion before beginning. A simple interrupted suture is easy to learn and fast, but unable to withstand stress. Vertical mattress sutures provide a good eversion of skin edges, closure of dead space, and strength, but also lead to scarrin...

Learn how to do cable squats. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn how to do a low single cable squat power cross punch. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do side to side pop push ups across a step. Presented by Real Jock Gay Fitness Health & Life.

Got a bag of old t-shirts that have been with you too long that you don't want to throw them away, but are piling up too fast that you're tempted to toss them on the counter at the Salvation Army? Keep your old t-shirts by your side without compromising storage space by making tarn.

Learn how to do a single cable scissor squat and row. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do single cable squats and rows. Presented by Real Jock Gay Fitness Health & Life. Benefits

Learn arm awareness in yoga without being in compromising and difficult poses. In this yoga how-to video Kira Ryder plays with using the cactus arm action to assist in creating the shoulder blade support in urdhva dhanurasana, upward facing bow pose, sometimes called wheel. Watch and learn how to work the cactus action movement to feel your arms while practicing yoga.

In this video tutorial, Better TV shows you how to take a complicated fish dish and make it your own -- without compromising flavor. You will need: parchment paper, salmon fish, tomatoes, eggplant, potatoes, squash, raisins, zucchini, sugar, honey, kalamata olives, roasted peppers, basil, green olives, onions, garlic, parsley.

Forget circle and square-shaped wedding cakes - pillowy clouds of icing and cake are the way to go! Be original without compromising your unique style by learning how to bake and decorate this lovely stacked pillow cake.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Apple's macOS operating system is just as vulnerable to attacks as any Windows 10 computer or Android smartphone. Hacker's can embed backdoors, evade antivirus with simple commands, and utilize USB flash drives to completely compromise a MacBook. In this always-updated guide, we'll outline dozens of macOS-specific attacks penetration testers should know about.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

The rumor that the iPhone 8 will ship with 3D camera system is not a new one, but a new analysis by Morgan Stanley's Charlie Chan lends credibility to the speculation. Now, it appears more likely than ever that Apple's next iPhone will ship with 3D capabilities, increasing potential for AR and VR integration in the future.

All you paying Spotify users are about to get another exclusive privilege besides getting out of all those annoying "Ever wonder what it would be like to have Spotify premium?" ads. The Sweden-based company is looking to lower the royalty fees they have to pay to major record labels for their music, by compromising on their policy that all their music be free to paying and nonpaying users. Spotify would for a limited time restrict access on major album releases to their paying subscribers.

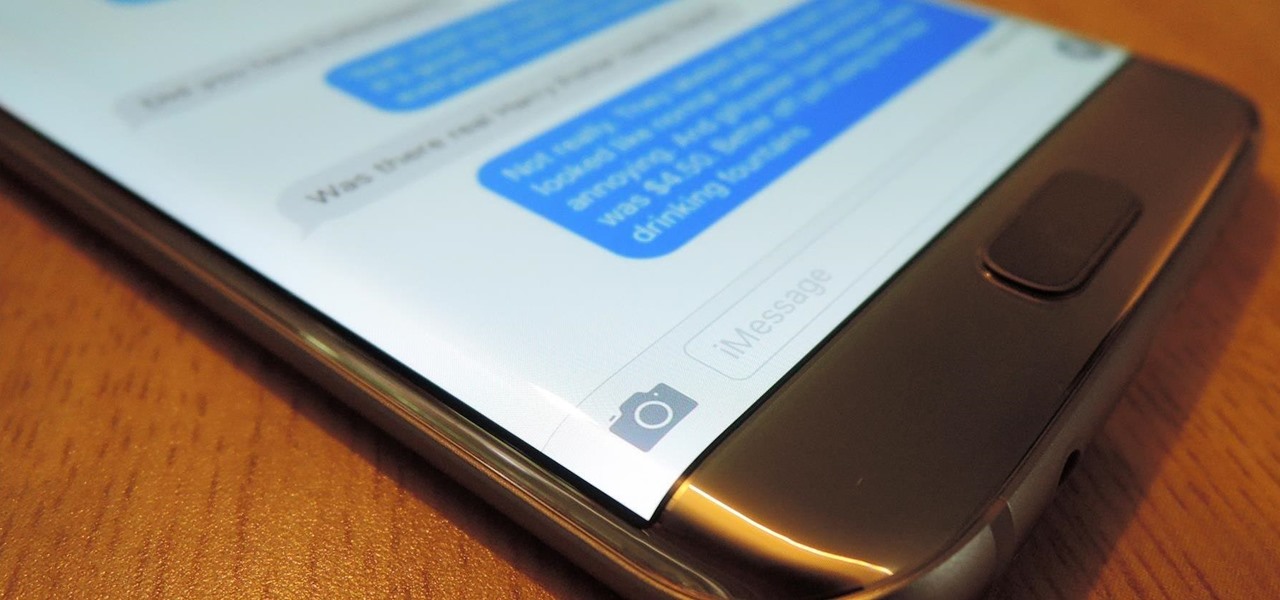
Android phones may soon be able to send and receive iMessages thanks to a new open-source app called PieMessage.

Since it was released last fall, Super Mario Maker has offered us a glimpse into the minds of some of the most evil people on the planet. The game, for Nintendo Wii U, lets players create their own Super Mario levels using a deep list of objects, enemies, and green pipes, which can then be uploaded for anyone to play.

The idle screen for the Chromecast is certainly beautiful. Full of many high-definition pictures taken of various parts of the world, it's almost a shame that we have to dismiss this screen in order to cast content.

Personally, I know life would be a lot easier if the people in it could just read my mind. Since that technology is currently unavailable, it's comforting to know that your air conditioner can be your personal telepathist with Sensibo.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

As we settle into our new normal, this extra time provides a perfect opportunity to learn new skills. Speaking a foreign language is a great way to expand your cultural boundaries while also training your brain. Not only will you pass the time more effectively, but you'll also be doing something positive for your health.

You might think you need to buy a thousand dollar phone to get a great experience while streaming movies and TV shows from services like Netflix, Hulu, and YouTube, but that's just not true anymore. While phone prices keep rising and the midrange segment now ranges from $300–$500, there are still cost-effective options that come with top-notch displays and media features.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

When explaining augmented reality to the uninitiated, Pokémon Go is often cited as an example. For all its popularity, though, many players would recommend disabling the AR capabilities in catching Pokémon.

One of the byproducts of the success of Pokémon Go was the viral images that made the rounds on social media of people putting Pikachus, Charmanders, and their brethren in compromising positions. Snapchat has a similar claim to fame, most recently with the inexplicable popularity of the dancing hotdog.

Ideally, wine would stay as perfect and delicious as the day it was first uncorked forever. But, thanks to a pesky process called oxidation, re-corked wine (no matter how you do it) pales in comparison to a fresh's bottles original magic.

Most people are familiar with the fact that vinegar adds sourness to a dish, in varying degrees from light acidity to puckering acid. However, vinegar can also be used in lieu of salt when seasoning the final touches to sauces, soups, and stews.

When Lollipop was released, Android's lock screen got a huge makeover. But most of the changes were made for aesthetic purposes rather than functionality.

Samsung's not one to make drastic changes to what already works. They've continued on with the IP68 rating under IEC 60529 first given to the Galaxy S8 all the way to the the Galaxy Note 10. If you're a little confused as to what this rating means, don't worry, it's actually pretty simple once you get to the meat and bones of it.