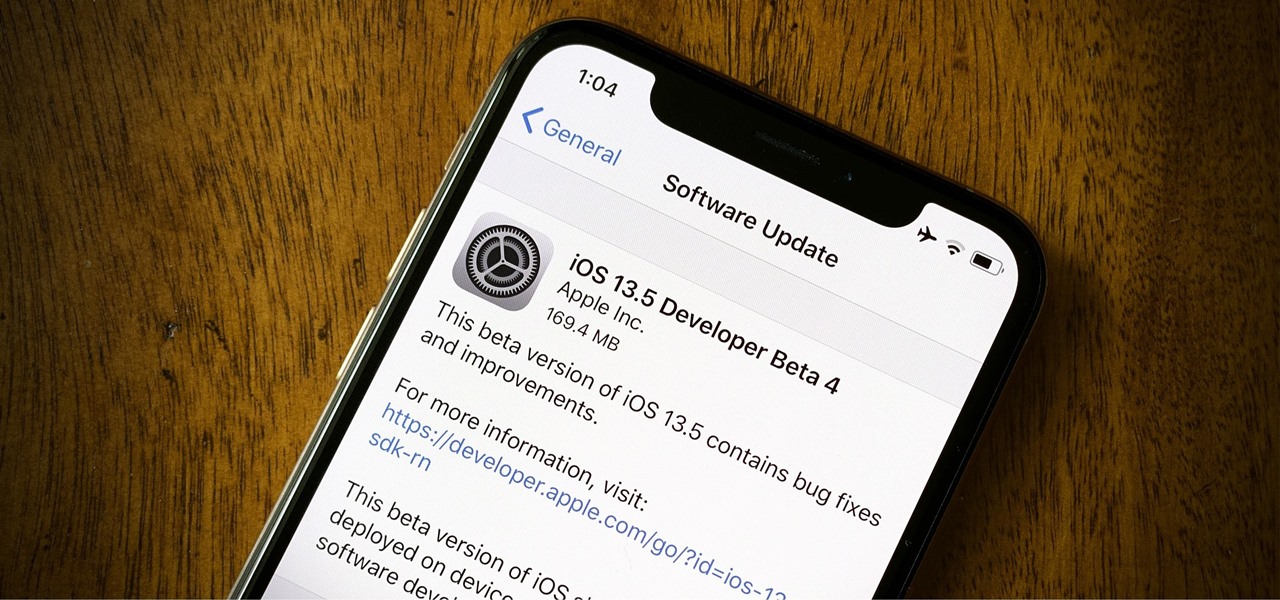
Apple released the fourth developer beta for iOS 13.5 today, Wednesday, May 6. This update comes one week after the release of iOS 13.5 dev beta 3, which introduced Apple and Google's joint COVID-19 exposure notification API to iOS for the first time. Apple updated that settings page to now include an "Exposure Logging" setting instead.

Apple released the fifth public beta for iOS 13.4 on March 10. The update comes three hours after the release of developer beta 5, and exactly one week after iOS 13.4 public beta 4.

Look, we like a new beta update as much as the next tester. There's nothing better than downloading and installing a fresh iOS seed, hunting down any and all new changes and features from the last. That said, we're a bit surprised Apple decided to release iOS 13.4 developer beta 5 on March 10 since dev beta 4 was such a minor update.
With today's release of iOS 13.4 developer beta 4, it seems Apple is closer than ever to releasing the official build for its upcoming iOS update. If you've been following the beta closely, you know that means new Memoji stickers, CarKey API support, and Mail toolbar updates, in addition to general bug fixes. Public testers can now take that extra step, as Apple just released 13.4 public beta 4 today.

March is looking to be an eventful month for Apple. Even with coronavirus throwing the tech industry into uncertainty, we still expect Apple to release the iPhone SE 2, the long-awaited follow up to the iPhone SE. Is it possible we'll also see iOS 13.4 fully released this month? We wouldn't be surprised if we do, seeing as Apple just released its fourth developer beta.

