
How To: Fix Mugen music problems
This will show you how to fix any music or sound problems within Mugen - the custom PC game engine. Plugins to get:


This will show you how to fix any music or sound problems within Mugen - the custom PC game engine. Plugins to get:

This tutorial was written with Windows 7 in mind, but the principle applies to all versions starting from 7.
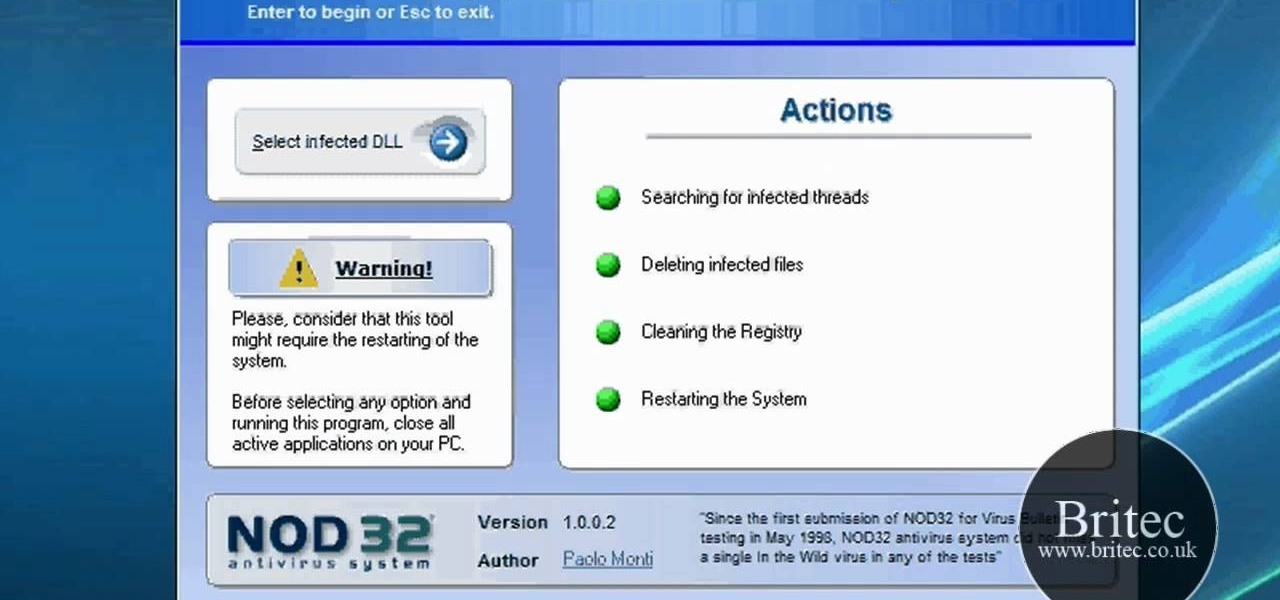
In this clip, you'll learn how to use the ESET UnDLL tool to rid yourself of poisoined DLL files. It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.
Looking for instructions on how to fix a missing or corrupt hal.dll error on a Windows PC? It's easy! So easy, in fact, that this home-computing how-to from the folks at Britec can present a complete overview of the process in just over five minutes. For more information, including step-by-step instructions, take a look.

