An accelerometer is capable of detecting how the device is being moved by the user, a feature which can add an extra level of functionality for an application which knows how to take advantage of it. This video explains several different methods for incorporating the presence of an accelerometer into your mobile content.
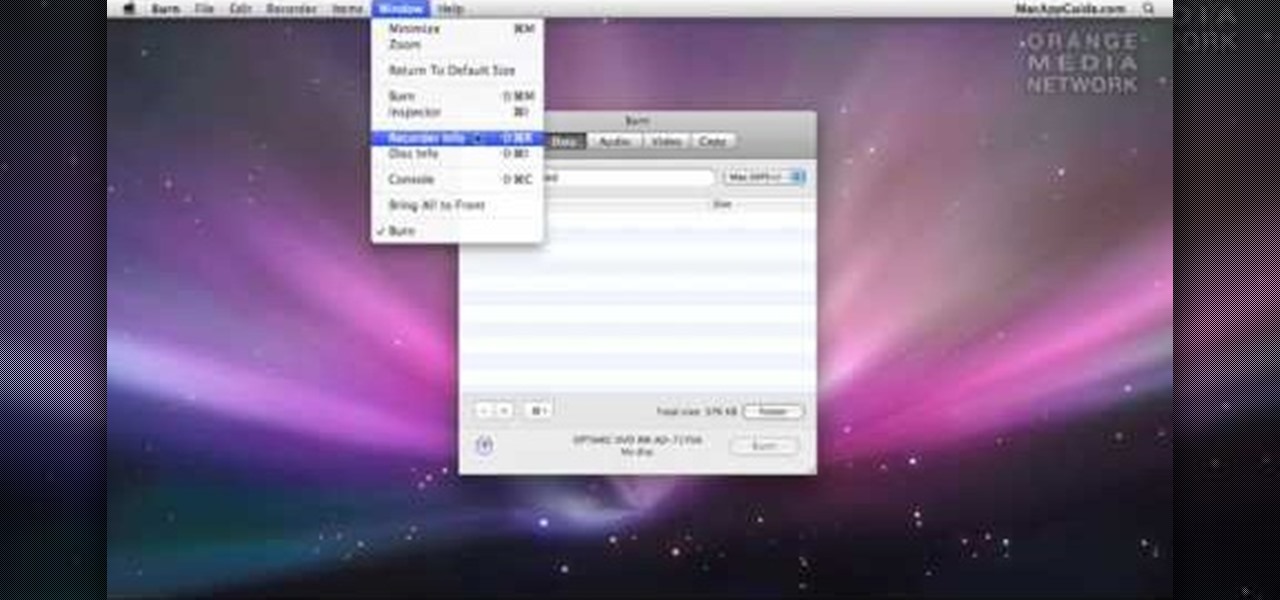
In this video tutorial, viewers learn how to burn a CD or DVD on a Mac computer with the Burn application. Burn is able to create data, audio and video discs. The Inspector window allows users to edit extra information about the disc. To open Inspector, press the Command and I button. It is also able to create disc copies. To burn a disc, name the disc and select a format. Them simply drag the file(s) into the program and click Burn. This video will benefit those viewers who have a file on th...
Tortoise is an incredibly useful tool for programmers and those who do write or are planning to write lots of software on a Windows machine. New users don't have to worry about getting an SVN, but more advanced users will appreciate the functionality.

In this clip, you'll learn how to use ATI Video Converter to transcode video. It's an easy process and this video presents a complete guide. For more information, including a full demonstration and detailed, step-by-step instructions, watch this helpful home-computing how-to.

The use of smart phones is not limited only as a mode of communication now-a-days. There are many things that can be done with the help of a smart phone.

If you thought Google was sitting on the sidelines of the growing race toward mainstreaming augmented reality, think again.

In this Windows 8 Tutorial you will learn how to change the application tile size for metro applications. If the application is not a metro style application you will not be able to re-size it. Their are a few benefits to changing the tile size of applications including the ability to have more applications viewable in smaller space so that you don't have to scroll through assuming you make applications smaller. Enlarging the application will allow you to see more information about that app. ...

