Keeping secrets out of the wrong hands warrants desperate measures—or maybe just sensical. If you have a secret, the best way to protect it is with a code—and the best way to transfer that secret message is via an electronic telegraph system. This video will show you how to make your own homemade electronic telegraph machine, so that you can send those encrypted Morse code messages to your friends without fear of prosecution.

QR codes are everywhere, from product packaging to airline boarding passes, making the scanners that read them a juicy target for hackers. Thanks to flaws in many of these proprietary scanning devices, it's possible to exploit common vulnerabilities using exploits packed into custom QR codes.

Windows Powershell is a powerful but unwieldy tool for web developers, with which the PowerGUI interface is a great means on interacting. This video will show you how to use SnippetManager, recently declared "Best Add-On" in "PowerGUI Challenge 2010", to create and manage code snippets to use in your projects.

If you are the proud owner of a Dodge Neon with a check engine light on and it's showing error code P0141 on your scanner, you probably need to replace the rear oxygen sensor. This video will show you how to do that as easily as possible.

If you've done major work on your engine recently, you may find yourself with error code P1345, which means your timing is off. In this video you'll learn how to use a lab scope to both diagnose and fix a distributor timing problem.

Error code P0300 is one of the most infamous in auto maintenance, indicating random misfires in the engine. This can mean several different things, and in this video mechanic Scotty Kilmer will teach you how to figure out where the problem is and fix it.

With the growing popularity of digital downloads, it's important for aspiring musicians to have some sort of download available of their music. If you're an unsigned musician, selling your music on iTunes might seem daunting, but it's actually very easy! Learn how to do it in this video.

Automotive computers and error codes are a blessing and a curse for mechanics. If your 2000 Ford Taurus shows error code P0171, that means the air fuel mixture is lean. This can be caused by a number of things, and this video will show you one easy thing to check for that might save you a trip to the shop.

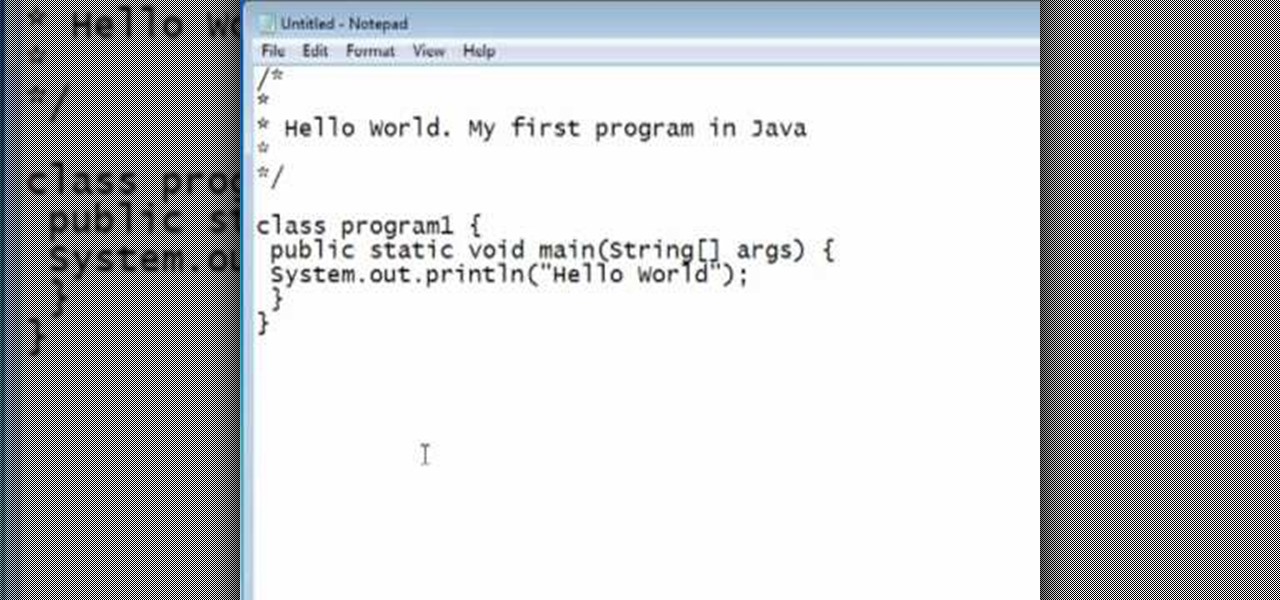
You should already have the JDK installed on your computer, and you should already have optimized your computer's settings. See How to install the Java Development Kit to start programming to do that if you haven't already.