Before the Sept. 2017 event held by Apple, we thought the new iPhone X would come in three different colors. While only a Space Gray and Silver option made it to the Nov. 2017 release, the missing third hue may finally be on its way, if the latest rumors are to be believed. If you can't wait for the new Blush Gold color, here's when and how you can expect to get your hands on one.

If the recent "state sponsored" Yahoo hack wasn't enough motivation for users to stop using their services, the latest news about Yahoo should be. Joseph Menn, a reporter at Reuters, just revealed that Yahoo created a custom email wiretap service for the US government.

A judge just handed down a ruling that will make the U.S. government's quest to unlock the work iPhone of one of the San Bernardino shooters much more difficult.

If you are anything like me, you have a knack for taking silly selfies of yourself, i.e., taking scotch tape and wrapping it around your face to make yourself look like the blob, or perhaps you like taking selfies of yourself in weird or unusual situations doing weird and unusual things.

The next mobile operating system for the iPhone, iOS 6, will be available in fall 2012. The major details and features were released 2 weeks ago a Apple's World Wide Developers Conference (WWDC). While the goal of these yearly OS updates is to move forward with technology, there are a couple of this to watch for. Keep reading to see the good and the not so good. Do Not Disturb

In a welcomed Wednesday twist, iOS 13.4 public beta 3 follows the release of developer beta 3 by just three hours. While that isn't super uncommon for most beta cycles, it is for this one. Apple waited 24 hours between dev beta 2 and public beta 2, and five full days between dev beta 1 and public beta 1. It's nice to see these betas coming out on the same day again.

So far, iOS 13.4 hasn't been a disappointment. From new Memoji stickers, a refreshed Mail toolbar, and even the beginnings of controlling your car with your iPhone, Apple's latest iOS update is looking like a good one. That's why we're excited that Apple just released the third 13.4 developer beta today, one week after the release of the second one.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

With the growing list of products Apple offers, the number of devices connected to your Apple ID can get quite extensive. Having all those devices connected to your Apple ID helps you keep track of them, but when it comes time to part ways with an Apple TV or Apple Watch, those devices can still be attached to your Apple ID. In some cases, this could affect the overall security of your account.

When Google introduced the Pixel 3 on October 9th, one of new additions they briefly mentioned was the Titan M security chip. While they did talk about how it will improve overall security, they didn't expand on the number of changes it brings to the Pixel 3's security. Well, they finally shared more, and it's a pretty big deal.

Each year, Apple seems to design its devices to be more difficult for owners to repair themselves. So when an iPhone breaks, a trip to the Genius Bar or an Apple Authorized Service Provider is most likely necessary. But if you have an iPhone X that needs a new battery, a leaked video just spilled the beans on how to replace the battery precisely as Apple would.

Starting Nov. 1, 2018, Google got a lot tougher with Android app developers. New apps being uploaded to the Play Store already had to target Android 8.0 Oreo or higher as of August, but now, every update to existing apps has to do the same. It may seem like a simple rule, but it will have some serious repercussions.

If you've ever connected your iPhone to a computer before, you know iOS prompts you to "Trust" the computer and enter your passcode to confirm. According to Apple, trusted computers can "sync with your iOS device, create backups, and access your device's photos, videos, contacts, and other content." That's a lot of permissions to hand off, especially if the computer's not your main laptop or desktop.

Followers are everything. After all, you need someone to listen to your tweets about last night's episode of your favorite TV show. But what about when people unfollow your account? Not only have you lost part of your follower base, you have no idea who left. Luckily, there are tools out there to help you learn just that, even if Twitter itself won't give up the info.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