While SSH is a powerful tool for controlling a computer remotely, not all applications can be run over the command line. Some apps (like Firefox) and hacking tools (like Airgeddon) require opening multiple X windows to function, which can be accomplished by taking advantage of built-in graphical X forwarding for SSH.

This Windows 8 guide is for those who are new adopters of the Windows 8 operating system. Maybe you just bought a new PC with Windows 8 and you need to learn your way around, then this tutorial is for you.

In this Windows 8 Tutorial you will learn how to pin application to the task bar. If you work with certain programs very often it will be beneficial to pin those Windows 8 applications to your task bar in the desktop view. Once you pin an application to task bar in desktop view it will always be visible too you and with one click you will be able to launch application. Thank you for viewing our Windows 8 tutorials. If you need help with a certain area of Windows 8 and would like us to make a ...

Apple has sprung a massive AR following since the announcement of their ARKit, with users waiting to see what exactly the tech giant will do next.

I have made a video to show how we can add an applet into web application. It is shown in two parts. The applet can communicate with database too.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Web application firewalls are one of the strongest defenses a web app has, but they can be vulnerable if the firewall version used is known to an attacker. Understanding which firewall a target is using can be the first step to a hacker discovering how to get past it — and what defenses are in place on a target. And the tools Wafw00f and Nmap make fingerprinting firewalls easy.

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

One of the worst-kept secrets in the tech world is Apple's plans for consumer-grade AR smartglasses, still unconfirmed publicly and only recently corroborated through a leaked account of an internal employee meeting.

An augmented reality system developed by Lyft might make it less awkward for drivers to figure out who they are supposed to pick up.

Eventually, even the most private company has to file its patents and unveil its tightly-held secrets, and Magic Leap is no exception.

In this Windows 8 tutorial, you will learn how to show and hide desktop application icons. The benefit of this is it allows you to quickly hide desktop icons and show them again when you need to have access via desktop.

Once you've installed Ubuntu with security in mind and reduced the possibility of network attacks on your system, you can start thinking about security on an application level. If a malicious file is opened on your system, will an attacker be able to access every file on the computer? The chances are much slimmer if you put the proper defenses in place.