In this video tutorial, viewers learn how to export MP3 with Audacity. Users will need to download the Lame_enc.dll encoder. The download link is located in the video description. Once downloaded, open Audacity and find the song that you want. Once you have found your song, simply drag the song into the program. Now click on File and select Export As MP3. It will then ask you to Lame_enc.dll file. Click on Yes and locate the file. Now wait for your file to finish encoding. This video will ben...
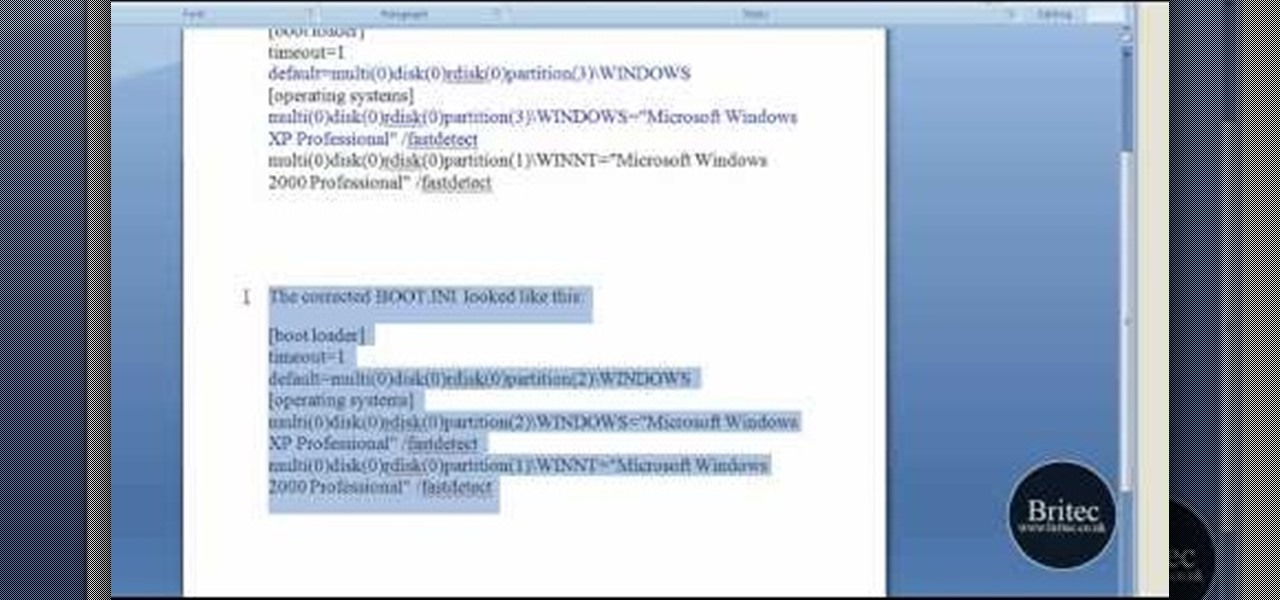
If you've received the "hal.dll is missing or corrupt" error message from your Windows machine, then you're in luck! This video will show you how to correct that problem with the Recovery Console tool that comes with the Windows 2000 and XP CDs.