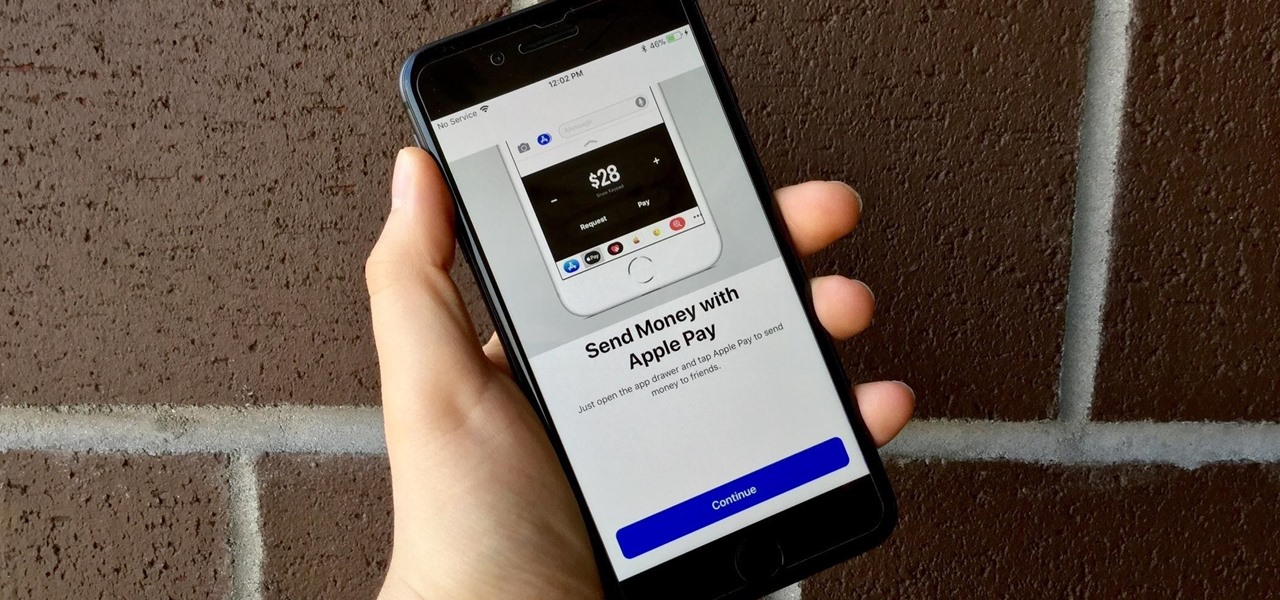
Move over Venmo, Apple Pay Cash is here, and it's built right into iMessage. If you're like us, you've been eagerly waiting to give this new feature a try on your iPhone ever since Apple announced it during WWDC 2017 back in June. While it was never released in the main iOS 11 update, it finally showed up in iOS 11.2.

A new medical development is going to change the way many of us look at getting the flu vaccine. A painless flu vaccine skin patch is making needles and vials a thing of the past. Researchers from the Georgia Institute of Technology and Emory University have shown that a flu vaccine can be administered safely and comfortably with this new patch, which delivers the vaccine through a matrix of tiny dissolving microneedles.

Yellow fever has emerged again in Brazil, causing death and disease to people unprepared for this mosquito-borne illness.

Welcome back, my fledgling hackers! It's been awhile since we did a Metasploit tutorial, and several of you have pleaded with me for more. I couldn't be happier to oblige, as it's my favorite tool. For the next several weeks, I'll intersperse some new guides that'll help expand your Metasploit skills and keep you abreast of new developments in Metasploit, so look for them in the near future.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Safari's private browsing mode on your iPhone won't sync to other Apple devices or remember your search history, AutoFill data, or visited webpages. Still, it doesn't stop anyone who accesses your iPhone from opening your private tabs. If you don't want anyone snooping through your private tabs, use Chrome instead so you can lock the tabs behind biometric authentication.

After years of testing and modifications, the US Army is moving forward with its customized version of HoloLens 2 from Microsoft.

Apple released iOS 13.4 to public beta testers on March 18. The update comes the same day we learned that iOS 13.4 would be made available March 24. The sixth beta is iOS 13.4's GM (golden master), even though Apple refers to it as "beta 6."