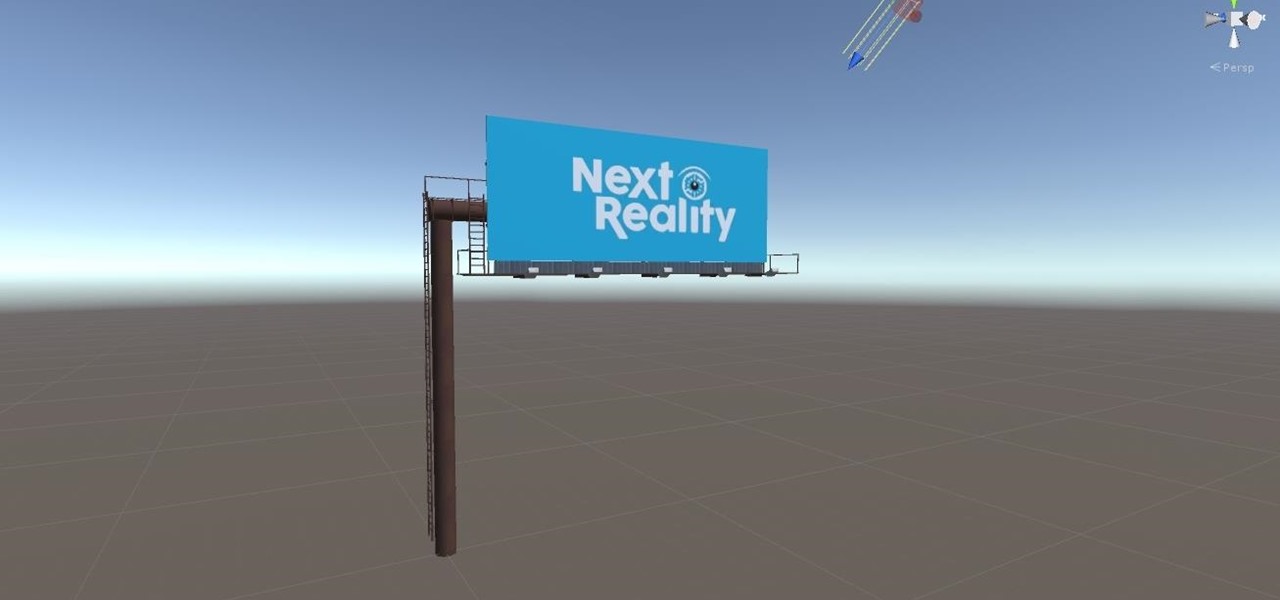
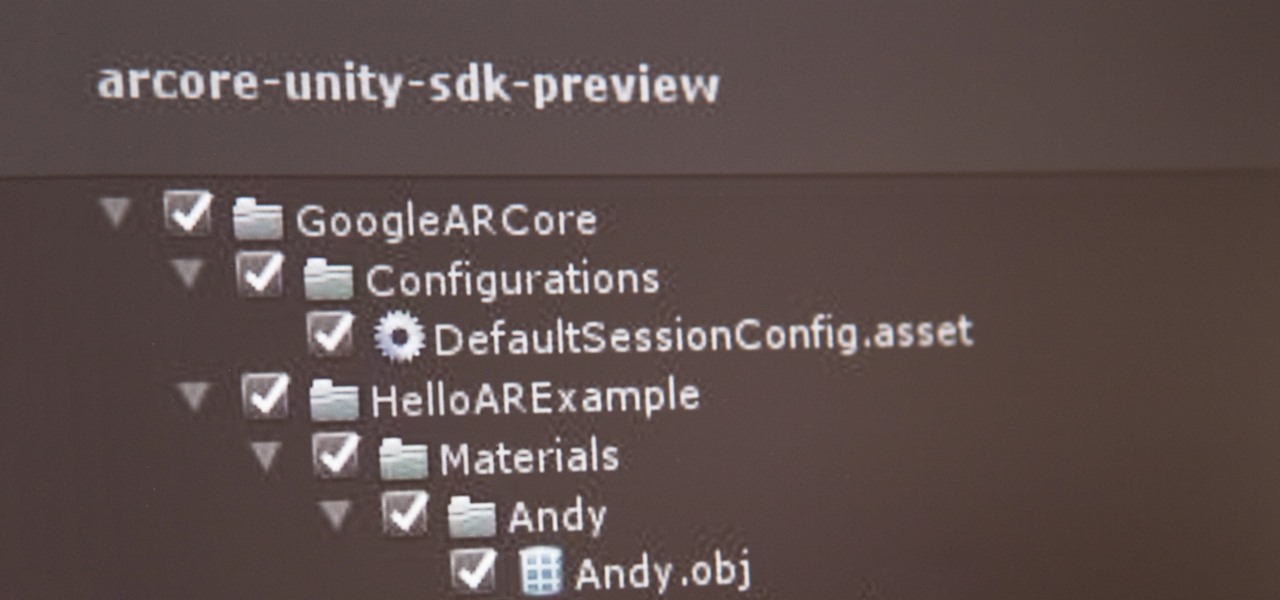
With the software installation out of the way, it's time to build the framework within which to work when building an augmented reality app for Android devices.

