Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

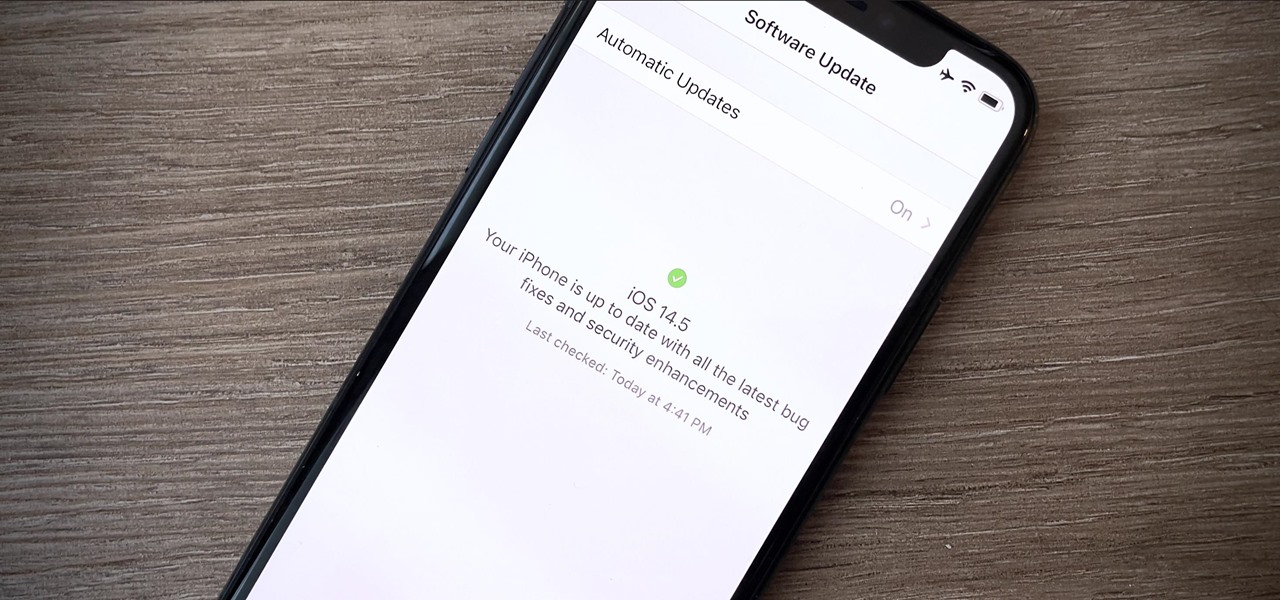
Apple seeded software testers iOS 14.5 public beta 6 today, Wednesday, March 31. The update includes a new battery calibration for iPhone 11, 11 Pro, and 11 Pro Max, as well as two new Siri voices.

Apple just seeded developers the sixth iOS 14.5 beta today, Wednesday, Mar. 31. The update includes a calibration for battery health measurements for the iPhone 11 line, as well as two new Siri voices.