Almost every video on YouTube is embeddable. Only those that choose not to feature an embed code or non-embeddable. This embed code can be accessed directly on the video page of the video that strikes you. If you want to embed it, simply click the "Embed" button underneath the video player to generate the embed code. You can tweak this embed code to better serve you and your WordPress blog or website. It will generate the code automatically, and you can grab it and use it for yourself. This c...

Kristin Holt is here show you some cheat codes that will make defeating the criminal underworld of Gotham City a downright breeze in LEGO Batman: The Videogame.

This Adobe After Effects tutorial shows you how to create the Matrix raining code text effect. Learn how to use this motion graphics and 2D effects compositing software and the automation options available to easily create a Matrix raining code effect in After Effects.

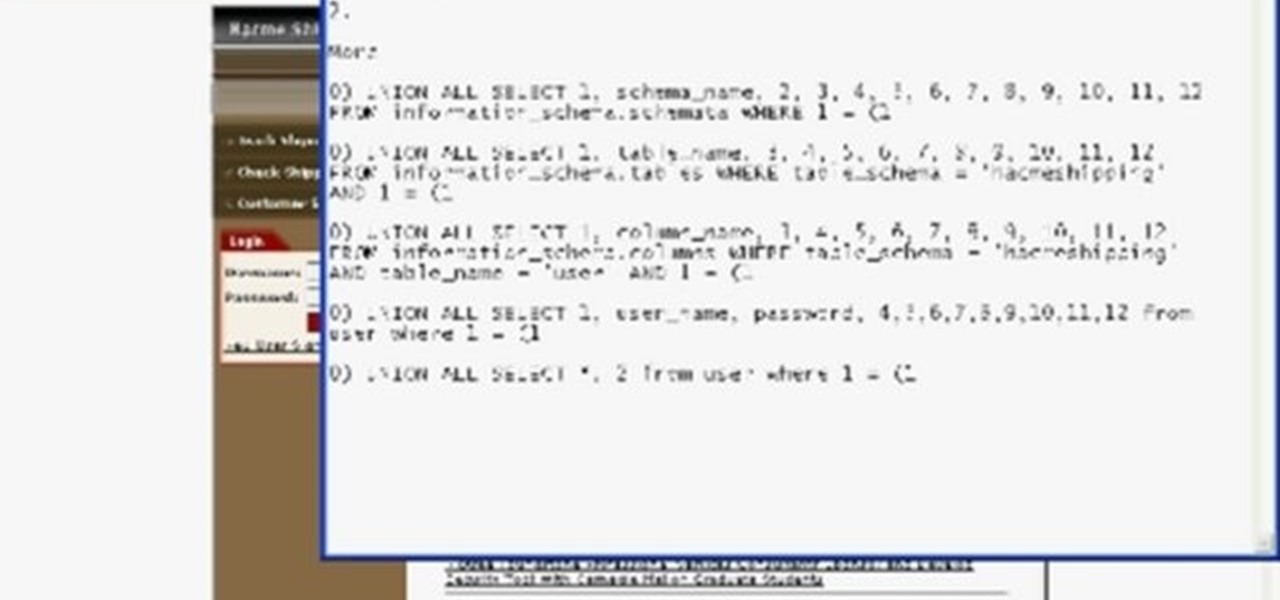
Foundstone Hacme Shipping is a web-based shipping application developed by Foundstone to demonstrate common web application hacking techniques such as SQL Injection, Cross Site Scripting and Escalation of Privileges as well as Authentication and Authorization flaws and how they are manifested in the code. Written in ColdFusion MX 7 using the Model-Glue framework and a MySQL database, the application emulates the on-line services provided by major shipping companies. This video will get you st...