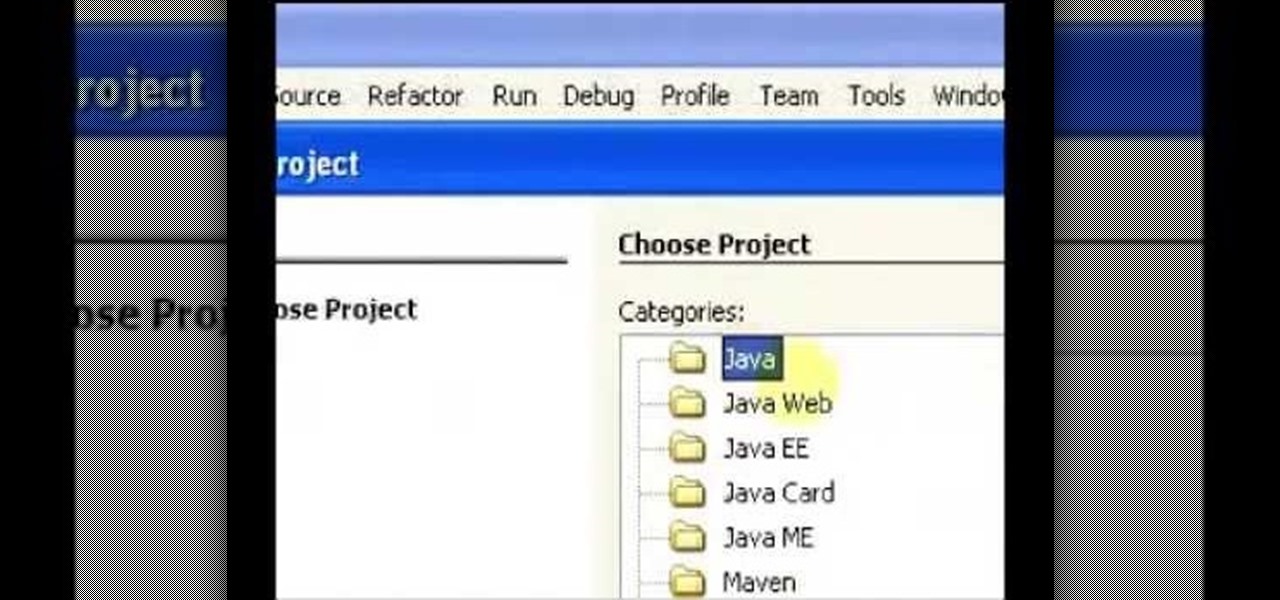
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.

As a kid, I was always interested in what was beyond our world. I remember lying down on the top of my dad's car and watching the stars for hour, gleefully excited whenever a shooting star streaked across the night sky.

Have you ever looked at your iPhone dock and wished you could place an extra, essential, or highly utilized app on there? Currently, with the basic settings you can only place four, but there's always that one that you wish could add to the mix.

Now that ARCore is out of its developer preview, it's time to get cracking on building augmented reality apps for the supported selection of Android phones available. Since Google's ARCore 1.0 is fairly new, there's not a lot of information out there for developers yet — but we're about to alleviate that.

The ability to execute system commands via a vulnerable web application makes command injection a fruitful attack vector for any hacker. But while this type of vulnerability is highly prized, it can often take quite a bit of time to probe through an entire application to find these flaws. Luckily, there is a useful tool called Commix that can automate this process for us.

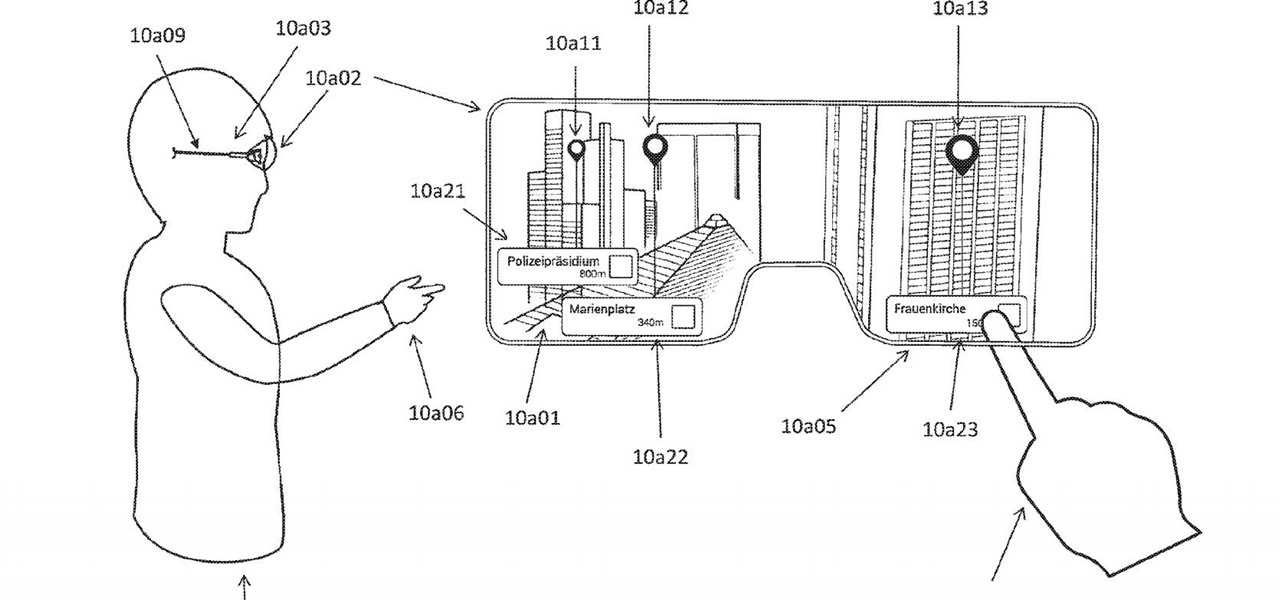
One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