So far, iOS 13's major point updates have all been pretty exciting for iPhone. We've seen iOS 13.1, 13.2, and 13.3 come and go, offering more than 60 new features and changes combined to that very first version of iOS 13. While iOS 13.3.1 was a minor update, its successor, iOS 13.4, is a return to form.
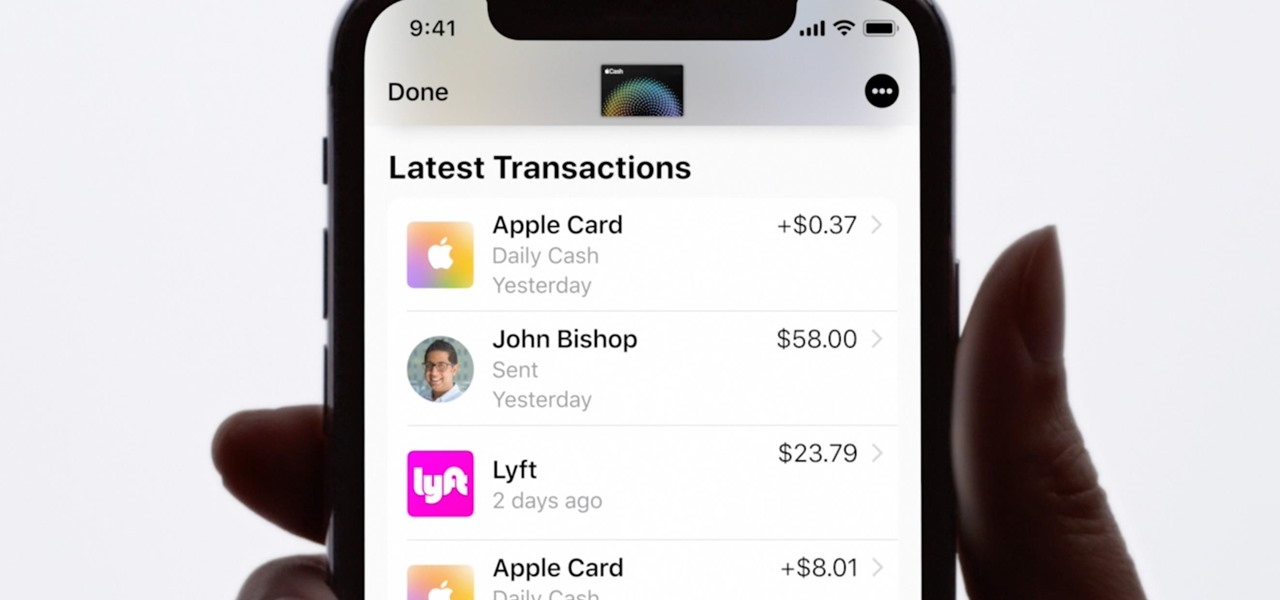
Apple Card is the iPhone OEM's big leap into the credit card market. Its low barrier to entry and ease of use make it an appealing option, especially for those who often pay for goods with Apple Pay. To get the best rewards possible, make sure you use the Apple Card at stores where you can get 3% cash back.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Ringtones and text tones can be annoying, so my iPhone is almost always set to vibrate on silent mode. Unfortunately, that causes me to miss phone calls and text messages when the device isn't in my hands or pockets. While I hate missing alerts, I'm still reluctant to switch to ring mode — and that's where another iOS and iPadOS feature helps out.

UPDATE: Entries are now closed. Thank you for participating! Next Reality is where we help you literally 'see' into the future of augmented reality, and to help with that mission we're offering three free pairs of Snap Spectacles 3 to three lucky readers who sign up for the Next Reality daily AR email newsletter.

Google doesn't get enough credit for it, but they definitely make some of the best phones for rooting and modding. Heck, if you want to replace the entire operating system on a Pixel, you can do it pretty easily. It all starts with the bootloader.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

Collaboration is available in many different Apple apps, from Notes and Reminders to Photos, Freeform, and even Files. Now you can add to the list Apple Music, which will let you collaborate on playlists with friends.

The race for the future of AR wearables gained steam this week with several pivotal developments. First, Apple, the subject of numerous reports and rumors regarding its purported AR headset, is reportedly eyeing an in-person unveiling of the device for later this year, rather than introduce it at its upcoming virtual Worldwide Developers Conference, which would usually be as good a time as any to make a big AR hardware announcement.

Welcome to the first annual Next Reality 30, our list of people who've made the biggest impact on the augmented reality space in the last 12 months — and what a 12-month roller-coaster ride it's been. Apple introduced ARKit-powered apps last fall, Google launched ARCore for Android soon after, Snapchat began monetizing AR, and the Magic Leap One headset finally came out. These are historic times.