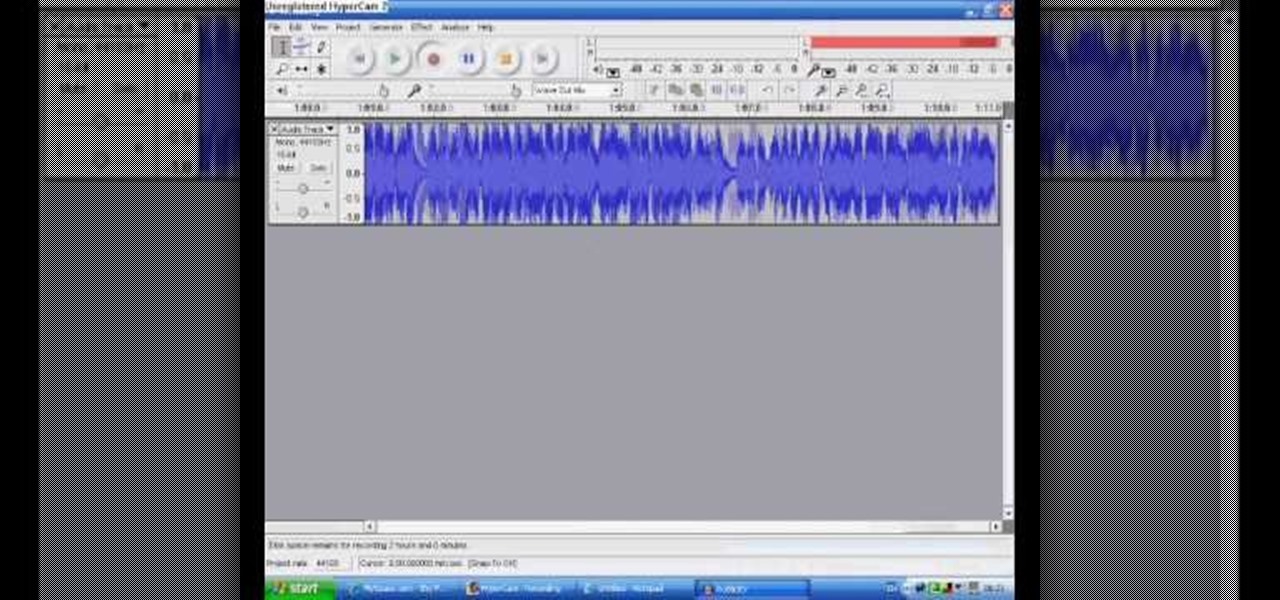
The video shows us how to use audacity to record audio. Firstly you need to have the software audacity installed in your system and for that Google and search for 'audacity' and after that you get a link to save and install the software. Once the installation is done, open audacity and on the drop down menu the default is set to microphone, change that to stereo mix and copy my settings. Once this is done we will be recording the audio. Go to a site like youtube and press the record button in...
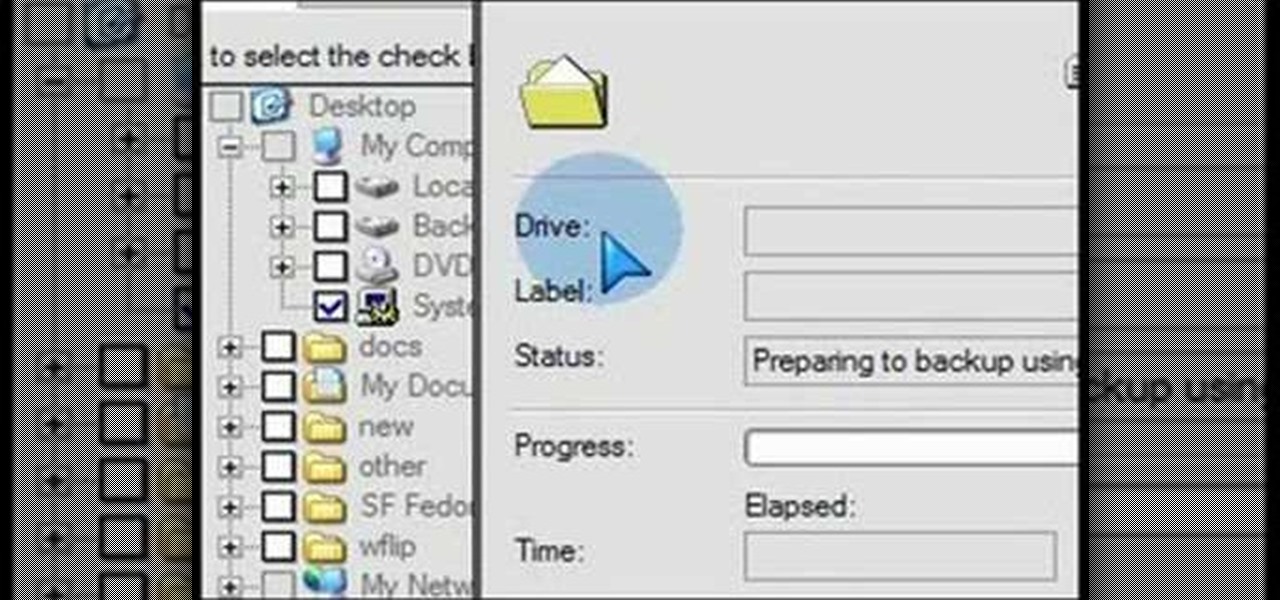
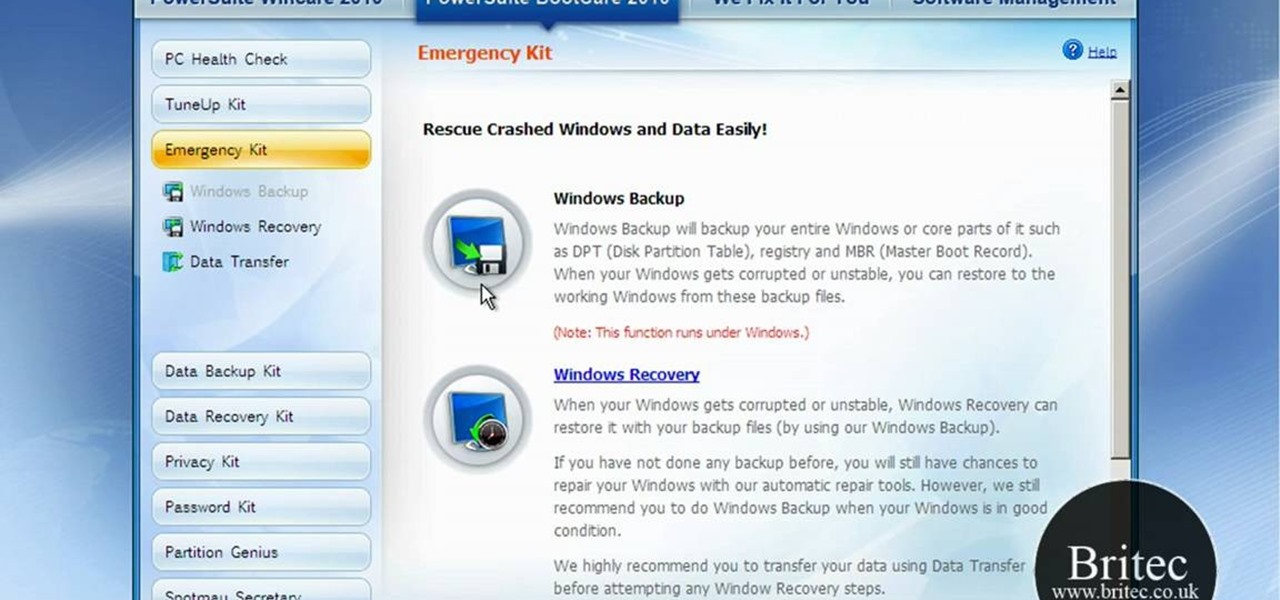
What if your PC crashed? What would you do? Everything would be gone, erased forever, and you'd be in a horrible and stressful situation, especially if all of you homework or work files were stored on your Windows PC. But why even enable yourself to be in that situation? In Windows XP, it's not uncommon to have experienced a corrupt registry or a missing DLL file, or having a blue screen of death.
Wondering how to create an app bundle in Mac OS X? In this two-part video tutorial series, you'll learn how to create an application that is completely self-contained and is drag-and-droppable/relocatable. Frameworks, PlugIns, and Resources are embedded in the .app bundle, thus avoiding the need for installers and avoiding issues like dll-hell. There is also a quick demonstration on how to enable Universal Binary building at 15:46. Take a look!
In this video tutorial, Chris Pels will show how to use the aspnet_merge.exe utility to combine assemblies that have been compiled using the aspnet_compiler.exe utility. First, view the output of the ASP.NET compilation process to learn what assemblies are created. Next, learn the mechanics of using the aspnet_merge.exe utility to merge assemblies from the compilation of a web site, first seeing how to control the compiled assembly names with the –prefix option. Then see how to merge all the ...
Ever wanted to become a programmer? This Delphi Training Series: Programming 101 is a sequence of training videos designed to teach the complete beginner how to become a programmer using Delphi.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