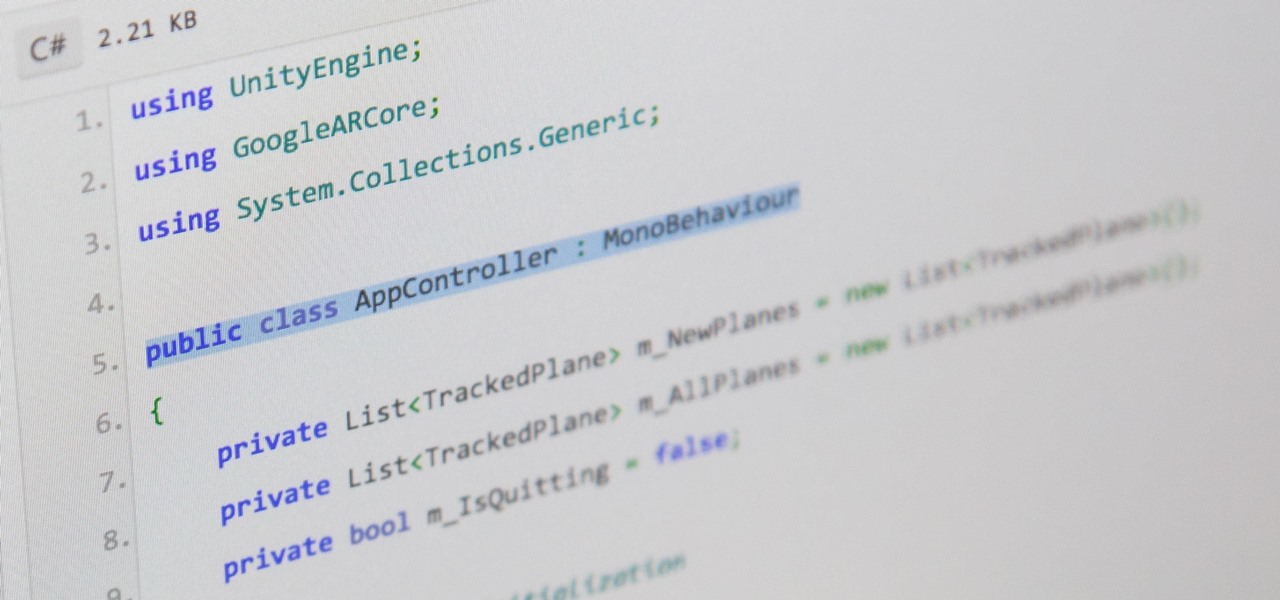
There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

Magic Leap has always been intensely secretive about its work on its augmented reality headset, so it's interesting that they're now publicly recruiting developers to build software for the device before its launch.

In this Windows 8 Tutorial you will learn how to search for application in the Windows 8 store. I know it can be a bit confusing for those who have just moved to the Windows 8 store on how to search for store applications in fact it took me like an hour to figure out how to search because all the visual cues were hidden away. However when you finish watching this Windows 8 tutorial you will see it is as easy as being able type on your keyboard to find applications in the Windows 8 store.