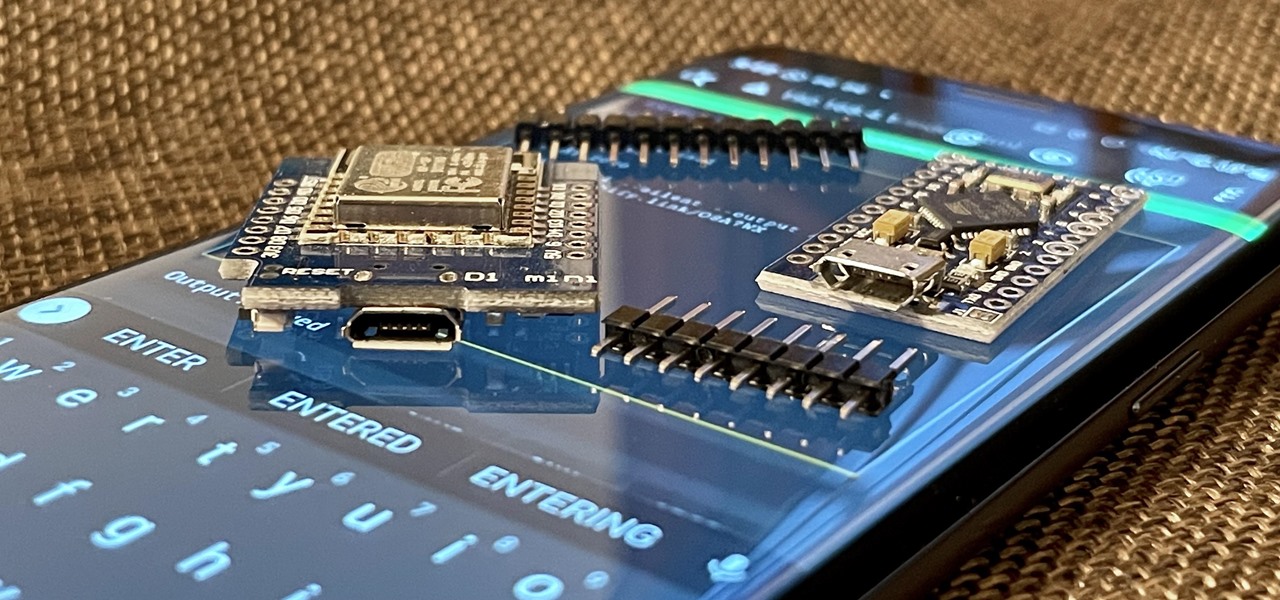
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Apple released iOS 17.4 on March 5 with over 30 new features, but now it's iOS 17.5's turn for the spotlight. The update, currently available as a release candidate, gives us a few interesting updates and changes for iPhone, including a new word game, and there's even a sneak peek at what could be coming in the stable build.

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

Apple's iOS 15.4 update for iPhone is out after 46 days of beta testing, and it has some exciting features you won't want to miss. Here's everything you need to know about the new software.

Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

You know it's crazy out there when governments start blocking social websites like Facebook, Twitter and even YouTube. But that's what happened in Egypt, when tens of thousands of anti-government protesters took to the streets on Tuesday (January 25th) in hopes of ending President Hosni Mubarak's 30 years of authoritarian power.

It's somewhat funny that the HTC ThunderBolt smartphone would be released around the same time as Apple's new Thunderbolt technology. Mainly because HTC's smartphone isn't exactly something I would compare to a flash of lightning, which averages around 60,000 miles per second. But Apple's new interconnect surely deserves the Thunderbolt designation.

New to eBay? Don't worry, setting up an account and buying and selling doesn't take that much effort at all. Everyone who has an Internet connection has at one point come across eBay, to find the perfect gift for their loved ones, to find the cheapest deals on plasma televisions and computers, or to get rid of their dusty, old record album collection in their web store.

It's no secret that Apple has retail stores in China, along with a large amount of Premium and Authorized Resellers. But a recent post by blogger BirdAbroad has caused quite a commotion in the world of all things Apple, claiming that in her home city of Kunming, there is another breed of Apple Store locations... "Un"Authorized ones.

This video demonstrates how to transfer iTunes purchases from one authorized computer to another. All you need to do is connect your iPod to a different computer and click transfer purchases. Transfer your iTunes movies to another computer.

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.
“The UK government is rounding on protesters ahead of this summer’s Olympics, issuing the first court order to ban an Occupy activist from the event. The unprecedented security measures for the Games have been branded as over-the-top,” reports RT.

Bad weekend for Apple, or so the New York Times reports. The top secret version of the next iPhone was mistakenly left in a bar, resulting in a complete breakdown of the yet-to-be released product.