Gigafide will show you how to slipstream Windows installations. You need to go to Vlite and download the program for Windows Vista. Install and run it. Select install at the main window. Use 7-zip to extract the ISO file. Next, go to that folder and run startcd.exe. You click next, agree to the terms and install it to the Vlite folder. Go to that folder, then Tools - x86 and select the file wimgapi.dll. Copy and paste that into the main Vlite folder. Go to Vlite, select your Windows Vista dis...

Welcome back, my budding hackers! Digital forensics is one of IT's most rapid-growing disciplines. All hackers should be familiar with digital forensics if for no other reason than to protect themselves. More than one hacker has been apprehended because they were unaware of the evidence trail they left behind.
This video shows you how to set environment variables in Windows XP. A lot of the older software written for windows requires the use of
Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Since the introduction of the Nexus 4 to the Google Play Store last November, the phone's been in constant demand thanks to the low price and sleek design. Even today, the phone is still listed as sold out. LG's Nexus 4 is also the only smartphone in circulation that can run a naked version of the Android operating system; one that does not come loaded with a manufacturer UI running over top of it.

Welcome back, my tenderfoot hackers! As you know, Metasploit is an exploitation framework that every hacker should be knowledgeable of and skilled at. It is one of my favorite hacking tools available.
MySpace is an excellent resource for up and coming musicians. If you just can't do without that hot new jam, then it's time to rip your favorite song using Audacity media player. This video tutorial demonstrates the process of ripping MySpace songs in a few easy to follow steps:

Check out this video tutorial on how to generate an Excel worksheet using XML. There's a free library from CarlosAG.net, and you need to get the free dll file from there. This video will show you how to use it. You need to use CreateExcelFile in Microsoft Visual Studio to use the XML. You will need to use Microsoft Excel 2003 or 2007 to open this file.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my greenhorn hackers! Congratulations on your successful hack that saved the world from nuclear annihilation from our little, bellicose, Twinkie-eating dictator. The rest of world may not know what you did, but I do. Good job! Now that we hacked into the malevolent dictator's computer and temporarily disabled his nuclear launch capability, we have to think about covering our tracks so that he and his minions can't track our good works back to us.
In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

You know what's awesome? You own a Nexus. That means, with Google's blessing, you have easier access and control over your device than other manufacturers allow. You can really dig in and do some interesting things if you root.

Whenever a new Android device is realized, the first thing I figure out how to do is to get it root access. Generally speaking, rooting has never been easier, with many one-touch methods like Stump and Towelroot available. But as manufacturers and carriers increase security with each new product, there is one tried-and-true root method that continues to work on most Samsung devices—Chainfire's CF Auto Root.

The problem of system freezes is not new to the world of Windows and this has come to light even in the latest Windows 8 release. In the event that your system freezes, you cannot open your desktop files, some controls stop functioning, or you are unable to launch the start screen applications either. You may experience this unusual behavior after updating Apps in the store or due to a driver issue. Sometimes, freezes occur because of video card problems too. In order to do away with these Wi...

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

In this tutorial I am going to show you how to create an undetectable Meterpreter Trojan using a Domain name. I have taken a few guides/tutorials and built it into one. The first part is creating the DNS Payload. The second part is creating the Executable file. Part 3 is using both in Shellter to create your undetectable Trojan. Part 4 is setting up your listener using Armitage.

How is it goin', fellow 1337 haXX0rZ! dtm here with another article, this time, we'll be looking at infecting PE files, executables in particular for this write-up. Obviously some prerequisite knowledge will be needed since this isn't really newbie-friendly. If you are still a beginner, fear not, it might still be interesting to read! Hopefully!

Hello fellow gray hat hackers, I wrote a program in python that helps me to fill up my proxychains.conf file, so I don't have to manually enter in the proxies. I figured I will give a little how-to of how I did it and maybe I could help some of you(hackers) out there to stay anonymous.

Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Welcome back, my greenhorn hackers! Continuing with my series on how to crack passwords, I now want to introduce you to one of the newest and best designed password crackers out there—hashcat. The beauty of hashcat is in its design, which focuses on speed and versatility. It enables us to crack multiple types of hashes, in multiple ways, very fast.

PowerShell Empire is an amazing framework that is widely used by penetration testers for exploiting Microsoft Windows hosts. In our previous guide, we discussed why and when it's important to use, as well as some general info on listeners, stagers, agents, and modules. Now, we will actually explore setting up listeners and generating a stager.

A hacker with privileged access to a Windows 10 computer can configure it to act as a web proxy, which allows the attacker to target devices and services on the network through the compromised computer. The probes and attacks appear to originate from the Windows 10 computer, making it difficult to detect the attacker's actual location.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Today I will show you how to create a simple keylogger in Visual C# Sharp, which will start up hidden from view, and record anything the user types on the keybord, then save it into a text file. Great if you share a PC and want to track what someone else is writing.

Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems useless. It affected both free and paid AVG owners.