Web applications are becoming more and more popular, replacing traditional desktop programs at an accelerated rate. With all these new apps out on the web comes various security implications associated with being connected to the internet where anyone can poke and prod at them. One of the simplest, yet the most prevalent types of security flaws found in modern web apps are SQL injections.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Visualization is one of the obvious commercial applications for technology such as Microsoft's HoloLens. The ability to see the assets of a project in different scales—from micro to larger-than-life—with a quick air tap will play a large part in the coming augmented reality revolution. Whether the assets are art for a game, interior design, raw financial data, or architecture, data visualization will play an important role in the future. This is due, in part, to our ability to absorb informat...

The reveal of Apple's new ARKit extensions for iPhones and iPads, while not much of a shock, did bring with it one big surprise. By finding a solution to surface detection without the use of additional external sensors, Apple just took a big step over many — though not all — solutions and platforms currently available for mobile AR.

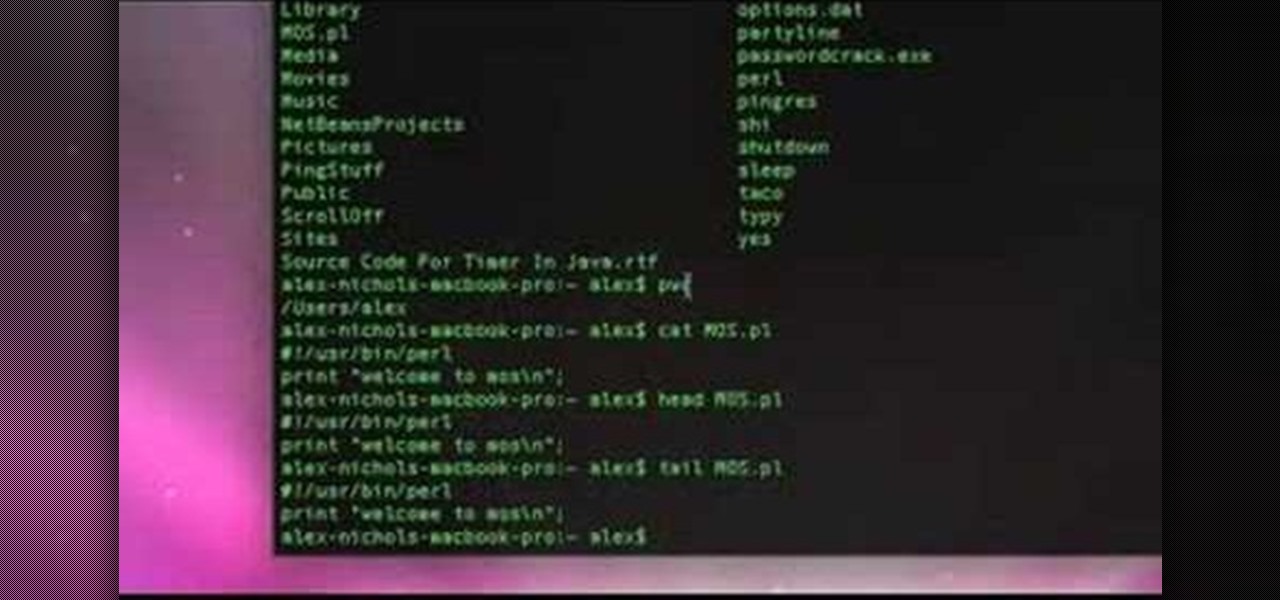
Every Apple computer running Mac OS X comes with a handy application called Terminal… MacBooks, MacBook Pros, Mac Pros, iMacs, etc. They all have Apple Terminal, and it can be found in your Utilities folder in Applications. Which means you can use it.