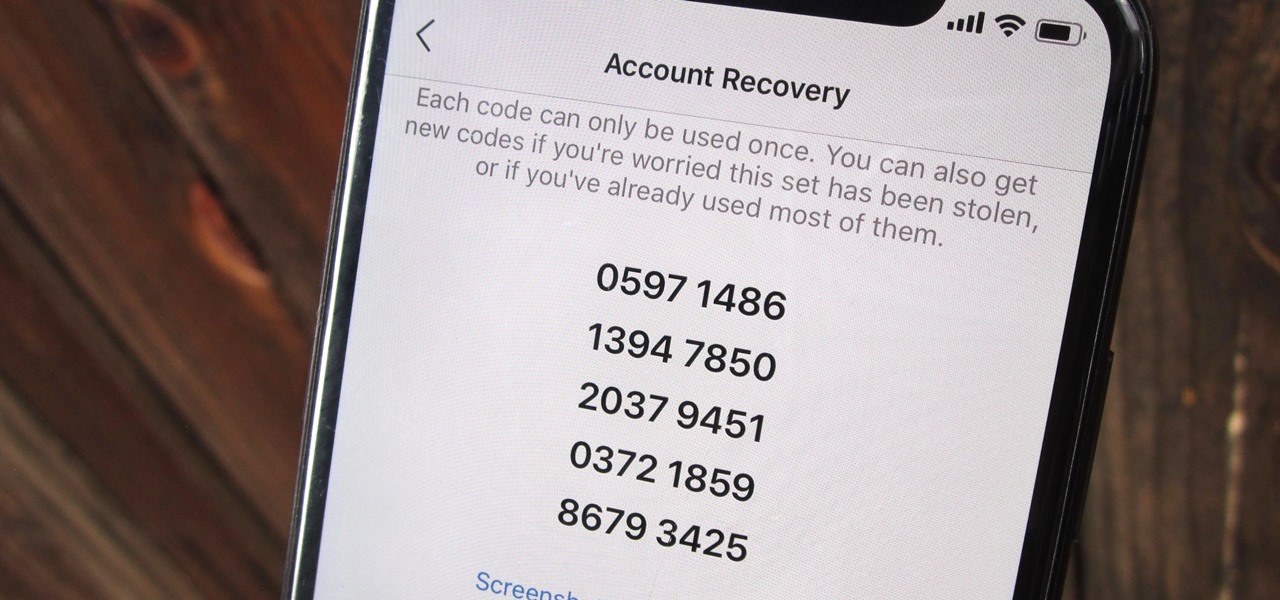
Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

From Instagram bot farms in China all the way to vending machines in Moscow that promise to sell you fake followers — the Facebook-owned empire is attracting the attention of the world around. When it comes to Russia especially, the country seems to be developing a little crush on the glorious IG queen.

Why should console players have all the fun? This tutorial shows you how to enter in cheat codes when you're playing Grand Theft Auto: San Andreas on the PC. Get everything you can as an XBox or Playstion player with these codes!

Make sure you watch the very bottom of the video, that is where the cheat codes will appear. Poptropica has the ability to use codes to get some extra goodies, and this video demonstrates a few of the better ones for you.

You can use the cheat codes "fastfire," "moreammo," "pointer," and "nohit" to get you a higher score when you're playing Gun Blood, a simple Flash game about gun duels. There are more codes, though, so watch the video and see what you like best!

In the world of coding you want to be clean and efficient. A great way to do this is with an IDE, such as Netbeans IDE. If you're ever working with a team, knowledge of a great IDE is a must. Check out this PHP coding tutorial and up your knowledge base.

If you're looking to break into Call of Duty 4, you can use the mod menu to access the cheat codes and give yourself all kinds of goodies. This tutorial shows you how to get to the menu and use these codes for yourself.

If you've already enabled the developer console, you know you can access the cheat menu in the game and enter codes to give you crazy cool stuff. But what to get? Here's a list of codes that you can use to give yourself immortality, kill every enemy in your immediate area, give yourself unlimited money and, of course, play in God Mode!

This tutorial shows you first how to create an object using Adobe Flash CS3, and then you're shown how you can use ActionScript code to make them spin and rotate. You can even cause the spinning to speed up using the right code!

If you have trouble emptying your trash on your Mac computer, you will need to launch the Terminal first, in order to begin troubleshooting the issue. The trash will often fail to accept items, if it believes that a program or object is in use. Move the application that you can't delete onto your desktop. Add a line of code to the terminal. Add the application to the code, by dragging it to the code. It will ask for your code. Enter your password. Press enter. You will need to use a Sudo code...

An easy way to view your CSS code of your website is through the Firefox plugin called Firebug. It's really helpful, especially if debugging your code. Just remember, you cannot save anything with Firebug, it's only for viewing code and adding codes for previewing webpages.

This instructional video shows you how to make a RSS ("Really Simple Syndication") feed using the free program RSS builder. RSS is a script that can be put up on a website that other users can subscribe to in order to get notified when the website gets updated. The xml code behind creating RSS feeds is explained. The code should be entered as shown and the file should be saved as "feed.xml" and upload it to a web server. Go to the URL mentioned, download and install RSS builder. Launch the pr...