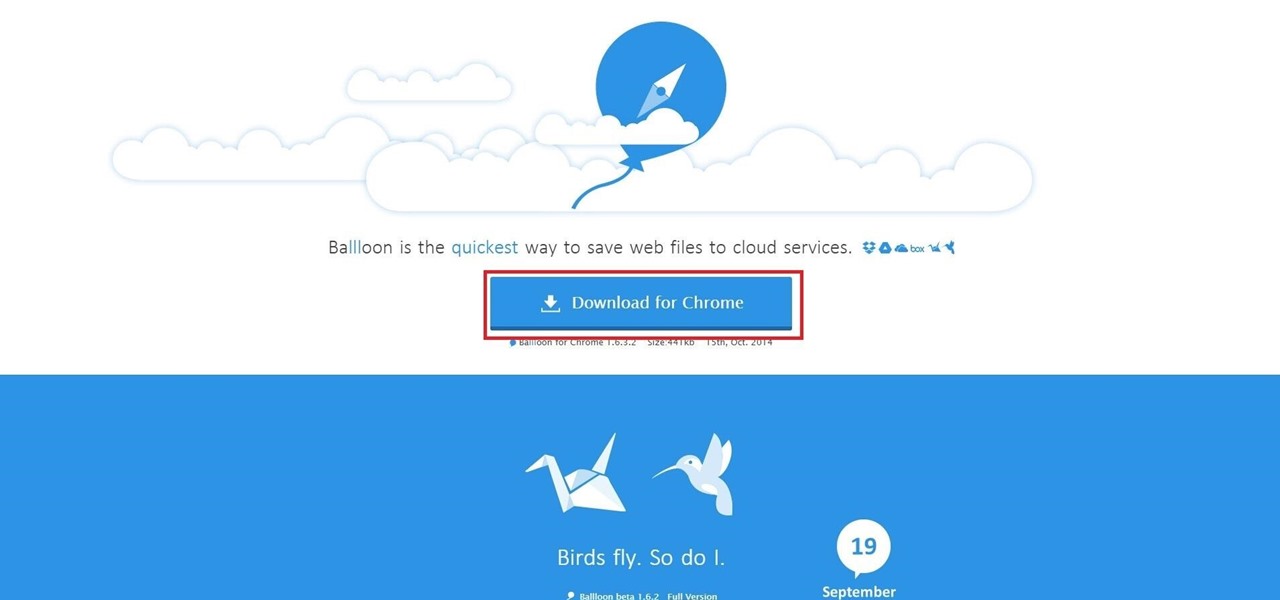
Step 1: First in first, you have to install a Chrome browser, and download Ballloon from official site You can also download it at Chrome Web Store

Professionally and academically speaking, I am a computer scientist, but I also enjoy lock picking as a hobby, so I thought I would share what knowledge I have with this. Before we start doing anything, first we need to understand the fundamentals of how locks work and then acquire and familiarize ourselves with basic lock-picking tools.

In the first part we differentiated the two types of control, mental and physical. In part 2 we will dig deeper into Physical crowd control and analyze examples that are present today.

This is my attempt to show people some cool things we can do with programming, and to give a small incentive for people to join the weekly Community Bytes. I wanted to make a tutorial on how to use Twitter from the command line with Python. This would have been an easy project to do not too far back, and a good bit of practice for a beginner to programming. It teaches that you can do useful stuff with programming. However, a while ago Twitter started using something called OAuth to access the...

This week, Apple announced the beta version of its new wireless, cloud-based service, iCloud. I wrote a summary of it here. The iCloud service includes some new features in the latest version of the iTunes Store, which allows you to access all your iTunes songs, mobile apps, and eBooks purchased in their respective iTunes stores and download that media to up to 10 of your devices—your iTunes supported Macs and PCs and mobile devices. This downloading can all be done wirelessly without you hav...

I can't say it's absolutely true, but when it comes to mobile word gaming, there's Scrabble people and then there's Words with Friends people. It feels segregational. Rarely does one play both. At least, that's what I see when it comes to my family and friends.

Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!

The game has undergone many transitions over the years, since its days as LEXIKO (1931) to its briefness as CRISS CROSS WORDS to its current and amalgamated, renowned brand of SCRABBLE. There has been many editions of the word board game along that historic metamorphosis, and SCRABBLE has even given in to pop culture, sports memorabilia, and fanaticism.