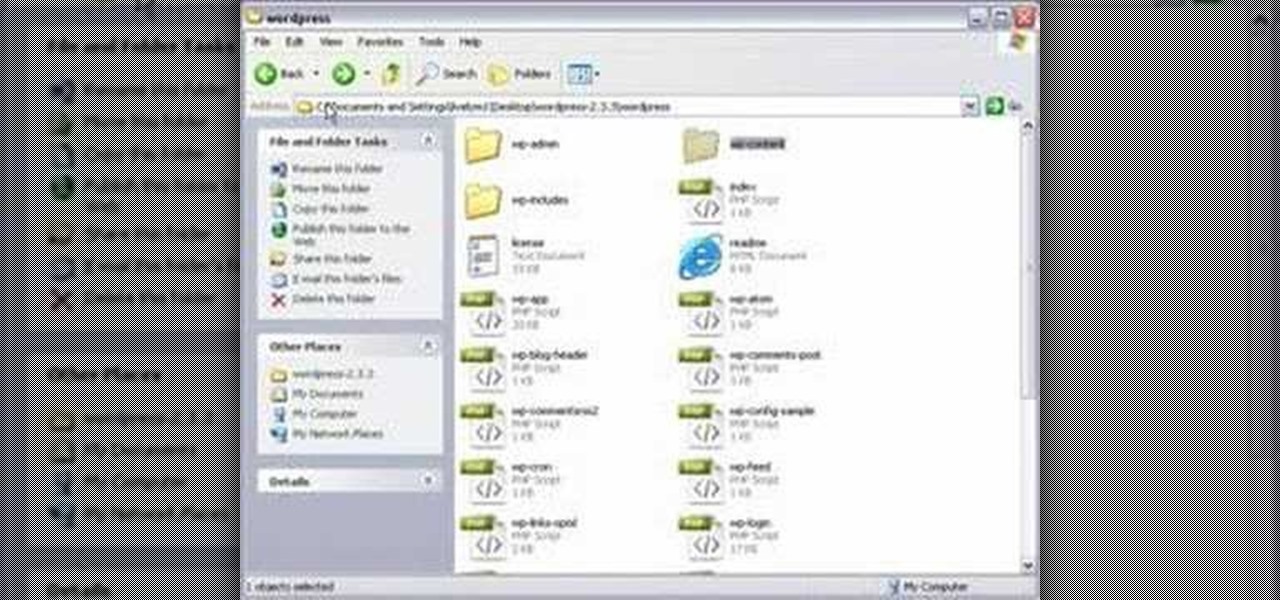
In this tutorial series Mike Lively shows how to convert Wordpress into the Adobe Flex 3 application Flexpress.

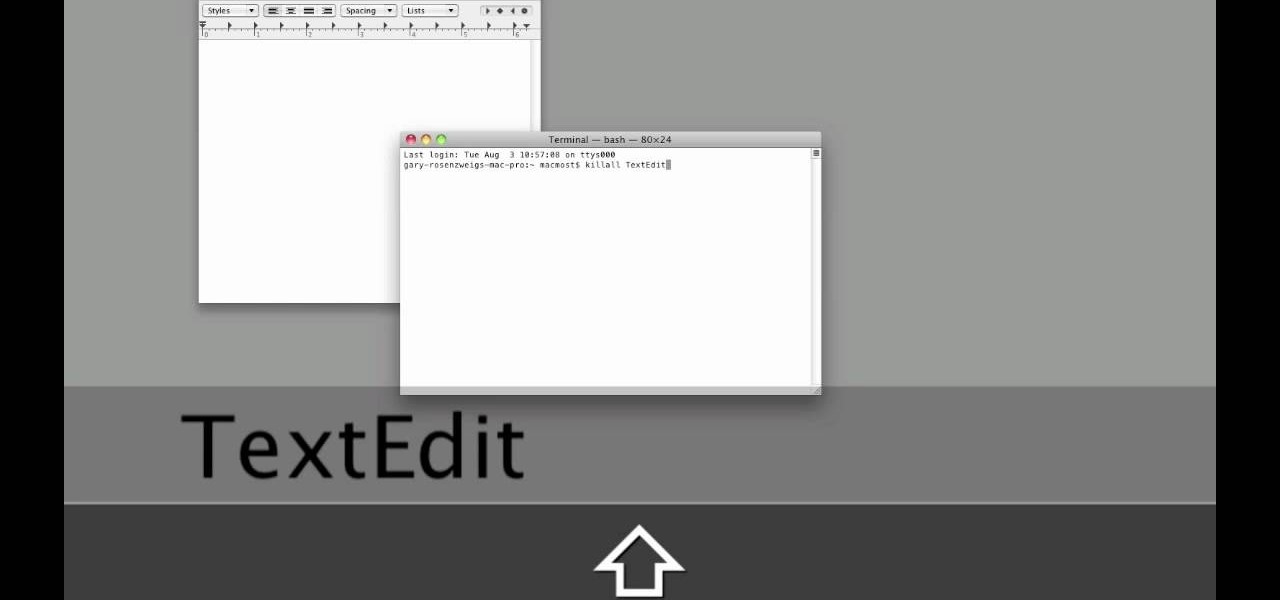
When it comes to closing applications in Mac OS X, there are more options available than just clicking the little red circle in the left-hand corner of an application window. There are, in fact, 10 different ways in which a person can quit an app. And this handy home-computing how-to demonstrates each and every one of them.