Imagine that every time you print a document, it automatically includes a secret code that could be used to identify the printer -- and, potentially, the person who used it. Sounds like something from a spy movie, right?

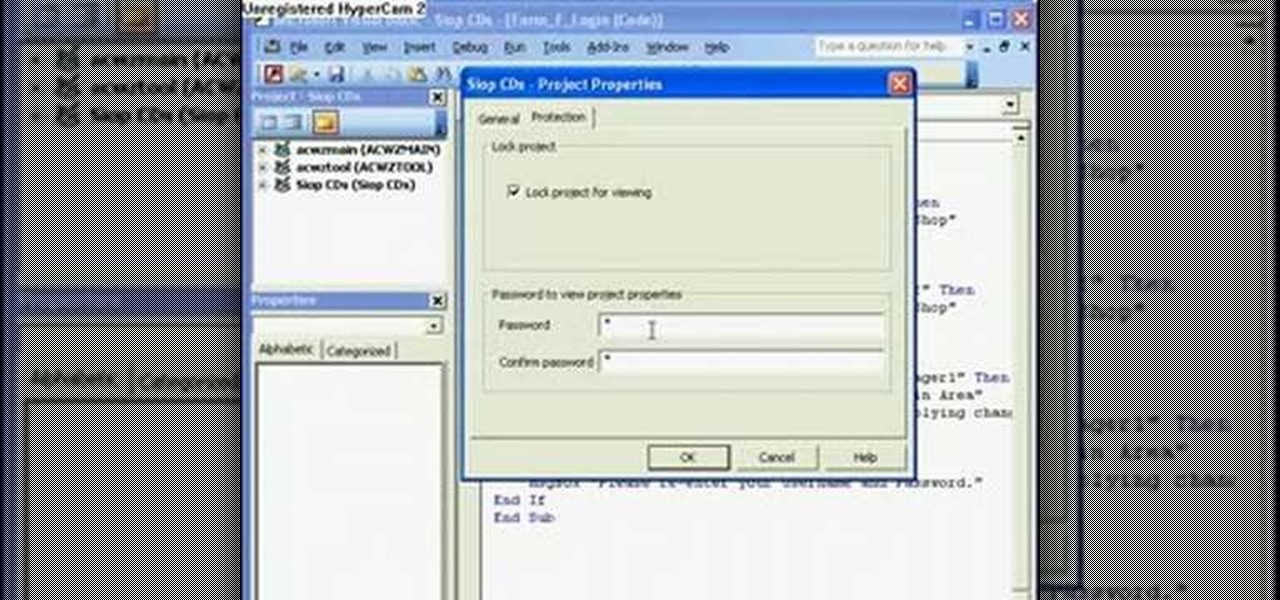
The Microsoft Office Access 2007 relational database manager enables information workers to quickly track and report information with ease thanks to its interactive design capabilities that do not require deep database knowledge. In this Microsoft Access video tutorial, you'll learn about protecting your VBA code from snoopy little trolls. For more information on keeping your VBA code secure, watch this MS Access how-to.

In this tutorial, Mike Lively of Northern Kentucky University demonstrates how to create a 3D clickable Carousel in Adobe Flex 3 and Papervision3D. All code can be downloaded from Google Code at:

This simple Adobe Flex tutorial shows how to download source code from Google Code and get it running in Adobe Flex. If you are new to programming and building applications with Adobe Flex, this project is a great way to practice or get started learning about Adobe Flex.

"There are 10 types of people in the world," the old joke goes, "those who understand binary, and those who don't." In this tutorial, you'll learn how to read and write binary code. With this neat tutorial, you'll join the former group. Make sense of the 1s and 0s of binary code, the symbolic atoms of machine language, with this how-to.

Learn how to enter code breaker codes on the PCSX2 Playstation 2 emulator for the PC. Entering these codes will allow you to cheat on emulated PS2 games. YOu will need to use a variety of other programs like Daemon tools to do this.

Wouldn't it be nice to know how many people actually visited your site each day, and how long they stayed there? Google Analytics is a great, free utility from Google that will tell you just that and so much more. In this clip, the Web Guru will show you how to use this program, generate and install an HTML code onto your site so that you can keep track of your visitors and demographics. This is a fantastic tool for advertising purposes and so you can see which content is working best for you...