Apple released iOS 13.4 to registered developers on March 18. The update comes just hours after news broke that iOS 13.4 would hit all compatible devices on March 24. The update is the GM (golden master), which makes it the same build as the official release we expect to see on March 24, although Apple does refer to it as "beta 6" on the dev site.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Database technology has vastly improved the way we handle vast amounts of data, and almost every modern application utilizes it in one way or another. But the widespread use of databases naturally invites a slew of vulnerabilities and attacks to occur. SQL injection has been around for awhile, and as such, there are many defense methods in place to safeguard against these types of attacks.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

As cheesy as it sounds, #HODL became a thing for a reason. A lack of discipline when dealing with cryptocurrencies can lead to impulse buys and panic selling, and ultimately, depleted funds. Luckily, Coinbase has a way to safeguard your cryptocurrency savings to not only protect them against thieves, but to also help you resist the urge to sell off your investments.

When traversing the web, you'll regularly come across websites that require you to create an account. With the majority of these accounts, protection is limited to a simple password. Despite this, many people are still using weak passwords such "123456." For these reasons, you really need a password manager, and our research has shown that LastPass is still your best bet.

As pentesters and hackers, we're going to be working with text frequently — wordlists, configuration files, etc. A lot of this we'll be doing on our machine, where we have access to whatever editor we prefer. The rest of it will be on remote machines, where the tools for editing will be limited. If nano is installed, we have an easy-to-use terminal text editor, but it isn't very powerful.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

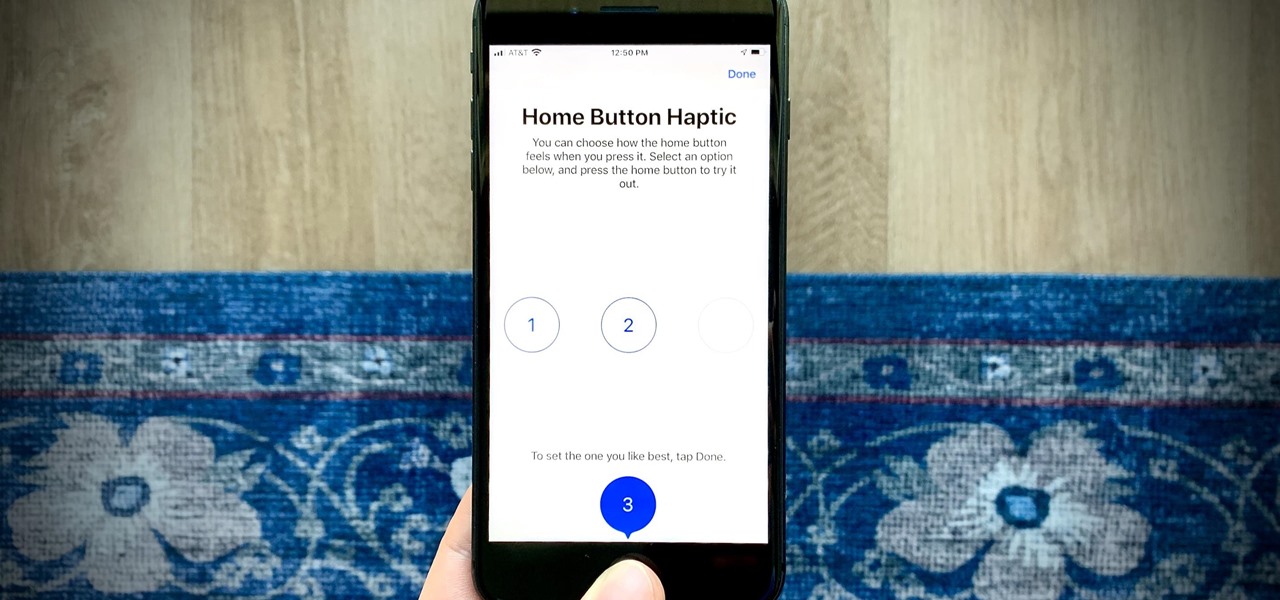
If there's been one signature design element for Apple's iPhones, it was the circular Home button. It served as the "everything" button for each iPhone model until last year's iPhone X, but now, it's completely absent from the iPhone XS, XS Max, and XR. Should you be worried? Short answer: No.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.