Adobe apparently did not plan for it's AIR protocol to lead to people turning their websites into programs, but it turns out that it is fairly easy to do. This video tutorial explains in great detail how to create an AIR application using Flash CS4. Topics include how to create a digital signature and .swf files that you will need to create the program.

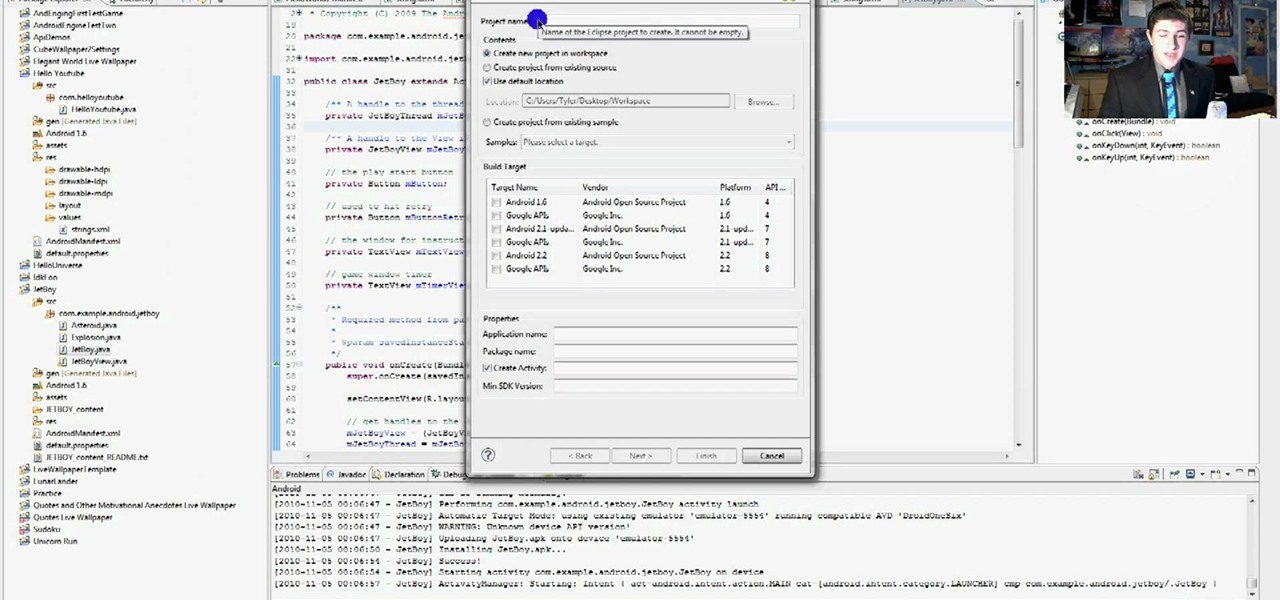
Develop your own Android app by following along this informative video. After installing the Eclipse IDE and the Android development environment, the walkthrough shows you the steps of compiling prewritten code into an Android app and viewing it on an emulator. Next, a step-by-step process to creating a simple "Hello World" app is demonstrated and explained.