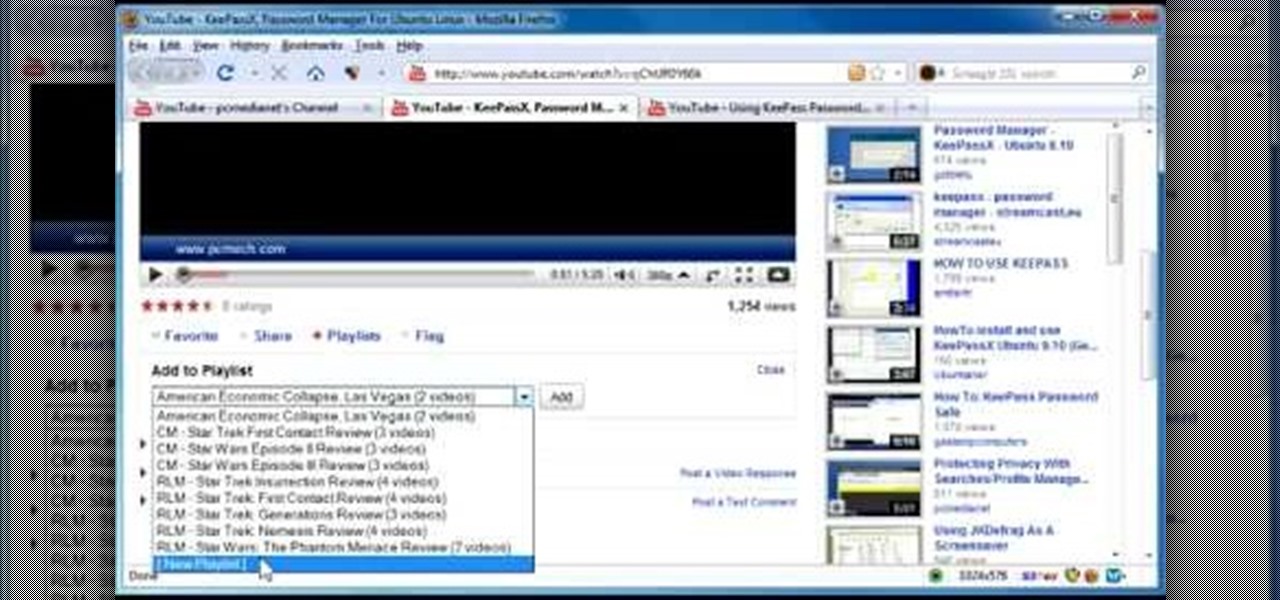
In this video, the author shows how one can make one's own playlists on YouTube, and also get the code which can be embedded on one's website or blog. All one has to do' according to the author, is to first load all the videos which one wants in a playlist and pause them. Then one has to click the 'Playlists' option under the video pane. In the drop-down list which opens, one can choose one of the existing playlists or create a new one, and then, simply click the 'add' button. This action has...

Want all of the GTAIV cheats? This is a Grand Theft Auto hack like you'd never believe. Get the cheat codes for every glitch and cheat in the game.

Mike Lively of Northern Kentucky University shows you how to create a light switch in Second Life with scripting. Part 1 demonstrates how to create a prim switch which turns on (brightens) a prim in Second Life. Part 2 goes through the Light Switch code line-by-line and adds a rotor to the light switch. The code is provided for free distribution on Google Code at

EternalBlue was a devastating exploit that targeted Microsoft's implementation of the SMB protocol. Metasploit contains a useful module that will automatically exploit a target, as long as it's vulnerable. But what if we wanted to exploit this vulnerability without Metasploit holding our hand? It can be done using a Python file to exploit EternalBlue manually.

Particular vulnerabilities and exploits come along and make headlines with their catchy names and impressive potential for damage. EternalBlue is one of those exploits. Originally tied to the NSA, this zero-day exploited a flaw in the SMB protocol, affecting many Windows machines and wreaking havoc everywhere. Here, we will use EternalBlue to exploit SMB via Metasploit.

There's actually more to the dialer screen on your OnePlus than meets the eye. Besides its obvious purpose of calling people, there's a vast array of secret codes that you can input to troubleshoot your device, in addition to revealing important information, making anonymous phone calls, and so much more.

One downside to iOS 11's awesome built-in QR code scanner in the Camera app is its only been live for a short while. In its short life, there has already been a security vulnerability discovered that was an issue for at least the last 4.5 months, but Apple has finally patched this weakness with its iOS 11.3.1 update.

The default Camera app got a few more tricks up its sleeves when iOS 11 was released, and the best addition by far was the inclusion of a built-in QR code reader since that meant no more third-party apps just for QR code scanning. However, Apple's built-in QR code scanner did have a vulnerability at one point that would let hackers direct you to a compromised website without you even noticing it.